- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: IPS Detection
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPS Detection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2021 10:48 AM
I configured my IPS policy by filtering by maleware and selecting "Drop and Block" for all snort rules. I have this event coming up (See atttached) matching one of the rules. Its the internal DNS server it seems being flagged as the attacker and event suggests maleware on it. I have researched all over on this , ran maleware scans, AV is on the server and have come up empty. The research I did suggest this server is part of a botnet but I cant find anything wrong with it and the snort definition states no known false positives. Any ideas here on how I can go about seeing if this is legit or not or where I can find doc on how to remediate?
- Labels:
-
IPS and IDS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2021 12:23 AM
there are few think you can do.
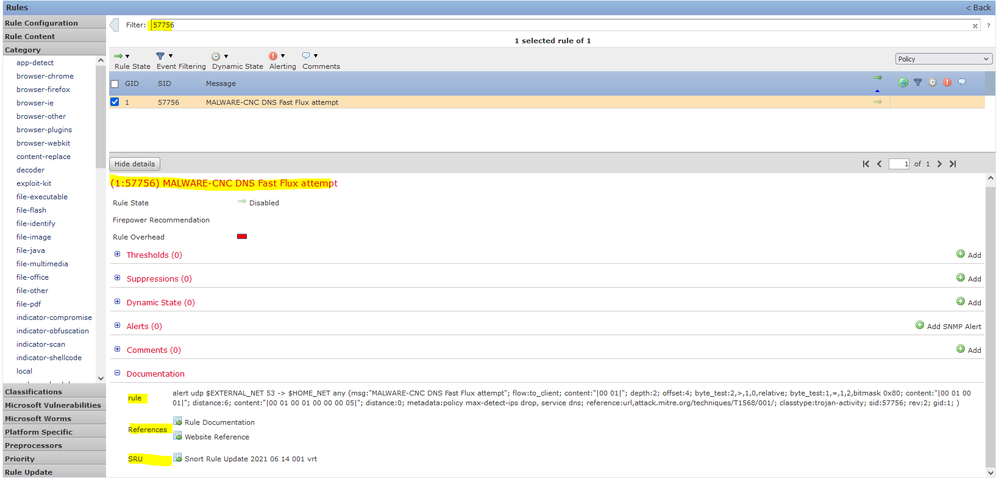
1. you can go to the intrusion policy snort rule and either you can disable this rule your snort id 1:57756 (https://attack.mitre.org/techniques/T1568/001/)
https://snort.org/rule_docs/1-57756 or you can Generate the event but not droping the packet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2021 01:21 AM
Have you defined your $HOME_NET and @$EXTERNAL_NET variables correctly (Variable set under objects)? The rule seems to indicate it should only flag hosts it believe are external.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2021 05:49 AM
I did define the variables as shown in the attached(EXTERNAL defined as exclusion of HOME-NE)
I am stumped and would hate to just turn off the rule if there actually is a legit threat here. I also have another snort rule as shown populating intrusion logs as well.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide