- Cisco Community
- Technology and Support
- Security
- Network Security
- Strange issue with ASA...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Strange issue with ASA...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2012 02:11 AM - edited 03-11-2019 05:24 PM
Dear all,
I explain my problem; sorry if I have to write a lot of configuration
An Antivirus Server (10.80.3.9) need to reach and need to be reachable from some network connected to a VSS. The AV is behind the BackEnd Firewall (ASA). I attach a simple schema of the network:
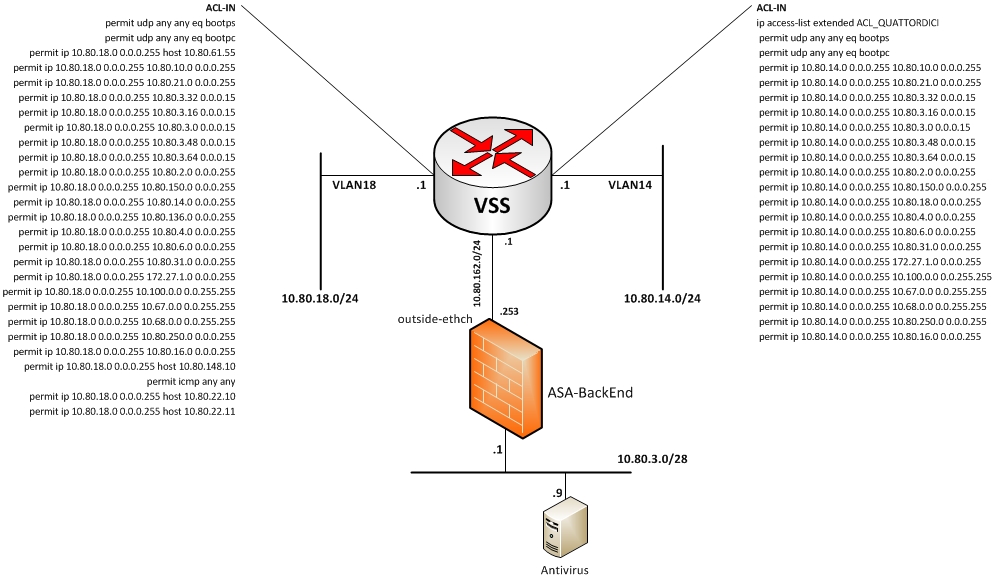
The AV is able to connect to the network 10.80.14.0/24 (on the right) but is not able to reache the network 10.80.18.0/24 (on the left); in the image you can see the ACL applied on the VSS for each of those network. The interface that connect the ASA to the VSS is named outside-ethch (SL 100) and the interface to wich the AV Server is connected is named Vlan610 (SL 100). ACL are applied on the Vlan610, but is a permit any any.
The problem is that the AV Server are able to reach every client on the network 10.80.14.0/24 and viceversa, but is not able to reach the client on the network 10.80.18.0/24. Client on this network can ping the IP of the AV server whereas the server cannot ping the client.
I made packet trace on the ASA and seem that traffic from 10.80.3.9 to 10.80.18.0 is permitted bue when I made a capture I see only the Echo Request from the server. Another strange thing, is that the server is able to ping the default gateway of the network 10.80.18.0 (on the VSS).
I attach also the configuration of the Cisco ASA with all the ACL...
interface Port-channel10.610
vlan 610
nameif vlan610
security-level 100
ip address 10.80.3.1 255.255.255.240 standby 10.80.3.2
!
interface Port-channel11
speed 1000
duplex full
nameif outside-ethch
security-level 100
ip address 10.80.162.253 255.255.255.0 standby 10.80.162.254
!
object network AHMAV
host 10.80.3.9
description Antivirus
object network LAN_10-80-10-0
subnet 10.80.10.0 255.255.255.0
object network LAN_10-80-14-0
subnet 10.80.14.0 255.255.255.0
object network LAN_10-80-150-0
subnet 10.80.150.0 255.255.255.0
description Admin Wirelss WLAN
object network LAN_10-80-18-0
subnet 10.80.18.0 255.255.255.0
object network LAN_10-80-3-0
subnet 10.80.3.0 255.255.255.0
object service RDP-service
service tcp source eq 3389 destination eq 3389
object network LAN-Borgonuovo
subnet 192.168.151.128 255.255.255.128
object network LAN_10-80-200-0
subnet 10.80.200.0 255.255.255.0
object network LAN_10-80-22-0
subnet 10.80.22.0 255.255.255.0
object network LAN_10-80-3-0_sub28
subnet 10.80.3.0 255.255.255.240
object network Antivirus
host 10.80.3.9
object service AV-tcp
service tcp destination eq 2967
object service AV-udp
service tcp destination eq 2967
object network Lan-Borgonuovo-NEW
subnet 10.80.250.0 255.255.255.0
object service tcp-5500
service tcp destination eq 5500
object service tcp-9000
service tcp destination eq 9000
object network LAN_10-80-3-0_mask28
subnet 10.80.3.0 255.255.255.240
object service RDP
service tcp destination eq 3389
object service tcp-17988
service tcp destination eq 17988
object service tcp-17990
service tcp destination eq 17990
object service tcp-3200
service tcp destination eq 3200
object service tcp-3389
service tcp destination eq 3389
object service tcp-9300
service tcp destination eq 9300
object service tcp-445
service tcp destination eq 445
object service tcp-6129
service tcp destination eq 6129
object network 10-100-62-62
host 10.100.62.62
object network 10-67-62-50_51
range 10.67.62.50 10.67.62.51
object network 10-67-62_140
host 10.67.62.140
object service tcp-1777
service tcp destination eq 1777
object service tcp-3050
service tcp destination eq 3050
object service tcp-3060
service tcp destination eq 3060
object network host-83.224.65.24
host 83.224.65.24
description smtp Vodafone
object service TCP-389
service tcp destination eq ldap
object service tcp-5009
service tcp destination eq 5009
object network host-10.80.130.2
host 10.80.130.2
object service tcp-5010
service tcp destination eq 5010
object service tcp-5011
service tcp destination eq 5011
object network host-10.80.33.21
host 10.80.33.21
object service tcp-5013
service tcp destination eq 5013
object network tiger
range 10.80.148.10 10.80.148.11
object service tcp-5012
service tcp destination eq 5012
object network host_10.80.3.14
host 10.80.3.14
object network host-10.80.18.34
host 10.80.18.34
object network host-10.80.31.12
host 10.80.31.12
object service tcp-13000-13001
service tcp destination range 13000 13001
object service tcp-14000-14001
service tcp destination range 14000 14001
object service udp-13000
service udp destination eq 13000
object service udp-15000
service udp destination eq 15000
object service tcp-13292
service tcp destination eq 13292
object service tcp-18000
service tcp destination eq 18000
object service udp-15001
service udp destination eq 15001
object service udp-7
service udp destination eq echo
object service tcp-13291
service tcp destination eq 13291
object-group network DM_INLINE_NETWORK_28
network-object object LAN_10-80-10-0
network-object object LAN_10-80-14-0
network-object object LAN_10-80-150-0
network-object object LAN_10-80-18-0
network-object object Lan-Borgonuovo-NEW
object-group service DM_INLINE_SERVICE_12
service-object icmp
service-object object tcp-13000-13001
service-object object tcp-14000-14001
service-object object tcp-445
service-object object tcp_135
service-object object udp-13000
service-object object udp-15000
service-object object udp_137
service-object object tcp-13291
service-object object tcp-13292
service-object object tcp-18000
service-object object tcp-9000
service-object object udp-7
service-object object udp-15001
object-group network DM_INLINE_NETWORK_29
network-object object LAN_10-80-10-0
network-object object LAN_10-80-14-0
network-object object LAN_10-80-18-0
network-object object Lan-Borgonuovo-NEW
object-group service DM_INLINE_SERVICE_13
service-object icmp
service-object object tcp-13000-13001
service-object object tcp-14000-14001
service-object object udp-13000
service-object object udp-15000
service-object object tcp-13292
service-object object tcp-18000
service-object object tcp-13291
service-object object tcp-9000
service-object object udp-7
service-object object udp-15001
access-list outside-be_access_in extended permit ip any any
access-list inside-ethch_access_in extended permit ip any any
access-list outside-ethch_access_in extended permit ip object-group DM_INLINE_NETWORK_31 10.80.3.0 255.255.255.240
access-list outside-ethch_access_in extended permit icmp object-group DM_INLINE_NETWORK_23 object LAN_10-80-3-0
access-list outside-ethch_access_in extended permit object-group DM_INLINE_SERVICE_13 object-group DM_INLINE_NETWORK_29 object Antivirus
access-list outside-ethch_access_in extended permit ip host 10.80.3.9 any log
access-list outside-ethch_access_in extended permit ip 10.80.18.0 255.255.255.0 host 10.80.3.9
access-list inside-ethch_authentication extended permit tcp 172.10.10.0 255.255.255.0 any
access-list vlan610_access_in extended permit ip any any
access-list vlan610_access_in extended permit icmp any any
access-list global_access extended permit icmp object LAN_10-80-3-0_mask28 any
access-list global_access extended permit ip object LAN_10-80-3-0 object LAN_10-80-3-0
access-list global_access extended permit icmp object LAN_10-80-3-0 object LAN_10-80-3-0
access-list global_access extended permit ip object LAN_10-80-3-0 object-group DM_INLINE_NETWORK_18
access-list global_access extended permit object-group DM_INLINE_SERVICE_12 object Antivirus object-group DM_INLINE_NETWORK_28
access-list capture_antivirus extended permit ip host 10.80.3.9 host 10.80.18.130 log
access-list capture_antivirus extended permit ip host 10.80.18.130 host 10.80.3.9 log
access-list capture_antivirus extended permit icmp any host 10.80.3.9
access-list capture_antivirus extended permit ip host 10.80.3.9 host 10.80.14.13 log
access-list capture_antivirus extended permit ip host 10.80.3.9 host 10.80.18.1 log
pager lines 24
monitor-interface vlan609
monitor-interface vlan610
monitor-interface vlan611
monitor-interface Cisco-Server
icmp unreachable rate-limit 1 burst-size 1
nat (vlan600,outside-ethch) source static AHMMIC AHMMIC destination static broadcast-ip nat-broad service tcp-1777 tcp-1777
!
object network internal-LAN-dummy
nat (inside-ethch,outside-ethch) dynamic interface
access-group inside-ethch_access_in in interface inside-ethch
access-group vlan26_access_in in interface vlan26
access-group vlan600_access_in in interface vlan600
access-group vlan609_access_in in interface vlan609
access-group vlan610_access_in in interface vlan610
access-group vlan611_access_in in interface vlan611
access-group Cisco-Server_access_in in interface Cisco-Server
access-group outside-ethch_access_in in interface outside-ethch
access-group global_access global
route outside-ethch 0.0.0.0 0.0.0.0 10.80.162.1 1
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Please, can anyone give me an idea to solve this problem?
Thank in advance,
Maurizio
- Labels:
-
NGFW Firewalls
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
