- Cisco Community
- Technology and Support
- Security
- Network Security
- From what I can tell,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Rapid7 connector problems and the latest LWP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2014 09:39 AM - edited 03-12-2019 05:35 AM
I have a question about an issue with LWP and the Rapid7 Connector.
Here is a snippet of whats going on:
Script Output:
<omitted>:[/opt/rapid7/nexpose/sourcefire_connector]# ./rapid7_connector.pl -csvfile=output.txt -plugininfo=InputPlugins/Nexpose.yaml
Wed Nov 19 14:43:08 2014 [INFO] NeXpose Report Processing Starting
Wed Nov 19 14:43:08 2014 [INFO] Site ID: <omitted>
Wed Nov 19 14:43:08 2014 [ERROR] Login response: Can't connect to <omitted>:3780 (certificate verify failed)
LWP::Protocol::https::Socket: SSL connect attempt failed error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed at /usr/lib/perl5/site_perl/5.8.8/LWP/Protocol/http.pm line 49.
Error : Login failed!
#Uname –a
Linux <omitted> 2.6.18-371.11.1.el5 #1 SMP Mon Jun 30 04:51:39 EDT 2014 x86_64 x86_64 x86_64 GNU/Linux
#cat /etc/redhat-release
Red Hat Enterprise Linux Server release 5.10 (Tikanga)
What we have attempted to do is set a Bash Environment variable like so:
export PERL_LWP_SSL_VERIFY_HOSTNAME=0
I've also done things like try and set it inside the perl scripts:
$ENV{'PERL_LWP_SSL_VERIFY_HOSTNAME'} = 0;
I've been doing this based on this type of research:
http://stackoverflow.com/questions/17756776/perl-lwp-ssl-verify-hostname-setting-to-0-is-not-working
Looks like as of LWP 5.8 or so the Verification of Hostname went from 'not required', 'disabled', or '0', to '1' or enforced.
I wasn't sure if others have seen this also?
- Labels:
-
NGIPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2014 01:55 PM
I'm seeing basically the exact same issue. Only difference is the build of linux, 2.6.18-274.17.1.el5 #1. You didn't happen to get a solution, did you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2016 08:07 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2016 08:00 PM
From what I can tell, something changed in how LWP validates certificates, at least on Linux (the issue doesn't seem to affect Windows). The fix I used was to add the root CA certificate for the Nexpose console to the trusted root certificate store.
For a Ubuntu/Debian based system:
1. Export the root certificate used for the Nexpose console. If you haven't done this before, here is a screenshot to point you in the right direction:
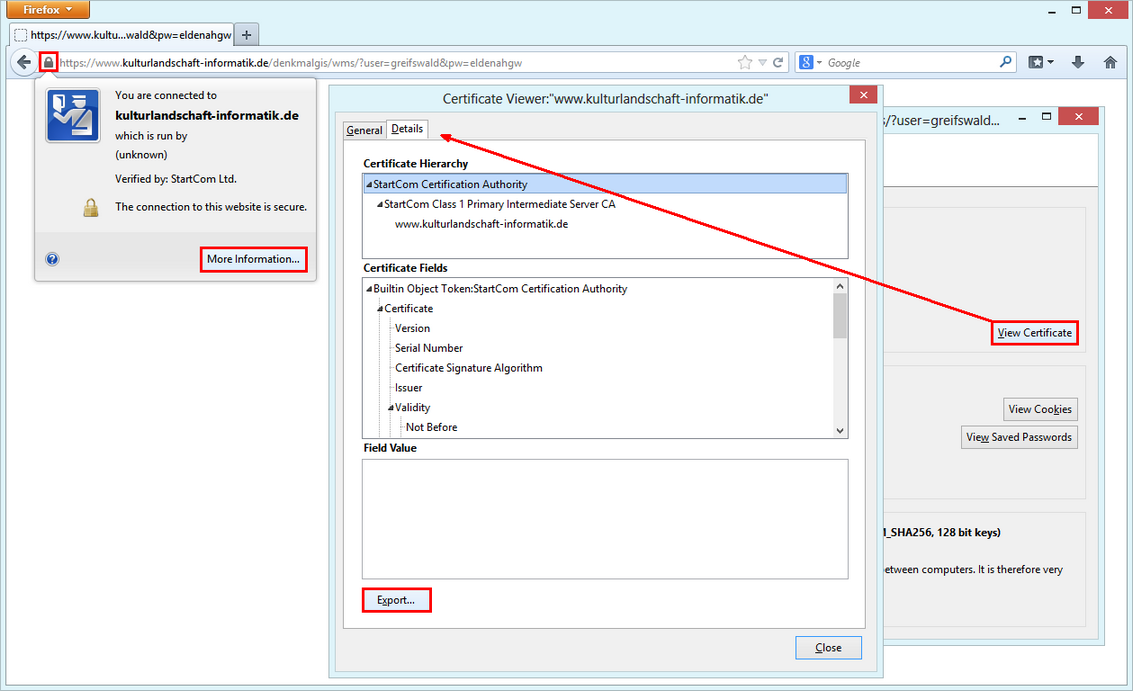
2. Copy the root certificate to the ca-certificates folder on the system hosting the connector:
sudo cp nexposeconsoleroot.crt /usr/local/share/ca-certificates/
3. Update the CA store:
sudo update-ca-certificates
4. The connector should now work.
If you want to remove the added root certificate:
sudo rm /usr/local/share/ca-certificates/nexposeconsoleroot.crt
sudo update-ca-certificates --fresh
For non-Debian based systems, commands to add root certificates on other platforms can be found here:
https://briansnelson.com/How_to_add_trusted_root_certificates
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
