- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: is this a violation of NAT rule?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
is this a violation of NAT rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2019 01:26 AM
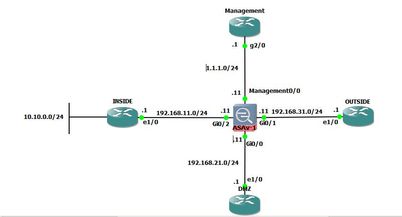
According to NAT section rule section 2 should be processed before section 3. In my test LAB the section 3 get processed. In other words Twice-NAT (after-auto) get processed. Expected is section 2 object NAT + PAT
There are two rules
1) Object NAT dynamic NAT+PAT(fallback)
2)Twice NAT after auto static source NAT
ciscoasa(config)# sh nat
Auto NAT Policies (Section 2)
1 (INSIDE) to (OUTSIDE) source dynamic NAT NAT+PAT
translate_hits = 10, untranslate_hits = 0
Manual NAT Policies (Section 3)
1 (INSIDE) to (OUTSIDE) source static 10.10.0.10 192.168.31.210
translate_hits = 15, untranslate_hits = 15
ciscoasa(config)#
!
ciscoasa(config)# sh run nat
!
object network NAT
nat (INSIDE,OUTSIDE) dynamic NAT+PAT
!
nat (INSIDE,OUTSIDE) after-auto source static 10.10.0.10 192.168.31.210
ciscoasa(config)#
ciscoasa(config)# sh run object-group network
object-group network NAT+PAT
network-object object NAT-POOL
network-object object PAT-POOL
!
ciscoasa(config)# sh run object network
object network NAT
range 10.10.0.1 10.10.0.5
object network NAT-POOL
range 192.168.31.100 192.168.31.101
object network PAT-POOL
host 192.168.31.200
object network 10.10.0.10
host 10.10.0.10
object network 192.168.31.210
host 192.168.31.210
ciscoasa(config)#
Test:
INSIDE#ping 8.8.8.8 so 10.10.0.10 repeat 1
Type escape sequence to abort.
Sending 1, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 10.10.0.10
!
Success rate is 100 percent (1/1), round-trip min/avg/max = 56/56/56 ms
INSIDE#
=================
OUTSIDE#
*Mar 17 09:57:08.767: IP: s=192.168.31.210 (Ethernet1/0), d=8.8.8.8, len 100, input feature, MCI Check(92), rtype 0, forus FALSE, sendself FALSE, mtu 0, fwdchk FALSE
*Mar 17 09:57:08.771: IP: s=192.168.31.210 (Ethernet1/0), d=8.8.8.8, len 100, rcvd 2
=================
There is no NAT or PAT as a result of section 2 NAT rule
ciscoasa(config)# show xlate
2 in use, 5 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from INSIDE:10.10.0.10 to OUTSIDE:192.168.31.210
flags sT idle 0:03:30 timeout 0:00:00
NAT from OUTSIDE:0.0.0.0/0 to INSIDE:0.0.0.0/0
flags sIT idle 1:08:36 timeout 0:00:00
ciscoasa(config)#
- Labels:
-
Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2019 03:21 AM
The source of the ping is 10.10.0.10, which is not included in
object network NAT
range 10.10.0.1 10.10.0.5
For this reason auto-nat will not be used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2019 05:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2019 06:12 AM - edited 03-20-2019 01:20 AM
In your configuration there is an object named NAT with IP range and NAT definition:
object network NAT
nat (INSIDE,OUTSIDE) dynamic NAT+PAT
object network NAT
range 10.10.0.1 10.10.0.5
object-group network NAT+PAT
network-object object NAT-POOL
network-object object PAT-POOL
'show nat' shows that there is an auto-NAT rule that translates whatever is configured in object named NAT to whatever configured in object-group named NAT+PAT.
Auto NAT Policies (Section 2)
1 (INSIDE) to (OUTSIDE) source dynamic NAT NAT+PAT
translate_hits = 10, untranslate_hits = 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2019 05:54 AM - edited 03-19-2019 06:04 AM
sorry you are right
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide