- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Site-to-Site VPN config issues on Firepower FTD 6.3 (Firepower 2140)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2020 03:05 PM - edited 02-21-2020 09:53 AM
Hello All,
I am configuring a new Firepower 2140 appliance and in order to connect it to our FMC I have first to create a VPN, through the FTD 6.3 management interface, to reach the FMC console!
I have managed to create the tunnel and the NAT to go along with the site to site VPN (the other end of the tunnel is an ASA 5555x). When I ping or try to access anything from the peer network (ASA 5555x side) I get the phase 1 of the VPN up, so the VPN tunnel connects but then when the local VLANs try to talk I see the traffic leaving (Tx) the 5555x firewall but I never get a reply (Rx) from the other end of the tunnel (Firepower 2140).
Reading the documentation, on the Firepower 2140 side I either have to create an Extended Access List on the Smart CLI Objects allowing the desired VLANs, already defined as Local and Remote Network under the Site-to-site VPN configuration, or I have to enable sysopt connection permit-vpn under FlexConfig. Unfortunately it seems there is no guide to explains the details of those steps from the FTD console. All the guides I found are for FCM, which I cannot access unless I setup the site-to-site VPN!
I have managed to create the access list, but I cannot see how can I apply/associate the specific access list in FTD to the specific site-to-site VPN. Also I cannot figure out the exact way to configure sysopt connection permit-vpn under FlexConfig. If anyone can help out on either or both I would be grateful!
Thanks!
If this was helpful, please vote as helpful by clicking on the star icon below.
-------------------------------------
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2020 10:33 AM
@Marvin Rhoadsis correct, you need to amend your NAT rules. The original and translated source would be VPN-Local-NETS, the original and translated destination would be VPN-Remote-NETS. The end result, traffic from VPN-Local-NETS to VPN-Remote-NETS would not be natted. The output of show run would look something like this, changes in bold:-
nat (inside,outside) source static VPN-Local-NETS VPN-Local-NETS destination static VPN-Remote-NETS VPN-Remote-NETS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2020 11:32 AM
Hello RJI,
I have amended this!
nat (inside,outside) source static VPN-Local-NETS VPN-Local-NETS destination static VPN-Remote-NETS VPN-Remote-NETS
I also had to amend the Access Control Policy and this is the only setting that would allow comms both ways:
If this was helpful, please vote as helpful by clicking on the star icon below.
-------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2020 03:12 PM
You do not need to create an Extended ACL nor enable sysopt, you control access over the VPN tunnel using rules defined in the Access Control Policy.
Another common issue with VPNs is you need to ensure that traffic between the local and remote networks is not natted by using a NAT exemption rule.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2020 04:04 PM
Hello RJI,
Thanks for your swift reply!
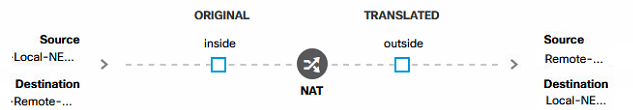
So, I have not ticked the NAT except on either side of the tunnel and I have created static bidirectional NAT on each firewall. Here is how it looks on the Firepower Appliance:
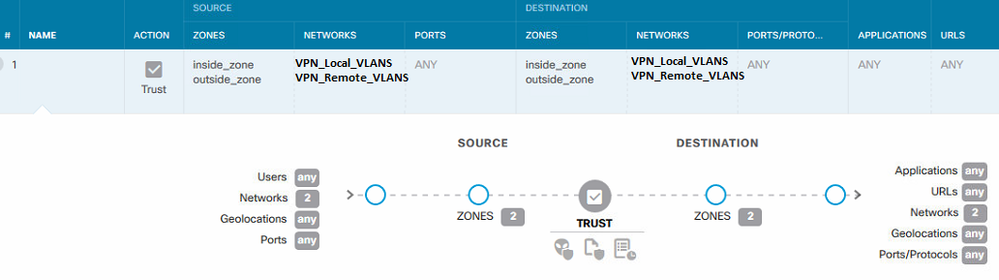
Also for the access policy I have created a separate Trusted policy for the VPN nets that I have placed above my normal Access Control Policy. Note inside_zone, is the inside interface and outside_zone is the outside interface:
Sorry if I sound a bit new to this but I have been working with ASA and Firepower over FMC for years, but this is the first time I use FTD.
Thanks.
If this was helpful, please vote as helpful by clicking on the star icon below.
-------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2020 07:15 PM
I'd check into routing.
Do the VLANs behind the remote Firepower 2140 have its inside interface as the gateway for the return traffic to the main site?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2020 06:19 AM
Hello Marvin,
Thanks for your response.
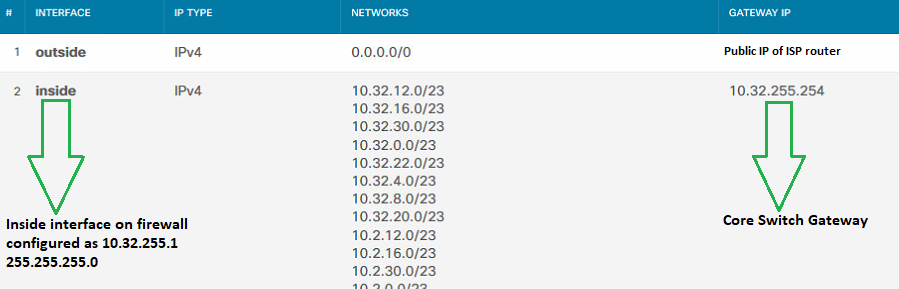
I can confirm that the outside interface has a route pointing to the ISP router (public IP) and the inside interface routes all local VLANs reconfigured on the core switch to the core switch. Note that the VLANs configured on the core switch can ping the internet.
If this was helpful, please vote as helpful by clicking on the star icon below.
-------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2020 08:38 AM
Ok, the routing looks good.
On your earlier post where you shared the NAT setup, it appears you may have on the "Translated" side have the networks reversed. You want Translated source and destination to be the same as Original. From what I can see in the GUI it tells Firepower to swap them. Can you verify with the cli output of "show running-configuration nat"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2020 08:52 AM
Hey Marvin,
Here is the output for show running-config nat:
nat (inside,outside) source static VPN-Local-NETS VPN-Remote-NETS destination static VPN-Remote-NETS VPN-Local-NETS
For the record, Local are the VLANs on the side of the Firepower and Remote are the Peer VLANs on the other site.
Thanks,
If this was helpful, please vote as helpful by clicking on the star icon below.
-------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2020 10:33 AM
@Marvin Rhoadsis correct, you need to amend your NAT rules. The original and translated source would be VPN-Local-NETS, the original and translated destination would be VPN-Remote-NETS. The end result, traffic from VPN-Local-NETS to VPN-Remote-NETS would not be natted. The output of show run would look something like this, changes in bold:-
nat (inside,outside) source static VPN-Local-NETS VPN-Local-NETS destination static VPN-Remote-NETS VPN-Remote-NETS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2020 11:32 AM
Hello RJI,
I have amended this!
nat (inside,outside) source static VPN-Local-NETS VPN-Local-NETS destination static VPN-Remote-NETS VPN-Remote-NETS
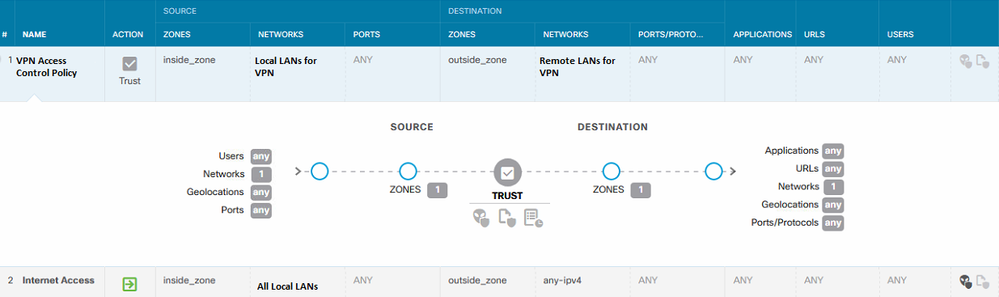
I also had to amend the Access Control Policy and this is the only setting that would allow comms both ways:
If this was helpful, please vote as helpful by clicking on the star icon below.
-------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2021 02:05 AM
Same Problem on 1010 managed with FDM...
Console output:
INFO: It is recommended that you enable sysopt connection permit-vpn when enabling IKEV1
INFO: It is recommended that you enable sysopt connection permit-vpn when enabling IKEV2
but in the FDM is no field to switch in on (Software 6.6.1)
Can someone help?
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2021 02:20 AM
Hi @BURKHARD LANDWEHR You can use FlexConfig to deploy that command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2021 02:24 AM
In the FDM I can´t find any point like flex config, can you explain that? Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2021 02:29 AM
Under DEVICE tab, Flexconfig is under Advanced configuration. You just need to define the old ASA commands under the Flexconfig object, then reference that object under the Flexconfig Policy and deploy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2021 03:38 AM
Ist a FTD 1010 not an old ASA... is this the Problem? I am using the FDM not ASDM?!? there is no device TAB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2021 03:45 AM
Sorry I Found it thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide