- Cisco Community
- Technology and Support
- Security
- Network Security
- FTD - IPSec failed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 03:22 AM
Hi everybody,
I have an FTD with FMC that must have a VPN tunnel IPSec with a router.
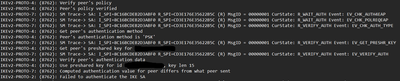
I have configured the FTD following all the instructions but I receive the message log error "Failed to authenticate the IKE SA".
Reading the debug messages I found this:
Both endpoints use the same PSK, maybe is something about the algorithms.
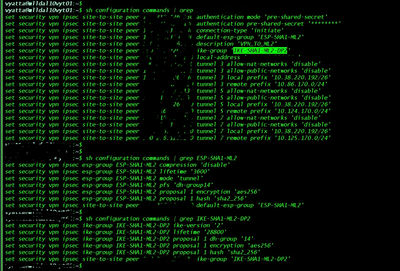
This is the remote peer config:
I've uploaded the debug logs too, please help me to find a solution.
Thanks for your help!!
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2023 03:23 AM - edited 03-29-2023 03:26 AM
@angelito_mas YES
The purpose of a NAT exemption rule when used with a VPN is to ensure traffic over the VPN is not translated. The original source and translated source are the same network and the original destination and translated destination are the same network.
In you scenario create an object for 10.86.170.0/24, this is the source network and another object for the destination network as 10.38.220.192/26. Repeat for the other internal networks. Then create the NAT exemption rules.
Only traffic from 10.86.170.0/24 to 10.38.220.192/26 will match this NAT exemption rule, traffic over the VPN will be routed using the real IP address. Traffic to the internet from these internal networks, which has a destination IP address of something other than 10.38.220.192/26 will not match this rule and match the existing Auto NAT and be translated behind the Firewall outside interface IP address.
Example:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 04:52 AM
@angelito_mas this is likely a PSK mismatch, double check the PSK and confirm the received peer's identity is matched correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 04:56 AM
How can I verify the peer's identity? This is my config:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 05:06 AM
@angelito_mas I assume you replaced the identity - IKEv2-PROTO-4: (5011): Use preshared key for id *remote* < I expect that was the IP address of the peer?
I suggest you and the peer replace your PSK, to be sure it's correct on both sides. Confirm no whitespace entered.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 05:12 AM - edited 03-13-2023 05:24 AM
one of Peer FTD or router is behind NATing device this make issue in identity,
you must config Peer and PSK with mapped IP not real IP.
also check for IKEv2
are you config remote identify address under ikev2 profile of router ?? this can solve issue if IP is NATing in some point between two Peer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 05:17 AM
Good suggestion, but...
IKEv2-PROTO-4: (5011): Checking NAT discovery
IKEv2-PROTO-4: (5011): NAT not found
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 05:27 AM
some times NAT-T is disable.
I only suggest for him to check this point.
thanks a lot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 05:30 AM
@MHM Cisco World Where I can check it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 06:06 AM
@angelito_mas nat-t is enabled as default and from the output of the debugs is looks like it is enabled.
To confirm, the id *remote* as per the debugs is the public IP address of the peer right?
Re-enter the PSK on both devices and confirm it is identical - on both sides.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 06:22 AM
as @Rob Ingram mention it enable by default
also I mention above
use correct IP in remote identity under IKEv2 profile of Router. did you check this point ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 07:18 AM
I can confirm you that the id *remote* as per the debugs is the public IP address of the peer and that the PSK on both devices is identical.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 03:44 PM
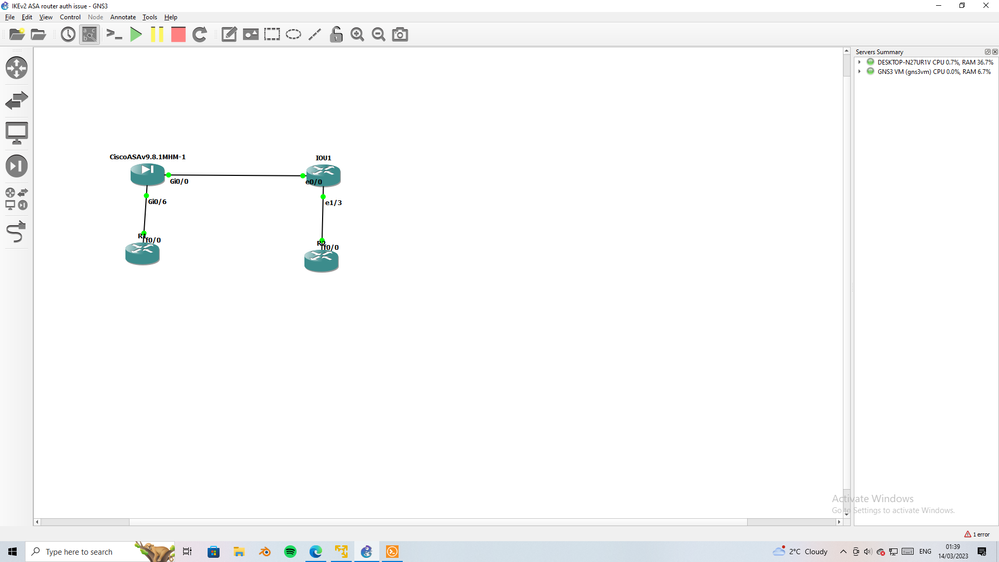
I run lab, to config IKEv2 between ASA and Router IOS,
I face same issue as you but
by check debug line by line I found issue
points to care in config :-
1- user address under ikev2 policy
2- use identity local address under profile
3- in proposal please match integrity with prf you use per-router and per-asa
4- transform set in router must not contain any AH, and in same time config hash in transform set and config same integrity in IKEv2 proposal in ASA
I do all and I success.
IOU1#show run
IOU1#show running-config
Building configuration...
Current configuration : 2744 bytes
!
! Last configuration change at 22:38:33 UTC Mon Mar 13 2023
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname IOU1
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
!
!
bsd-client server url https://cloudsso.cisco.com/as/token.oauth2
mmi polling-interval 60
--More--
*Mar 13 22:38:33.352: %SYS-5-CONFIG_I: Configured from console by console
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
!
!
!
!
no ip icmp rate-limit unreachable
!
!
!
!
!
!
!
!
!
!
!
!
no ip domain lookup
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
cts logging verbose
!
!
!
redundancy
!
!
ip tcp synwait-time 5
!
!
crypto ikev2 proposal mhm
encryption des
integrity md5
group 5
!
crypto ikev2 policy mhm
match address local 100.0.0.2
proposal mhm
!
crypto ikev2 keyring mhm
peer any
address 100.0.0.1
pre-shared-key local mhm
pre-shared-key remote mhm
!
!
!
crypto ikev2 profile mhm
match address local 100.0.0.2
match identity remote address 100.0.0.1 255.255.255.255
identity local address 100.0.0.2
authentication remote pre-share
authentication local pre-share
keyring local mhm
!
!
!
crypto ipsec transform-set mhm esp-des esp-md5-hmac
mode tunnel
!
!
!
crypto map mhm 10 ipsec-isakmp
set peer 100.0.0.1
set transform-set mhm
set pfs group5
set ikev2-profile mhm
match address 100
!
!
!
!
!
interface Ethernet0/0
ip address 100.0.0.2 255.255.255.0
crypto map mhm
!
interface Ethernet0/1
no ip address
shutdown
!
interface Ethernet0/2
no ip address
shutdown
!
interface Ethernet0/3
no ip address
shutdown
!
interface Ethernet1/0
no ip address
shutdown
!
interface Ethernet1/1
no ip address
shutdown
!
interface Ethernet1/2
no ip address
shutdown
!
interface Ethernet1/3
ip address 20.0.0.2 255.255.255.0
!
interface Serial2/0
no ip address
shutdown
serial restart-delay 0
!
interface Serial2/1
no ip address
shutdown
serial restart-delay 0
!
interface Serial2/2
no ip address
shutdown
serial restart-delay 0
!
interface Serial2/3
no ip address
shutdown
serial restart-delay 0
!
interface Serial3/0
no ip address
shutdown
serial restart-delay 0
!
interface Serial3/1
no ip address
shutdown
serial restart-delay 0
!
interface Serial3/2
no ip address
shutdown
serial restart-delay 0
!
interface Serial3/3
no ip address
shutdown
serial restart-delay 0
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 100.0.0.1
!
!
!
access-list 100 permit ip 20.0.0.0 0.0.0.255 10.0.0.0 0.0.0.255
!
control-plane
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
transport input none
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2023 01:46 AM
Hi guys,
finally we made it. It was the PRF algorithm that was not enabled on the other side..
We choose to use ikev1 to simplify the process.
By the way, now we have some routing problems. The protected networks do not talk.
From the FTD CLI i see the network advertised but i cannot reach it:
PCO-N-FWRA1# show route static
S* 0.0.0.0 0.0.0.0 [1/0] via x.x.x.x, WAN
S 10.0.0.0 255.0.0.0 [5/0] via 172.27.58.209, services_internet
V 10.38.220.192 255.255.255.192 connected by VPN (advertised), WAN
S 172.16.0.0 255.240.0.0 [1/0] via 172.27.58.225, dcs_internet
S 172.27.1.0 255.255.255.0 [1/0] via 172.27.58.225, dcs_internet
V 192.168.254.1 255.255.255.255 connected by VPN (advertised), WAN
V 192.168.254.2 255.255.255.255 connected by VPN (advertised), WAN
V 192.168.254.52 255.255.255.255 connected by VPN (advertised), WAN
I've already enabled the access policy.
Can you help me?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2023 01:50 AM
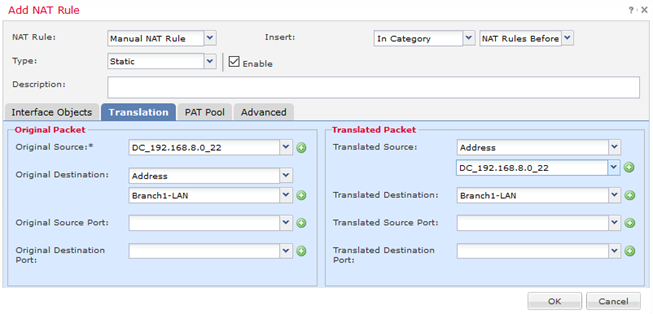
@angelito_mas Please run "show crypto ipsec sa" and provide the full output.
Do you have a NAT exemption rule to ensure the VPN traffic is not unintentially translated?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2023 01:57 AM
Here you are:
PCO-N-FWRA1# show crypto ipsec sa
interface: WAN
Crypto map tag: CSM_WAN_map, seq num: 1, local addr: 190.216.126.130
access-list CSM_IPSEC_ACL_2 extended permit ip 10.86.170.0 255.255.255.0 10.38.220.192 255.255.255.192
local ident (addr/mask/prot/port): (10.86.170.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.38.220.192/255.255.255.192/0/0)
current_peer: 150.238.239.218
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 190.216.126.130/0, remote crypto endpt.: 150.238.239.218/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: clear-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: C21F04A2
current inbound spi : 4D1402FD
inbound esp sas:
spi: 0x4D1402FD (1293157117)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv1, }
slot: 0, conn_id: 203, crypto-map: CSM_WAN_map
sa timing: remaining key lifetime (kB/sec): (4374000/2400)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0xC21F04A2 (3256812706)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv1, }
slot: 0, conn_id: 203, crypto-map: CSM_WAN_map
sa timing: remaining key lifetime (kB/sec): (4374000/2400)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: CSM_WAN_map, seq num: 1, local addr: 190.216.126.130
access-list CSM_IPSEC_ACL_2 extended permit ip 10.124.170.0 255.255.255.0 10.38.220.192 255.255.255.192
local ident (addr/mask/prot/port): (10.124.170.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.38.220.192/255.255.255.192/0/0)
current_peer: 150.238.239.218
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 190.216.126.130/0, remote crypto endpt.: 150.238.239.218/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: clear-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: CAA5EEE9
current inbound spi : C2A97AE0
inbound esp sas:
spi: 0xC2A97AE0 (3265886944)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv1, }
slot: 0, conn_id: 203, crypto-map: CSM_WAN_map
sa timing: remaining key lifetime (kB/sec): (4374000/2400)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0xCAA5EEE9 (3399872233)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv1, }
slot: 0, conn_id: 203, crypto-map: CSM_WAN_map
sa timing: remaining key lifetime (kB/sec): (4374000/2400)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: CSM_WAN_map, seq num: 1, local addr: 190.216.126.130
access-list CSM_IPSEC_ACL_2 extended permit ip 10.125.170.0 255.255.255.0 10.38.220.192 255.255.255.192
local ident (addr/mask/prot/port): (10.125.170.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.38.220.192/255.255.255.192/0/0)
current_peer: 150.238.239.218
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 190.216.126.130/0, remote crypto endpt.: 150.238.239.218/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: clear-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: C80A954D
current inbound spi : 4FE23246
inbound esp sas:
spi: 0x4FE23246 (1340224070)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv1, }
slot: 0, conn_id: 203, crypto-map: CSM_WAN_map
sa timing: remaining key lifetime (kB/sec): (4374000/2401)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0xC80A954D (3356136781)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv1, }
slot: 0, conn_id: 203, crypto-map: CSM_WAN_map
sa timing: remaining key lifetime (kB/sec): (4374000/2401)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide