- Cisco Community
- Technology and Support
- Security
- Network Security
- okay that shows ASA is
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Many TCP retransmissions on Cisco ASA Log to a specific website.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2017 01:00 PM - edited 03-12-2019 01:45 AM
Hi everyone.
I am stuck on a problem for several days and could not solve it so far. When I try to access a specific website, a timeout error occurs on browser. Tried to open wireshark to analyze the packet and could see many TCP retransmissions. It happens on Ciso ASA Capture as well.
The IP address of the website appears on Top 10 Protected Servers under SYN Attack on ASA Firewall Dashboard. (I do not know why, because it is a corporate website hosted outside our LAN).
I am able to open the website from everywhere, except from the company LAN. We have already checked proxy settings, DNS and everything looks fine.
Also we are able to open the website through browser with no problems, but the problem happens a few seconds later.
Attached a wireshark capture from internal host to the web site.
Thanks in advance.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2017 08:35 PM
Hi,
Where this attached capture has been take? Looking at it it seems that SYN is timing out. SYN/ACK which should be the responded by server is not being returned.
Can you apply bi-directional capture on both ingress and egress interface of ASA and share with us?
Thanks
Pranay
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2017 06:38 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2017 06:39 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2017 09:45 PM
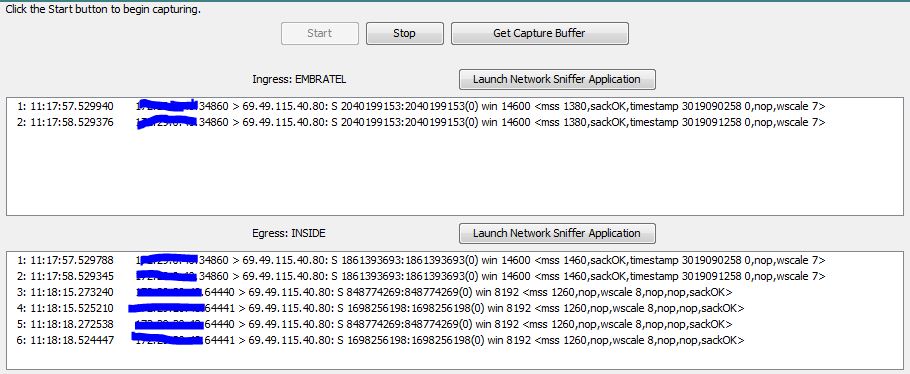
I see two captures, which one is correct?
Looking at this one it seems ASA is dropping packet.
Assuming your webserver is located behind "EMBRATEL", please provide following output
packet-tracer input inside tcp <inside test machine IP> 12345 69.49.115.40 80
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 05:44 AM
Hi Pranay.
Thanks for your time.
The first attachment is a capture from inside to outside interface. The second one is from outside to inside, mapping the IP addresses of internal host and website.
EMBRATEL is another Internet link which I connected to the ASA in order to force the connection to the website to go through that Internet link. But the problem remains the same even with another internet link. The original interface is the OUTSIDE. Both interfaces have Public IP addresses and different service providers. That's why I suspected the problem should be the ASA.
Here we have the output of Packet tracer as you requested:
PS.: the output was omitted. Results of the all phases was: allow.
packet-tracer input insIDE tcp <Internal IP Address> 55500 69.49.115.40 80
Result:
input-interface: INSIDE
input-status: up
input-line-status: up
output-interface: OUTSIDE
output-status: up
output-line-status: up
Action: allow
As you can see, there is no rule that may deny the flow between the internal hosts and the website.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 05:44 AM
Is it possible to share relevant part of your config like Nat access-list and objects? You can hide public IP.Also I need to know if this web server is in your network or on internet and what is the IP.Sorry but I need to have all info again to avoid any drag in solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 06:08 AM
I will try to send you the configs.
First I would like to inform the website is outside our LAN. We do not manage this web service. We are able to access the site when the flow is not going through ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 06:20 AM
okay, my concern is that we are seeing egress capture nil. This means ASA is dropping it.
Let's tale some more output
cap capi interface <inside interface> match tcp any host 69.49.115.40
cap capo interface <outside interface> match tcp any host 69.49.115.40
cap asp type asp-drop all <make sure this doesn't fill up with time, so try to initiate traffic soon enough>
Initiate traffic,after test
show cap capi
show cap capo
show cap asp | in 69.49.115.40
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 06:33 AM
Here we have the results:
show cap capi
45 packets captured
1: 11:24:09.936963 172.29.20.48.60056 > 69.49.115.40.23: S 3723490640:3723490640(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
2: 11:24:12.933499 172.29.20.48.60056 > 69.49.115.40.23: S 3723490640:3723490640(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
3: 11:24:17.295318 172.29.20.48.60067 > 69.49.115.40.80: S 1119405222:1119405222(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
4: 11:24:17.295654 172.29.20.48.60068 > 69.49.115.40.80: S 3965396553:3965396553(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
5: 11:24:17.544924 172.29.20.48.60069 > 69.49.115.40.80: S 1104174006:1104174006(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
6: 11:24:18.932691 172.29.20.48.60056 > 69.49.115.40.23: S 3723490640:3723490640(0) win 8192 <mss 1260,nop,nop,sackOK>
7: 11:24:20.292862 172.29.20.48.60068 > 69.49.115.40.80: S 3965396553:3965396553(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
8: 11:24:20.294799 172.29.20.48.60067 > 69.49.115.40.80: S 1119405222:1119405222(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
9: 11:24:20.544969 172.29.20.48.60069 > 69.49.115.40.80: S 1104174006:1104174006(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
10: 11:24:26.293197 172.29.20.48.60067 > 69.49.115.40.80: S 1119405222:1119405222(0) win 8192 <mss 1260,nop,nop,sackOK>
11: 11:24:26.296142 172.29.20.48.60068 > 69.49.115.40.80: S 3965396553:3965396553(0) win 8192 <mss 1260,nop,nop,sackOK>
12: 11:24:26.543139 172.29.20.48.60069 > 69.49.115.40.80: S 1104174006:1104174006(0) win 8192 <mss 1260,nop,nop,sackOK>
13: 11:24:38.812046 172.29.20.48.60080 > 69.49.115.40.80: S 1874722260:1874722260(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
14: 11:24:39.063168 172.29.20.48.60081 > 69.49.115.40.80: S 3867230085:3867230085(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
15: 11:24:41.811695 172.29.20.48.60080 > 69.49.115.40.80: S 1874722260:1874722260(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
16: 11:24:41.994943 172.29.0.40.58747 > 69.49.115.40.80: S 3356381847:3356381847(0) win 14600 <mss 1460,sackOK,timestamp 3105894723 0,nop,wscale 7>
17: 11:24:42.062801 172.29.20.48.60081 > 69.49.115.40.80: S 3867230085:3867230085(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
18: 11:24:42.994287 172.29.0.40.58747 > 69.49.115.40.80: S 3356381847:3356381847(0) win 14600 <mss 1460,sackOK,timestamp 3105895723 0,nop,wscale 7>
19: 11:24:45.044553 172.29.0.40.58893 > 69.49.115.40.80: S 2414024878:2414024878(0) win 14600 <mss 1460,sackOK,timestamp 3105897773 0,nop,wscale 7>
20: 11:24:46.044339 172.29.0.40.58893 > 69.49.115.40.80: S 2414024878:2414024878(0) win 14600 <mss 1460,sackOK,timestamp 3105898773 0,nop,wscale 7>
21: 11:24:47.811817 172.29.20.48.60080 > 69.49.115.40.80: S 1874722260:1874722260(0) win 8192 <mss 1260,nop,nop,sackOK>
22: 11:24:48.063000 172.29.20.48.60081 > 69.49.115.40.80: S 3867230085:3867230085(0) win 8192 <mss 1260,nop,nop,sackOK>
23: 11:24:48.094584 172.29.0.40.58925 > 69.49.115.40.80: S 3819779359:3819779359(0) win 14600 <mss 1460,sackOK,timestamp 3105900823 0,nop,wscale 7>
24: 11:24:49.094355 172.29.0.40.58925 > 69.49.115.40.80: S 3819779359:3819779359(0) win 14600 <mss 1460,sackOK,timestamp 3105901823 0,nop,wscale 7>
25: 11:24:51.668208 172.29.20.48.60084 > 69.49.115.40.80: S 1490377439:1490377439(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
26: 11:24:54.666194 172.29.20.48.60084 > 69.49.115.40.80: S 1490377439:1490377439(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
27: 11:25:00.663433 172.29.20.48.60084 > 69.49.115.40.80: S 1490377439:1490377439(0) win 8192 <mss 1260,nop,nop,sackOK>
28: 11:25:04.821292 172.29.20.48.60094 > 69.49.115.40.80: S 2212941114:2212941114(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
29: 11:25:07.820697 172.29.20.48.60094 > 69.49.115.40.80: S 2212941114:2212941114(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
30: 11:25:13.829028 172.29.20.48.60094 > 69.49.115.40.80: S 2212941114:2212941114(0) win 8192 <mss 1260,nop,nop,sackOK>
31: 11:25:47.059414 172.29.0.40.60135 > 69.49.115.40.80: S 241789380:241789380(0) win 14600 <mss 1460,sackOK,timestamp 3105959788 0,nop,wscale 7>
32: 11:25:48.059368 172.29.0.40.60135 > 69.49.115.40.80: S 241789380:241789380(0) win 14600 <mss 1460,sackOK,timestamp 3105960788 0,nop,wscale 7>
33: 11:25:50.109613 172.29.0.40.60154 > 69.49.115.40.80: S 3636168467:3636168467(0) win 14600 <mss 1460,sackOK,timestamp 3105962838 0,nop,wscale 7>
34: 11:25:51.109338 172.29.0.40.60154 > 69.49.115.40.80: S 3636168467:3636168467(0) win 14600 <mss 1460,sackOK,timestamp 3105963838 0,nop,wscale 7>
35: 11:25:53.159583 172.29.0.40.60206 > 69.49.115.40.80: S 3839917808:3839917808(0) win 14600 <mss 1460,sackOK,timestamp 3105965888 0,nop,wscale 7>
36: 11:25:54.159385 172.29.0.40.60206 > 69.49.115.40.80: S 3839917808:3839917808(0) win 14600 <mss 1460,sackOK,timestamp 3105966888 0,nop,wscale 7>
37: 11:25:57.598022 172.29.20.48.60108 > 69.49.115.40.80: S 4270315261:4270315261(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
38: 11:25:57.598647 172.29.20.48.60109 > 69.49.115.40.80: S 1484888710:1484888710(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
39: 11:25:57.850297 172.29.20.48.60110 > 69.49.115.40.80: S 727977138:727977138(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
40: 11:26:00.597808 172.29.20.48.60108 > 69.49.115.40.80: S 4270315261:4270315261(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
41: 11:26:00.598693 172.29.20.48.60109 > 69.49.115.40.80: S 1484888710:1484888710(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
42: 11:26:00.852784 172.29.20.48.60110 > 69.49.115.40.80: S 727977138:727977138(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
43: 11:26:06.596969 172.29.20.48.60108 > 69.49.115.40.80: S 4270315261:4270315261(0) win 8192 <mss 1260,nop,nop,sackOK>
44: 11:26:06.598952 172.29.20.48.60109 > 69.49.115.40.80: S 1484888710:1484888710(0) win 8192 <mss 1260,nop,nop,sackOK>
45: 11:26:06.857041 172.29.20.48.60110 > 69.49.115.40.80: S 727977138:727977138(0) win 8192 <mss 1260,nop,nop,sackOK>
show cap capo
18 packets captured
1: 11:26:48.982081 ***************.60121 > 69.49.115.40.80: S 2726257141:2726257141(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
2: 11:26:49.225391 ***************.60122 > 69.49.115.40.80: S 1833460272:1833460272(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
3: 11:26:51.988687 ***************.60121 > 69.49.115.40.80: S 2726257141:2726257141(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
4: 11:26:52.141426 ***************.33050 > 69.49.115.40.80: S 1513450852:1513450852(0) win 14600 <mss 1380,sackOK,timestamp 3106024869 0,nop,wscale 7>
5: 11:26:52.159873 ***************.60125 > 69.49.115.40.80: S 2765765039:2765765039(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
6: 11:26:52.219837 ***************.60122 > 69.49.115.40.80: S 1833460272:1833460272(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
7: 11:26:53.140373 ***************.33050 > 69.49.115.40.80: S 1513450852:1513450852(0) win 14600 <mss 1380,sackOK,timestamp 3106025869 0,nop,wscale 7>
8: 11:26:55.159980 ***************.60125 > 69.49.115.40.80: S 2765765039:2765765039(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
9: 11:26:55.190801 ***************.33087 > 69.49.115.40.80: S 189733825:189733825(0) win 14600 <mss 1380,sackOK,timestamp 3106027919 0,nop,wscale 7>
10: 11:26:56.190374 ***************.33087 > 69.49.115.40.80: S 189733825:189733825(0) win 14600 <mss 1380,sackOK,timestamp 3106028919 0,nop,wscale 7>
11: 11:26:57.985041 ***************.60121 > 69.49.115.40.80: S 2726257141:2726257141(0) win 8192 <mss 1260,nop,nop,sackOK>
12: 11:26:58.162360 ***************.60127 > 69.49.115.40.80: S 237582266:237582266(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
13: 11:26:58.225086 ***************.60122 > 69.49.115.40.80: S 1833460272:1833460272(0) win 8192 <mss 1260,nop,nop,sackOK>
14: 11:26:58.240679 ***************.33093 > 69.49.115.40.80: S 2566801134:2566801134(0) win 14600 <mss 1380,sackOK,timestamp 3106030969 0,nop,wscale 7>
15: 11:26:59.240389 ***************.33093 > 69.49.115.40.80: S 2566801134:2566801134(0) win 14600 <mss 1380,sackOK,timestamp 3106031969 0,nop,wscale 7>
16: 11:27:01.161231 ***************.60125 > 69.49.115.40.80: S 2765765039:2765765039(0) win 8192 <mss 1260,nop,nop,sackOK>
17: 11:27:01.162146 ***************.60127 > 69.49.115.40.80: S 237582266:237582266(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
18: 11:27:07.167609 ***************.60127 > 69.49.115.40.80: S 237582266:237582266(0) win 8192 <mss 1260,nop,nop,sackOK>
18 packets shown
show cap asp | include 69.49.115.40
The command above returns no information.
Once again, thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 06:37 AM
okay that shows ASA is forwarding traffic and we are seeing no response from server side. No ASA drops. The ip that you have hidden, are they public IP or private. If later is the case then you need to investigate why server is not responding this. If ********* is private IP it is NAT issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 06:39 AM
The hidden IP is the public IP address (OUTSIDE interface).
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 06:46 AM
Are you able to ping everything else on internet from ASA? You need to check with server admin are they seeing your IP. I am pretty sure ASA is not a culprit,btw you said there is another ISP interface on ASA, can you take captures on it too and make sure server is not responding on other interface, if that would be the case, it might not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 07:29 AM
I am able to access any website.
Here we have the capture as you requested:
packet-tracer input insIDE tcp 172.29.20.1 55500 69.49.115.40 80
Result:
input-interface: INSIDE
input-status: up
input-line-status: up
output-interface: EMBRATEL
output-status: up
output-line-status: up
Action: allow
18 packets shown
91: 12:26:06.483587 ***************.62606 > 69.49.115.40.80: S 3734512828:3734512828(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
92: 12:26:06.483937 ***************.62607 > 69.49.115.40.80: S 1636223969:1636223969(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
93: 12:26:06.734779 ***************.62608 > 69.49.115.40.80: S 3109391032:3109391032(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
94: 12:26:09.478277 ***************.62606 > 69.49.115.40.80: S 3734512828:3734512828(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
95: 12:26:09.483312 ***************.62607 > 69.49.115.40.80: S 1636223969:1636223969(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
96: 12:26:09.728371 ***************.62608 > 69.49.115.40.80: S 3109391032:3109391032(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
97: 12:26:15.478689 ***************.62606 > 69.49.115.40.80: S 3734512828:3734512828(0) win 8192 <mss 1260,nop,nop,sackOK>
98: 12:26:15.483556 ***************.62607 > 69.49.115.40.80: S 1636223969:1636223969(0) win 8192 <mss 1260,nop,nop,sackOK>
99: 12:26:15.728630 ***************.62608 > 69.49.115.40.80: S 3109391032:3109391032(0) win 8192 <mss 1260,nop,nop,sackOK>
100: 12:26:31.301437 ***************.34410 > 69.49.115.40.80: S 1000067133:1000067133(0) win 14600 <mss 1380,sackOK,timestamp 3109604037 0,nop,wscale 7>
101: 12:26:32.300811 ***************.34410 > 69.49.115.40.80: S 1000067133:1000067133(0) win 14600 <mss 1380,sackOK,timestamp 3109605037 0,nop,wscale 7>
102: 12:26:32.679926 ***************.62668 > 69.49.115.40.80: S 1992970945:1992970945(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
103: 12:26:32.680323 ***************.62669 > 69.49.115.40.80: S 2774775862:2774775862(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
104: 12:26:32.932904 ***************.62671 > 69.49.115.40.80: S 1171529549:1171529549(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
105: 12:26:34.351590 ***************.34435 > 69.49.115.40.80: S 4011591003:4011591003(0) win 14600 <mss 1380,sackOK,timestamp 3109607087 0,nop,wscale 7>
106: 12:26:35.350781 ***************.34435 > 69.49.115.40.80: S 4011591003:4011591003(0) win 14600 <mss 1380,sackOK,timestamp 3109608087 0,nop,wscale 7>
107: 12:26:35.676310 ***************.62669 > 69.49.115.40.80: S 2774775862:2774775862(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
108: 12:26:35.680567 ***************.62668 > 69.49.115.40.80: S 1992970945:1992970945(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
109: 12:26:35.930417 ***************.62671 > 69.49.115.40.80: S 1171529549:1171529549(0) win 8192 <mss 1260,nop,wscale 8,nop,nop,sackOK>
The hidden IP is the other ISP link.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2017 07:42 AM
Really strange...Can you plug ISP EMBRATEL directly in a laptop with same IP as currently assigned to ASA and try to access this specific website. I am still not sure if ASA is the problem.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

