- Cisco Community
- Technology and Support
- Security
- Network Security
- Firepower initial config doesn't seem to block threats - any help appreciated
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firepower initial config doesn't seem to block threats - any help appreciated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2019 06:32 PM - edited 03-12-2019 07:14 AM
Hi
A client of mine has recently purchased two ASA 5516-X with Firepower devices and, not being very experienced with the product, I can't seem to get it to block simple threats.
Details of one of the units is in the text below, but basically I don’t believe that the IPS is preventing traffic that it should (and is permitting all traffic).
I suspect that this is a very simple configuration issue but I don’t understand why the traffic is not being dropped as I suspect that it should. Any help with this would be most appreciated.
Some problem details
We have deployed the ASA 5516-X in a VLAN
# show ver
Cisco Adaptive Security Appliance Software Version 9.8(3)8
Firepower Extensible Operating System Version 2.2(2.97)
Device Manager Version 7.9(2)152
Compiled on Tue 07-Aug-18 22:53 PDT by builders
System image file is "disk0:/asa983-8-lfbff-k8.SPA"
# show module
Mod Card Type Model Serial No.
---- -------------------------------------------- ------------------ -----------
1 ASA 5516-X with FirePOWER services, 8GE, AC, ASA5516 JAD224702H9
sfr FirePOWER Services Software Module ASA5516 JAD224702H9
Mod MAC Address Range Hw Version Fw Version Sw Version
---- --------------------------------- ------------ ------------ ---------------
1 70b3.1779.602d to 70b3.1779.6035 3.2 1.1.14 9.8(3)8
sfr 70b3.1779.602c to 70b3.1779.602c N/A N/A 6.3.0-83
Mod SSM Application Name Status SSM Application Version
---- ------------------------------ ---------------- --------------------------
sfr ASA FirePOWER Up 6.3.0-83
Mod Status Data Plane Status Compatibility
---- ------------------ --------------------- -------------
1 Up Sys Not Applicable
sfr Up Up
The system has been deployed with a Bridged connection (BVI) translating between VLAN 500 and 2501.
I have a device with IP host address of .4 in VLAN 500 and a second windows PC with host address of .180 in VLAN 2501
Packets are passing through the ASA Firewall between these devices and are being directed to the SFR module. The SFR Module is sensing the traffic and allowing it.
Logs from the ASA and FirePower are confirming that this is occurring.
However when I use NMAP to simulate various attacks and scans, the SFR does not appear to be providing any protection and is still allowing the traffic.
have attached parts of the Firepower rules. I have tried various ways to implement the same thing all without changing the behavior.
No intrusions show in the firepower log but I can see the connections. I can also verify that the packets are getting through.
I have tried various TCP and UDP port-scans, DOS Scripts, vulnerability scripts using nMap.
Thanks for any assistance...
Config of ASA:
: Saved
:
: Serial Number: JAD224702H9
: Hardware: ASA5516, 8192 MB RAM, CPU Atom C2000 series 2416 MHz, 1 CPU (8 cores)
: Written by enable_15 at 10:52:44.695 WST Thu Dec 20 2018
!
ASA Version 9.8(3)8
!
firewall transparent
hostname IPS1
domain-name x.local
enable password
names
no mac-address auto
!
interface GigabitEthernet1/1
channel-group 1 mode active
no nameif
no security-level
!
interface GigabitEthernet1/2
shutdown
no nameif
no security-level
!
interface GigabitEthernet1/3
shutdown
no nameif
no security-level
!
interface GigabitEthernet1/4
shutdown
no nameif
no security-level
!
interface GigabitEthernet1/5
shutdown
no nameif
no security-level
!
interface GigabitEthernet1/6
shutdown
no nameif
no security-level
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
!
interface GigabitEthernet1/8
shutdown
no nameif
no security-level
!
interface Management1/1
management-only
nameif management
security-level 0
ip address y.32.1.200 255.255.255.0
!
interface BVI250
ip address x.30.132.240 255.255.255.0
!
interface Port-channel1
lacp max-bundle 8
nameif Po1
security-level 0
!
interface Port-channel1.500
vlan 500
bridge-group 250
nameif FCRMon-Current
security-level 50
!
interface Port-channel1.2501
vlan 2501
bridge-group 250
nameif FCRMon-Test
security-level 50
!
ftp mode passive
clock timezone WST 8
dns server-group DefaultDNS
domain-name x.local
same-security-traffic permit inter-interface
access-list SFR_REDIRECT extended permit ip any any
access-list global_access extended permit ip any any
pager lines 24
logging enable
logging asdm informational
mtu management 1500
mtu Po1 1500
mtu FCRMon-Current 1500
mtu FCRMon-Test 1500
no failover
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-792-152.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
access-group global_access global
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
http server enable
http 10.32.1.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh 10.32.1.0 255.255.255.0 management
ssh timeout 30
ssh key-exchange group dh-group1-sha1
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 10.32.1.254 source management
ssl cipher default low
ssl cipher tlsv1 low
ssl cipher tlsv1.1 low
ssl cipher tlsv1.2 low
ssl cipher dtlsv1 low
dynamic-access-policy-record DfltAccessPolicy
class-map SFR_REDIRECT
match access-list SFR_REDIRECT
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
description To SFR
class inspection_default
inspect dns migrated_dns_map_1
inspect esmtp
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect sip
inspect skinny
inspect sqlnet
inspect sunrpc
inspect tftp
inspect xdmcp
class SFR_REDIRECT
sfr fail-open
policy-map type inspect dns migrated_dns_map_2
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:2fd83b9b2128497f41bdd9e484c3714d
: end
- Labels:
-
NGIPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2019 12:45 AM - edited 01-24-2019 12:51 AM
your ASA code config look fine to me. now coming to firepower SFR config.
you have to define few things in parallel to make it inline work to generate the alerts. have you define the intrusion policy in ASDM for SFR and also get the option as drop and generate log the alert. also looking in your ACP your rule allow any any and the default rule is intrusion blanced security and connectivity check this link will help you to setup the box correctly in regards to SFR.
https://www.petenetlive.com/KB/Article/0001107
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2019 07:29 PM - edited 02-03-2019 07:48 PM
Thanks Sheraz(?)
I have looked at the link and (apart from it referring to an older release), it looks pretty much what I have implemented. I don't have file policies or any malware licences.
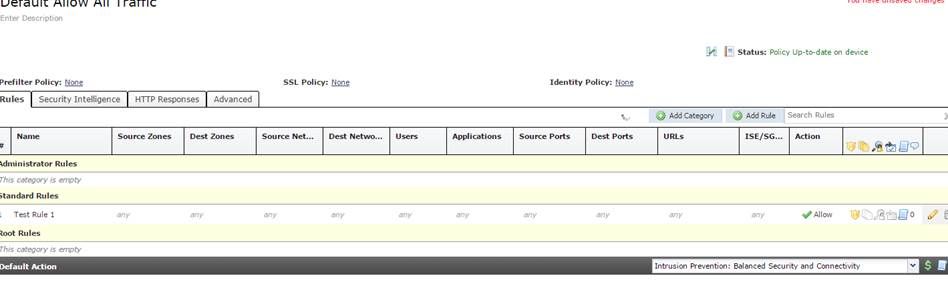
I have an intrusion policy called "Test". In this I have tried using the "Balanced" and "Maximum" base policies. In addition I have added rules to prevent Port Scanning (All options) as well as (for testing) ICMP replies. These I have set to "Drop and Generate Events". The Policy states to Drop when Inline (Yes).
I have created an Access Control Policy which uses "Test" as the Inspection Intrusion Policy and have set the Action to Allow.
I have tried using <any> for source and destination zones and networks, and have also tried setting specific values for these.
I am only using ASDM and don't have the Firepower manager if that makes any difference to anything at all.
When testing, ICMP replies are successfully being dropped by FirePower - yay - and I have seen some intrusion drops at times so the policies do seem to be working sort of.
My issue, however, is that most port scans and intrustion attempts generated by NMAP seem to successfully pass.
Perhaps I don't understand how Firepower reacts to NMAP scans and maybe I don't understand port scanning in general, but in my mind I should not be able to successfully determine through NMAP which ports are open on an end device. I can maybe understand if a few packets get through before the IPS works out that a scan is in progress, but when I try using NAMP -sV <end device> every open port on the end device is reported as open. And when using some the NMAP vulnerability and brute-force scripts, these seem to get through successfully.
Interestingly, none of these attempts (except the ICMP replies) seem to get logged in the Real Time Event Log under "connection" or "Intrusion", but is shown in the ASA traffic log (possibly because they are not set to generate an event?). I do get a lot of UDP traffic for multicast addresses logged in the "connection" page. This is mostly IGMP Client traffic. My access-list for defining traffic to be passed to the SFR is a basic permit ip any any.
If anybody can make any sense of this or would like to enlighten me as to why this might be or wish to debunk anything, please feel free.
Thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide