- Cisco Community
- Technology and Support
- Security
- Network Security
- Security flaws of NAT over the Edge Router vs the Firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Security flaws of NAT over the Edge Router vs the Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2021 08:58 PM - edited 06-30-2021 11:09 PM
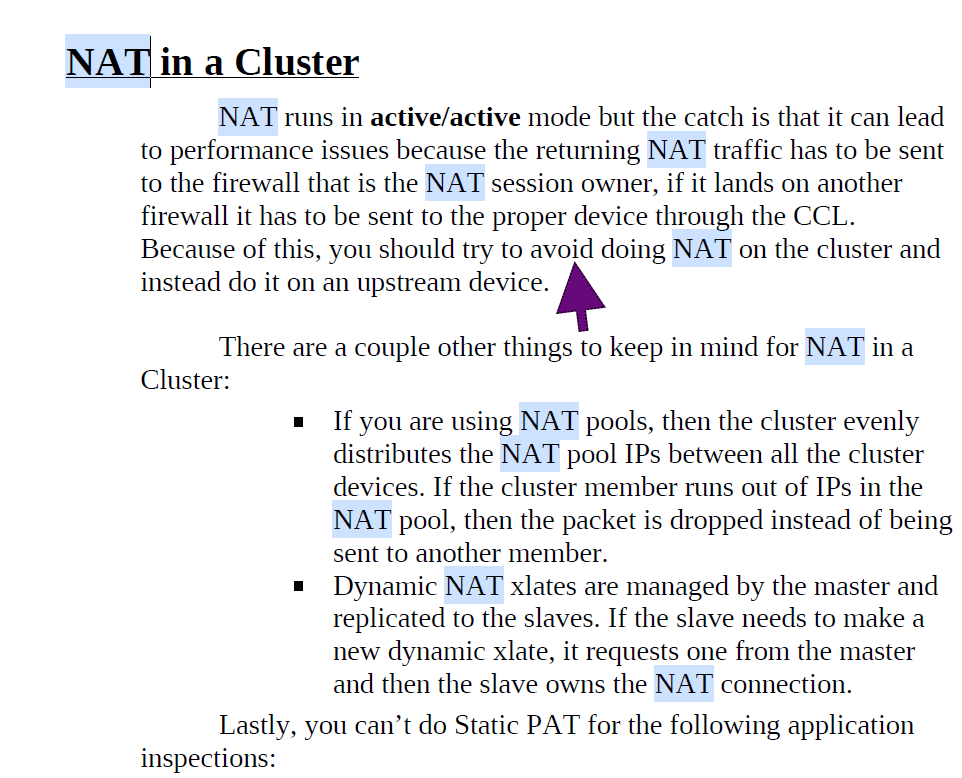
In a FPR Clustered Deployment Scenario due to the performance issues you're not supposed to do the NAT over the firewall cluster
Sources:
BRKSEC-3032 and CCNP Security SNCF 300-710
if we decide to do the recommendation here, and do the NAT on an ASR-9K instead, what kind of attacks can be done on the router who is doing the NAT here?
one could be denial of service, and
one type of DDoS(Layer 3) is the NAT attack, for eating up your NAT/PAT pool, although this type of attack can only take place when the connection is initiated from outside first..
that can be mitigated by a feature called vDDoS on an ASR-9K, what other kind of attacks can take place if we're not doing nat over the Firepower vs. an ASR router?
and don't get me wrong our network is currently running the NAT(overload PAT) over the ASR-9906 and I haven't bought the vDDoS license yet, and it's been like this for 5 month now, we haven't experienced any attacks yet...
one reason that we haven't experienced any DDos attacks yet, is because we have private customers, but our IP can be searched in range attacks
no need to mention, we have a very high bandwidth uplink(above 30G), and we need very low latency for our environment since it's too big and our customers!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2021 02:05 PM
Hi,
NAT with pat-pools with fewer PAT IPs than cluster members could cause traffic outages when the master role switches.
If there are more cluster units than there are global IP addresses in the pat-pool used for NAT. This can cause traffic failures if the master role changes and the new master has no IP address, or when additional units are added to the cluster.
You can have ASA/FTD on cluster with PAT IPs equal to the number of units in the cluster.
The above rules have changed in versions starting releases 9.15 and 6.7
https://www.cisco.com/c/en/us/td/docs/security/asa/asa915/release/notes/asarn915.html
Regards,
Chakshu
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2021 03:17 PM - edited 06-30-2021 09:40 PM
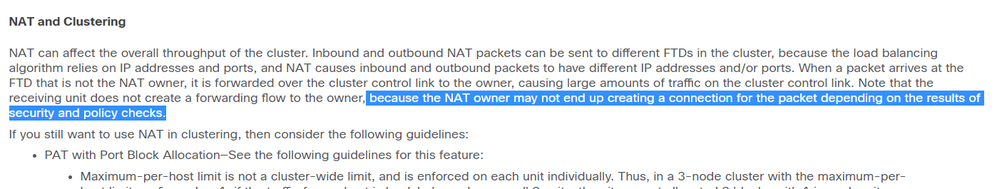
I haven't looked at the link you provided yet, but from what I understand, you're referring to the failure portion of the scenario like "what if the concurrent pat translations exceed the random port ranges assigned to each cluster member or what if one unit fails", however I am asking about what if there won't be any failures or there are sufficient port number to do overloaded pat on, but I am asking about the performance aspect, if the traffic comes back from outside and doesn't hit the owner of that xlate traffic needs to punted to the owner for translation(even if we're using data spanned etherchannel trunk), and that can cause asymmetry or latency?! or that's not the case?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2021 09:37 PM - edited 07-01-2021 11:35 AM
Deploying a Cluster for Firepower Threat Defense for Scalability and High Availability - Cisco
Hello Again
an update...
I guess inconsistent hashing on outgoing vs ingoing flows is inevitable, unless Cisco comes up with a protocol that sync the xlate owner between the Nexus 7k and FTD cluster, so packets would be punted to the right unit on its way back.
Another workaround could be if we bundle the inside ports together and separate from outside ports together, and on etherchannel we use dst ip-l4port and on the other etherchannel we use src ip-l4port, this way traffic always hit the same member in both direction, since we aren't using the combination of src-dst and we're not bundling the both outside inside interfaces together, load balancing can't be that good, but It should be around 40 to 60% ratio, hence not all users are only going to one internet server..
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide