- Cisco Community
- Technology and Support
- Security
- Network Security
- Multi vlan on the inside interface of firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Multi vlan on the inside interface of firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2019 08:11 PM
Hi,
I have a layer 3 switch (Cisco Catalyst 3560) with multiple vlans configured on it, and connect to switch is inside interface of ASA 5505. Only host in the same vlan with inside interface of firewall can ping it, but I need all vlans can.
How would I config this?
- Labels:
-
Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2019 09:05 PM
Did you configure any layer 3 interface on this switch? If yes, normally all vlans should be able to communicate each others.
If the goal is to keep layer 2 only on the switch and layer 3 on the firewall then you need to create subinterfaces on your inside cable with all your vlans and allow traffic between them or configure the same security level and put the command same-security-traffic permit inter-interface
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2019 09:30 PM
All my vlans can communicate with each others.
My goal is make all vlans can go through firewall.
But inside interface of firewall can access only one vlan.
Do you have any idea?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2019 08:41 PM
If so, you have a simple option which consists into moving all your layer 3 to your firewall. For that you can have a trunk interface amd create your svi (interface vlan) on your asa. Be careful you're limited to 20 vlans.
A doc that can help:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa72/configuration/guide/conf_gd/int5505.pdf
If you want to keep all your vlans on your switch and just route your traffic on asa for Internet access, you can have an interco subnet between your switch and your asa, and then add a default static route in your switch pointing to your asa. On your asa you will have to configure a static route pointing to your switch off you can summarize all your inside networks (or multiple routes depending on your IP scheme).
Let me know which option you're trying to do, i can then show a quick config example.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2022 05:12 PM
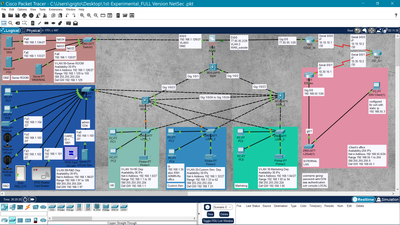
Same problem here
I'd like to keep the VLANs on the Layer 3 switch within my Inside network
just dont know how to make the ASA5505 to route all of them to the internet
my VLANs live happely togather well connected with one another, all hosts are pinging
each other easely, but no connection with the edge router, or the ASA's outside network. I'm a student, and this is killing me. Please, any advize will be very appreciated. Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2024 04:15 PM
it is an ASA5505, so the layer3 interfaces on the ASA are "interface vlan xxx", the ethernet interfaces are switchport on this device (hisis a big difference bettween ASA5505 andotther ASA devices). Configurig a switcport on the ASA as VLAN trunk (that is, what is on tis device similar to subinterfaces on other ASAs) requires a securityplus license. Without a securitplus license on ASA5505, you may connec one ethernet port per VLAN to an access port in the same VLAN. Be shure to *not* configure layer3 interfaces on the switch in each VLAN, ottherwise the switch will do the routing bypassing the firewall.
Also be shure to configure "same-security-traffic pemit inter-interface" if you want to enable comunication between layer3 interfaces with the same security level. The ASA deniesby defaultt all traffic between intterfaces of the same security level (independent from any access-lists).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2022 06:35 PM - edited 05-24-2022 06:35 PM
Have you tried creating a static route on your ASA? Try creating this maybe this can help. just let me know
route INSIDE 192.168.0.0(your inside network subnet) 255.255.0.0(subnetmask) 192.168.1.1(your Layer3 gateway ip) 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2022 04:14 AM
Thank Herald,
it is a great idea.
The only problem I have now is, how to implement it,
i'm a student and not very experienced one,
that is why I learn from examples, and not so good with the idea on its own.
If you can demonstrate with example how and in which device to nest the commands,
it will be splendid.
Many Thanks
George
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2022 07:05 PM
are you using FMC? ASDM? FDM or pure CLI? let me know so i can show you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2022 04:03 AM
no special GUI
just Packet Tracer's user interface simulation
I use P/T for all my work, no real equipment involved
Thank you
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


