- Cisco Community
- Technology and Support
- Security
- Network Security
- NAT with 2 ISPs/2 different public IP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAT with 2 ISPs/2 different public IP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 04:23 AM - edited 03-11-2019 02:39 PM
Hi,
We have an issue with some NAT on an ASA 5510. Here is a simplified drawing of the ASA setup:
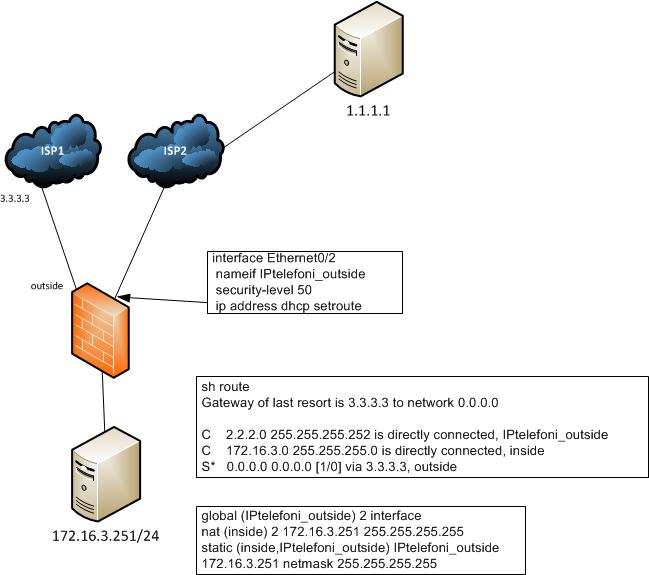
So the issue is when we try to send traffic from 172.16.3.251 to 1.1.1.1 we got this message in the log:
Oct 18 2011 12:32:12: %ASA-3-305006: portmap translation creation failed for udp src inside
172.16.3.251 /37166 dst outside:1.1.1.1/23
It looks like there is an issue with NAT but maybe is cause of the DUAL ISP setup as packets are routed through the outside interface and not IPtelefoni_outisde?
Thanks in advance for your help,
Laurent
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 04:29 AM
Thats absolutely correct, the return packets are being sent back from the outside interface, because the default route points to it. You can follow this thread and discussion between me and jon to understand wats needed:
https://supportforums.cisco.com/message/3465111#3465111
Let me know if you have any questions.
Thanks,
Varun
Varun Rao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 04:44 AM
Hi Varun,
Thanks a lot for your reply
Is the solution you are suggesting in the post valid for 8.2(2)?
************************************************************************
Your requirement is:
NAT rule - 67.111.140.10 -> 10.10.10.10
NAT rule - 67.222.140.10 -> 11.11.11.10
ISP 1 - static outside 67.111.140.X/24
ISP 2 - static outside 67.222.140.X/24
The servers needs to be accessed from two different ISP's
We can try this:
object network public_isp1
host 67.111.140.10
object network private_isp1
host 10.10.10.10
object network public_isp2
host 67.222.140.10
object network private_isp2
host 11.11.11.10
nat (ISP1,inside) source dynamic any interface destination static public_isp1 private_isp1
nat (ISP2,inside) source dynamic any interface destination static public_isp2 private_isp2
this way traffic coming from ISP2 would return from there only.
******************************************************************************************************************
Regards,
Laurent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 04:50 AM
No the one in the post is for post 8.3 software, I have not tested it with the ASA 8.2 software but it should work with that as well, although syntax would be different in that case.
Varun
Varun Rao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 05:09 AM
Ok. I will test in GNS3 and let you know. What is the alternative solution to your solution? Contexts?
Thanks.
/Laurent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 05:12 AM
Definitely yes, if this doesn't work then you can go for multiple contxets on ASA and connect different ISp on the contexts.
Varun
Varun Rao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 05:15 AM
Thanks a lot for your help Varun. I wil let you know how is going.
/Laurent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 05:56 AM
Sure no problem, I'll also test it in my lab and let you know the syntax required for it.
Varun
Varun Rao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 06:01 AM
Nice of you ;-)
/Laurent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 07:46 AM
Hi Varun,
I think I am waiting for your config as I have no idea how I could make the same config as yours in 8.2 ;-)
Looking forward to hearing from you.
/Laurent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 10:20 AM
Hi,
Ca you explain me once again, is the server on the internet and needs to be accessed inly from ISP2?
Wat traffic is it, i mean wat port you need to connect to?
Can you give me the following:
show run nat
show run global
show run static
show run route
show run interface
Varun
Varun Rao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2011 01:46 PM
Hi Varun,
Thanks for helping!
If you look at the drawing; what we want to achieve is one to one NAT between 172.16.3.251 and the outside public IP provided through DHCP by ISP2. So any type of traffic initiated by 172.16.3.251 should be natted to the outside DHCP public IP and any type of traffic from 1.1.1.1 destined to the outside DHCP public IP should be natted to 172.16.3.251
Any other type of traffic from the inside that is to say from any host in 172.16.3.0 /24 subnet should be natted to the outisde IP connected to ISP1 exept 172.16.3.251.
I hope I am not confusing you;-) Do you think it is possible to do apply your solution in 8.2? If not what do you suggest?
Looking forward to hearing from you.
Best regards,
Laurent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2011 11:06 AM
Hi Laurent,
I guess then, you can use this:
nat (ISP2) 5 0.0.0.0 0.0.0.0 outside
global (inside) 5 interface
static (inside,ISP2) interface 172.16.3.251
But doing this would block any other access on the ISP2 interface, like ssh or telnet.
You can also do port forwarding, where in you can just use ports like 80 and 443 required for the connection.
I haven't tried it but its the same concept as used in 8.3 or above.
Thanks,
Varun
Varun Rao
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2011 01:44 AM
Hi Varun,
So we found a solution. We simply added a route to host 1.1.1.1 as the customer only need ISP2 to connect to 1.1.1.1
Thanks a lot for your help. I will definitely keep your solution in mind for next time.
Best regards,
Laurent
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
