- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2016 08:46 PM - edited 03-12-2019 01:11 AM
Hi,
I have a network existing like this:
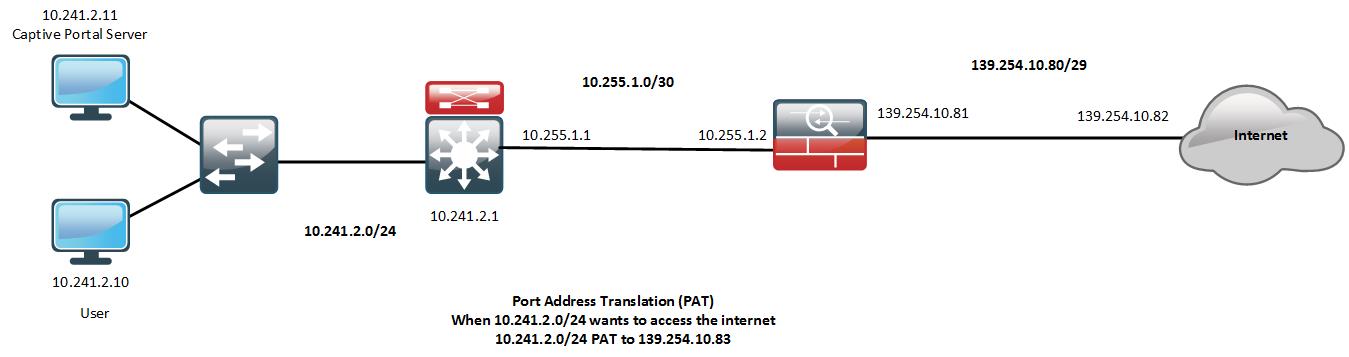
Now, I have a domain name called "reg.mydomain.com" and will be resolved to 139.254.10.84.
I need that domain name pointing to Captive Portal Server (10.241.2.11:38080), so when I access reg.mydomain.com:38080, it will show up the web page from 10.241.2.11:38080.
I did the static NAT from Cisco ASA:

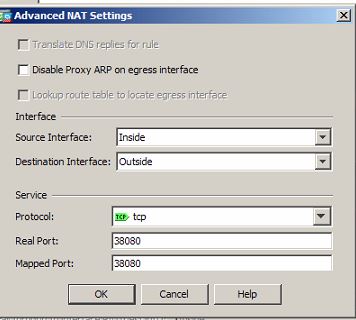
With the configuration of Static NAT, I can access the 139.255.10.84:38080 which will be translated to 10.241.2.11:38080 from other internet access (with different IP Public of 139.255.10.80/29).
But when I tried to access 139.255.10.84:38080 from the user inside firewall (10.241.2.10, which will be NAT PAT to 139.255.10.83 when access to internet), it always timed out. What is configuration that I missing in the Cisco ASA?
Thank you for your help.
Regards,
Arie
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2016 09:58 AM
Hello Arie,
A twice NAT, basically speaking would change both the source AND destination of the packet for example:
Original Pkt: Src:10.241.2.2 // Dst:139.254.10.84
NATed Pkt: Src: ASA "inside interface IP" // Dst: 10.241.2.11
The source change is necessary as this type of scenarios generally cause asymmetric routing.
In this case and if I understand correctly both the Client and the server would be located behind the inside interface; so the command "same-security-traffic permit intrainterface" is required as the traffic would be coming in and out the same interface.
Hence the NAT would look something like this:
object network obj-10.241.2.0_24
subnet 10.241.2.0 255.255.255.0
!
object network obj-10.241.2.11
host 10.241.2.11
!
object network obj-139.254.10.84
host 139.254.10.84
!
Nat (inside,inside) source dynamic obj-10.241.2.0_24 interface destination obj-139.254.10.84 obj-10.241.2.11
!
same-security-traffic permit intrainterface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2016 12:20 AM
hi,
DNS is UDP port 53.
could you change the protocol to UDP instead?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2016 03:29 AM
Hi,
Thanks for your reply. But, if I'm not using DNS, when I access 139.255.10.84:38080 from inside host (10.241.2.10), it's also not working.
If I access 139.255.10.84:38080 from other IP public or other outside host, then it's working.
Do you have any idea how to solve it first?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2016 01:09 PM
Hello Arie,
There is a couple of things you can do and some of them depend on the version and what you want to achieve. You can configure dns inspection so that the ASA would change the dns reply so that when the end host resolves the URL he gets the real (private) IP of the server.
Also you can configure the ASA to do a twice NAT which would basically make the ASA change the destinations from 139.254.10.84 ----> 10.241.2.11 but the configuations for this would depend on the version you are currently running.
Care to tell us what is the version?
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2016 06:41 PM
Hi,
The ASA Version is 9.4(2)11.
About twice NAT, so the first NAT is 10.241.2.11 ---> 139.254.10.84 and then the second NAT is from 139.254.10.84 ---> 10.241.2.11, is this correct?
If I do a twice NAT, what configuration do I need to do?
Thank you
Arie
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2016 09:58 AM
Hello Arie,
A twice NAT, basically speaking would change both the source AND destination of the packet for example:
Original Pkt: Src:10.241.2.2 // Dst:139.254.10.84
NATed Pkt: Src: ASA "inside interface IP" // Dst: 10.241.2.11
The source change is necessary as this type of scenarios generally cause asymmetric routing.
In this case and if I understand correctly both the Client and the server would be located behind the inside interface; so the command "same-security-traffic permit intrainterface" is required as the traffic would be coming in and out the same interface.
Hence the NAT would look something like this:
object network obj-10.241.2.0_24
subnet 10.241.2.0 255.255.255.0
!
object network obj-10.241.2.11
host 10.241.2.11
!
object network obj-139.254.10.84
host 139.254.10.84
!
Nat (inside,inside) source dynamic obj-10.241.2.0_24 interface destination obj-139.254.10.84 obj-10.241.2.11
!
same-security-traffic permit intrainterface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2016 08:09 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2016 02:16 PM
Hi Arie,
Are you currently having the high CPU with the config in place? U turning can cause high CPU, but that would depend on what type of inspections is the ASA doing.
Let me know,
Carlos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2016 07:39 PM
Hi,
Yes, I'm having the high CPU with the config in place. When I delete the config, it becomes normal.
I use the default inspection in the ASA:
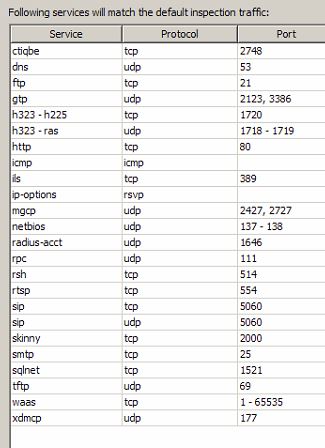


Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2016 02:05 AM
Hi,
I have implemented that configuration this morning and the afternoon I found out that the CPU utilization of ASA increase till 97%. Does that twice-NAT consume high CPU resource?
I have removed the configuration to see the CPU utilization and I found out the CPU utilization about 27%.
Thank you
Arie
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


