- Cisco Community
- Technology and Support
- Security
- Network Security
- Flickr uploading tool via ISA2000
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Flickr uploading tool via ISA2000
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2011 06:33 AM - edited 03-11-2019 12:31 PM
Strange issue this,
I have a flickr upload tool, when using direct through our ASA5510, upalds are fine.
The problem is when the request comes via our proxy using ISA2000 it never works (my pc > proxy > asa). Watching the logs, the destination port seems to go in a loop and increment by 1
Here's a screenshot.
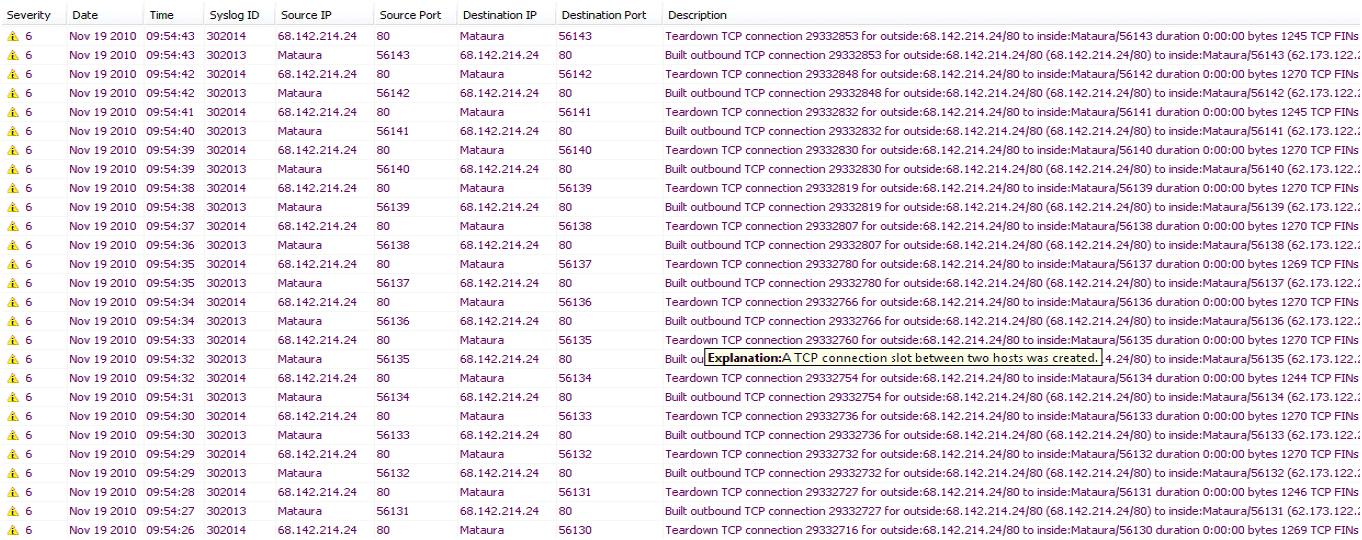
Any ideas?
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2011 09:02 AM
As you can see there is still no reference to 68.142.x.x (yet I can see it in the logging).
Both Mataura (my PC) and Makassar (ISA) are in the full access group to the Internet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2011 01:14 AM
Anys ideas then?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2011 02:39 AM
Ok, I did another Packet Capture, for the ingress I selected 'Inside' and set the Source to the ISA Server IP and Host to the Destination IP of 68.142.214.24
For the Egress I selected 'Outside', the Source as 68.142.214.24 and the Destination as the ISA Server IP and received this for the 'Get Capture' but it only populated the Ingress
518 packets captured
1: 10:31:05.756918 10.0.0.27.7517 > 68.142.214.24.80: S 391741528:391741528(0) win 65535
2: 10:31:05.903243 68.142.214.24.80 > 10.0.0.27.7517: S 3661029724:3661029724(0) ack 391741529 win 5840
3: 10:31:05.903838 10.0.0.27.7517 > 68.142.214.24.80: . ack 3661029725 win 65535
4: 10:31:05.903929 10.0.0.27.7517 > 68.142.214.24.80: P 391741529:391742248(719) ack 3661029725 win 65535
5: 10:31:06.041288 68.142.214.24.80 > 10.0.0.27.7517: . ack 391742248 win 7190
6: 10:31:06.068111 68.142.214.24.80 > 10.0.0.27.7517: P 3661029725:3661030271(546) ack 391742248 win 7190
7: 10:31:06.068142 68.142.214.24.80 > 10.0.0.27.7517: F 3661030271:3661030271(0) ack 391742248 win 7190
8: 10:31:06.068752 10.0.0.27.7517 > 68.142.214.24.80: . ack 3661030272 win 64989
9: 10:31:06.068798 10.0.0.27.7517 > 68.142.214.24.80: R 391742248:391742248(0) ack 3661030272 win 0
10: 10:31:07.069957 10.0.0.27.7518 > 68.142.214.24.80: S 4189409753:4189409753(0) win 65535
11: 10:31:07.195760 68.142.214.24.80 > 10.0.0.27.7518: S 1489261078:1489261078(0) ack 4189409754 win 5840
12: 10:31:07.196202 10.0.0.27.7518 > 68.142.214.24.80: . ack 1489261079 win 65535
13: 10:31:07.196278 10.0.0.27.7518 > 68.142.214.24.80: P 4189409754:4189410473(719) ack 1489261079 win 65535
14: 10:31:07.323072 68.142.214.24.80 > 10.0.0.27.7518: . ack 4189410473 win 7190
15: 10:31:07.363506 68.142.214.24.80 > 10.0.0.27.7518: P 1489261079:1489261624(545) ack 4189410473 win 7190
16: 10:31:07.363552 68.142.214.24.80 > 10.0.0.27.7518: F 1489261624:1489261624(0) ack 4189410473 win 7190
17: 10:31:07.364132 10.0.0.27.7518 > 68.142.214.24.80: . ack 1489261625 win 64990
18: 10:31:07.364193 10.0.0.27.7518 > 68.142.214.24.80: R 4189410473:4189410473(0) ack 1489261625 win 0
19: 10:31:08.363048 10.0.0.27.7519 > 68.142.214.24.80: S 256218219:256218219(0) win 65535
20: 10:31:08.509815 68.142.214.24.80 > 10.0.0.27.7519: S 2460791939:2460791939(0) ack 256218220 win 5840
21: 10:31:08.510242 10.0.0.27.7519 > 68.142.214.24.80: . ack 2460791940 win 65535
22: 10:31:08.510319 10.0.0.27.7519 > 68.142.214.24.80: P 256218220:256218939(719) ack 2460791940 win 65535
23: 10:31:08.658245 68.142.214.24.80 > 10.0.0.27.7519: . ack 256218939 win 7190
24: 10:31:08.686350 68.142.214.24.80 > 10.0.0.27.7519: P 2460791940:2460792510(570) ack 256218939 win 7190
25: 10:31:08.686396 68.142.214.24.80 > 10.0.0.27.7519: F 2460792510:2460792510(0) ack 256218939 win 7190
26: 10:31:08.686960 10.0.0.27.7519 > 68.142.214.24.80: . ack 2460792511 win 64965
27: 10:31:08.687037 10.0.0.27.7519 > 68.142.214.24.80: R 256218939:256218939(0) ack 2460792511 win 0
28: 10:31:09.691233 10.0.0.27.7522 > 68.142.214.24.80: S 2539672277:2539672277(0) win 65535
29: 10:31:09.827517 68.142.214.24.80 > 10.0.0.27.7522: S 2839919120:2839919120(0) ack 2539672278 win 5840
30: 10:31:09.827944 10.0.0.27.7522 > 68.142.214.24.80: . ack 2839919121 win 65535
31: 10:31:09.828021 10.0.0.27.7522 > 68.142.214.24.80: P 2539672278:2539672997(719) ack 2839919121 win 65535
32: 10:31:09.965404 68.142.214.24.80 > 10.0.0.27.7522: . ack 2539672997 win 7190
33: 10:31:10.001998 68.142.214.24.80 > 10.0.0.27.7522: P 2839919121:2839919667(546) ack 2539672997 win 7190
34: 10:31:10.002029 68.142.214.24.80 > 10.0.0.27.7522: F 2839919667:2839919667(0) ack 2539672997 win 7190
35: 10:31:10.002609 10.0.0.27.7522 > 68.142.214.24.80: . ack 2839919668 win 64989
36: 10:31:10.002670 10.0.0.27.7522 > 68.142.214.24.80: R 2539672997:2539672997(0) ack 2839919668 win 0
37: 10:31:10.999109 10.0.0.27.7523 > 68.142.214.24.80: S 1308149304:1308149304(0) win 65535
38: 10:31:11.125115 68.142.214.24.80 > 10.0.0.27.7523: S 557634201:557634201(0) ack 1308149305 win 5840
39: 10:31:11.125542 10.0.0.27.7523 > 68.142.214.24.80: . ack 557634202 win 65535
40: 10:31:11.125619 10.0.0.27.7523 > 68.142.214.24.80: P 1308149305:1308150024(719) ack 557634202 win 65535
41: 10:31:11.252718 68.142.214.24.80 > 10.0.0.27.7523: . ack 1308150024 win 7190
42: 10:31:11.281891 68.142.214.24.80 > 10.0.0.27.7523: P 557634202:557634772(570) ack 1308150024 win 7190
43: 10:31:11.281922 68.142.214.24.80 > 10.0.0.27.7523: F 557634772:557634772(0) ack 1308150024 win 7190
44: 10:31:11.282547 10.0.0.27.7523 > 68.142.214.24.80: . ack 557634773 win 64965
45: 10:31:11.282608 10.0.0.27.7523 > 68.142.214.24.80: R 1308150024:1308150024(0) ack 557634773 win 0
46: 10:31:12.278702 10.0.0.27.7524 > 68.142.214.24.80: S 1254110367:1254110367(0) win 65535
47: 10:31:12.425164 68.142.214.24.80 > 10.0.0.27.7524: S 2415734454:2415734454(0) ack 1254110368 win 5840
48: 10:31:12.425652 10.0.0.27.7524 > 68.142.214.24.80: . ack 2415734455 win 65535
49: 10:31:12.425728 10.0.0.27.7524 > 68.142.214.24.80: P 1254110368:1254111087(719) ack 2415734455 win 65535
50: 10:31:12.574112 68.142.214.24.80 > 10.0.0.27.7524: . ack 1254111087 win 7190
51: 10:31:12.603102 68.142.214.24.80 > 10.0.0.27.7524: P 2415734455:2415735025(570) ack 1254111087 win 7190
52: 10:31:12.603148 68.142.214.24.80 > 10.0.0.27.7524: F 2415735025:2415735025(0) ack 1254111087 win 7190
53: 10:31:12.603713 10.0.0.27.7524 > 68.142.214.24.80: . ack 2415735026 win 64965
54: 10:31:12.603774 10.0.0.27.7524 > 68.142.214.24.80: R 1254111087:1254111087(0) ack 2415735026 win 0
55: 10:31:13.615980 10.0.0.27.7525 > 68.142.214.24.80: S 221106100:221106100(0) win 65535
56: 10:31:13.745719 68.142.214.24.80 > 10.0.0.27.7525: S 945200089:945200089(0) ack 221106101 win 5840
57: 10:31:13.746146 10.0.0.27.7525 > 68.142.214.24.80: . ack 945200090 win 65535
58: 10:31:13.746223 10.0.0.27.7525 > 68.142.214.24.80: P 221106101:221106820(719) ack 945200090 win 65535
59: 10:31:13.877884 68.142.214.24.80 > 10.0.0.27.7525: . ack 221106820 win 7190
60: 10:31:13.913481 68.142.214.24.80 > 10.0.0.27.7525: P 945200090:945200635(545) ack 221106820 win 7190
I'd really like to get this resolved so would appreciate further assistance please.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2011 05:23 AM
Try with this capture and see if you are able to get any outputs:
access-list capin permit ip any host 68.142.214.24
access-list capin permit ip host 68.142.214.24 any
capture capin access-list capin pack 1520 interface inside
access-list capout permit ip any host 68.142.214.24
access-list capout permit ip host 68.142.214.24 any
capture capout access-list capout pack 1520 interface outside
capture capasp asp type all
If you see ooutput on the inside and the outside get also the ASP drop one so we can take a look.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2011 07:11 AM
Sorry, I don't understand. Are they commands I need to type in the command line interface?
What do you mean by 'get also the ASP drop one'
Also I'm still not convinced by the port number increase when the packets come from the ISA Server since I do not see this behaviour when it is bypassed
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2011 04:30 AM
Javier,
Ok, scrap the idea, this is definately an issue with ISA 2000
I've found another solution, but I need to be able to add all my domain computers into a group (these do not have static IP's)
Is there a way to create a group (ip range) so I can add it to another group to allow full internet access (i already have a full internet access group)
Thanks,
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2011 04:30 PM
You can define a third interface and do not crete an access list to allow full access to the outside. Here is a small example of how to enable a DMZ interface on a FastEthernet0/2.
interface FastEthernet0/2
no shutdown
nameif DMZ
security 50
ip address x.x.x.x 255.255.255.0
nat (dmz) 1 0 0
global (outside) 1 interface ******** if not already there
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
