- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Firepower is not dropping packets. How to enable rules to generate events
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 03:03 AM - edited 02-21-2020 08:19 AM
Hello community
I am trying to generate some events in order to monitor my environment, but I am facing some issues.
I want to drop connections which use "public" or "private" community on snmp gets, but I am being not successfull.
I would appreciate some help.
I am trying to establish a connection to a switch/router using "public" community. I get no answer because that community is not configured, but I'd like to drop that try using firepower resources.
I attach my config.
It seems that the connection crosses the FW:
Oct 03 2018 08:53:07: %ASA-6-302015: Built inbound UDP connection 181208 for OUTSIDE:10.3.51.97/54829 (10.3.51.97/54829) to INSIDE:10.1.51.1/161 (10.1.51.1/161)
And is being inspected:
ASA-CDS-1# sho conn | in 10.1.51.1
UDP OUTSIDE 10.3.51.97:54829 INSIDE 10.1.51.1:161, idle 0:01:19, bytes 44, flags X
UDP OUTSIDE 10.3.51.97:54828 INSIDE 10.1.51.1:161, idle 0:01:37, bytes 44, flags X
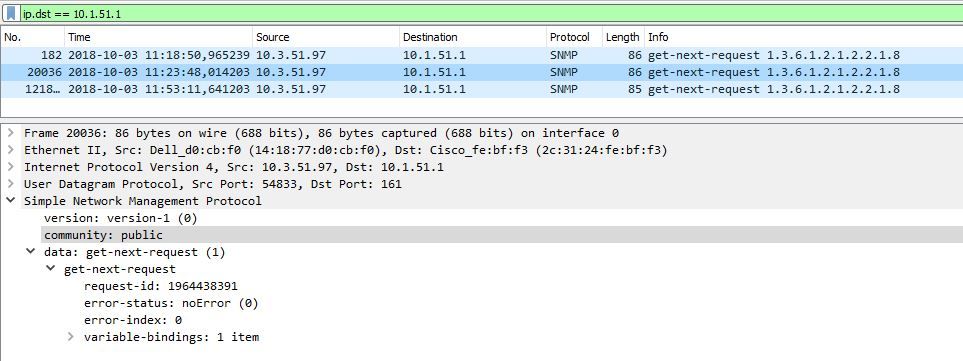
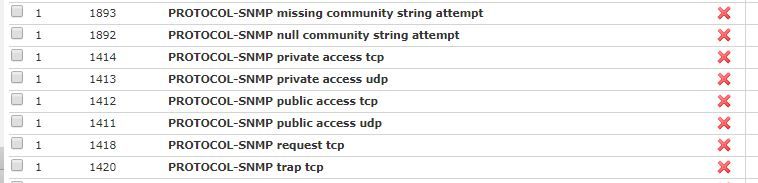
I am using community "public" to make the request:
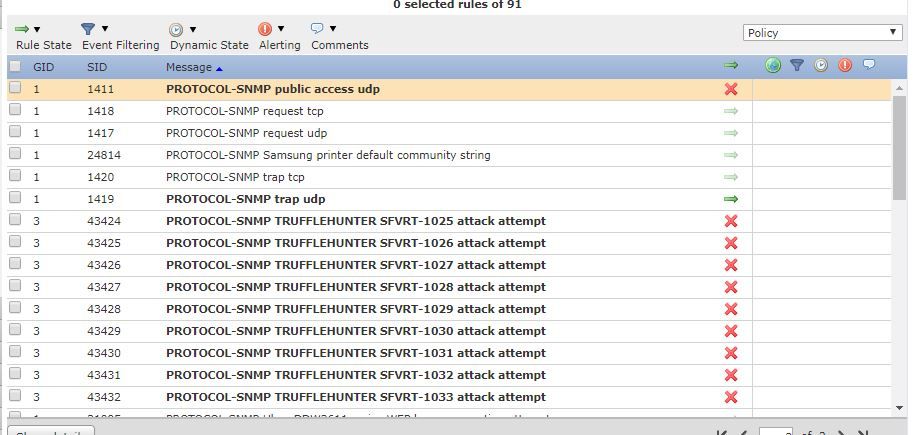
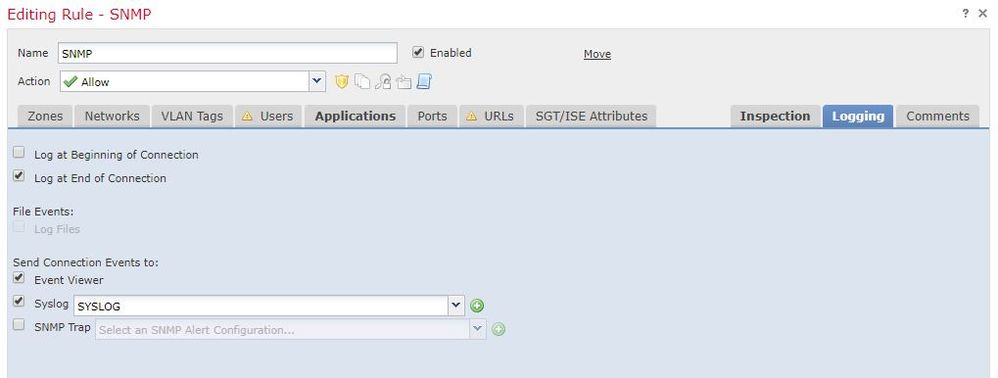
I enabled the rule to generate the event:
I commited the config and deployed to the devices.
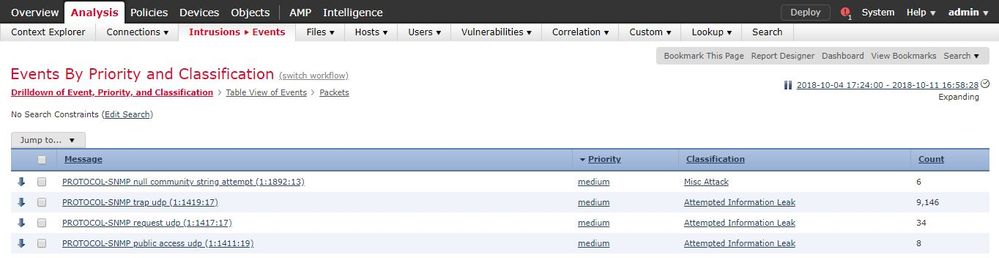
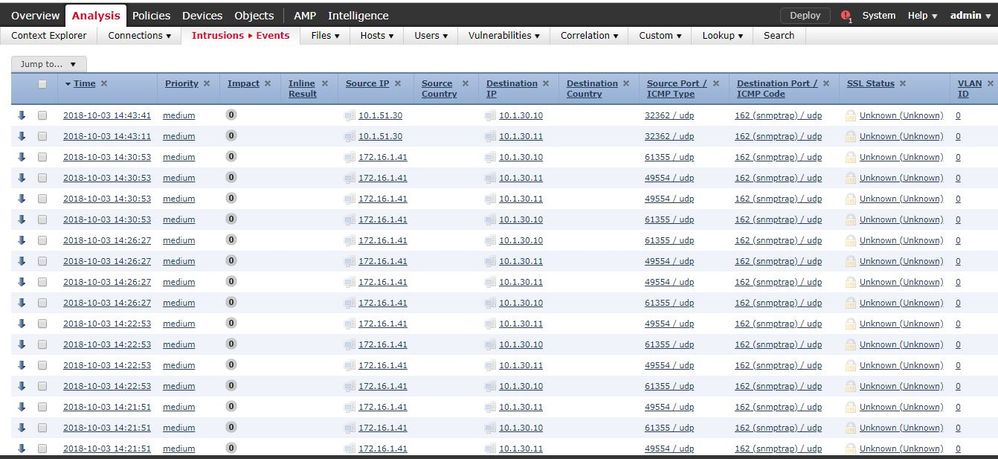
My problem is that it seems that this is not generating intrussion events.
Enabling another rules (icmp echo reply) I can see those events.
Should I apply anything else?
Is this rule made for this goal?
Solved! Go to Solution.
- Labels:
-
IPS and IDS
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 08:26 AM
Hello
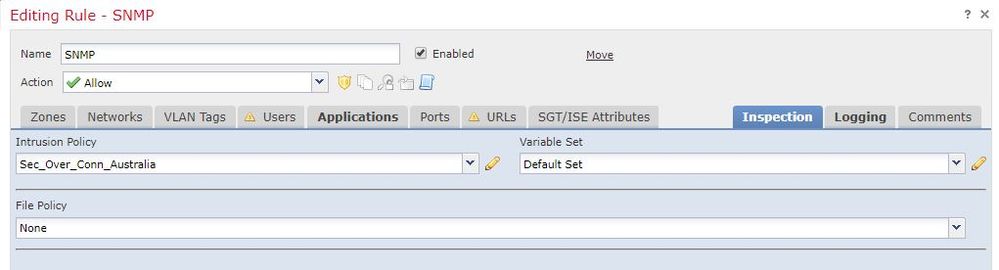
I could fix this, I will share my config in order to help someone.
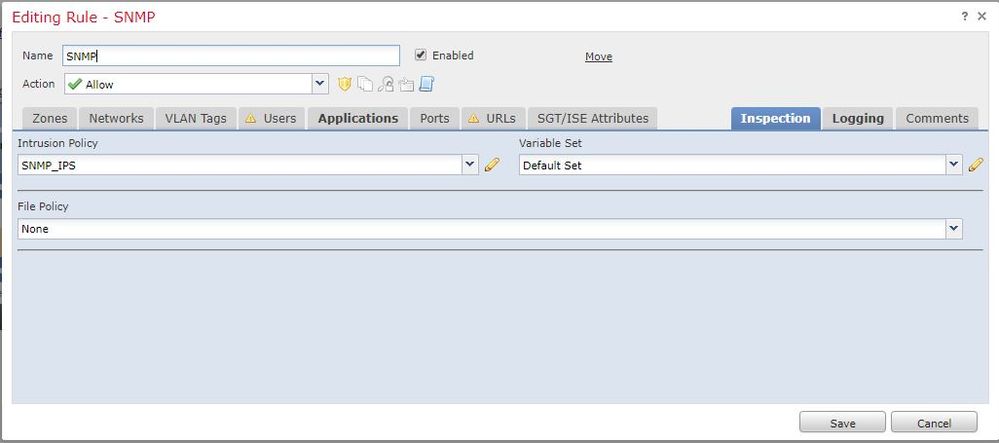
It's important to apply the Intrusion Policy on the access rule, because if traffic matches, it does not apply the default IPS policy.
Oh, and I had to reload the device too!!!!
And rememember to enable the rule, (maybe) it is not enabled by default.
Here they are:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 04:25 AM
Is that IPS rule in your deployed Intrusion policy?
If so, does the policy (or rule with that policy associated that's otherwise allowing the traffic) have "log at beginning of connection" selected?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 08:17 AM
Hello Marvin
Thank you for your help.
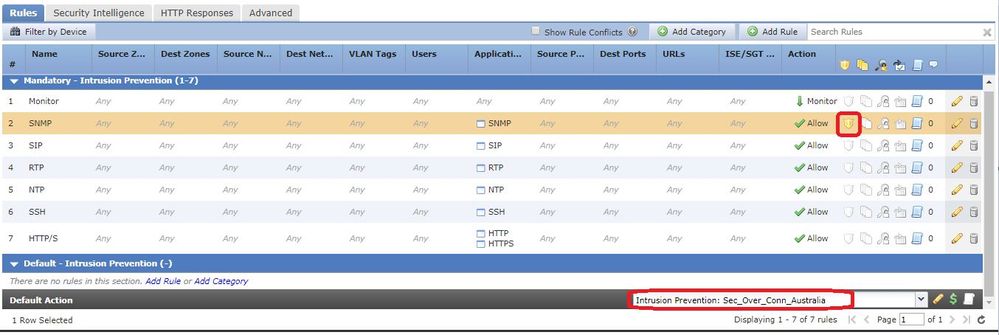
I have applied as "default Action" and inside access rule too.
This is the config:
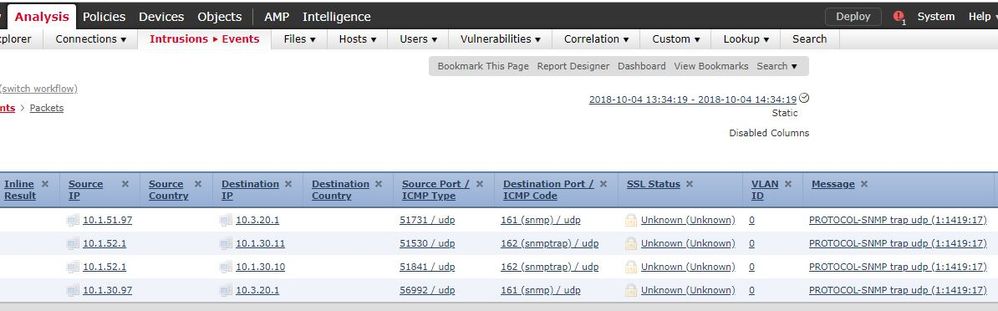
I enabled snmp traps too, and I can see those events.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 08:26 AM
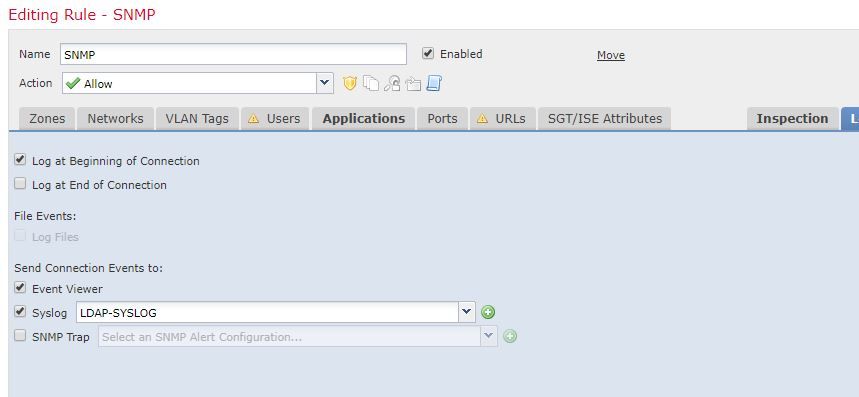
Try "Log at Beginning of Connection".
A udp flow will never have a FIN packet and thus won't signal the connection is ended.
Also, when you change the rule to block you must log at beginning to generate events since there won't be a FIN no matter what protocol is being used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2018 08:39 AM
Hello
I tried to detect those events enabling "Log at beggining..." but it does not detect them.
It shows snmp request or traps, but I am not able to drop a request which uses community "public".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 08:26 AM
Hello
I could fix this, I will share my config in order to help someone.
It's important to apply the Intrusion Policy on the access rule, because if traffic matches, it does not apply the default IPS policy.
Oh, and I had to reload the device too!!!!
And rememember to enable the rule, (maybe) it is not enabled by default.
Here they are:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 09:46 AM
Thanks for sharing your solution! It helps the community as a whole.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide