- Cisco Community
- Technology and Support
- Security
- Network Security
- Migrating DMZ from ASA to FTD
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Migrating DMZ from ASA to FTD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2023 01:28 AM
Hi All,
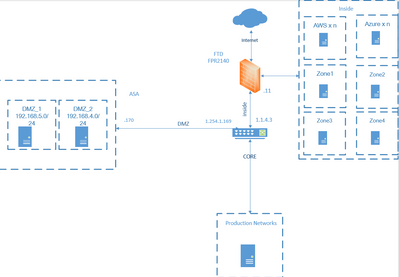
I've been tasked with migrating DMZ from a legacy ASA to a FMC managed FTD.
Currently there's a transit LAN to route DMZ destined traffic to the ASA.
We have a 20G (2x10g) port-channel between the core switch and the FTD and all zones listed below are mapped to sub-interfaces.
My plan is to migrate both DMZ and route via the FTD INSIDE, but unsure whether this is a good idea as it's routing dirty traffic with everything else.
Initially, I thought that each zone are protected from one another unless traffic is explicitly allowed, so this is fine but more I think about it became more unsure.
Any suggestion is very much appreciated.
Before
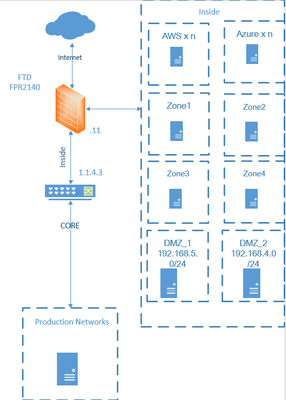
After
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2023 02:52 AM - edited 09-06-2023 02:55 AM
@atsukane I would keep the dirty (DMZ) traffic away from the trusted (inside) networks.
You could place each Zone/DMZ etc with it's own VRF to maintain the segmentation, and route to the FTD and if permitted acess the other Zones/DMZ networks.
Or you could just move the DMZs from the core on to a separate interface of the the FTD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2023 03:27 AM
Thanks @Rob Ingram
I have not dealt with VRF in the past, so I had some reading. It's an interesting concept and seems pretty straight forward to configure on FMC.
I'll play around with it and also try separate interfaces on FTD option as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2023 03:35 AM
@atsukane VRF will be required on the switches the Zones/DMZs are connected to, this ensures segmentation. The only way these Zones/DMZs can communicate with each other is routing traffic to the FTD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2023 05:00 AM
@Rob Ingram Ah, ok that makes more sense actually, thank you.
Still trying to get head around how to get this done so I may come back with more questions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2023 05:47 AM
I've been busy with other works and just revisiting this and updated the diagram to depict interfaces/zones better than the originally posted.
Internet switch is there to split the single fibre presentations to a pair of FTDs and just passing vlans.
We are fully virtualised, aside from some physical load-balancers, and are all connected to the core switch, so the FTD is the core router for the firewalled off vlans.
Using a dummy interface and a zone on the FTD, accessing the DMZ resource over the internet was no problem, but having trouble with internal access.
Just want to make sure the below diagram, the part circled in red, is correct and possible or am I getting this all wrong?
The lazy side of me is telling me to just add the DMZ interface as sub-interface of the inside port-channel as that would be a simple solution
thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2023 05:56 AM
@atsukane is the DMZ physically connected to the core switch (that's what it looks like)....but there is also a grey line connecting directly to the firewall?
I personally preferring having DMZ servers connected to different switching hardware and physically connected to a different firewall interface. If the DMZ is directly connected to the core switch, then as long as they are different vrf then traffic must be routed up to the FTD and cannot access the LAN directly (unless the ACP permits it).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2023 06:16 AM
Thanks @Rob Ingram DMZ are different interfaces on the firewall, sorry, the grey lines were bit confusing.
Production servers and DMZ servers are all VMs within the same vCentre, and connected via the core.
(Physically, we have Nexus switches (L2) between the core switch and the UCS chassis/hosts .)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2023 09:20 AM
@atsukane so if you are having problems with internal access from the new DMZ, are there Access Control Polices to explictly permit the traffic? Is routing setup correctly via the correct interfaces?
Run packet-tracer from the CLI to simulate the traffic flow and provide the output if necessary.
Any NAT rules that may unintentially translate the traffic between the DMZ and internal networks?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 01:51 AM
Thank you @Rob Ingram I have now connected the DMZ portchannel directly to Nexus switches and it's working as expected.
Thanks again for your assistance.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide