- Cisco Community
- Technology and Support
- Security
- Network Security
- FTPserver in DMZ + Dual ISP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2010 04:46 AM - edited 03-11-2019 11:25 AM
Hi Guys,
I'm trying for the last 3 days to get FTP work in my DMZ. In fact the FTPserver itself works, because i can FTP from the inside to the DMZ. But from the Outside to the DMZ i don't get it working.
The situation:
See the network diagram for details.
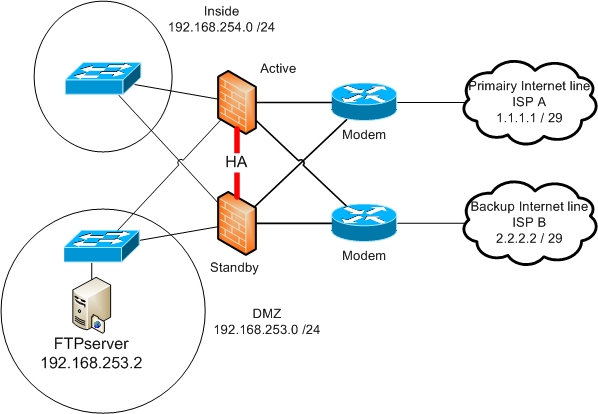
2x ASA5505 in Active/Standby
5 interfaces: Inside, Outside, Backup and DMZ, Managment
ISP A is tracked, if it goes down automaticly switchover to ISP B.
Two different public IP addresses: ISP A = 1.1.1.x / 29 ISP B = 2.2.2.x / 29. So with each ISP we have about 5 or 6 public IP addresses.
DMZ = 192.168.253.0 /24 DMZ interface = 192.168.253.1 FTT = 192.168.253.2
The problem:
The FTP server in the DMZ is not accessible from the internet. ASDM's Packet Tracer keeps dropping at the NAT rule.
From the DMZ to the outside everything is passing, according to Packet Tracer. Also from the Inside to the DMZ i can ftp.
Another question:
We have two different public IP ranges. Our customers reach the ftp by DNS name: ftp.company.com
How can i achive that the FTPserver is still accessible when our primary ISP fails, and the routing occurs via ISP B (= other public ip range). Something with DNS?
Below is the (sanetized) config (sensitive info is deleted):
ASA Version 7.2(4) ! hostname PK1-FW1 domain-name default.domain.invalid enable password 7eiKHCMaZZwOv/Ls encrypted passwd 2KFQnbNIdI.2KYOU encrypted names dns-guard ! interface Vlan1 description Connected to internal LAN nameif inside security-level 100 ip address 192.168.254.2 255.255.255.0 standby 192.168.254.3 ! interface Vlan2 description Connected to primary ISP nameif outside security-level 0 ip address 1.1.1.2 255.255.255.252 ! interface Vlan3 description Connected to backup ISP nameif backup security-level 0 ip address 2.2.2.2 255.255.255.248 ! interface Vlan4 description For management purposes only! nameif Management security-level 100 ip address 192.168.4.5 255.255.255.0 standby 192.168.4.6 management-only ! interface Vlan253 nameif DMZ security-level 50 ip address 192.168.253.1 255.255.255.0 ! interface Vlan255 description LAN Failover Interface ! interface Ethernet0/0 switchport access vlan 2 ! interface Ethernet0/1 switchport access vlan 3 ! interface Ethernet0/2 ! interface Ethernet0/3 switchport access vlan 253 ! interface Ethernet0/4 switchport access vlan 4 ! interface Ethernet0/5 switchport access vlan 255 ! interface Ethernet0/6 ! interface Ethernet0/7 ! ftp mode passive clock timezone CEST 1 clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00 dns domain-lookup outside dns server-group DefaultDNS domain-name default.domain.invalid object-group network Department_Vlans description Vlans per department object-group network Allowed_FTP description Clients/Departments allowed to use FTP object-group service Allowed_Protocols tcp description group of allowed protocols object-group protocol TCPUDP protocol-object udp protocol-object tcp object-group service DM_INLINE_TCP_1 tcp group-object Allowed_Protocols object-group service DM_INLINE_TCP_2 tcp port-object eq ftp port-object eq ftp-data object-group service Allow_SVN tcp-udp port-object eq 888 object-group service TCP_Allow_Filesharing_Inside-DMZ tcp port-object eq 135 port-object eq 445 port-object eq netbios-ssn object-group service UDP_Allow_Filesharing_Inside-DMZ udp port-object eq netbios-ns object-group service DM_INLINE_TCP_3 tcp port-object eq ftp port-object eq ftp-data object-group service Allow_FileSharing_FTP01 tcp-udp port-object eq 135 port-object eq 137 port-object eq 139 port-object eq 445 object-group service Allowed_FTP01_Protocols tcp port-object eq ftp port-object eq ftp-data port-object eq www port-object eq https port-object eq domain object-group service Allow_FTP tcp port-object eq ftp port-object eq ftp-data object-group network DM_INLINE_NETWORK_1 network-object Servers 255.255.255.0 network-object ICT 255.255.255.0 access-list backup_access_in extended permit icmp any any echo-reply access-list backup_access_in extended permit object-group TCPUDP any interface backup object-group Allow_SVN access-list outside_access_in extended permit icmp any any echo-reply access-list outside_access_in extended permit object-group TCPUDP any interface outside object-group Allow_SVN access-list outside_access_in extended permit tcp any host FTP01 object-group DM_INLINE_TCP_3 access-list inside_access_in extended permit object-group TCPUDP any any eq domain access-list inside_access_in extended deny ip Productie-No-Internet 255.255.255.0 any access-list inside_access_in extended permit ip object-group Migration_group any access-list inside_access_in extended permit tcp Servers 255.255.255.0 any eq smtp access-list inside_access_in extended deny tcp Servers 255.255.255.0 any eq smtp access-list inside_access_in extended permit ip Servers 255.255.255.0 any access-list inside_access_in extended permit tcp object-group Department_Vlans any object-group Allowed_Protocols access-list inside_access_in extended permit tcp object-group Allowed_FTP any object-group DM_INLINE_TCP_2 access-list inside_access_in extended permit tcp any any object-group bittorrent access-list 110 extended permit ip Default_Vlan 255.255.0.0 192.168.253.0 255.255.255.0 access-list DMZ_access_in extended permit ip any any access-list DMZ_access_in extended permit icmp any any echo access-list DMZ_access_in extended permit tcp any any object-group Allowed_FTP01_Protocols access-list DMZ_access_in extended permit object-group TCPUDP host FTP01 object-group DM_INLINE_NETWORK_1 object-group Allow_FileSharing_FTP01 access-list OUTSIDE_IN extended permit tcp any host FTP01 object-group Allow_FTP access-list OUTSIDE_IN extended permit icmp any any echo-reply access-list OUTSIDE_IN extended permit object-group TCPUDP any interface outside object-group Allow_SVN pager lines 24 logging enable logging list test level notifications logging buffered warnings logging asdm warnings mtu inside 1500 mtu outside 1500 mtu backup 1500 mtu Management 1500 mtu DMZ 1500 ip verify reverse-path interface inside ip verify reverse-path interface Management ip audit name Attack attack action alarm ip audit name Info info action alarm ip audit interface inside Info ip audit interface inside Attack ip audit interface outside Info ip audit interface outside Attack ip audit interface backup Info ip audit interface backup Attack ip audit interface DMZ Info ip audit interface DMZ Attack failover failover lan unit secondary failover lan interface failover Vlan255 failover polltime unit 1 holdtime 3 failover polltime interface 1 holdtime 5 failover interface ip failover 192.168.255.1 255.255.255.252 standby 192.168.255.2 monitor-interface inside monitor-interface outside monitor-interface backup monitor-interface Management monitor-interface DMZ icmp unreachable rate-limit 10 burst-size 1 asdm image disk0:/asdm-524.bin no asdm history enable arp timeout 14400 nat-control global (outside) 1 interface global (backup) 1 interface nat (inside) 0 access-list 110 nat (inside) 1 Default_Vlan 255.255.0.0 dns nat (DMZ) 1 192.168.253.0 255.255.255.0 static (inside,outside) tcp interface 888 192.168.0.194 888 netmask 255.255.255.255 dns static (inside,backup) tcp interface 888 192.168.0.194 888 netmask 255.255.255.255 dns static (inside,backup) udp interface 888 192.168.0.194 888 netmask 255.255.255.255 dns static (inside,outside) udp interface 888 192.168.0.194 888 netmask 255.255.255.255 dns static (DMZ,outside) tcp interface ftp FTP01 ftp netmask 255.255.255.255 dns static (DMZ,outside) tcp interface ftp-data FTP01 ftp-data netmask 255.255.255.255 dns access-group inside_access_in in interface inside access-group OUTSIDE_IN in interface outside access-group backup_access_in in interface backup access-group DMZ_access_in in interface DMZ route outside 0.0.0.0 0.0.0.0 213.125.16.81 1 track 1 route backup 0.0.0.0 0.0.0.0 188.201.212.129 254 ! router rip network 192.168.254.0 passive-interface outside passive-interface backup passive-interface Management passive-interface DMZ default-information originate version 2 ! timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute http server enable http 192.168.4.0 255.255.255.0 Management http ICT 255.255.255.0 inside no snmp-server location no snmp-server contact snmp-server enable traps snmp authentication linkup linkdown coldstart fragment chain 1 inside fragment chain 1 outside fragment chain 1 backup fragment chain 1 Management fragment chain 1 DMZ sla monitor 123 type echo protocol ipIcmpEcho 213.51.160.52 interface outside num-packets 3 frequency 10 sla monitor schedule 123 life forever start-time now service resetoutside crypto ipsec transform-set TRANS_ESP_AES-256_SHA esp-aes-256 esp-sha-hmac crypto ipsec transform-set TRANS_ESP_AES-256_SHA mode transport crypto dynamic-map outside_dyn_map 20 set pfs crypto dynamic-map outside_dyn_map 20 set transform-set TRANS_ESP_AES-256_SHA crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map crypto map outside_map interface outside crypto isakmp enable outside crypto isakmp policy 10 authentication pre-share encryption aes-256 hash sha group 5 lifetime 86400 ! track 1 rtr 123 reachability telnet timeout 5 ssh ICT 255.255.255.0 inside ssh 192.168.4.0 255.255.255.0 Management ssh timeout 5 ssh version 2 console timeout 0 management-access Management ntp server 193.67.79.202 prefer ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum 512 id-randomization id-mismatch action log policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect netbios inspect rsh inspect rtsp inspect skinny inspect esmtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp ! service-policy global_policy global prompt hostname context Cryptochecksum:0289a7cab68afeb8fde4d99723647e99 : end
Thanks in advance.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2010 03:00 AM
Hi everyone,
Guess what, It works! i can reach the FTP server. All the ftp tests i did, i did them from the internal LAN. my thoughts were that when i ftp to the outside address, the packets also are delivered on the outside address. But it seems not true.
Anyway, i connected a lapto directly to the modem of our backup internet line, and i could reach the FTP server at the outside address i specified.
The only challange i have now is to get the traffic routed to the static public IP of the ftp server (spare address of the primary ISP), also when the primary line is down.
I guess i got to call both ISP's...
Anyway, thanks for all the help and replies!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2010 07:55 AM
Hey,
Great to hear that! The fact that you were trying to access the FTP server from the LAN using the Public IP explains why you were facing those problems. Well, if you really need that, then you will need U-turning configured on the ASA:
static (dmz,inside) 1.1.1.3 192.168.253.2
All the best in the future!!
Thanks and Regards,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2010 08:30 AM
Hey,
To make the FTP server accessible via the backup line, i've made the same settings i did with the primairy line. the only difference is that i applied the ACL to the backup interface, and the NAT rule i specified with another spare public IP, from the other ISP. After disabling the primairy line, all traffic goes via the backup line, but the ftp server isn't reachable...
Also the ACL doesn't show any hits.
I've to go now. Tomorrow is another day:)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2010 08:44 AM
Hi,
Just to clarify one thing here. So originally when traffic passes thro the primary line, the DNS resolves to the IP address 1.1.1.3. Now assuming on the backup line we have the public IP as 2.2.2.3 for the FTP server, then does the DNS also reflect this change when the backup line becomes active?
Regards,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2010 12:17 AM
At this stage i don't use dns. I connect to the public ip address of the ftp server.
When everything works as it should, then i make two A-records on the DNS servers of the hosting company where our domains are hosted, each with one of the public IP adresses of the ftp server. According to the an engineer of the hosting company. He thinks that this is the only way to make it sort of HA, but he never had done it this way, with two host records.
Another question:
I've configured dual ISP on our ASA's:
http://www.cisco.com/warp/public/110/pix-dual-isp.pdf
When the primary link is active, is incoming traffic at the backup interface also accepted and routed into the asa, or how does that work?
When it's not, then the two A-records story can't work, since customers are randomly pointed to one of the two IP's
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2010 12:31 AM
Hey,
> When the primary link is active, is incoming traffic at the backup interface also accepted and routed into the asa, or how does that work?
My guess is that the ASA might actually drop packets being routed to the "backup" interface (because of reverse path lookup) or end up routing the return packets incorrectly (since the default route will be pointing out the primary interface). I have not tried this out before so i am not really sure. But the fact is that when we have dual ISP config as the one we have here, only one link is supposed to be active and passing ttraffic at any point in time.
Regarding the DNS issue, won't it be possible to do what NT said previously (somehow track the primary IP 1.1.1.3 and when that is unreachable, failover the DNS record to 2.2.2.3)?Again, i ahve not worked with DNS servers so am not sure if such a thing is even possible.
Regards,
Prapanch
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
