- Cisco Community
- Technology and Support
- Security
- Network Security
- how to disable Accept connections using TLSv1
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
how to disable Accept connections using TLSv1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 07:25 AM
I need to disable the TLSv1.1 on ASA FDM 5516x and i have already disable the TLSv1.0 & 1.1 from SSL Settings via GUI & then according to the below showing command results i still can see TLSv1.1 still active
> show ssl
Accept connections using SSLv3 or greater and negotiate to TLSv1.2 or greater
Start connections using TLSv1 and negotiate to TLSv1 or greater
SSL DH Group: group14 (2048-bit modulus, FIPS)
SSL ECDH Group: group19 (256-bit EC)
SSL trust-points:
Self-signed (RSA 2048 bits RSA-SHA256) certificate available
Self-signed (EC 256 bits ecdsa-with-SHA256) certificate available
Certificate authentication is not enabled
> show running-config ssl
ssl server-version tlsv1.2
ssl cipher tlsv1.2 custom "ECDHE-ECDSA-AES256-GCM-SHA384,ECDHE-RSA-AES256-GCM-SHA384,DHE-RSA-AES256-GCM-SHA384"
> show running-config all ssl
ssl server-version tlsv1.2
ssl client-version tlsv1
ssl cipher default medium
ssl cipher tlsv1 medium
ssl cipher tlsv1.1 medium
ssl cipher tlsv1.2 custom "ECDHE-ECDSA-AES256-GCM-SHA384,ECDHE-RSA-AES256-GCM-SHA384,DHE-RSA-AES256-GCM-SHA384"
ssl cipher dtlsv1 medium
ssl dh-group group14
ssl ecdh-group group19
ssl certificate-authentication fca-timeout 2> show ssl> show running-config ssl> show running-config all ssl
> show version
---------------[ EGCAI01-Firepower ]----------------
Model : Cisco ASA5516-X Threat Defense (75) Version 7.0.1 (Build 84)
UUID : 8b6ebab4-5347-11eb-b351-b67ba7c78576
Rules update version : 2023-10-25-001-vrt
VDB version : 353
----------------------------------------------------
I have also enable the SSL encryption & Block_SSL3.0_and_TLS1.0_and_TLS1.1 as per below :
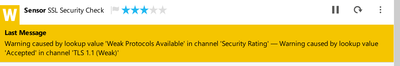
Also still showing TLSv1.1 enabled on the PRTG server ! so how can i disable TLSv1.1 totally from the fdm !?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 08:04 AM
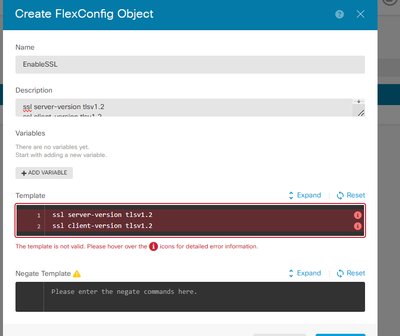
You can try to add "ssl client-version tlsv1.2" with FlexConfig (FDM may not accept it though), although this doesn't make much sense on FTD. This command sets TLS version when device is a TLS client, but FTD doesn't support clientless WebVPN and hence doesn't initiate TLS connections from Lina code.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 08:43 AM
THANKS for your reply and i have tried flexconfig but below error coming
Also that mean i can ignore this one and will be be usable !? and no way to disable it !? or enable TLSv1.2 on client level ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 08:48 AM
@amralrazzaz I believe you can only set the TLS settings for Remote Access VPN connections, not the Web GUI - https://www.cisco.com/c/en/us/td/docs/security/firepower/70/fdm/fptd-fdm-config-guide-700/fptd-fdm-system.html#Cisco_Task_in_List_GUI.dita_80e542fa-4b68-4611-bdcc-c0dee2540488
"The SSL cipher settings control which TLS versions and encryption cipher suites are allowed for TLS/SSL connections to the device. Specifically, these settings control the ciphers clients are allowed to use when establishing remote access VPN connections"
An SSL decryption rule would be for traffic through the FTD not to itself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 09:02 AM
Now i got you and thanks for clarification.
So in my case with the above outputs from show SSL command s I'm safe ! & for the TLSv1.2 on the client level doesn't matter coz im not using remote access vpn connections for the users!
btw S-RAS or site2site VPN already configured but i think that's not related to our case ! as im targeting the safe remote connection to the FTD GUI via website with stronge encryption methods and i have already change the SSL settings anyway to TLTv1.2 adn creating policy for the traffic goes through the FDM not to the FDM it self as you said & no more action i can do ? right ?
> show running-config ssl
ssl server-version tlsv1.2
ssl cipher tlsv1.2 custom "ECDHE-ECDSA-AES256-GCM-SHA384,ECDHE-RSA-AES256-GCM-SHA384,DHE-RSA-AES256-GCM-SHA384"
> show ssl
Accept connections using SSLv3 or greater and negotiate to TLSv1.2 or greater
Start connections using TLSv1 and negotiate to TLSv1 or greater
SSL DH Group: group14 (2048-bit modulus, FIPS)
SSL ECDH Group: group19 (256-bit EC)
SSL trust-points:
Self-signed (RSA 2048 bits RSA-SHA256) certificate available
Self-signed (EC 256 bits ecdsa-with-SHA256) certificate available
Certificate authentication is not enabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2024 12:11 PM
@Rob Ingram can you check this too if it okay or i have to do something else? :
> show ssl-policy-config
============[ NGFW-Default-SSL-Policy ]=============
=================[ Default Action ]=================
Default Action : Do Not Decrypt
======[ Category: admin_category (Built-in) ]=======
=====[ Category: standard_category (Built-in) ]=====
-------[ Block_SSL3.0_and_TLS1.0_and_TLS1.1 ]-------
State : Enabled
Action : Block
Source Networks : Source Services : Destination Networks
: Destination Services : URLs
Certificates : Subject DN : Issuer DN
: Versions : SSL v3.0
TLS v1.0
TLS v1.1
Logging Configuration
DC : Yes
End : Yes
Syslog : AC58b5f59a-b6f3-11eb-b14a-572da8a7f4ea
=======[ Category: root_category (Built-in) ]=======
============[ Trusted CA Certificates ]=============
=============[ Undecryptable Actions ]==============
Unsupported Cipher Suite : Inherit Default Action
Unknown Cipher Suite : Inherit Default Action
Compressed Session : Inherit Default Action
Uncached Session ID : Inherit Default Action
SSLv2 Session : Inherit Default Action
Handshake Error : Inherit Default Action
Decryption Error : Block
ALSO I CAN SEE STILL TLSv1.1 enabled on below ! or its just showing the available versions to be using if needed and its not enabled?!
> show ssl-protocol
The supported ssl protocols are TLSv1.1 TLSv1.2
>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 12:55 PM
I will check this case tonight
Update you
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide