- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Need Help in Configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Need Help in Configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2013 02:25 AM - edited 03-11-2019 07:39 PM
Hello Everyone
I am new to ASA & I need some help to configure it (or say to solve my problem).
I am looking the answer for following qus. (Refer to diagram)
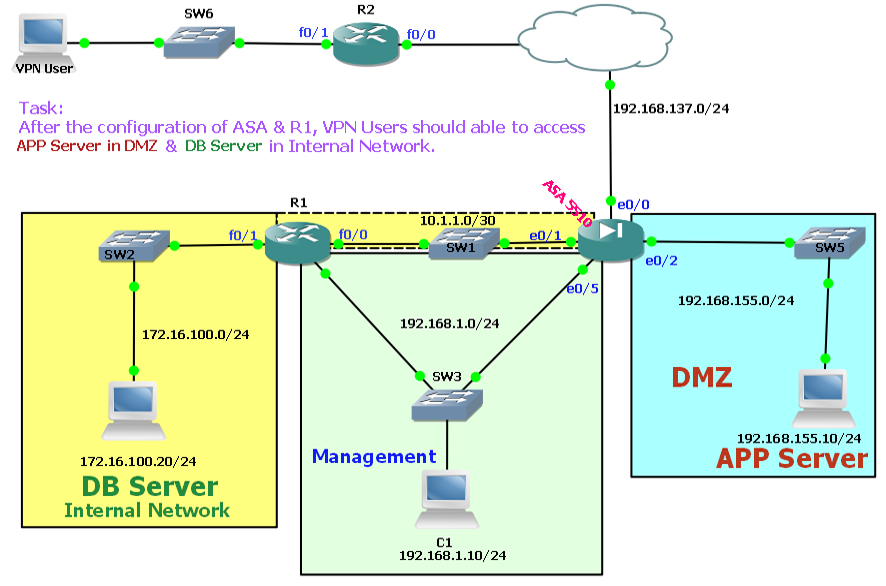
Q1) ASA 5510 is not able to ping directly connected router (R1) on int f0/0. But Router (R1) can ping to ASA (on int e0/1). I want my asa to ping router interface (on fa0/0.) How can I solve this problem?
Q2) As shown in pic there is some sort of DB server resides in internal network & client (office owner) don’t want to move DB Server into DMZ. Now the problem is VPN users can connect Application Server in DMZ Zone but they (VPN Users) are not able to connect DB Server in Internal network :wall: .
Router behind the ASA is configured as Zone Based firewall. but to check the connectivity, I removed the interfaces from Firewall Zones but still no success.
I am trying to emulate real networks in GNS. Configurations that I am running on Router & ASA are As below (& attached as well).
Thanks in Advance
ASA 5510 Configuration
-----------------------------------
: Saved
: Written by enable_15 at 09:06:32.029 UTC Tue Sep 17 2013
!
ASA Version 8.4(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
nameif outside
security-level 0
ip address 192.168.137.2 255.255.255.0
!
interface GigabitEthernet1
nameif inside
security-level 90
ip address 10.1.1.1 255.255.255.252
!
interface GigabitEthernet2
nameif dmz
security-level 80
ip address 192.168.155.1 255.255.255.0
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
nameif managment
security-level 100
ip address 192.168.1.2 255.255.255.0
!
ftp mode passive
object network NAT-PAT
subnet 10.1.1.0 255.255.255.252
object network NETWORK_OBJ_10.1.50.0_25
subnet 10.1.50.0 255.255.255.128
object network NETWORK_OBJ_192.168.155.0_24
subnet 192.168.155.0 255.255.255.0
access-list LAB-VPN-TU1_splitTunnelAcl standard permit 192.168.155.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
mtu dmz 1500
mtu managment 1500
ip local pool VPN-POOL 10.1.50.1-10.1.50.100 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (dmz,outside) source static NETWORK_OBJ_192.168.155.0_24 NETWORK_OBJ_192.168.155.0_24 destination static NETWORK_OBJ_10.1.50.0_25 NETWORK_OBJ_10.1.50.0_25 no-proxy-arp route-lookup
!
object network NAT-PAT
nat (any,outside) dynamic interface
route outside 0.0.0.0 0.0.0.0 192.168.137.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 192.168.1.0 255.255.255.0 managment
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ikev1 enable outside
crypto ikev1 policy 130
authentication crack
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 150
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
tftp-server managment 192.168.1.10 configuration
webvpn
group-policy LAB-VPN-TU1 internal
group-policy LAB-VPN-TU1 attributes
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value LAB-VPN-TU1_splitTunnelAcl
username cisco password 3USUcOPFUiMCO4Jk encrypted privilege 15
tunnel-group LAB-VPN-TU1 type remote-access
tunnel-group LAB-VPN-TU1 general-attributes
address-pool VPN-POOL
default-group-policy LAB-VPN-TU1
tunnel-group LAB-VPN-TU1 ipsec-attributes
ikev1 pre-shared-key cisco
!
!
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http
crashinfo save disable
Cryptochecksum:448032afabde680b07dd000e22804571
: end
R1 Configuration
----------------
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
no logging buffered
!
no aaa new-model
memory-size iomem 5
ip cef
!
ip domain name lab.local
ip name-server 8.8.8.8
ip name-server 8.8.8.8
!
multilink bundle-name authenticated
parameter-map type protocol-info yahoo-servers
server name scs.msg.yahoo.com
server name scsa.msg.yahoo.com
server name scsb.msg.yahoo.com
server name scsc.msg.yahoo.com
server name scsd.msg.yahoo.com
server name cs16.msg.dcn.yahoo.com
server name cs19.msg.dcn.yahoo.com
server name cs42.msg.dcn.yahoo.com
server name cs53.msg.dcn.yahoo.com
server name cs54.msg.dcn.yahoo.com
server name ads1.vip.scd.yahoo.com
server name radio1.launch.vip.dal.yahoo.com
server name in1.msg.vip.re2.yahoo.com
server name data1.my.vip.sc5.yahoo.com
server name address1.pim.vip.mud.yahoo.com
server name edit.messenger.yahoo.com
server name messenger.yahoo.com
server name http.pager.yahoo.com
server name privacy.yahoo.com
server name csa.yahoo.com
server name csb.yahoo.com
server name csc.yahoo.com
parameter-map type protocol-info msn-servers
server name messenger.hotmail.com
server name gateway.messenger.hotmail.com
server name webmessenger.msn.com
parameter-map type protocol-info aol-servers
server name login.oscar.aol.com
server name toc.oscar.aol.com
server name oam-d09a.blue.aol.com
parameter-map type regex ccp-regex-nonascii
pattern [^\x00-\x80]
crypto pki trustpoint TP-self-signed-998521732
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-998521732
revocation-check none
rsakeypair TP-self-signed-998521732
!
!
crypto pki certificate chain TP-self-signed-998521732
quit
!
!
username sabby privilege 15 password 0 simi
!
!
class-map type inspect imap match-any ccp-app-imap
match invalid-command
class-map type inspect match-any ccp-cls-protocol-p2p
match protocol edonkey signature
match protocol gnutella signature
match protocol kazaa2 signature
match protocol fasttrack signature
match protocol bittorrent signature
class-map type inspect match-all SDM_GRE
match access-group name SDM_GRE
class-map type inspect match-any CCP_PPTP
match class-map SDM_GRE
class-map type inspect smtp match-any ccp-app-smtp
match data-length gt 5000000
class-map type inspect match-any ccp-skinny-inspect
match protocol skinny
class-map type inspect http match-any ccp-app-nonascii
match req-resp header regex ccp-regex-nonascii
class-map type inspect match-any ccp-cls-insp-traffic
match protocol pptp
match protocol dns
match protocol https
match protocol icmp
match protocol imap
match protocol pop3
match protocol tcp
match protocol udp
class-map type inspect match-all ccp-insp-traffic
match class-map ccp-cls-insp-traffic
class-map type inspect match-any ccp-cls-icmp-access
match protocol icmp
match protocol tcp
match protocol udp
class-map type inspect match-any ccp-cls-protocol-im
match protocol ymsgr yahoo-servers
match protocol msnmsgr msn-servers
match protocol aol aol-servers
class-map type inspect match-all ccp-protocol-pop3
match protocol pop3
class-map type inspect match-any ccp-h225ras-inspect
match protocol h225ras
class-map type inspect pop3 match-any ccp-app-pop3
match invalid-command
class-map type inspect match-all ccp-protocol-p2p
match class-map ccp-cls-protocol-p2p
class-map type inspect match-any ccp-h323-inspect
match protocol h323
class-map type inspect match-all ccp-protocol-im
match class-map ccp-cls-protocol-im
class-map type inspect match-all ccp-icmp-access
match class-map ccp-cls-icmp-access
class-map type inspect match-all ccp-invalid-src
match access-group 100
class-map type inspect http match-any ccp-app-httpmethods
match request method bcopy
match request method bdelete
match request method bmove
match request method bpropfind
match request method bproppatch
match request method connect
match request method copy
match request method delete
match request method edit
match request method getattribute
match request method getattributenames
match request method getproperties
match request method index
match request method lock
match request method mkcol
match request method mkdir
match request method move
match request method notify
match request method options
match request method poll
match request method post
match request method propfind
match request method proppatch
match request method put
match request method revadd
match request method revlabel
match request method revlog
match request method revnum
match request method save
match request method search
match request method setattribute
match request method startrev
match request method stoprev
match request method subscribe
match request method trace
match request method unedit
match request method unlock
match request method unsubscribe
class-map type inspect match-any ccp-sip-inspect
match protocol sip
class-map type inspect http match-any ccp-http-blockparam
match request port-misuse im
match request port-misuse p2p
match request port-misuse tunneling
match req-resp protocol-violation
class-map type inspect match-all ccp-protocol-imap
match protocol imap
class-map type inspect match-all ccp-protocol-smtp
match protocol smtp
class-map type inspect match-all ccp-protocol-http
match protocol http
!
!
policy-map type inspect ccp-permit-icmpreply
class type inspect ccp-icmp-access
inspect
class class-default
pass
policy-map type inspect http ccp-action-app-http
class type inspect http ccp-http-blockparam
log
reset
class type inspect http ccp-app-httpmethods
log
reset
class type inspect http ccp-app-nonascii
log
reset
class class-default
policy-map type inspect smtp ccp-action-smtp
class type inspect smtp ccp-app-smtp
reset
class class-default
policy-map type inspect imap ccp-action-imap
class type inspect imap ccp-app-imap
log
reset
class class-default
policy-map type inspect pop3 ccp-action-pop3
class type inspect pop3 ccp-app-pop3
log
class class-default
policy-map type inspect ccp-inspect
class type inspect ccp-invalid-src
drop log
class type inspect ccp-protocol-http
inspect
service-policy http ccp-action-app-http
class type inspect ccp-protocol-smtp
inspect
service-policy smtp ccp-action-smtp
class type inspect ccp-protocol-imap
inspect
service-policy imap ccp-action-imap
class type inspect ccp-protocol-pop3
inspect
service-policy pop3 ccp-action-pop3
class type inspect ccp-protocol-p2p
drop log
class type inspect ccp-protocol-im
drop log
class type inspect ccp-insp-traffic
inspect
class type inspect ccp-h323-inspect
inspect
class type inspect ccp-h225ras-inspect
inspect
class class-default
policy-map type inspect ccp-permit
class class-default
policy-map type inspect ccp-pol-outToIn
class type inspect CCP_PPTP
pass
class class-default
drop log
!
zone security in-zone
zone security out-zone
zone-pair security ccp-zp-self-out source self destination out-zone
service-policy type inspect ccp-permit-icmpreply
zone-pair security ccp-zp-in-out source in-zone destination out-zone
service-policy type inspect ccp-inspect
zone-pair security ccp-zp-out-zone-To-in-zone source out-zone destination in-zone
service-policy type inspect ccp-pol-outToIn
zone-pair security ccp-zp-out-self source out-zone destination self
service-policy type inspect ccp-permit
!
!
!
!
!
interface FastEthernet0/0
description $FW_OUTSIDE$
ip address 10.1.1.2 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
interface FastEthernet0/1
description $FW_INSIDE$
ip address 172.16.100.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
interface FastEthernet1/0
ip address 192.168.1.1 255.255.255.0
duplex auto
speed auto
!
ip route 0.0.0.0 0.0.0.0 10.1.1.1
!
!
ip http server
ip http authentication local
ip http secure-server
ip nat inside source list 1 interface FastEthernet0/0 overload
!
ip access-list extended SDM_GRE
remark CCP_ACL Category=1
permit gre any any
!
access-list 1 permit any
access-list 100 remark CCP_ACL Category=128
access-list 100 permit ip host 255.255.255.255 any
access-list 100 permit ip 127.0.0.0 0.255.255.255 any
access-list 100 permit ip 10.1.1.0 0.0.0.3 any
!
control-plane
!
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2013 04:38 AM
Hi,
Q1:
policy-map type inspect ccp-permit
class class-default
---> no clause so default should be drop: ip inspect log drop-pkt and ping from ASA if this is the ZBF blocking then just modify this to not
drop the pings:
ip access-list extended FW_PING_ACL
permit icmp host 10.1.1.1 host 10.1.1.2 echo
class-map type inspect match-all FW_PINGS
match protocol icmp
match access-group name FW_PING_ACL
policy-map type inspect ccp-permit
class type inspect FW_PING
inspect
class class-default
drop log
Q2: could you explain further what is the problem and what you want to do
VPN users should be able to ping this server but can't but they can communicate with it anyway ?
VPN users can communicate with other machines in this subnet but they shouldn't ?
I don't understand the DMZ problem,as your topology this is a DMZ,no ?
Regards
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2013 06:14 AM
Thanks for reply
I just edited the first post pls have a look agian
Here is second problem
Client don’t want to move DB Server into DMZ. VPN users not able to connect DB Server in Internal Network. (but they are accessing Application Server in DMZ over VPN without any problem).
Thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
