- Cisco Community
- Technology and Support
- Security
- Network Security
- IPS Event Action Filter is not working properly.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPS Event Action Filter is not working properly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 08:31 AM - edited 03-10-2019 06:08 AM
Hi,
We have a local syslog server which listens on UDP 514 port. As many UDP frames has been cut I've done some investigation and found dropped packets (action requested by IPS). This was 1206.0 signature which is "IP Fragmant Too Small". I have created a new entry in IPS Policies to filter this out, but it didn't help. As a test I have disabled the signature completly and all frames have been delivered fine. Another thing I've tried was bringing the new action filter to the top and enabled "Stop on Match" option. Still the same. The only one solution is to disable the signature, but we can't do it.
This is ASA-SSM-20 installed on ASA 5520 version 7.1(6)E4, mode: inline
Bug search tool didn't show any related bugs.
I have checked Database integrity and get "No errors found while performing database integrity checks.
My questions are:
1. What can cause an action to be ignored on IPS?
2. Is it worth to use "Repair Database" tool? If yes what is the impact.
3. Is it possible to check hit counts on each action filter?
Regards
Mariusz
- Labels:
-
IPS and IDS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2014 11:29 PM
By default, the Summarizer is enabled. If you disable it, all signatures are set to Fire All with no summarization. If you configure individual signatures to summarize, this configuration will be ignored if the Summarizer is not enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 07:36 AM
Thanks for reply.
Summarizer is enabled. All signature settings are left as default.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 08:36 AM
Hey
Just for a test..
Inside the Sensor Management, Blocking, Blocking Properties.
Add the IP as Never Block, just for a test..
Anyway, Dont you think that you should update your version?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2014 07:22 AM
Hi,
Thanks for your input Diego.
I have added the IP as you've suggested, but no difference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2014 07:45 AM
Hum... Very weird, I never see it before!
I think you have a missmatch configuration, like, something is not matching with anything so, the filter does not apply..
I know you did, but, maybe a new double-check in the configuration? Src Addr, Signature ID... Is everything correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2014 04:06 AM
Hi All,
Filter settings below:
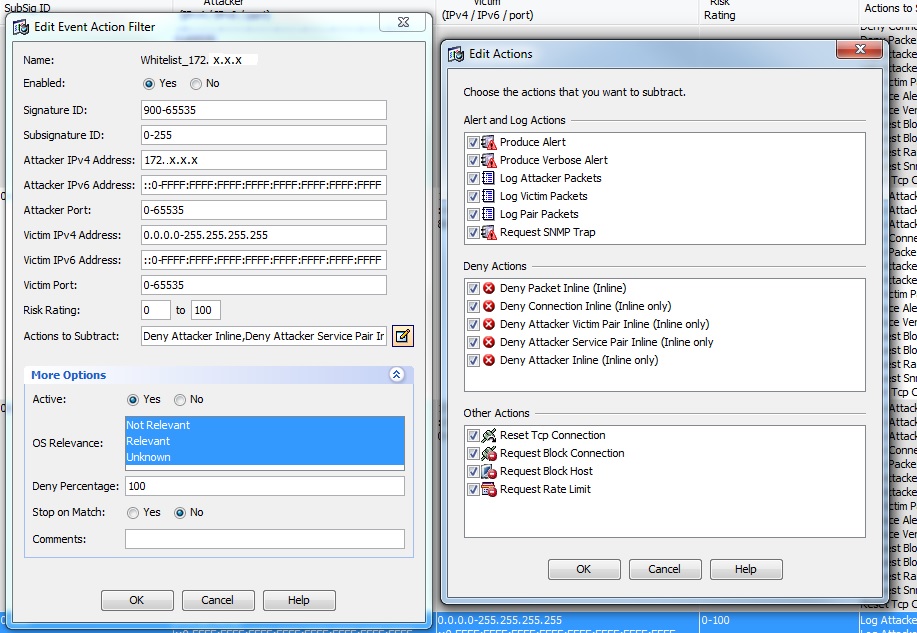
The filter works partially as I don't get alerts on the IPS itself.
Firewall LOG:
4 Feb 14 2014 15:33:22
IPS LOG (when enabled):
evIdsAlert: eventId=1352793300955167909 vendor=Cisco severity=low
originator:
hostId: SSM02
appName: sensorApp
appInstanceId: 1192
time: Feb 14, 2014 15:33:22 UTC offset=0 timeZone=GMT00:00
signature: description=IP Fragment Too Small id=1206 version=S212 type=anomaly created=20030801
subsigId: 0
sigDetails: Too many small IP fragments in datagram
interfaceGroup: vs0
vlan: 0
participants:
attacker:
addr: 172.x.x.x locality=OUT
port: 39715
target:
addr: x.x.x.x locality=OUT
port: 514
os: idSource=unknown type=unknown relevance=relevant
alertDetails: InterfaceAttributes: context="single_vf" physical="Unknown" backplane="GigabitEthernet0/1" ;
riskRatingValue: 50 targetValueRating=medium attackRelevanceRating=relevant
threatRatingValue: 50
interface: GigabitEthernet0/1 context=single_vf physical=Unknown backplane=GigabitEthernet0/1
protocol: udp
Our next step is to make a service policy exception on the firewall itself. We are also considering reloading the IPS device or at least the analysis engine.
Thanks for all your help so far. Any more suggestions are most welcome. I'll keep you up to date.
Regards
Mariusz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2014 07:14 AM
Update:
I configured the service policy rule on the firewall to bypass IPS. Still the same.
The only one option which works is to disable the signature.
Any more ideas?
Regards
Mariusz
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
