- Cisco Community
- Technology and Support
- Security
- Network Security
- Packet Tracer NAT fail - WTF?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2012 07:22 AM - edited 03-11-2019 03:42 PM
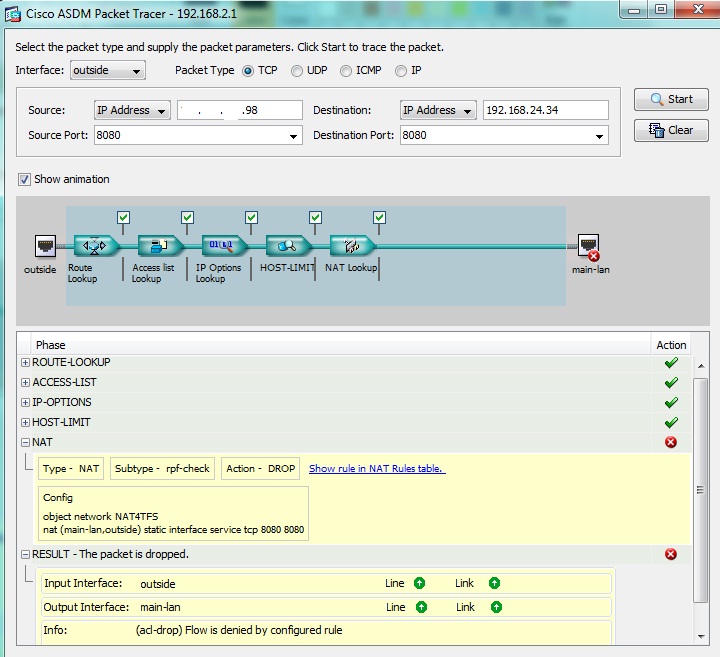
Before I changed all my service tcp objects from identifying both source and destination ports to simply SOURCE ports, and after I made the changes the packet trace was the same so that is not my issue.
Here is my latest runconfig. I was sure my NAT rules were right (8.43)
Saved
:
ASA Version 8.4(3)
!
hostname AgileDevelopment
enable password SrnWJ82Q9IsDq97j encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
switchport access vlan 12
!
interface Ethernet0/7
switchport access vlan 12
!
interface Vlan1
no forward interface Vlan12
nameif main-lan
security-level 100
ip address 192.168.24.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address ab.abc.def.230 255.255.255.248
!
interface Vlan12
nameif admin-dmz
security-level 100
ip address 192.168.2.1 255.255.255.0
!
ftp mode passive
clock timezone AST -2
clock summer-time ADT recurring
same-security-traffic permit inter-interface
object network obj_any_main-lan
subnet 0.0.0.0 0.0.0.0
description Applied by router ---> SNAT for main lan
object network TrustedInternetUsers
subnet ab.abc.def.0 255.255.255.0
object network Corporate-user
host .98
description Corp Ojbect for access to TFS, OM
object network 3-remote-h
subnet .0.0 255.255.0.0
object network 3-remote-w
subnet .0 255.255.255.0
object network 1-remote
host .4
object network 2-remote
host .133
object network ISP-GatewayIP
host ab.abc.def.225
object network VS-pcIP
host 192.168.24.34
object network obj_any-admin-dmz
subnet 0.0.0.0 0.0.0.0
description Used to apply SNAT for DMZ (internet access)
object service input-port
service tcp source eq www
object service OM1
service tcp source eq 5080
object service OM2
service tcp source eq 8088
object service OM3
service tcp source eq https
object service TFS
service tcp source eq 8080
object service RDP
service tcp source eq 3389
object service RouterAdmin
service tcp source eq 3334
object network NAT4OM3
host 192.168.24.34
object network NAT4OM1
host 192.168.24.34
object network NAT4OM2
host 192.168.24.34
object network NAT4RDP
host 192.168.24.34
object network NAT4TFS
host 192.168.24.34
object network NAT4WWW2OM1
host 192.168.24.34
object-group network Router-Admin
description Remote access to adjust router settings
network-object object 2-remote
network-object object TrustedInternetUsers
object-group network TFS-usergroup
description DND Access TFS, Open Meetings and RDP
network-object object TrustedInternetUsers
network-object object 3-remote-h
network-object object 3-remote-w
network-object object 1-remote
network-object object 2-remote
object-group service OMServiceGroup
service-object object OM1
service-object object OM2
service-object object OM3
object-group service CorporateServiceGroup
service-object object OM2
service-object object OM3
service-object object input-port
access-list outside_access_in remark Access to VS-TFS
access-list outside_access_in extended permit object TFS object-group TFS-usergroup object VS-pcIP
access-list outside_access_in extended permit object RDP object-group TFS-usergroup object VS-pcIP
access-list outside_access_in extended permit object TFS object Corporate-user object VS-pcIP
access-list outside_access_in remark Access to Open Meetings
access-list outside_access_in extended permit object-group OMServiceGroup object-group TFS-usergroup object VS-pcIP
access-list outside_access_in extended permit object-group CorporateServiceGroup object Corporate-user object VS-pcIP
access-list outside_access_in remark remote access to VS
pager lines 24
logging asdm informational
mtu main-lan 1500
mtu outside 1500
mtu admin-dmz 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
!
object network obj_any_main-lan
nat (main-lan,outside) dynamic interface
object network obj_any-admin-dmz
nat (admin-dmz,outside) dynamic interface
object network NAT4OM3
nat (main-lan,outside) static interface service tcp https https
object network NAT4OM1
nat (main-lan,outside) static interface service tcp 5080 5080
object network NAT4OM2
nat (main-lan,outside) static interface service tcp 8088 8088
object network NAT4RDP
nat (main-lan,outside) static interface service tcp 3389 3389
object network NAT4TFS
nat (main-lan,outside) static interface service tcp 8080 8080
object network NAT4WWW2OM1
nat (main-lan,outside) static interface service tcp 5080 www
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 ab.abc.def.225 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication enable console LOCAL
aaa authentication http console LOCAL
aaa authentication ssh console LOCAL
http server enable 3334
http server session-timeout 60
http 192.168.2.0 255.255.255.0 admin-dmz
http 192.168.24.0 255.255.255.0 main-lan
http .133 255.255.255.255 outside
http ab.abc.def.0 255.255.255.0 outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh 192.168.24.0 255.255.255.0 main-lan
ssh .133 255.255.255.255 outside
ssh ab.abc.def.0 255.255.255.0 outside
ssh 192.168.2.0 255.255.255.0 admin-dmz
ssh timeout 10
ssh version 2
console timeout 0
dhcpd address 192.168.24.5-192.168.24.10 main-lan
dhcpd dns ab.0.0.96 ab.0.0.97 interface main-lan
dhcpd enable main-lan
!
dhcpd dns ab.0.0.96 ab.0.0.97 interface outside
!
dhcpd address 192.168.2.5-192.168.2.10 admin-dmz
dhcpd dns ab.0.0.96 ab.0.0.97 interface admin-dmz
dhcpd enable admin-dmz
!
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 209.87.233.53 source outside
webvpn
username user5- password Xl5915GPBhncsPAQ encrypted
username user3- password mAVJxjP/lM8yc59F encrypted
username user4- password w7V/UFyrOwnQknqm encrypted
username user2- password .NJvJ7zi.ROsatP7 encrypted
username user1- password OZCdJRBWiCmcaFZ. encrypted
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:9cb5b5e2fb04a7c463aa077743174534
: end
no asdm history enable
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2012 08:23 AM
Problem solved.
Initially my service ports were both source and destination.
Upon advice I changed these all to source.
Today I tried changing them all to destination.
Why you ask, because when for giggles I wanted to recreate the rule I was testing in CLI - using putty, I simply modified the existing rule by using a default service (Citrex). Lo and behold for the first time I got a service rule that looked familiar.... ended with "eq citrix."
The moral, is CLI is for dummies but use it because it will help you in ASDM troubleshooting LOL.
(I then noticed all the default rules were set for destination)
I was able to change all my service ports to destination except ONE,, you guessed it the main one I was testing.
I kept getting ipv6 errors associated when trying to change it to destination. HOW WEIRD is that. So I deleted it and reinserted it.
Packet trace - good
Real test - success.
so service objects should all be shown on runconfig as.......
service tcp destination eq xxxx
Oh and by the way, my ACL rules did not change format. They were good the whole time, it was by service ports that were effed up.
Thanks for all your patience on round one, now the simple ipsec and ssl vpn saga begins. I hope to heck remote managment works LOL.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
