Hi all,
I have set up an ASA firewall 5506x on packet tracer connected to a Multilayer Switch. I have configured ICMP to allow ping through + for the firewall to inspect icmp (through the use of Access-list permit icmp any any + policy-map global policy inspect icmp).
Here's a related Screenshot of the Setup:
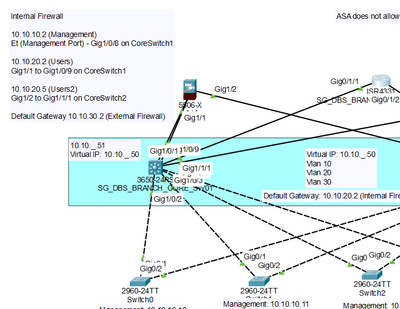
p.s. there are 2 direct connections between the Internal Firewall and the Multilayer Core Switch. One of which is for the Management Port that ASA 5506-x has.
The result was that while I am able to ping from a Gig port (Switch) to Gig port (ASA), I am unable to ping from the Multilayer Switch GigabitEthernet Port into the Management Port of the ASA firewall.
Considering the icmp was successful for Gig Port to Gig Port, I think it is safe to assume there is no error regarding the ACLs set and the inspection of icmp under the policy-map.
I've also tried the following troubleshooting/testing and these are the results:
1. My firewall is unable to self-ping its own Management Port IP Address, but is able to self-ping its other ports' IP addresses.
2. Simulation Mode: I pinged the firewall's Management IP Address from the Multilayer Switch, but instead of one ICMP packet being sent to the ASA firewall, the Multilayer Switch sent out a ICMP broadcast message instead. It seemed as though the Management IP address of the ASA firewall is unknown to the Multilayer Switch. I've attached the related Screenshot as well below:
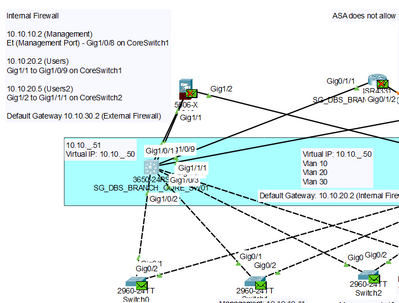
Extra Points:
a) The connections between the Internal Firewall (ASA 5506x) and Core_Switch_01 (Multilayer Switch) are both set as Switchport mode access on both ends. Management Connection uses VLAN 10 while the Users Connection uses Vlan 20. I've checked this configuration after reviewing another discussion board (Unable to ping ASA's Management interface - why? - Cisco Community).
Hope to receive some advice from the experts here. Please let me know what the possible issues could be so that I can brush up the loopholes in my understanding. Thank you in advance!