- Cisco Community
- Technology and Support
- Security
- Network Security
- Ok so I I should create the
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VLANs on ASA5505
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2014 04:16 AM - edited 03-11-2019 09:40 PM
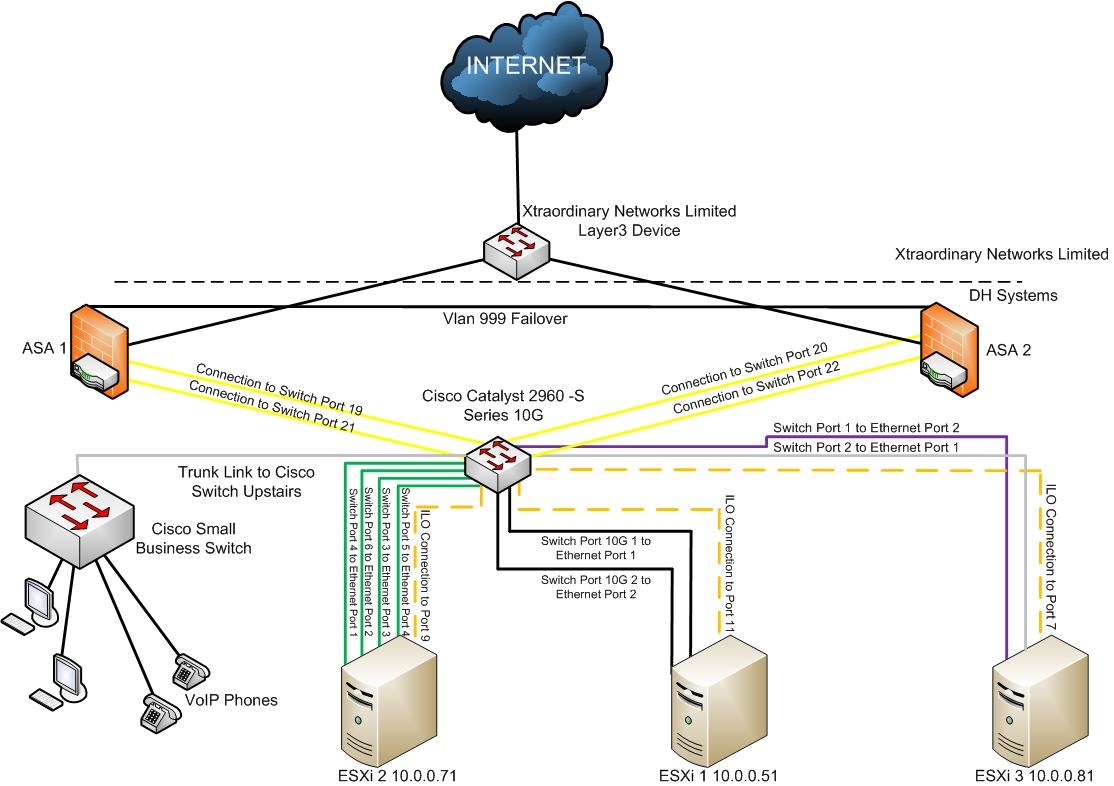
Hi, can somebody help me out with the configs for this scenario at my company's network? (photo below)
I want to create 2 vlans, VLAN 10 for Servers and Desktops and VLAN 20 for the IP phones. I'm not to sure on how to do this through the ASA 5505 as I'm used to using subinterfaces on a router (I'm straight out of college) and although we have the security plus license it still wont let me create a subinterface.
So how do I make everything communicate? Do I create the vlans through the command line and then set the ethernet port to an access port with the correct vlan ID?
Also, do I set the ethernet ports on the ASA to trunks (the connection between the ASA and 10GB switch) or access ports? Again, this is because I'm used to using Router-on-a-Stick!!
The 10GB Switch that has 4 connections to the ASA's (2 for each ASA) will they ports need to be trunks or access ports? Do i create vlan's 10 and 20 on this switch with an IP address or...? I know that I'll have to make the port that connects to the upstairs switch a trunk port as there will be tagged info getting sent down it.
The upstairs switch just requires a trunk link to be made for the link that goes downstairs, and pretty much all other ports can be access ports with the correct vlan enabled on that port as another dumb switch connects into these ports and our desktops connect into the dumb switches.
Any help would be very much appreciated! P.S. the networks i want to use for VLAN 10 is 10.0.0.0/24 and for VLAN20 10.0.1.0/24
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2014 05:25 AM
The 5505 is configured like a L3-switch. You have VLAN-interfaces and these vlans are used on L2-trunk-ports. Or you dedicate one vlan to a single L2-interface.
But you should also ask yourself if you really want to firewall the ip-phone-traffic. In larger environments its a best practice, but in small networks like yours perhaps not needed.
If you don't need the firewalling for these, then you could configure the 2960-S as your L3 "core"-switch which routes through all networks. The ASAs were connected with a transit-link in that case. Regardless of the solution, I would always separate Servers and Desktops in their own VLANs. Also for that it could be a good idea to use the 2960 in routed mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2014 06:04 AM
Ok so I I should create the vlan interfaces on the ASA and set up the port that connects the ASA to the switch as a trunk? and allow all vlans along?
It's not really my decision, my boss wants the IP phones on one network and the rest on another network. The reason I didnt want to put the servers and desktops on separate vlans and keep them on the same vlan was because of file transfers between the servers and the desktops which get done daily, as the ASA is only 100Mbps these transfers would be tedious!.
The other problem if got is that my boss wants the ip phones to be on the same network as our asterisk server, which is a virtual machine on one of the ESXi's, but thats a problem for someone else haha.
How do I use the 2960 in router mode? this would allow everything to be done at the switch then wouldnt it instead of everything going upto the ASA, thus meaning higher speeds?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2014 06:27 AM
sw1(config)#ip routing> The other problem if got is that my boss wants the ip phones to be on the same network as our asterisk server, which is a virtual machine on one of the ESXi's, but thats a problem for someone else haha.
Also very easy. If you have multiple NICs in your vmware-host, dedicate one for the voice-vlan and connect that to an voice-Vlan access-port on the switch. If you don't have enough NICs in the server, then configure it as a trunk to the switch.
If you have all functional vlans (desktop/server/voice) on the switch, you only need one more vlan as a transfer-network to the ASAs. This network will be the ASA-inside-network.
With that design you will have the most flexibility.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2014 07:05 AM
Ok thanks for your help, I'll do this as soon as i can. I follow what your saying upto the last part about the transfer network. I understand that this will be used to transmit all the traffic out the switch destined for the outside but how do I set that up? also, do i have to add a default route into the 2960 poiting at the ASA1?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2014 07:32 AM
> also, do i have to add a default route into the 2960 poiting at the ASA1?
- On the switch you need a static default route pointing to the ASA.
- On the ASA you need a static route for all your internal networks pointing to the switch-ip.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



> How do I use the 2960 in router mode? this would allow everything to be done at the switch then wouldnt it instead of everything going upto the ASA, thus meaning higher speeds?
sw1(config)#sdm prefer ?default Default bias
lanbase-routing Supports both IPv4 and IPv6 Static Routing