- Cisco Community
- Technology and Support
- Security
- Network Security
- Syslogs for VPN Allows and Denies hitting Extended ACL on FMC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2023 05:19 AM
I'm hoping someone on here has ran into a similar issue as us with trying to log all permitted and denied traffic for RAVPN traffic on FTDs.
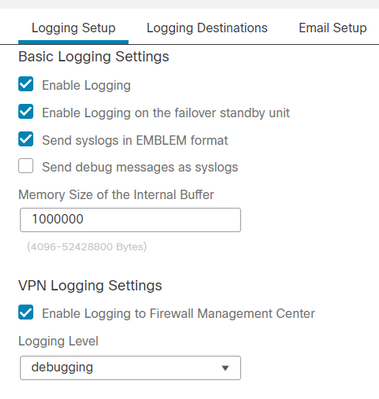
We recently migrated from ASA to FTD and have had trouble with getting all of the logs we'd like to see on our Syslog Server for VPN traffic. I have enabled Syslog under Platform Settings and have VPN Log Settings checked with logging level set to Debugging like in the screenshot below:
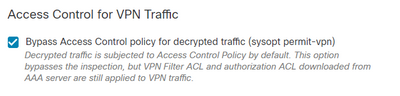
We do receive some syslogs for VPN events, but it looks like I am only seeing traffic denied by our default drop rule. I'm not seeing any of the allowed traffic being logged. Also, we are using an extended ACL which is tied to a DAP to filter the VPN traffic so this traffic would not hit our normal ACP based on the below setting.
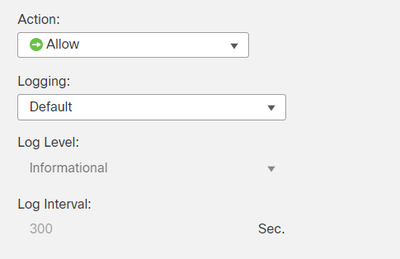
Below is a screenshot of how logging is configured on one of our Extended Access List Rules used in one of our VPN policies. All rules are setup the same way.
Thanks,
Josh
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2023 03:12 AM
I think a better solution to view RA VPN connections in Syslog is to disable the Bypass Access Control Policy option and create access rule entries in the ACP for this traffic and log that towards syslog.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2023 06:41 PM
Hello Josh,
hope you are doing well. I see you have reported this issue to our TAC team and our TAC engineer has provided an explanation and an alternative solution. Thanks very much for contacting our TAC team.
Regards
---------
You can also learn more about Secure Firewall (formerly known as NGFW) through our live Ask the Experts (ATXs) session. Check out Cisco Network Security ATXs Resources [https://community.cisco.com/t5/security-knowledge-base/cisco-network-security-ask-the-experts-resources/ta-p/4416493] to view the latest schedule for upcoming sessions, as well as the useful references, e.g. online guides, FAQs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2023 03:12 AM
I think a better solution to view RA VPN connections in Syslog is to disable the Bypass Access Control Policy option and create access rule entries in the ACP for this traffic and log that towards syslog.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2023 05:20 AM
Hi Marius,
Yeah, that's what we have decided to do. When we first set this up, we used the FTD Migration Tool and it so it migrated all of our rules as extended ACLs. TAC recommended we move our rules to our ACP which is what we are doing.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide