- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FTD block traffic in same VLAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2018 05:08 AM - edited 02-21-2020 07:40 AM
I have Ftd but still in test environment as we have try to get it on production two times but it fail because it blocks the traffic in the same vlan i know its wired but that what happened the hosted in same vlan is blocked a cant even ping its always say ping translate fail . I have upgraded to 6.2.3 and the same issues exist ..
any help to solve it
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2018 02:52 AM
it was miss config in nat command that turn the Device as proxy arp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2018 06:23 AM - edited 04-26-2018 06:24 AM
Unlike with classic ASA software, Firepower Threat Defense by default allows same-security traffic both inter- and intra-interface.
Can you share screenshots of your access control policy and interface settings? you might also use packet-tracer to check what's happening with a test traffic flow.
Also, architecturally, why would traffic within a VLAN even attempt to transit the FTD appliance? Normally a host would arp for the destination address and, finding it, send the traffic directly to the destination MAC address and not use any gateway or network-based firewall or IPS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2018 07:06 AM
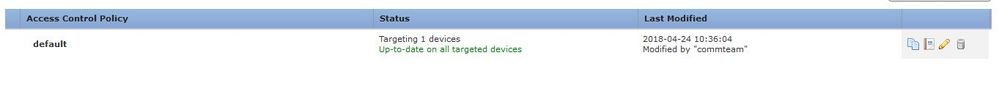
i know its wired that its block traffic in L2 but that what really happen .
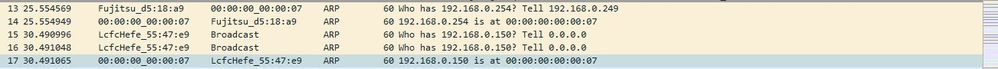
there is the screen shot and the packet tracer output y will see it drooped
and i have capture the L2 traffic y will see what happen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2018 07:18 AM
Can you share cli packet-tracer output?
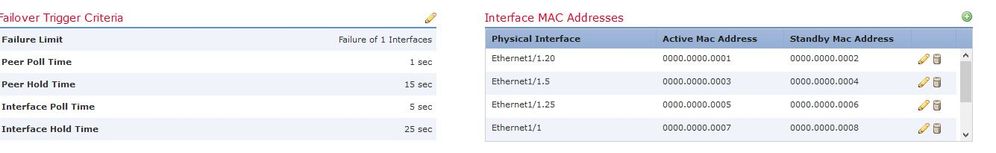
Alos it looks like you are using custom MAC addresses all beginning with 0000.0000.000x. I wonder if this is causing any problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2018 07:52 AM
> packet-tracer input Core-Vlan tcp 192.168.0.200 111 192.168.0.201 11
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 192.168.0.201 using egress ifc Core-Vlan
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: DROP
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced deny ip any any rule-id 268434432 event-log flow-start
access-list CSM_FW_ACL_ remark rule-id 268434432: ACCESS POLICY: default - Default
access-list CSM_FW_ACL_ remark rule-id 268434432: L4 RULE: DEFAULT ACTION RULE
Additional Information:
Result:
input-interface: Core-Vlan
input-status: up
input-line-status: up
output-interface: Core-Vlan
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2018 07:54 AM
how custom MAC addresses make problem ?
its not duplicate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2018 08:00 AM
The custom MAC addresses aren't necessarily a problem. But a basic rule is when there is a problem, we look for unusual settings.
Your packet-tracer shows the traffic being denied due to an ACL. Have a look at your access control and prefilter policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2018 02:15 AM
the question now why FTD act in L2 instead of Switchs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2018 06:16 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2018 08:02 AM
Your FTD device can also be setup to do integrated routing and bridging, thus effectively acting as a switch. If so, you need a policy to permit inter-interface traffic within a given BVI group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2018 03:32 AM
and how can i disable it .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2018 03:52 AM
Have a look at the interfaces setup in FMC.
If there is integrated routing and bridging, there will be bridge groups and switched interfaces configured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2018 01:55 PM
but i ll try to remove it i use the interfaces and see if still block traffic or not
i ll check and feed you back .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 12:59 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 06:06 AM
Well you seem to have two Cisco devices configured with the IP address 192.168.0.9.
00:24:51 Cisco Systems, Inc
38:90:A5 Cisco Systems, Inc
You've not shared sufficient details of your setup to let us provide any further insight.
If this is under support you might just open a TAC case and the engineer can work with you in real time. If it's just a lab then why not share the full configuration?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide