- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: How to configure Firepower AMP to not upload files to the cloud / only local analysis
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to configure Firepower AMP to not upload files to the cloud / only local analysis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2019 03:05 AM - edited 02-21-2020 09:46 AM
Hi
we just want to perform File checking on known files (Hash comparison) and also local analysis on FMC, when it is a unknown file. We do not want to upload any files in the cloud. How must a Policy for this look like? I read a lot in the docs, but didn´t finally get to know if this config is good.
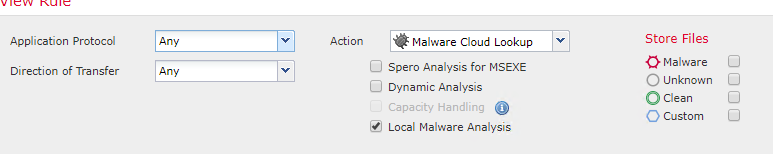
Would this rule fit the requirements above?
Thanks!
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2019 08:36 PM
Potentially yes. However, is your goal to block malware or only monitor and be alerted when malware files traverse your network? The action "Malware Cloud Lookup" will only check and record the disposition of the files that traverse your network but no blocking will occur.
With regards to your other question: The "Dynamic Analysis" option is what will instruct the FMC to upload unknown files to the cloud for analysis. If you leave that box unchecked, then no files will be uploaded.
You can get detailed info on all of this in the configuration guide for FMC:
I hope this helps!
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2019 05:59 AM
Hi,
in general, wheter only monitoring or also with a blocking action, no upload of files to the cloud should actually happen. That´s the main point.
But additionally to what you say, the Spero analysis also performs uploads, right?
I think the site you pointed to actually contains some addtional helpful information.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-24-2019 12:11 PM
It really all depends on how you configure your policy/rules. Below is a snip it directly from the link that I mentioned in my previous post:
Spero Analysis
Spero analysis examines structural characteristics such as metadata and header information in executable files. After generating a Spero signature based on this information, if the file is an eligible executable file, the device submits it to the Spero heuristic engine in the AMP cloud. Based on the Spero signature, the Spero engine determines whether the file is malware. You can also configure rules to submit files for Spero analysis without also submitting them to the AMP cloud.
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2019 04:36 AM
Thank you, Know I understand, Spiro is only for executable files... I think I will need to read more into it first, another huge topic...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide