- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASAv Vs MultiContext
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 09:33 AM - edited 07-12-2020 11:22 PM
What would be the difference between deploying two Logical Devices inside of a same FP 9300 box vs just having two context on a single Logical Device?
What can you do with Multiple Logical Devices that you can't do with Multiple Context?
Thx a lot
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2020 10:48 PM
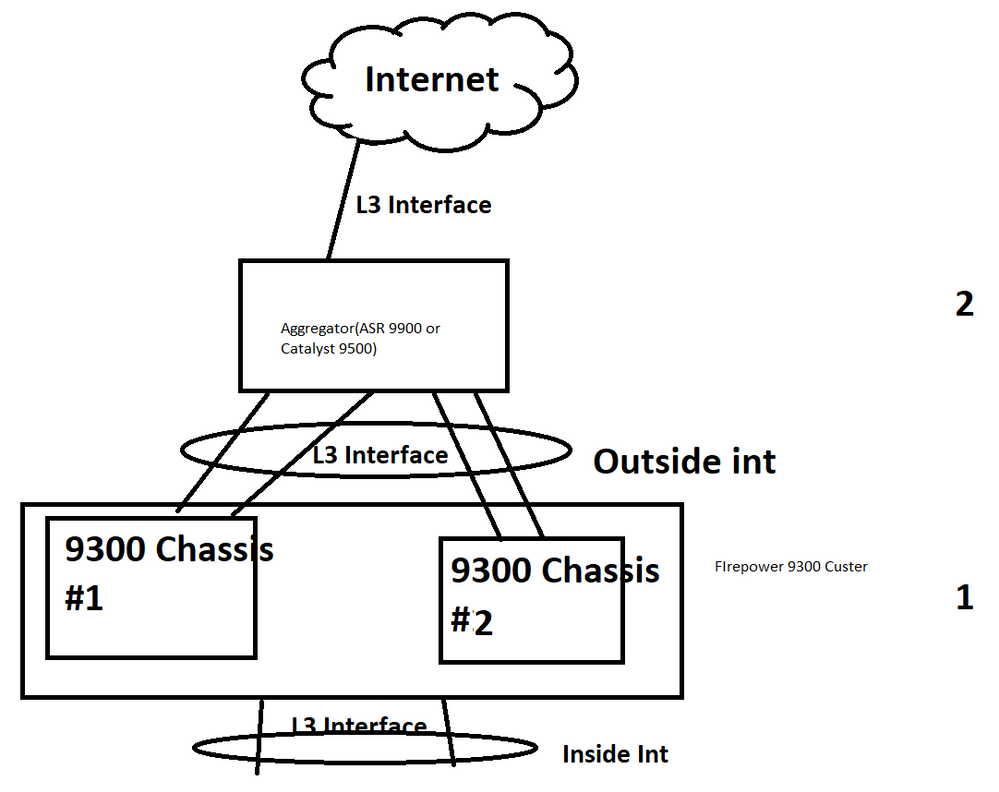
1. With a high end setup such as this, we would expect to see an external router doing BGP to one or more providers. Most likely the customer environment will have provider-independent address space assigned to them directly from their regional Internet registry (ARIN, RIPE, APNIC, LANIC). So no NAT is needed on the router - you have just regular routing with the customer address sapce facing the firewall and the point to point links (usually /30s) facing the provider(s).
2. The router should be the outermost device. That's where the routing functionality takes place and you have many many more options for both routing as well as other things such as you mentioned like DMVPN.
3. There may be an intermediate switch (or set of switches in a stack, VSS pair or vPC sort of arrangement) between the firewall cluster and any routers. That allows us to separate the Layer 2 resiliency (EtherChannel) from Layer 3 (ECMP). There are a number of considerations for that which are explained in more detail here:
...as well in the Cisco Live presentation I mentioned earlier in this thread.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 09:56 AM
you need to do 2 different ASAv. (not multicontext under ASAv, which has limitation look at below document).
ASAv has limitation see below : ( as per my last deployment of mine)
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 11:24 AM - edited 07-07-2020 01:11 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 10:19 AM
I'm confused by your question. ASAv does not run on the FP9300.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 10:39 AM - edited 07-07-2020 12:00 PM
P.S. I guess ASAv is the term used in Azure/AWS environments when you just mount a software image version, and you are not dealing with the hardware itself?!!, I didn't mean that here, I meant ASA logical devices
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 10:56 AM
As other have mentioned, ASAv is not something that runs on Firepower 9300. ASAv runs on VMware ESXi or KVM or in AWS and Azure.
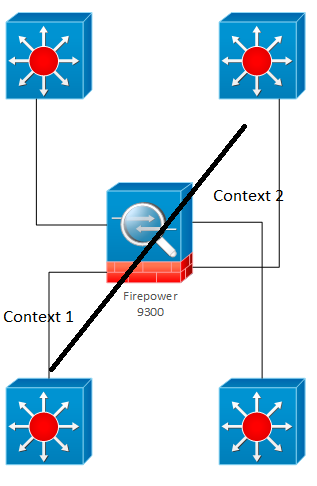
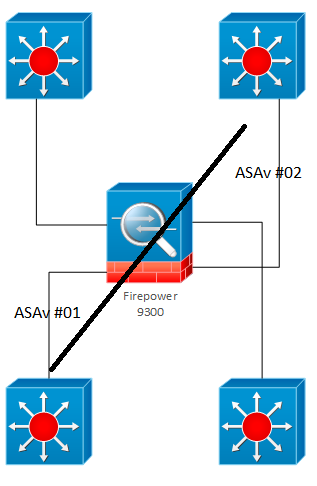
Firepower 9300 can run an ASA logical device (or multiple ASA logical devices if you have multiple Security Modules or SMs). A given ASA logical device on a Firepower 9300 can be single context or multiple context.
If the ASA logical devices are separate ones, each has dedicated SM hardware and interfaces.
ASA contexts share a given SM and may optionally share interfaces.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 11:38 AM - edited 07-07-2020 02:31 PM
1) So we can't create two or three Logical devices on the same SM-40 for example?
so the ability to have multiple ASAs is not license related, it's module related?
2) Could you also confirm that we have this limitation of Active/Active on Logical Devices the same way as ASAv?
the ASAv does not support the following ASA features:
- Clustering
- Multiple context mode
- Active/Active failover
- EtherChannels
- Shared AnyConnect Premium Licenses
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 01:09 PM
2) Could you also confirm that we have this limitation of Active/Active on Logical Devices the same way as ASAv?
ACTIVE/ ACTIVE means multi-context, if ASAv does not support multi-context, there is no A/A - its only Active-Standby.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 01:13 PM - edited 07-07-2020 02:32 PM
My mistake I didn't really mean ASAv from the beginning, I meant Logical Devices
I don't think a logical device has any of those limitations?!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2020 01:16 AM
Correct - the ability to run multiple ASA logical devices on a given Firepower 9300 is constrained to one per SM. You can have 1, 2 or 3 SMs in a Firepower 9300 chassis.
Any ASA logical device running on a Firepower 9300 can be multiple context, subject to ASA context licensing.
Any ASA logical devices running on a Firepower 9300 chassis can be clustered - both intra chassis (assuming you have multiple SMs) and inter-chassis.
Note that FTD logical devices on Firepower 9300 chassis are not the same. They don't have the concept of multi context. They have multi instance. You can run multi instance FTD on a Firepower 9300 with a single SM subject to hardware (CPU cores and memory) constraints.
For more detail please refer to Cisco Live presentation BRKSEC-3035 from Cisco Live Europe 2020.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-10-2020 11:05 AM - edited 07-10-2020 05:07 PM
That's a hell of a presentation and I need to go through the documentations as well but I haven't found time yet, thank you
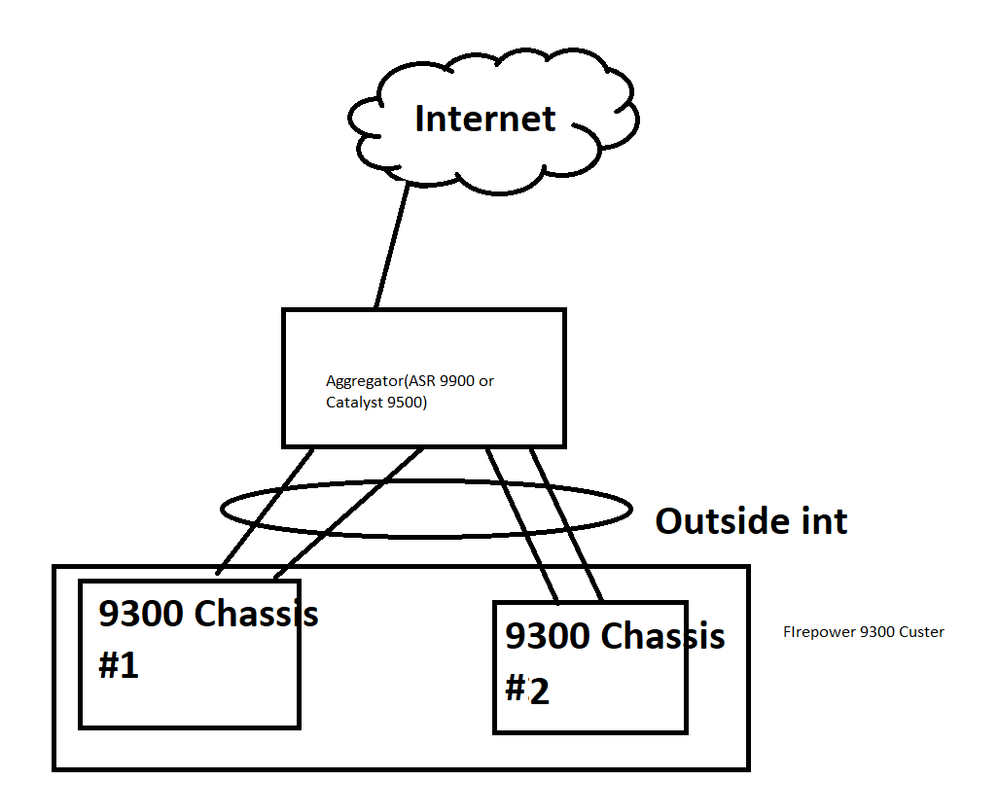
If you can help with how do we aggregate the outside interface on Firepower 9300 Cluster(two chassis ECMP chosen), and obviously it can't be a trunk of both inside and outside
What type of a device(aggregator) do I need on the outside interface since we NAT usually on the outside interface of the ASA, how can we put another L3 interface on the other end before it goes to the internet, so we're gonna NAT two times? once at the ASA cluster, once at the Aggregator(whether a switch or a router)?
Or we don't NAT at all at the ASA, we just NAT on the last hop(Router)?!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2020 04:55 AM
Is this for real world or theoretical use case?
Generally when one is looking at over half a million US$ setup like you've diagrammed there will be a high level and low level design prepared by the implementing team. It wouldn't be something designed by asking a couple of questions in a public forum.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2020 01:11 PM
Good information provided by the user, But question are you the one who going to deploy ? is this green field or brownfield deployment?
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2020 09:25 PM - edited 07-12-2020 11:24 PM
it's a brownfield
and please answer my questions, it doesn't matter that it's a real case scenario or not, it doesn't matter that we have unlimited budget, this forum is for people who have technical questions, and everything in technology has an an answer to it, thank you so much guys for sharing your infield experience as I can't find these in textbooks
but let me rephrase my questions,
1) Where does the NAT typically take place in productions that have both firewall and a router(who is a DMVPN hub)
- Only at the Firewall(behind a router) on Number one, although I don't think this can be possible
- Both being nat-ed at the Firewall and the Router(twice) Number 1 and 2
- Only at the router(number 2)
2) Generally in most productions out there, router is behind the firewall or firewall is behind the router? I found it would be highly inconvenient in lotta of ways, to place the firewall as the last node, specially if you are a DMVPN hub.
is placing the router as the last node can compromise the security at all?
3) How do we aggregate the outside interface of the two chassis(cluster ECMP), is there a special device, or you can use either a Router(ASR 9000 nVR cluster) or a L3 interface switch SVL(Stackwise virtual)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2020 10:48 PM
1. With a high end setup such as this, we would expect to see an external router doing BGP to one or more providers. Most likely the customer environment will have provider-independent address space assigned to them directly from their regional Internet registry (ARIN, RIPE, APNIC, LANIC). So no NAT is needed on the router - you have just regular routing with the customer address sapce facing the firewall and the point to point links (usually /30s) facing the provider(s).
2. The router should be the outermost device. That's where the routing functionality takes place and you have many many more options for both routing as well as other things such as you mentioned like DMVPN.
3. There may be an intermediate switch (or set of switches in a stack, VSS pair or vPC sort of arrangement) between the firewall cluster and any routers. That allows us to separate the Layer 2 resiliency (EtherChannel) from Layer 3 (ECMP). There are a number of considerations for that which are explained in more detail here:
...as well in the Cisco Live presentation I mentioned earlier in this thread.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide