- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: %FTD Duplicate TCP SYN from inside to outside with different init
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
%FTD Duplicate TCP SYN from inside to outside with different initial
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2024 08:32 AM - edited 04-05-2024 08:40 AM
Hello all
I'm receiving hundreds of warning messages i am getting in our syslog from our Cisco ASA 5516-x. The warning message is:
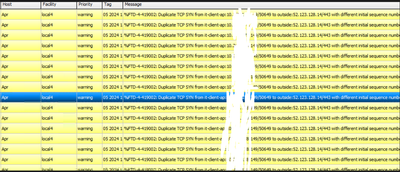
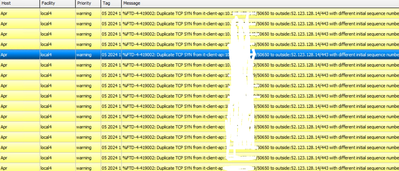
Message: %FTD-4-419002: Duplicate TCP SYN from it-client-ap:10.245.xx.1x/54557 to outside:5x.1xx.1x9.x/443 with different initial sequence number
Message: %FTD-4-419002: Duplicate TCP SYN from it-client-ap:10.245.xx.1x/50650 to outside:5x.1xx.1x9.x/443 with different initial sequence number
Message: %FTD-4-419002: Duplicate TCP SYN from it-client-ap:10.245.xx.1x/50650 to outside:5x.1xx.1x9.x/443 with different initial sequence number
This messages appears during working hours when users connected to WIFI office VLAN using the inside ASA port (it-client-ap) and maybe on other vlans like LAN but what im facing now is big numbers of warning massages coming through that interface above
im not sure if this is kind of flooding attack of kid of DoS attacks but how can i resolve this issue and what kind of show commands that i can use to troubleshoot and try to solve ,
Note: Also i have no problems with any services on my private network, like internet connection and VPN S2S works fine, though I'm still concerned about what's going on because there's large amount of those logs per day
Current ASA version is : Cisco ASA5516-X Threat Defense (75) Version 7.0.1 (Build 84)
Also no routing configured on ASA and ASA is directly connected to L3 core switch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2024 08:41 AM
check is there is any asymmetric in routing
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2024 08:44 AM
Can you please share with me more details and how to check !?
No routing configured on the ASA its just
ISP---ASA---L3 CORE SWITCH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2024 10:24 AM - edited 04-06-2024 11:17 AM
It clear there is no need routing all subnet direct connect (except defualt route for internet it needed...)
Check this link
It can DDoS so shun the IP or add ACL drop connect from this IP.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2024 05:02 AM
Can show me how to shun the IP addresses which appears on logsys and what does shun do to that ip , is it blocking that ip totally from accessing the network or just block the huge traffic coming from that device ! because i have more devices with same massages coming from them!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2024 11:01 AM
@amralrazzaz if this traffic is from source inside to outside, then a device on the inside of the network is either spoofing traffic or misbehaving.
Error Message %FTD-4-419002: Received duplicate TCP SYN from in_interface :src_address /src_port to out_interface :dest_address /dest_port with different initial sequence number.
Explanation A duplicate TCP SYN was received during the three-way-handshake that has a different initial sequence number from the SYN that opened the embryonic connection. This may indicate that SYNs are being spoofed. This message occurs in Release 7.0.4.1 and later.
Is it just the one device (10.245.xx.1x) or multiple devices generating these alerts?
I would physically find the device(s) that is generating these events and see if its a rogue device or there is an issue with it and if needs be remove it from the network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2024 11:28 AM
Dear its coming from multiple devices , i thin whenever there is client connected to wifi office it keep sending these kind of waring massages from them to our syslog system not only one device and once all these client disconnected from the wifi office network this massage disappeared
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide