- Cisco Community
- Technology and Support
- Security
- Network Security
- FirePower publish internal webserver
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 02:16 AM - edited 03-12-2019 06:50 AM
Hi all,
I am new to FirePower, and now migrating ASA 5520 to FirePower 2110 (FTD 6.2.2).
I have finished initial setup of FirePower 2110 by FirePower Device Manager (FDM), specified the outside interface with 113.x.x.2/24, inside interface with 192.168.1.2 for example.
We have 64 public IP addresses.
I am going to publish internal webserver to internet by FDM.
Followed the cisco document to create Providing Access to an Inside Web Server (Static Auto NAT).
Where HKCitrixIT01Internal is the internal address 192.168.1.5 for example. And HKCitrixIT01Ext is the public address 113.x.x.5 for example.
I can't find reference about the Access Control rule for the web server publishing, so simply create a Access Control rule to allow any service.
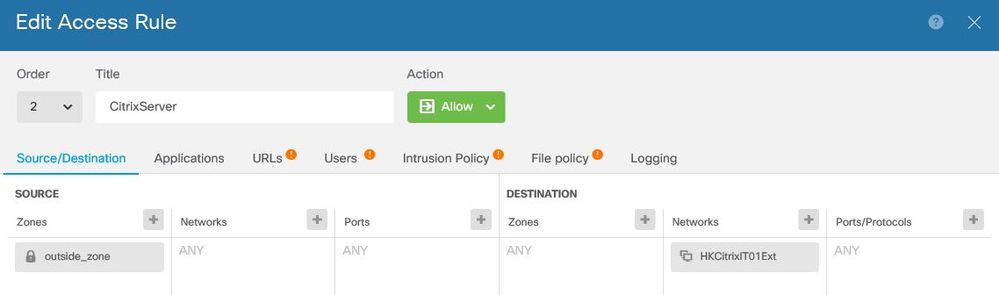
I can ping the outside interface publish IP 113.x.x.2 from internet, but ping to the 113.x.x.5 is failed.
And I check the Policies hit from Monitoring page, hit is zero .....
Any advise?
Thanks.
Notmen
Solved! Go to Solution.
- Labels:
-
NGIPS
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 07:45 AM
Hello Roy,
I ran into a similar issue when I was first using FDM. I think the issue that I ran into is that if you accept the default NAT policies configured when you first load FDM, the (any,outside) PAT statement has precedence over the other policies.
Edit this policy and change the source interface to inside (Or whatever the nameif of your segment is).
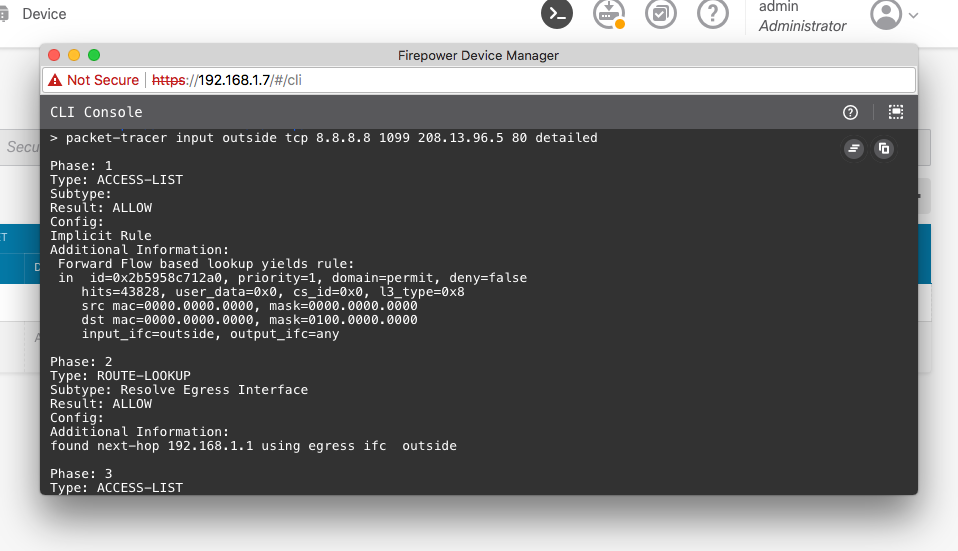
Try a packet tracer to your internal server from an internet address before and after your change and you should see a change in the behavior of your NAT processing in the packet-tracer output.
-A
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 04:15 PM
Change the Access rule destination network to HKCitrixIT01Internal. The Firepower (and ASA) Access rules should reference the internal server ip address.
Access rules always use the real IP addresses when determining an access rule match, even if you configure NAT. For example, if you configure NAT for an inside server, 10.1.1.5, so that it has a publicly routable IP address on the outside, 209.165.201.5, then the access rule to allow the outside traffic to access the inside server needs to reference the server’s real IP address (10.1.1.5), and not the mapped address (209.165.201.5).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 01:10 AM - edited 07-25-2018 01:10 AM
Dear Rahul,
Tried the destination network to HKCitrixIT01Internal but no luck.
Also changed the destination zone to inside_zone, no luck.
The Policy hit still keep zero. Seems no packet arrive the outside interface?
Is ping allowed by default? I can ping the outside internet IP 113.x.x.2 only.
Thanks,
Notmen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 07:45 AM
Hello Roy,
I ran into a similar issue when I was first using FDM. I think the issue that I ran into is that if you accept the default NAT policies configured when you first load FDM, the (any,outside) PAT statement has precedence over the other policies.
Edit this policy and change the source interface to inside (Or whatever the nameif of your segment is).
Try a packet tracer to your internal server from an internet address before and after your change and you should see a change in the behavior of your NAT processing in the packet-tracer output.

-A
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 05:43 PM
Dear Aaron,
Thank You very much!! You save my days!
It should be very helpful for other newbies to FirePower device.
BTW, your FDM interface is more advanced to mine. What is your FTD version?
Regards,
Roy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2018 06:39 AM
Whoops, sorry I think that screen shot was from the 6.3 beta.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2019 01:46 AM
Hi Roy Lee,
Can you share the Nat configuration you have done on FTD.
Thanks in advance
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


