- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Configuring & Understanding OSPF HMAC Authentication
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-10-2021 11:33 AM - edited 10-10-2021 11:37 AM
Summary
In the past when IOS 12.x was hot stuff we used MD5 to authenticate OSPF neighbors. This worked great on ethernet networks because OSPF is a multicast routing protocol and malicious actors could easily multicast to 224.0.0.5 and modify the routing table.
OSPFv2 has always included three types of authentication schemes, null authentication, cleartext password a.k.a simple password and cryptographic authentication. Null is equivalent to no authentication. Cleartext provides a very basic authentication method for protecting against accidental inclusion of an OSPF router onto the network. Cryptographic authentication provides a secure method for OSPF neighbors to communicate. This method enables neighbors to generate a hashed digest to verify each packet received was not tampered with during transit and that each packet received was sent by a router that is allowed to participate in the OSPF domain. RFC 5709 adds newer, stronger methods of cryptographic authentication for OSPF.
Now in 2021 and for several years before, there are better ways to secure this traffic. You may have heard me rant about this before but MD5 is dead, please stop using it where ever possible. </endrant> In this document I will describe the modern way of securing your OSPF neighbor traffic using keys and HMAC with a strong SHA based hashing method. The methods that are described below are able to configured per-interface or per-network \ per-subnet. This is another set-it and forget-it method for hardening your network without adding a lot of complexity.
Please understand this does not provide confidentiality, it does not encrypt the message. As of 2021, there is no method of encrypting the payload in OSPF. Discussed below is a method of authenticating the message and verifying that it came from a valid OSPF neighbor.
Requirements
- OSPF v2 – If you’re using IPv4, you’re using OSPF v2
- Modern IOS or IOS XE
Configuration Steps
This is not a how-to on setting up OSPF, in this doc we assume that you already have an OSPF neighbor relationship established and here we will build authentication on top of that existing neighbor relationship.
First let’s create the key. The key, the algorithm and the key string need to be the same on both neighbors.
!
configure terminal
key chain ospf-hmac-key1
key 1
cryptographic-algorithm hmac-sha-512
key-string use-128-hex-digits-here
!
end
!
Note: The recommended size for a SHA-256 HMAC is 64 bytes with full entropy. 64 bytes is the minimum for SHA-512 HMAC and this is an acceptable key size.
Be sure to use full entropy when generating your key, just mashing on your keyboard isn’t the same. In 2021 and beyond use HMAC-SHA-512.
There are tools below for generating hex keys with full entropy.
Now let’s apply the key to the OSPF process on our interfaces.
!
configure terminal
interface Gigabit0/1
ip ospf authentication key-chain ospf-hmac-key1
!
end
!
Yup, that’s it. Pretty simple huh… It's small changes like this that build upon each other to make the network much more secure!
Verification
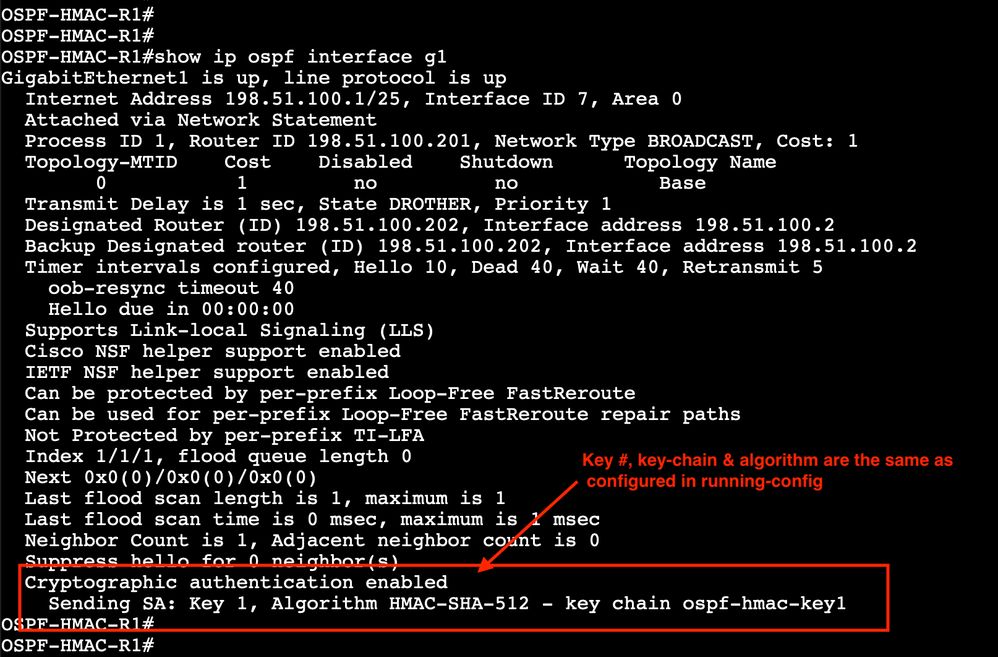
show ip ospf interface g1
In this output you will see that the traffic on the interface is protected. As mentioned earlier this is interface specific.
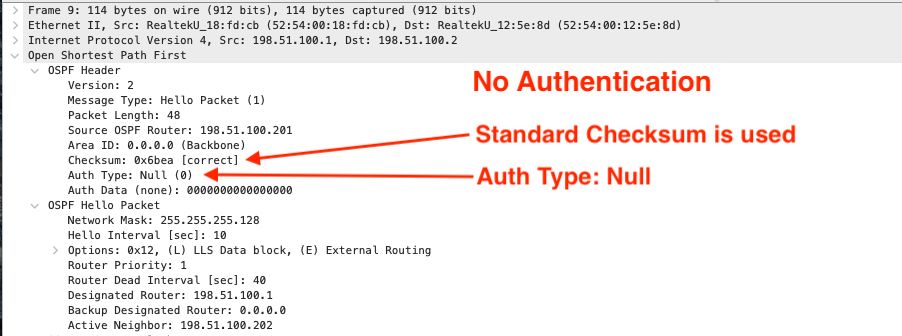
The frame below shows clear text hello. This does NOT contain any authentication and is shown for compare \ contrast purposes. The two things that stand out in this frame are Auth Type is null. The RFC clearly states null is equivalent to no authentication. The second thing that stands out is that the standard checksum is enabled. With HMAC the checksum should be all zeros.
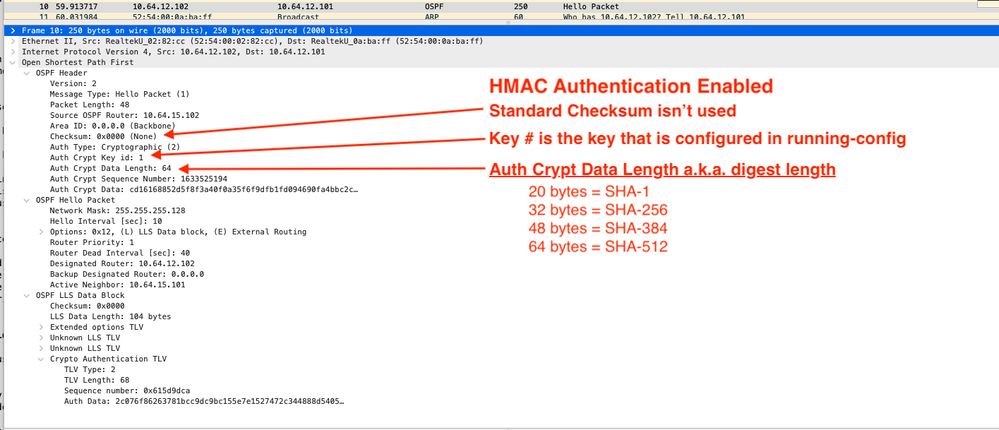
The frame below shows an OSPF hello packet with HMAC-SHA-512.
How do we know? First, we see the standard checksum is all zeros, next we see that Auth Crypt Data Length is equal to 64, we know from RFC 5709 that this means HMAC-SHA-512 is enabled. Third, there are just a lot of Auth Crypt fields that weren’t there in the clear text frame.
FAQ
What is a hash?
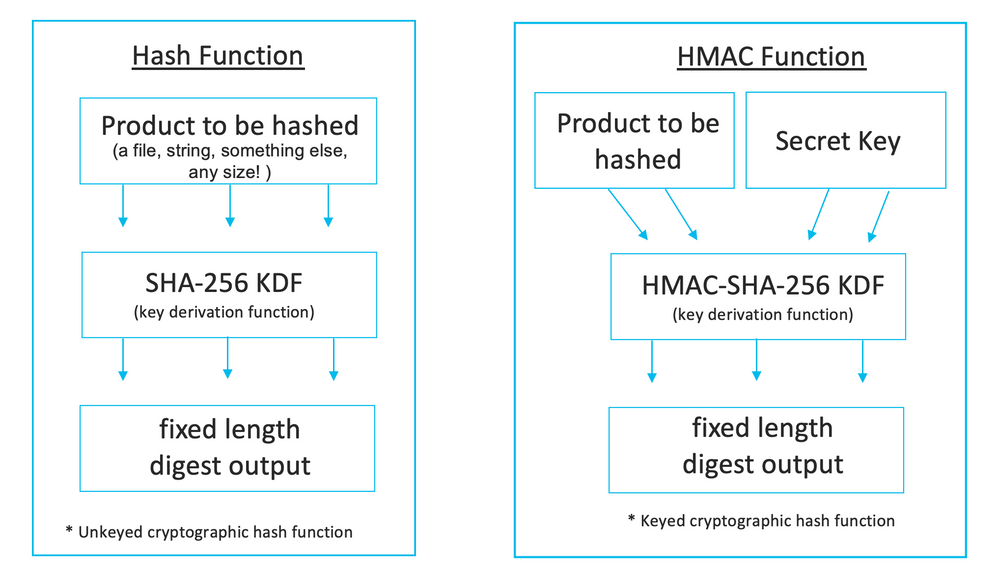
A hash is a mathematical function that converts one value to different value with a fixed length. Examples of hashing include compression, cryptography and checksum. The output of a hash function is sometimes called a digest or a hash. Hashing is a one-way function and should never be reversible. Since hashing typically reduces the size of the input data there is a small possibility that different input will lead to the same output, this is called a collision. There are dozens of different hashing functions and several hashing purposes, not all purposes are for cryptography.
What is HMAC?
HMAC is a ‘Hash based Message Authentication Code’. HMAC steps up a standard hash by adding in a secret key into the KDF process. HMAC helps authenticate a message that one device sends to another. HMAC is like a cyclic redundancy check or CRC with a few differences.
The secret key is configured on both devices, so it is ‘known’.
The secret key is never transmitted across the unsecure medium.
The message is sent in the clear so it is known by both devices.
Both devices both perform an HMAC function on the data using the secret key and as long as the hash output is the same the message can be considered authentic and
The cryptographic strength of the HMAC depends on the size of the secret key.
HMAC is much simpler than using public key infrastructure.
HMAC is used in common protocols like IPsec, SSH and TLS.
What is the difference between a hash and an HMAC ?
A hash uses a standard algorithm to derive the digest. This can provide validation.
An HMAC adds a variable, the secret key, into the algorithm. This secret key is what provides the authentication! The digest won’t be the same on the receiving end if the secret key isn’t known by the receiver.
What is SHA-xxx?
SHA-256, SHA-384 and SHA-512 are message digest algorithms. They are used to compute a hash value. A hash function takes data and returns a fixed length string or value.
MD5 hashes are 128 bits (16 bytes) and are typically displayed as 32 hex digits
SHA-1 hashes are 160 bits (20 bytes) and are typically displayed as 40 hex digits
SHA-256 hashes are 256 bits (32 bytes) and are typically displayed as 64 hex digits
SHA-512 hashes are 512 bits (64 bytes) and are typically displayed as 128 hex digits
What is a KDF?
A KDF is a Key Derivative Function. This is a mathematical task that is used in cryptography.
Troubleshooting
debug ip ospf packet
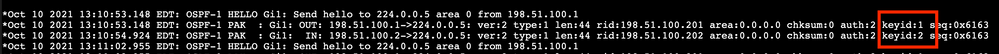
This debug shows us that the key used in the key chain has the wrong index number. As stated above in the config section the key and the key string have to be identical on all adjacent routers.
References & Tools
RFC 2104 – Keyed Hashing for Message Authentication
https://datatracker.ietf.org/doc/html/rfc2104
RFC 4868 – Using HMAC-SHA-xxx with IPsec
https://datatracker.ietf.org/doc/html/rfc4868
RFC 5869 – HMAC-based Extract & Expand KDF
https://datatracker.ietf.org/doc/html/rfc5869
RFC 5709 - OSPF HMAC-SHA Cryptographic Authentication
https://datatracker.ietf.org/doc/html/rfc5709
RFC 6094 – Summary of Cryptographic Authentication Algorithms for Routing Protocols
https://datatracker.ietf.org/doc/html/rfc6094
RFC 6151 - Updated Security Considerations for MD5 and HMAC-MD5
https://datatracker.ietf.org/doc/html/rfc6151
MD5 is no longer acceptable where collision resistance is required such as digital signatures. It is not urgent to stop using MD5 in other ways, such as HMAC-MD5; however, since MD5 must not be used for digital signatures, new protocol designs should not employ HMAC-MD5. Alternatives to HMAC-MD5 include HMAC-SHA256 [HMAC] [HMAC-SHA256] and [AES-CMAC] when AES is more readily available than a hash function.
Hash Generator (multiple sizes)
https://passwordsgenerator.net/md5-hash-generator/
HMAC Generator (multiple sizes)
https://www.freeformatter.com/hmac-generator.html
CRC vs Hashes
https://eklitzke.org/crcs-vs-hash-functions
Sample MD5 Configuration for Authentication in OSPF (LEGACY)
https://www.cisco.com/c/en/us/support/docs/ip/open-shortest-path-first-ospf/13697-25.html
HMAC
https://en.wikipedia.org/wiki/HMAC
HMACSHA256 Constructors from Microsoft
The key can be any length. However, the recommended size is 64 bytes.
Since one hex digit is equal to ½ of a byte the key should be 128 hex characters long.
Key Size for HMAC-SHA256
https://crypto.stackexchange.com/questions/34864/key-size-for-hmac-sha256
HMAC-SHA-512 with 256-bit key
https://crypto.stackexchange.com/questions/62530/hmac-sha-512-with-a-256-bit-key
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Amazing guide.
Can we use the same key for multiple neighbor relationship on different link or we have to create a new key for each ones?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You tell us to use full entropy instead of mashing at the keyboard, but you don't make it clear how full entropy is achieved.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@mscott21 , good call out.
https://github.com/timmayg/openssl/blob/main/01-generate_random_numbers.md
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks, I actually just posted a much lengthier python script on my LinkedIn to answer my own question but this is short and sweet
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: