Introduction
This community article will go through the step-by-step process of how to integrate Catalyst SD-WAN with ISE. This integration enables identity-based firewall rule making on Catalyst Edge devices for micro-segmentation at the branch.
Prerequisite: ISE Configuration
Step 1 - Configure ISE before Catalyst SD-WAN integration
Step 1.1 - Enable PxGrid services.
Step 1.2 - Enable password-based account creation. This is required so SD-WAN Manager can make API calls to ISE to create credentials.
Step 1.3 - Enable ERS and OpenAPI (enabled by default in ISE 3.4 or later).

Step 2 - Add Active Directory as external identity source (Optional)
Step 2.1 - Add AD as an external identity source for user/usergroup integration on ISE.
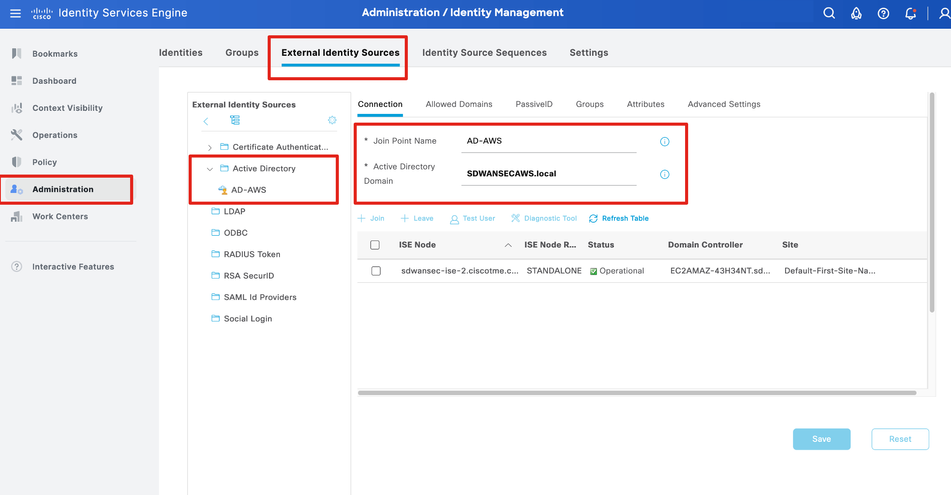
Step 2.2 - Select usergroups to be made available for policy configuration.

Step 3 - SGT Integration: Configure SGTs and static IP to SGT mappings on ISE if demo/testing is required (Optional)
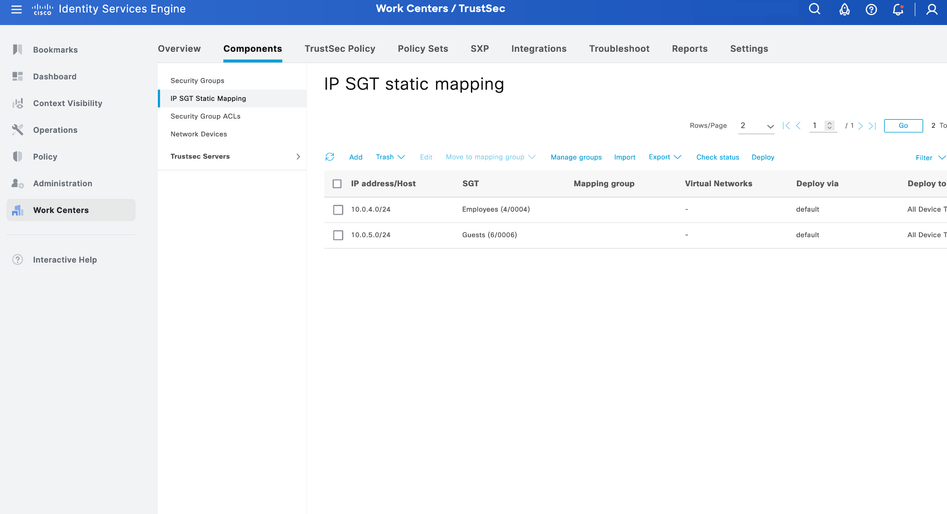
Step 3.1 - Create additional SGTs and IP-to-SGT static mappings to test identity-based FW rules if needed.
Step 3.2 - The SGT to IP mappings will be shared from ISE to Controller through SXP which then would be shared to edge devices within that domain.
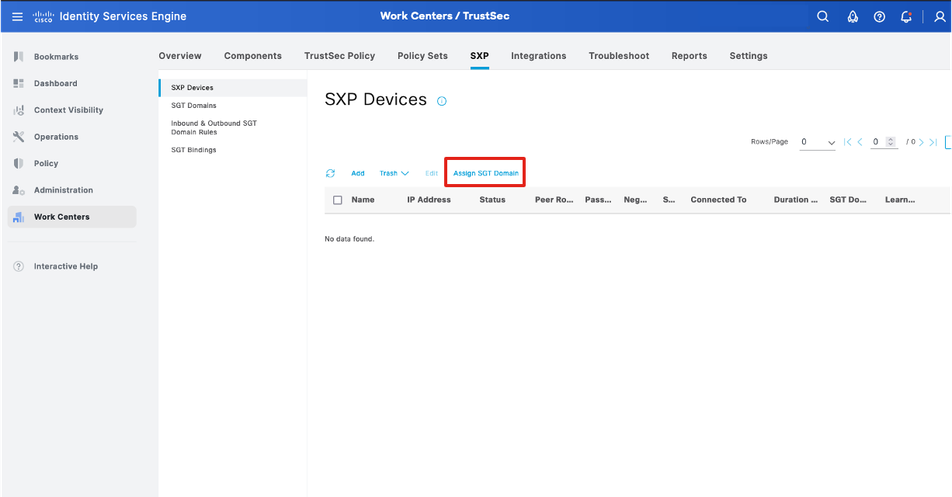
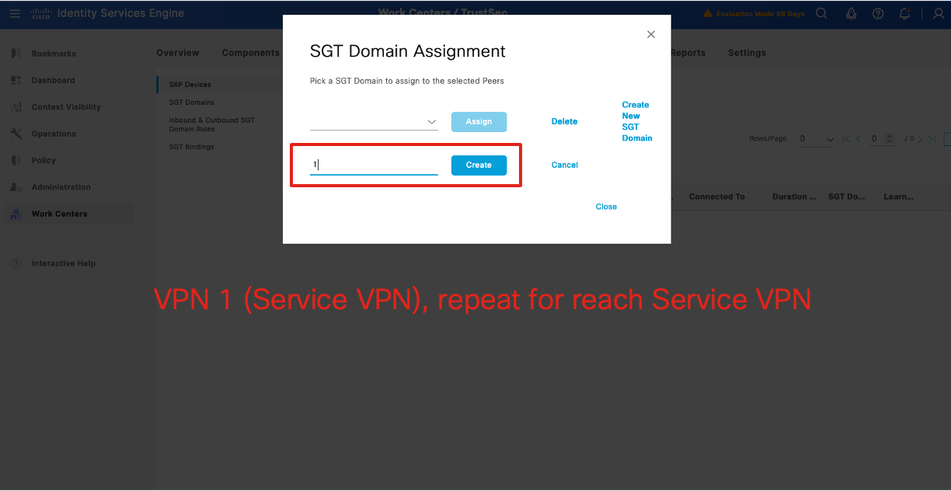
Step 3.3 - Create SGT domain for every VPN
SXP Domain is a collection of SXP devices, and the administrator can decide which domain to send IP-to-SGT mappings to. Controller will send IP –SGT Mappings to SD-WAN Edge based on what VPNs are associated with that SXP domain.
Create new SGT Domain.
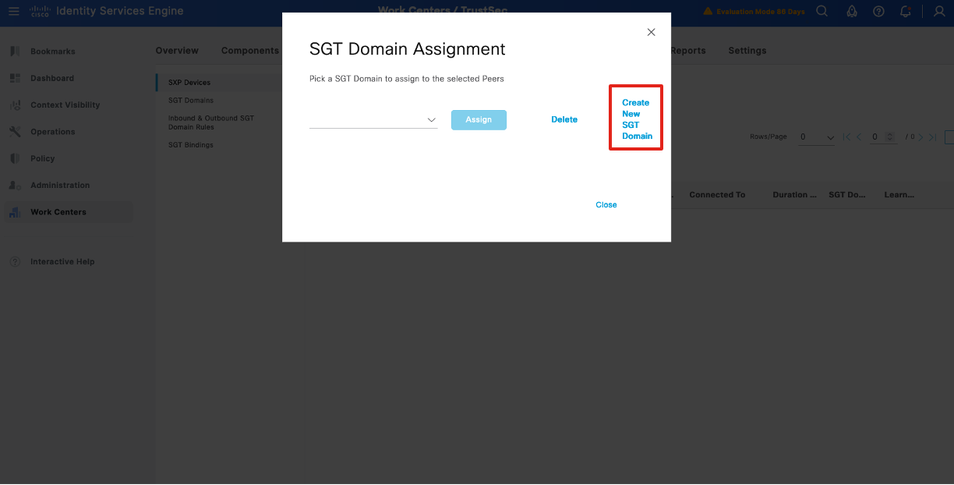
Repeat for each Service VPN.
Step 3.4 - Add SD-WAN Controller as new SXP Device.
Add Controller as SXP device to receive updates from new IP-SGT mappings created on ISE
Click 'Add' to add new SXP device.
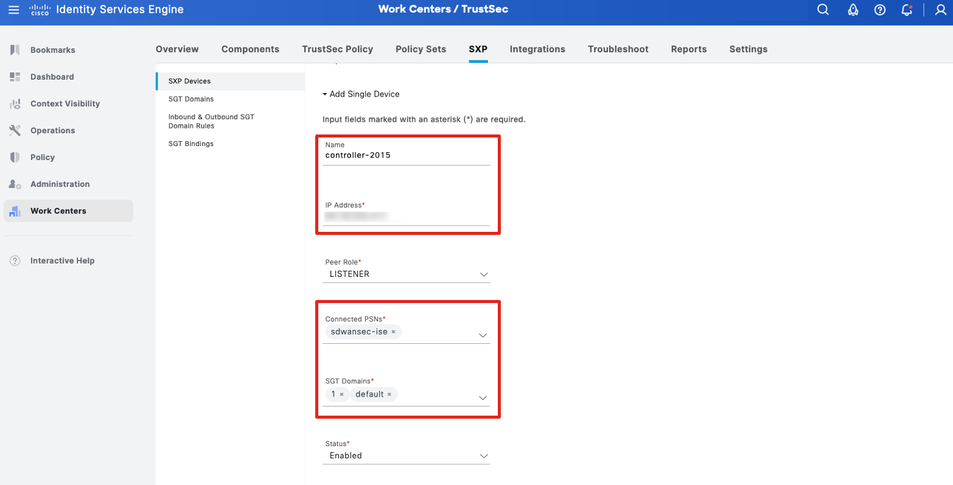
Add SD-WAN Controller information.
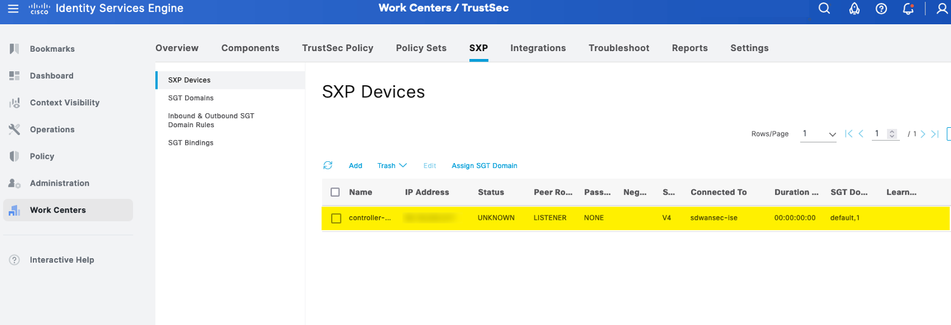
Save the configuration.
Catalyst SD-WAN Manager and ISE integration configuration
Step 4 - Configure SD-WAN controller for ISE integration
On the Catalyst SD-WAN Manager, attach a device template to the SD-WAN Controller.
Step 4.1 - For the VPN0 template, add the static DNS mapping of ISE.

Then, push the template to the SD-WAN Controller.

Step 4.2 - Add ISE integration on Catalyst SD-WAN Manager
Go to Administration > Identity Service Engine. Then click on 'Add Connection'.

Add ISE details.

Option 1: Select and add User Groups info.

Option 2: Select Security Group Tags

Then click 'Submit'.
Once integrated, Catalyst SD-WAN Manager does the rest of the automation such as:
- Creating client account for PxGrid
- Adding credentials on SD-WAN controller (vSmart) for ISE connectivity
- Pulls user/user-group (or SGT) information for security policy creation
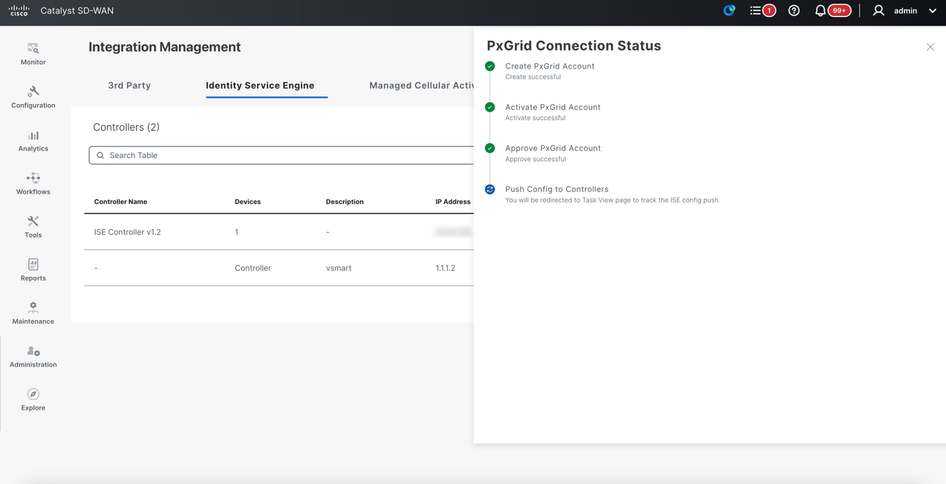
Verification
Check connection status of ISE integration.
Once ISE integration is complete, refresh the integration page and status should show as ‘Connected’ and ‘In Sync’.
Deleting ISE connection will require that identity-list references in the security policies are deleted first.

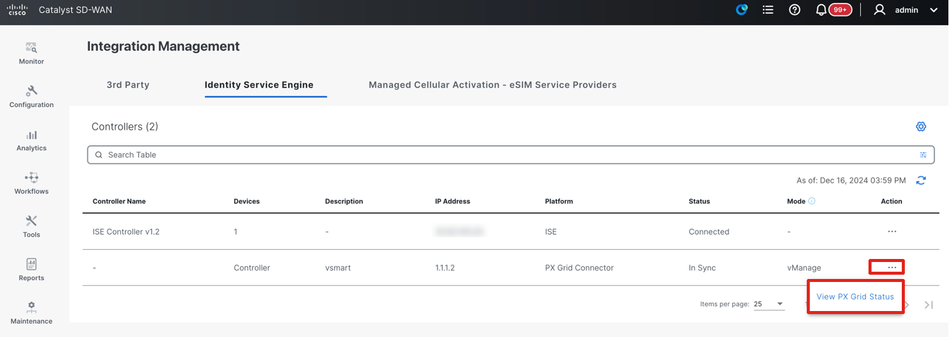
View PxGrid status
You can check the PX Grid status by clicking on the three dots under ‘Action’ and select ‘View PX Grid Status’
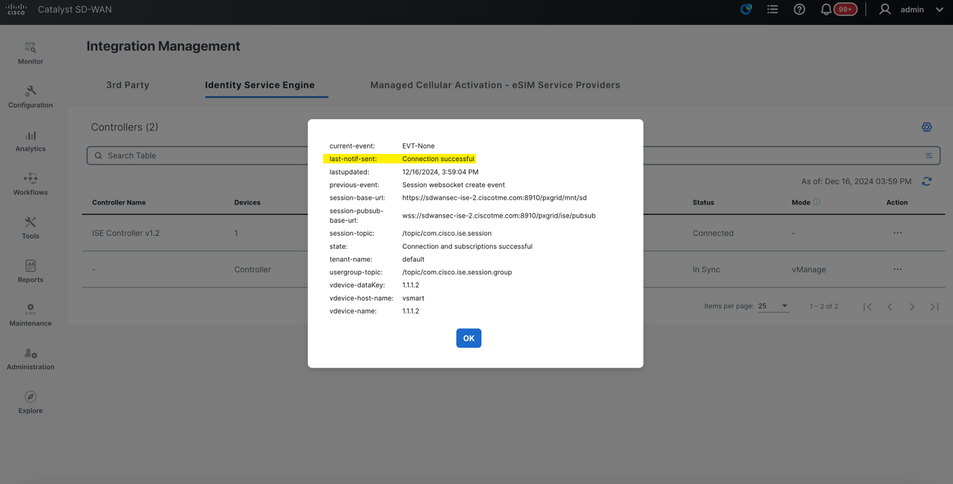
Successful integration will show as ‘Connection Successful’
Otherwise, you will see error message such as ‘Connectivity Failed’
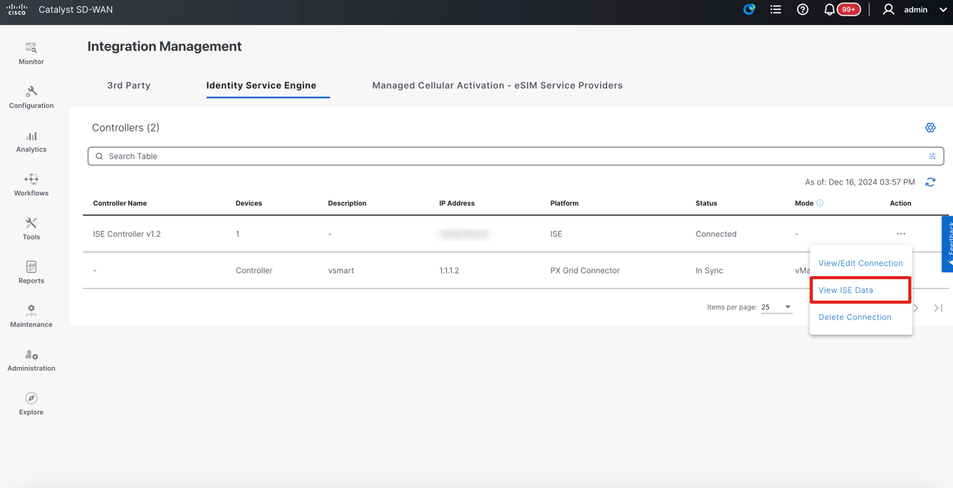
User Groups integration: Check user info learned on Catalyst SD-WAN Manager from ISE
Click on 'View ISE Data'.
Click on 'Users' tab.
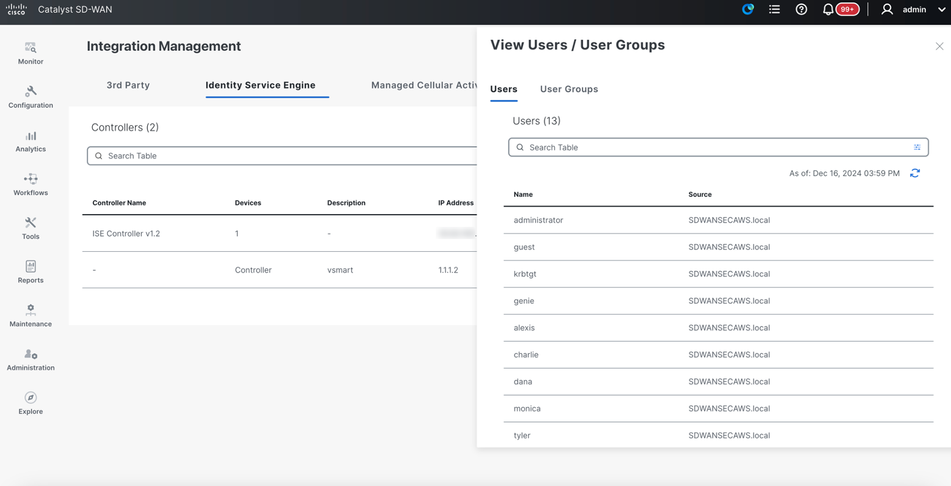
Click on 'User Group' tab.
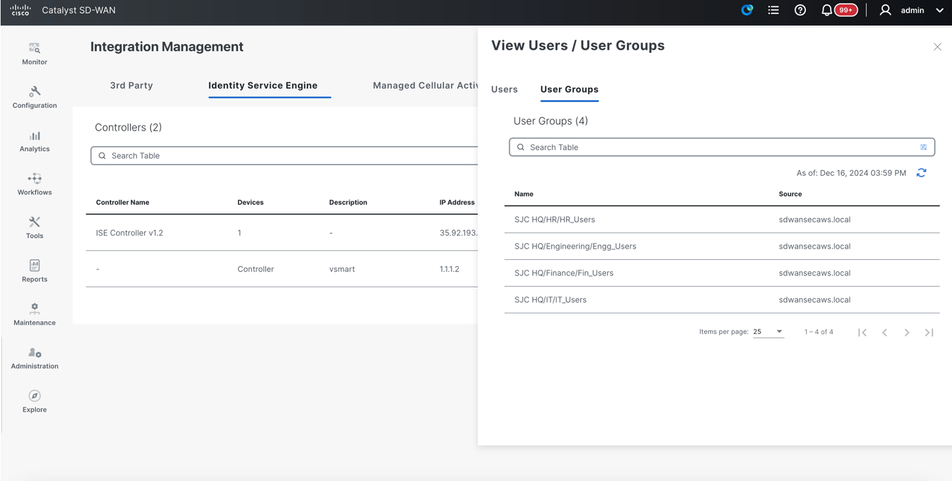
SGT integration: Check SGT info learned on Catalyst SD-WAN Manager from ISE
Same process to view SGT data. Click on 'View ISE Data'.