- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: SSH Configuration , Outside Interface, Cisco Firepower 1100 Series
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 05:14 AM - edited 02-03-2023 05:20 AM
Hi
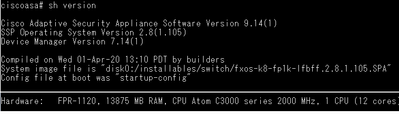
I have a Cisco Firepower 100 Series (1120).
System image file is "disk0:/installables/switch/fxos-k8-fp1k-lfbff.2.8.1.105.SPA"
Hardware: FPR-1120, 13875 MB RAM, CPU Atom C3000 series 2000 MHz, 1 CPU (12 cores)
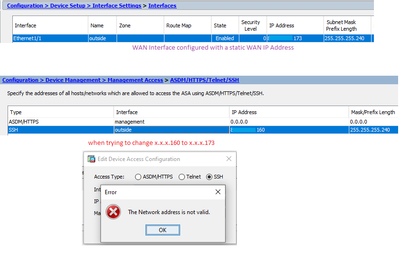
I am trying to enable the SSH and has configured the WAN /Outside Interface and default route as well (route outside 0 0 xx.yy.zz).
Problem: Now when I finished with SSH configuration, I can't SSH to the device, even not being asked for user /Password authentication. And one thing I noticed is that WAN address is modified and same as WAN/Outside interface which I configured statically.
And when I try to edit it, I cannot as it show message of incorrect IP Address, see below:
My WAN IP address ends in 173 while under SSH it's changed to 160.
Note: The IP Address is verified, was working fine with a different device in past.
| Config t crypto key generate rsa modulus 2048 aaa authentication ssh console LOCAL ssh version 2 ssh 8x.yy.zz.173 255.255.255.240 Outside ssh timeout 30 |
route outside 0 0 8x.yy.zz.161 |
aaa authentication ssh console LOCAL |
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 11:43 AM
No problem. Let's break it down a bit.
- Your WAN Outside interface IP is 8x.yy.zz.173/28 (subnet mask 255.255.255.240)
- The subnet ID of that IP is 8x.yy.zz.160/28 as pointed by @Marvin Rhoads
- You want to allow SSH to the firewall via Outside interface
The firewall shows the IP 8x.yy.zz.160/28 in the SSH section because you issued the command "ssh 8x.yy.zz.173 255.255.255.240 Outside". The command you issued has the subnet mask 255.255.255.240, because of this the firewall converts the IP address 8x.yy.zz.173 into the subnet ID which is 8x.yy.zz.160/28. This is why! If you want to see the IP 8x.yy.zz.173 in the SSH section, then you need to remove the command "ssh 8x.yy.zz.173 255.255.255.240 Outside" and replace it with "ssh 8x.yy.zz.173 255.255.255.255 Outside", so you need to change the last octet in the subnet mask from 240 to 255.
However, as I mentioned before, the command "ssh ... Outside" is used to define the source IP addresses or subnet that are allowed to SSH to the firewall, obv they still need to authenticate before they are allowed accesses to the firewall.
So, if you change the command "ssh 8x.yy.zz.173 255.255.255.240 Outside" to "ssh 8x.yy.zz.173 255.255.255.255 Outside" it means that the firewall will only accept the SSH connections from the IP 8x.yy.zz.173, but this will never happen as the IP 8x.yy.zz.173 is the firewall WAN interface itself, and the SSH connections would never source from that IP.
What you would need to do to get this to work is just changing the IP 8x.yy.zz.173 in the command "ssh 8x.yy.zz.173 255.255.255.240 Outside" to the source public IP that you will use to source the SSH traffic from.
If you want to widely allow the firewall to accept the SSH connections from anywhere which is not really recommended, then you can swap the command "ssh 8x.yy.zz.173 255.255.255.240 Outside" with "ssh 0 0 Outside". The best security practice in this case would be to define the public IP addresses that would source the SSH traffic, example:
"ssh 1.2.3.4 255.255.255.255 Outside"
"ssh 10.20.30.40 255.255.255.255 Outside"
"ssh 100.200.3.4 255.255.255.255 Outside"
and so on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 06:48 AM
Not sure why you see those IP addresses changed on the ASDM, does it do the same if you look at the config from the CLI?
Also, the command "ssh 8x.yy.zz.173 255.255.255.240 Outside" should define the source network or IP address that will be allowed to connect to the firewall via SSH. For example, if your home public IP is 1.2.3.4 and you want to allow it to SSH into the firewall, then that command should look like this:
ssh 1.2.3.4 255.255.255.255 Outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 07:21 AM
@Aref Alsouqi thanks for reply.
YES, same results from CLI.
Have following command already in the configuration.
ssh 8x.yy.zz.173 255.255.255.240 Outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 08:37 AM
You're welcome. You would need to remove that command and replace it with whatever IP addresses or subnet you want to allow to SSH into the firewall as in my previous example. If you want to allow SSH from anywhere in the world then you can replace that command with the following:
ssh 0 0 Outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 11:17 AM
@Aref Alsouqi thanks for followuo.
Let's solve this first:
ssh 8x.yy.zz.173 255.255.255.240 Outside
WAN IP : 8x.yy.zz.173
Subnet: 255.255.255.240
Interface: Outside
In case of success, I should be able to SSH to this FW with this WAN IP address 8x.yy.zz.173 <I don't see if something is wrong with this command>
Now the original question, what is causing the IP address to be changed? While I have used it on Cisco Router 890 ISR.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 08:46 AM
x.x.x.160 255.255.255.240 is a subnet ID.
x.x.x.173 is a host address. If you want to restrict access to a specific host then use as 32-bit mask (255.255.255.255).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 11:10 AM
@Marvin Rhoads Thanks for your input.
My ISP has provided the following details:
IP: XX.XX.YY.173
Subnet: 255.255.255.240
Gateway: YY.YY.YY.161
Note: Above information is valid and I was able to SSH on Cisco Router 890 series ISR in past with same information.
what is the possible explanation of change of the IP address in firewall?
What should I do now? change the subnet from 255.255.255.240 to 255.255.255.255?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 12:02 PM
Your firewall (Firepower 1120 running ASA image) outside interface must have the same netmask as provided by your ISP.
You have mixed up the "ssh" command (which tells the firewall what addresses may ssh to it) with the interface address configuration.
Once you have configured the outside address and default route, your should be able to ping the gateway (and Internet addresses) from the ASA itself.
@Aref Alsouqi already mentioned the commands to allow access to the ASA outside (public IP) address. Generally we restrict that access to only trusted source addresses/subnets.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 11:43 AM
No problem. Let's break it down a bit.
- Your WAN Outside interface IP is 8x.yy.zz.173/28 (subnet mask 255.255.255.240)
- The subnet ID of that IP is 8x.yy.zz.160/28 as pointed by @Marvin Rhoads
- You want to allow SSH to the firewall via Outside interface
The firewall shows the IP 8x.yy.zz.160/28 in the SSH section because you issued the command "ssh 8x.yy.zz.173 255.255.255.240 Outside". The command you issued has the subnet mask 255.255.255.240, because of this the firewall converts the IP address 8x.yy.zz.173 into the subnet ID which is 8x.yy.zz.160/28. This is why! If you want to see the IP 8x.yy.zz.173 in the SSH section, then you need to remove the command "ssh 8x.yy.zz.173 255.255.255.240 Outside" and replace it with "ssh 8x.yy.zz.173 255.255.255.255 Outside", so you need to change the last octet in the subnet mask from 240 to 255.
However, as I mentioned before, the command "ssh ... Outside" is used to define the source IP addresses or subnet that are allowed to SSH to the firewall, obv they still need to authenticate before they are allowed accesses to the firewall.
So, if you change the command "ssh 8x.yy.zz.173 255.255.255.240 Outside" to "ssh 8x.yy.zz.173 255.255.255.255 Outside" it means that the firewall will only accept the SSH connections from the IP 8x.yy.zz.173, but this will never happen as the IP 8x.yy.zz.173 is the firewall WAN interface itself, and the SSH connections would never source from that IP.
What you would need to do to get this to work is just changing the IP 8x.yy.zz.173 in the command "ssh 8x.yy.zz.173 255.255.255.240 Outside" to the source public IP that you will use to source the SSH traffic from.
If you want to widely allow the firewall to accept the SSH connections from anywhere which is not really recommended, then you can swap the command "ssh 8x.yy.zz.173 255.255.255.240 Outside" with "ssh 0 0 Outside". The best security practice in this case would be to define the public IP addresses that would source the SSH traffic, example:
"ssh 1.2.3.4 255.255.255.255 Outside"
"ssh 10.20.30.40 255.255.255.255 Outside"
"ssh 100.200.3.4 255.255.255.255 Outside"
and so on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 12:36 PM
@Aref Alsouqi Appreciated a well explained reply.
So I will change the command as "ssh 8x.yy.zz.173 255.255.255.255 Outside" in order to get the correct WAN Address.
WAN IP=8x.yy.zz.173 which will be dedicated to this FW. However, I will connect to this FW from another ISP /IP. As 8x.yy.zz.173 will be only used to access the FW. So in this case, source and destination will NOT be same IPs.
Feel free to correct if it doesn't sound "logical"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 03:03 AM
You need to define the source IP in the command "ssh 8x.yy.zz.173 255.255.255.255 Outside" not the firewall WAN interface IP. I would read this command as allow SSH from x.x.x.x to the firewall Outside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 10:59 AM
@Aref Alsouqi Thanks again, for testing purposes, I will do this "ssh 0 0 Outside".
So I need to modify the following:
ssh 8x.yy.zz.173 255.255.255.240 Outside >> ssh 0 0 Outside <<
Will get back with results. Have a nice weekend!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 02:10 AM
Yeah, that's correct and you're very welcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 02:40 AM
@Aref Alsouqi Perfect, I can confirm that using SSH 0 0 outside worked fine, I do understand that instead of allowing everywhere, SSH should be limited to certain IP, but for the time being, SSH is working fine, thanks for highlighting source IP and FW IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2023 06:05 AM
You're welcome sir.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide