- Cisco Community
- Technology and Support
- Security
- Network Security
- FTD (firewall) Blocked or blacklisted
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2021 10:16 AM
Hi all,
I have configured an inbound access for exchange online to allow communication with internal VIP on ports tcp-25 and 442. I have the NAT rule in place and the policy to allow the traffic. However, I am seeing the traffic being dropped by SNORT in phase 36. I did some research nut couldn't find an answer on how to resolve the issue. Please keep in mind that I am new to CISCO FTDs. I have attached the NAT configs and following is the packet tracer o/p from the firewall. Thanks a lot in advance for your help!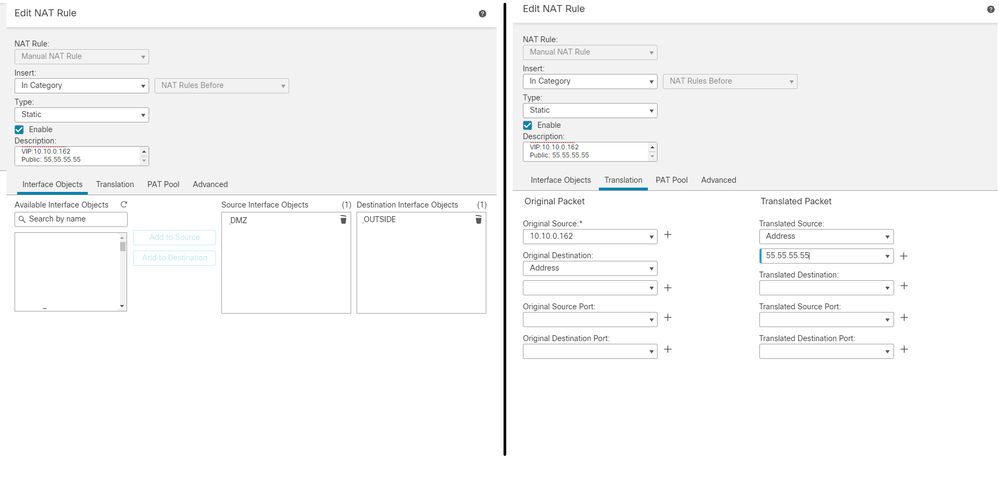
10: 04:58:36.493321 192.241.199.18.48195 > 55.55.55.55.443: S 3429135431:3429135431(0) win 65535
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (DMZ,OUTSIDE) after-auto source static 10.10.0.162 55.55.55.55 description ExchangeHybri VIP NAT VIP:10.10.0.162 Public: 55.55.55.55
Additional Information:
NAT divert to egress interface DMZ(vrfid:0)
Untranslate 55.55.55.55/443 to 10.10.0.162/443
Phase: 4
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip ifc OUTSIDE any any rule-id 268453888
access-list CSM_FW_ACL_ remark rule-id 268453888: ACCESS POLICY: access_control_list_2130-FTD-1 - Mandatory
access-list CSM_FW_ACL_ remark rule-id 268453888: L7 RULE: From_Black_Listed_Countries
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 5
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 6
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (DMZ,OUTSIDE) after-auto source static 10.10.0.162 55.55.55.55 description ExchangeHybri VIP NAT VIP:10.10.0.162 Public: 55.55.55.55
Additional Information:
Static translate 192.241.199.18/48195 to 192.241.199.18/48195
Phase: 7
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip ifc OUTSIDE any any rule-id 268453888
access-list CSM_FW_ACL_ remark rule-id 268453888: ACCESS POLICY: access_control_list_2130-FTD-1 - Mandatory
access-list CSM_FW_ACL_ remark rule-id 268453888: L7 RULE: From_Black_Listed_Countries
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 10
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 11
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (DMZ,OUTSIDE) after-auto source static 10.10.0.162 55.55.55.55 description ExchangeHybri VIP NAT VIP:10.10.0.162 Public: 55.55.55.55
Additional Information:
Static translate 192.241.199.18/48195 to 192.241.199.18/48195
Phase: 12
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 13
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 14
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip ifc OUTSIDE any any rule-id 268453888
access-list CSM_FW_ACL_ remark rule-id 268453888: ACCESS POLICY: access_control_list_2130-FTD-1 - Mandatory
access-list CSM_FW_ACL_ remark rule-id 268453888: L7 RULE: From_Black_Listed_Countries
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 15
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 16
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (DMZ,OUTSIDE) after-auto source static 10.10.0.162 55.55.55.55 description ExchangeHybri VIP NAT VIP:10.10.0.162 Public: 55.55.55.55
Additional Information:
Static translate 192.241.199.18/48195 to 192.241.199.18/48195
Phase: 17
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 18
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 19
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip ifc OUTSIDE any any rule-id 268453888
access-list CSM_FW_ACL_ remark rule-id 268453888: ACCESS POLICY: access_control_list_2130-FTD-1 - Mandatory
access-list CSM_FW_ACL_ remark rule-id 268453888: L7 RULE: From_Black_Listed_Countries
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 20
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 21
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (DMZ,OUTSIDE) after-auto source static 10.10.0.162 55.55.55.55 description ExchangeHybri VIP NAT VIP:10.10.0.162 Public: 55.55.55.55
Additional Information:
Static translate 192.241.199.18/48195 to 192.241.199.18/48195
Phase: 22
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 23
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 24
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip ifc OUTSIDE any any rule-id 268453888
access-list CSM_FW_ACL_ remark rule-id 268453888: ACCESS POLICY: access_control_list_2130-FTD-1 - Mandatory
access-list CSM_FW_ACL_ remark rule-id 268453888: L7 RULE: From_Black_Listed_Countries
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 25
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 26
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (DMZ,OUTSIDE) after-auto source static 10.10.0.162 55.55.55.55 description ExchangeHybri VIP NAT VIP:10.10.0.162 Public: 55.55.55.55
Additional Information:
Static translate 192.241.199.18/48195 to 192.241.199.18/48195
Phase: 27
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 28
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 29
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:
Phase: 30
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Phase: 31
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (DMZ,OUTSIDE) after-auto source static 10.10.0.162 55.55.55.55 description ExchangeHybri VIP NAT VIP:10.10.0.162 Public: 55.55.55.55
Additional Information:
Phase: 32
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 33
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 34
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 1860002021, packet dispatched to next module
Phase: 35
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 36
Type: SNORT
Subtype:
Result: DROP
Config:
Additional Information:
Snort Trace:
Packet: TCP, SYN, seq 3429135431
Session: new snort session
AppID: service unknown (0), application unknown (0)
Firewall: starting AC rule matching, zone 1 -> 3, geo 0 -> 0, vlan 0, sgt 0, src sgt type 0, dest_sgt_tag 0, dest sgt type 0, user 9999997, icmpType 0, icmpCode 0
Firewall: block rule, 'Default Action' , drop
Snort: processed decoder alerts or actions queue, drop
Snort id 6, NAP id 2, IPS id 0, Verdict BLACKLIST, Blocked by Firewall
Snort Verdict: (black-list) black list this flow
Result:
input-interface: OUTSIDE(vrfid:0)
input-status: up
input-line-status: up
output-interface: DMZ(vrfid:0)
output-status: up
output-line-status: up
Action: drop
Drop-reason: (firewall) Blocked or blacklisted by the firewall preprocessor, Drop-location: frame 0x000000aaae003f28 flow (NA)/NA
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2021 07:40 PM
This is blocked by your firewall rules. Its not matching any rule hence
getting blocked by default action. See this.
Firewall: block rule, 'Default Action' , drop
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2021 07:40 PM
This is blocked by your firewall rules. Its not matching any rule hence
getting blocked by default action. See this.
Firewall: block rule, 'Default Action' , drop
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2021 06:04 AM
Hi Mohammed,
Thanks for your reply. I actually labbed the design two days ago and yes you're right it was a missing private IP in the policy list, which is blocked by the default rule.
Thanks.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


