- Cisco Community
- Technology and Support
- Security
- Network Security
- PREFILTER ANALYZE VS FASTPATH
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
PREFILTER ANALYZE VS FASTPATH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2020 01:12 PM
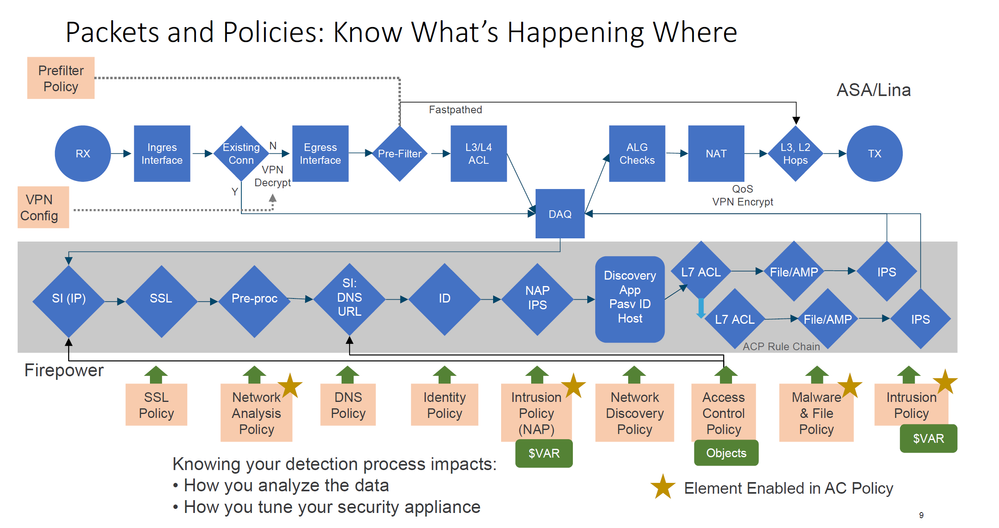
With Prefilter Fastpath, traffic bypasses inspection and is basically fastpathed out of the ftd device into what you may call a "toll bypass' hardware lane of some sort.
With Prefilter Analyze the traffic does not bypass inspection....the question is when the traffic returns from the "snort instance" inspection does it go into the "toll bypass" lane and out of the device or does it return and go through the other items such as Flow Update, ALG, QOS, ETC?
Thanks, Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2020 09:23 PM
If the packet was analyzed by Snort it will come out via DAQ into the ALG and subsequent steps like any normal fully analyzed packet.
Only if the prefilter action was Fastpath (or Drop of course) would it skip those steps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2023 06:25 AM
Hi @Marvin Rhoads so is Fast Path basically just using the outer header IP to allow/block the traffic? If we were to want the FTD to secure internal networks as much as possible would it be a good reason to not allow Fast Path (given let's say no performance issues or something)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2023 07:28 AM - edited 11-20-2023 07:28 AM
Fastpath will only be able to use the classic 5-tuple (protocol, source IP, source port, destination IP, destination port) like a legacy ASA. Known trusted flows (for instance bulk backup jobs or IPsec VPN traffic that terminates inside the firewall on some other device) can be added in the prefilter to bypass Snort altogether as a performance enhancement but it is recommended to use it sparingly.
But you are right:
"Prefiltering can be thought of as the first phase of access control before the firewall passes connections onto more resource-intensive evaluation controls. A prefilter policy uses limited, outer-header criteria to process connections quickly. The rule actions available in a prefilter policy are Fastpath, Block and Analyze.
The Fastpath rule action in the prefilter policy bypasses all further packet inspection and handling, including security intelligence, authentication requirements, SSL decryption, access control rules, deep inspection (IPS), network discovery and rate limiting."
Reference: https://secure.cisco.com/secure-firewall/v7.2/docs/access-control-policy
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


