- Cisco Community
- Technology and Support
- Security
- Network Security
- SOLVED: ASA5506 - Internal network not routed via public PPPoE interface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SOLVED: ASA5506 - Internal network not routed via public PPPoE interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2019 04:15 AM - edited 02-21-2020 09:16 AM
Hi,
we're having a problem with out ASA5506.
The public interface "outsideSub" has internet connection via PPPoE.
The ping test to a public DNS server from the outsideSub iface is successful.
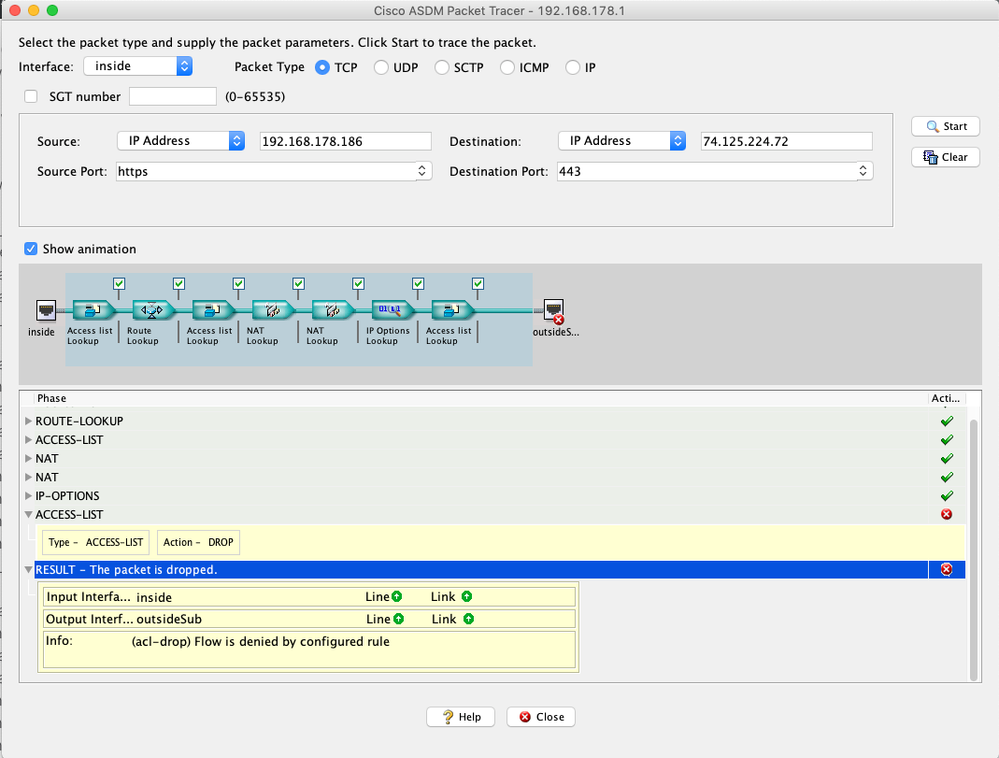
However, the package trace shows that TCP packets are blocket using an ACL.
Also, hosts in the internal subnet do not have internet connection.
This is the current config:
: Saved
:
: Serial Number: JAD211802J4
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
: Written by admin at 12:07:48.259 CEDT Thu Jul 4 2019
!
ASA Version 9.6(1)
!
hostname firewall
enable password WHzrdccdxogzFJXY encrypted
names
!
interface GigabitEthernet1/1
nameif outside
security-level 0
no ip address
!
interface GigabitEthernet1/1.100
nve-only
vlan 7
nameif outsideSub
security-level 0
pppoe client vpdn group telekom
ip address pppoe
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address dhcp
!
interface GigabitEthernet1/3
nameif DMZ
security-level 50
ip address 192.168.3.1 255.255.255.0
!
interface GigabitEthernet1/4
nameif guest
security-level 1
ip address 192.168.5.1 255.255.255.0
!
interface GigabitEthernet1/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
shutdown
no nameif
no security-level
no ip address
!
interface Management1/1
management-only
no nameif
no security-level
ip address dhcp
!
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
dns domain-lookup outsideSub
dns server-group DefaultDNS
name-server 217.69.169.25 outsideSub
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network insideSub
object network WWW-EXT
host 87.140.26.169
object network WWW-INT
host 192.168.3.2
object service https
service tcp source range 0 1024 destination eq https
object network internal-webserver
host 192.168.3.2
object network dect-gateway
host 192.168.178.15
object service http
service tcp source eq www destination eq www
description http
object-group service DM_INLINE_SERVICE_1
service-object tcp-udp destination eq sip
service-object tcp destination eq www
service-object tcp destination eq https
object-group service DM_INLINE_SERVICE_2
service-object udp
service-object tcp destination eq sip
service-object udp destination eq sip
service-object tcp destination eq 5090
service-object tcp destination eq https
service-object tcp destination eq www
service-object udp destination range 30000 31000
service-object udp destination eq 3478
service-object udp destination eq 3479
service-object udp destination range 40000 41000
object-group service DM_INLINE_SERVICE_3
service-object udp
service-object tcp destination eq sip
service-object udp destination eq sip
service-object tcp destination eq https
service-object tcp destination eq 5090
service-object udp destination range 30000 30900
service-object udp destination range 40000 40900
service-object udp destination eq 5070
service-object udp destination eq 5080
object-group service DM_INLINE_SERVICE_6
service-object tcp destination eq https
service-object tcp-udp destination eq domain
service-object tcp destination eq www
object-group service DM_INLINE_TCP_1 tcp
port-object eq www
port-object eq https
object-group service DM_INLINE_TCP_2 tcp
port-object eq www
port-object eq https
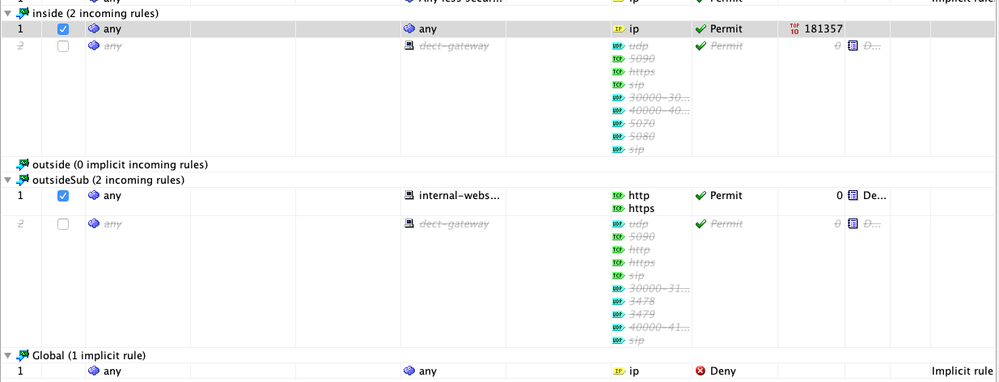
access-list inside_access_in extended permit ip any any
access-list inbound extended permit tcp any object internal-webserver object-group DM_INLINE_TCP_2 log debugging
access-list inbound extended permit object-group DM_INLINE_SERVICE_2 any object dect-gateway log debugging inactive
access-list DMZ_access_in extended permit tcp any object internal-webserver object-group DM_INLINE_TCP_1
access-list DMZ_access_in extended permit object-group DM_INLINE_SERVICE_6 object internal-webserver any
access-list DMZ_access_in extended permit ip any any inactive
access-list inside_access_in_1 extended permit ip any any
access-list inside_access_in_1 extended permit object-group DM_INLINE_SERVICE_3 any object dect-gateway log debugging inactive
access-list guest_access_in extended permit ip any interface outsideSub
access-list telefon_access_in extended permit object-group DM_INLINE_SERVICE_1 any any
pager lines 24
logging enable
logging asdm informational
mtu outside 1492
mtu outsideSub 1492
mtu inside 1500
mtu DMZ 1500
mtu guest 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
!
object network obj_any
nat (any,outsideSub) dynamic interface
object network internal-webserver
nat (DMZ,outsideSub) static interface service tcp https https
!
nat (inside,outsideSub) after-auto source dynamic any interface
nat (DMZ,outsideSub) after-auto source dynamic any interface
nat (guest,outsideSub) after-auto source dynamic any interface
access-group inbound in interface outsideSub
access-group inside_access_in_1 in interface inside
access-group DMZ_access_in in interface DMZ
route outsideSub 0.0.0.0 0.0.0.0 87.140.26.169 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.178.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=192.168.178.1,CN=firewall
keypair ASDM_LAUNCHER
crl configure
crypto ca trustpool policy
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
certificate 213f335c
308202d2 308201ba a0030201 02020421 3f335c30 0d06092a 864886f7 0d010105
0500302b 3111300f 06035504 03130866 69726577 616c6c31 16301406 03550403
130d3139 322e3136 382e3137 382e3130 1e170d31 39303231 31303831 3332345a
170d3239 30323038 30383133 32345a30 2b311130 0f060355 04031308 66697265
77616c6c 31163014 06035504 03130d31 39322e31 36382e31 37382e31 30820122
300d0609 2a864886 f70d0101 01050003 82010f00 3082010a 02820101 00b8ce18
cf8bf6f6 dd3ee4fb a4dfe76c 4fe03a80 f81cd905 e46d54f9 f012b3ef a7b1b18e
986a25c1 72e2958e 358069bc 19cb4f82 6c64ae3e 093c5728 d459f866 6f96236a
510542c1 31fa49da 3abda6f9 9fd94928 f50cd6e4 0efd84e7 347f347b 599cffe4
ffc329ab 20e73469 4eea0f70 eccbbfe9 8b836d74 308d2726 141b774e bfc67f7b
01fd29f3 95270e96 1f772697 f860eb11 7e0686a7 d3a67ddf 1bc9d1f1 dfd8e56b
0dd0383b 77450eae d40e73b1 42eaa054 bdf1df88 bce74fa3 786577f4 761e2bb5
a7a64f7f bd438ccd a17fb35c 2259eb15 6e7fae71 41f7a8f2 1bcf7de0 1d681b31
67c3accc 8f335083 c1c785aa 287efa1b 001f9364 9ca24063 1df21744 0d020301
0001300d 06092a86 4886f70d 01010505 00038201 010005c6 2bb39f28 b70fc7f0
a36607a8 2548e727 f15ac207 fb9158dc 2d40b205 01bbdfca a400a80d f7ceddf9
9e970bb2 1ea6f27c 5abf5213 36c6e0bb da17f51f 11b57d6a 1a23d549 1da464b0
4eb0b2a9 8930c91d c4cab838 0467fe35 222fe4b1 8b1341a6 ea83f447 f415300e
c1d4307e 3ae79b83 99800943 6a1dfd1c 22f3313b cc16ad04 852268b0 d028aa16
b50ce50a bc6b7060 db1e01c4 c76395b4 cdfee801 a1d3a9f4 74398b92 cba196cf
8fca0659 305b10f7 fee4e90a 00ec7220 6401044c c20cd391 74cd12db acc1427f
d6d5f324 f5b15a43 b97eb21e 07fac702 81aed9a9 1828acae 91702b57 994e3618
3c2e2e50 55bb0fc3 18da4c73 399d0c17 830a9389 b679
quit
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.178.0 255.255.255.0 inside
ssh timeout 5
ssh key-exchange group dh-group14-sha1
console timeout 0
vpdn group telekom request dialout pppoe
vpdn group telekom ppp authentication pap
dhcpd dns 217.69.169.25
dhcpd auto_config inside
dhcpd option 3 ip 192.168.5.1
!
dhcpd address 192.168.5.2-192.168.5.254 guest
dhcpd dns 217.69.169.25 interface guest
dhcpd enable guest
!
ntp server 188.68.54.53 source outsideSub
ssl trust-point ASDM_Launcher_Access_TrustPoint_0
dynamic-access-policy-record DfltAccessPolicy
username admin password WRN6n6ecK1px5qbL encrypted privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:2e518b4508919eb399ce4cb4eae31eca
: end
Here are two screenshots to clearify the problem/configuration:
The NAT rules or routes were not changed explicitly!
The only change that has been done was changing the internalSub PPPoE setting to "use a static IP".
We did not have internet connection with the static IP, so we switched the iface setting back to PPPoE.
Ever since, the NATing/routing problem exists.
Unfortunately, there are no configuration backups and the config was written to flash...
We'd really appreciate your help!
EDIT: The issue was that "VTEP source interface" was checked in the virtual interface settings.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide