- Cisco Community
- Technology and Support
- Security
- Network Security
- Unable to enable Restconf on Cisco C9300, IOS-XE 17.3.4
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Unable to enable Restconf on Cisco C9300, IOS-XE 17.3.4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2022 02:49 AM
Hey Guys,
i tried basically everything in the internet.
My ::> show run
Any more parts interesting for you? What am I missing.
> -----curl https//:{host}:443 -u "name:pw" ------------ is not working either! Postman neither! Browser neither...
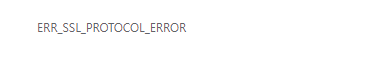
Chrome is giving me:
Has anyone an idea? Thanks to everyone!
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2022 03:08 AM - edited 10-21-2022 03:10 AM
what License you have on the switch ?
can you post @:
# show platform software yang-management process
most of the time netconf uses port TCP 830
some reference :
https://developer.cisco.com/docs/ios-xe/#!enabling-netconf-on-ios-xe/163
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2022 05:21 AM
Hi! Thanks for the fast response!
This is my Output:
_________
Switch-ZTP-Telemetry-Generic#show platform software yang-management process
confd : Running
nesd : Running
syncfd : Running
ncsshd : Running
dmiauthd : Running
nginx : Running
ndbmand : Running
pubd : Running
gnmib : Running
________
Concerning the licences. I've got network advantage & dna advantage.
Should be possible to enable RESTCONF... don't you think? (RESTCONF, not NETCONF btw
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2022 09:34 AM - edited 10-21-2022 09:35 AM
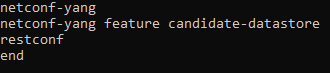
just tested with Cat 9300 netconf works as expected :
#show run | in netco
netconf-yang
netconf-yang feature candidate-datastore
#show netconf-yang datastores
Datastore Name : running
Datastore Name : candidate
# show netconf-yang sessions
R: Global-lock on running datastore
C: Global-lock on candidate datastore
S: Global-lock on startup datastore
Number of sessions : 1
session-id transport username source-host global-lock
--------------------------------------------------------------------------------
24 netconf-ssh mgmt 10.10.10.5 None
root@Linux# ssh bbcisco@10.10.10.10 -p 830 -s netconf
The authenticity of host '[xxxxxxxxxxxx]:830 ([xxxxxxxxxxx]:830)' can't be established.
RSA key fingerprint is SHA256:hAiw/dNTtVPwFVVpu6S+fAAdrIZf+6YSkvsawddhaug.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '[xxxxxxxxxx]:830' (RSA) to the list of known hosts.
mgmt@xxxxxxxxxx's password:
<?xml version="1.0" encoding="UTF-8"?>
<hello xmlns="urn:ietf:params:xml:ns:netconf:base:1.0">
<capabilities>
<capability>urn:ietf:params:netconf:base:1.0</capability>
<capability>urn:ietf:params:netconf:base:1.1</capability>
<capability>urn:ietf:params:netconf:capability:confirmed-commit:1.1</capability>
<capability>urn:ietf:params:netconf:capability:confirmed-commit:1.0</capability>
<capability>urn:ietf:params:netconf:capability:candidate:1.0</capability>
<capability>urn:ietf:params:netconf:capability:rollback-on-error:1.0</capability>
<capability>urn:ietf:params:netconf:capability:validate:1.0</capability>
<capability>urn:ietf:params:netconf:capability:validate:1.1</capability>
.....
<capability>
urn:ietf:params:netconf:capability:notification:1.1
</capability>
</capabilities>
<session-id>24</session-id></hello>]]>]]>
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2022 11:37 PM
So netconf is working on my device too!
But i cant access the switch via HTTP / RESTCONF. You have any idea on that too?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2022 07:18 AM
aaa new-model
!
aaa authorization exec default local
!
ip http server
ip http authentication local
ip http secure-server
!
restconf
From my Linux box :
# curl -i -k -X "OPTIONS" "https://10.10.9.100:443/restconf/data/Cisco-IOS-XE-native:native/logging/monitor/severity" -H 'Accept: application/yang-data+json' -u 'admin:Cisco123'
HTTP/1.1 200 OK
Server: nginx
Date: Mon, 24 Oct 2022 14:18:32 GMT
Content-Type: text/html
Content-Length: 0
Connection: keep-alive
Allow: DELETE, GET, HEAD, PATCH, POST, PUT, OPTIONS
Cache-Control: private, no-cache, must-revalidate, proxy-revalidate
Accept-Patch: application/yang-data+xml, application/yang-data+json
Pragma: no-cache
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2022 04:54 AM
Unfortunately did not change anything
any more ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2022 08:39 AM
what did not change ? can you explain what steps you followed ?
post the latest config for us to review again.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2022 01:45 AM
Thanks for your response!
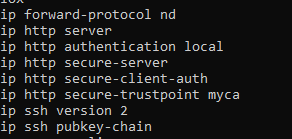
So i added to my config what you wrote:
aaa new-model
!
aaa authorization exec default local
!
ip http server
ip http authentication local
ip http secure-server
!
restconf
_____________
But i still can't access my switch. Neither with Postman, Curl, Browser, nor Java OkHTTP Client.
I always get some errors related to something like this.
SSL Handshake failed.
Received fatal alert: internal_error > at at java.base/sun.security.ssl.Alert.createSSLException(Alert.java:133)
The above mentioned Chrome SSL error message.
My Config is attached.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2022 11:35 AM
seems to be some bugs on 17.3.X code, don't have bug in hand to give you.
Try postman settings :
https://developer.cisco.com/codeexchange/github/repo/jeremycohoe/cisco-ios-xe-postman-collections
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide