- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Cisco AI Endpoint Analytics and Cisco ISE Integration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
09-30-2020
02:28 PM
- edited on
09-30-2020
02:29 PM
by
kthiruve
![]()
- Introduction
- Integration
- AI Endpoint Analytics Profile Labels
- AI Endpoint Analytics Attributes shown in ISE
- AI Endpoint Analytics Attributes used in ISE Custom Profiler Policies
- ISE Profiler Policies used in ISE Authorization Rules
- Recap and Summary
Introduction
This article is being written to explain the integration between Cisco AI Endpoint Analytics and Cisco ISE with particular focus on the attributes AI Endpoint Analytics sends to ISE and how ISE interprets them in order to assign Profiles and authorization results.
Integration
ISE needs to be connected to Cisco DNA Center. Here is a guide for making this integration.
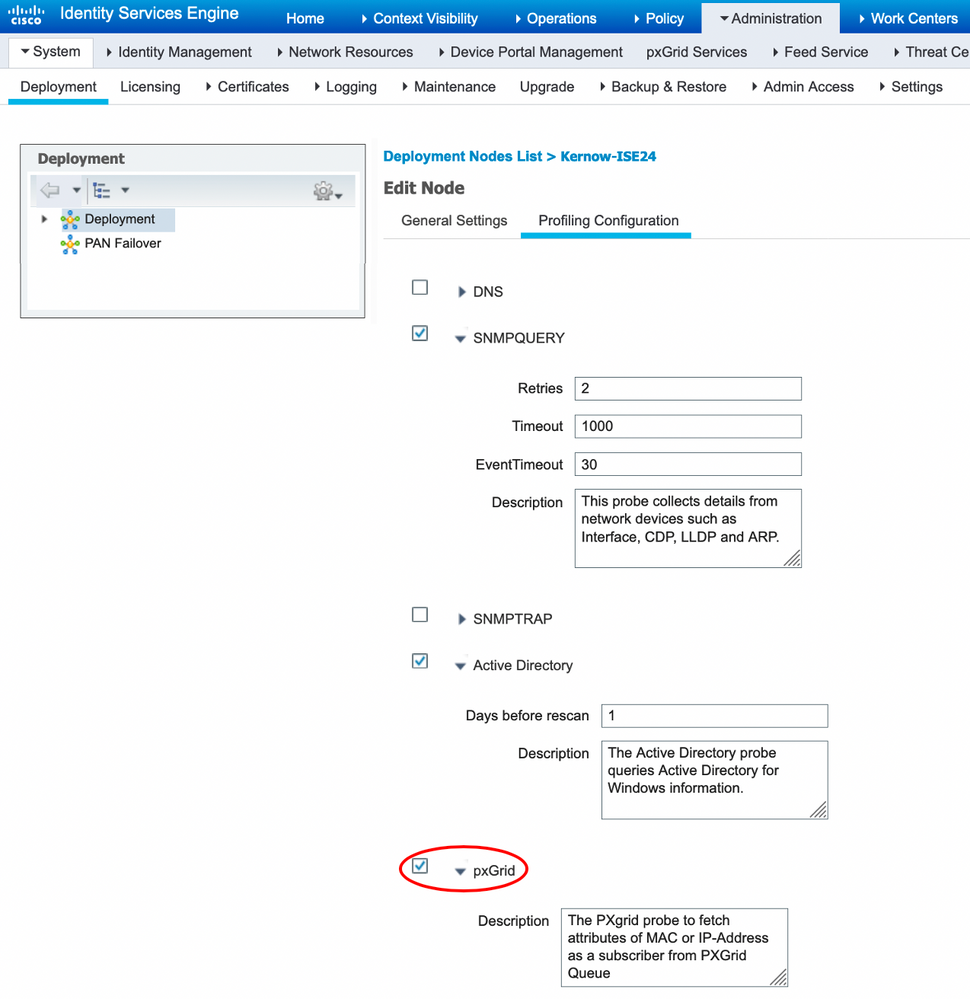
Additionally, the ISE pxGrid probe needs to be enabled which allows pxGrid to receive endpoint context from Cisco DNA Center/Endpoint Analytics as shown in the following example:
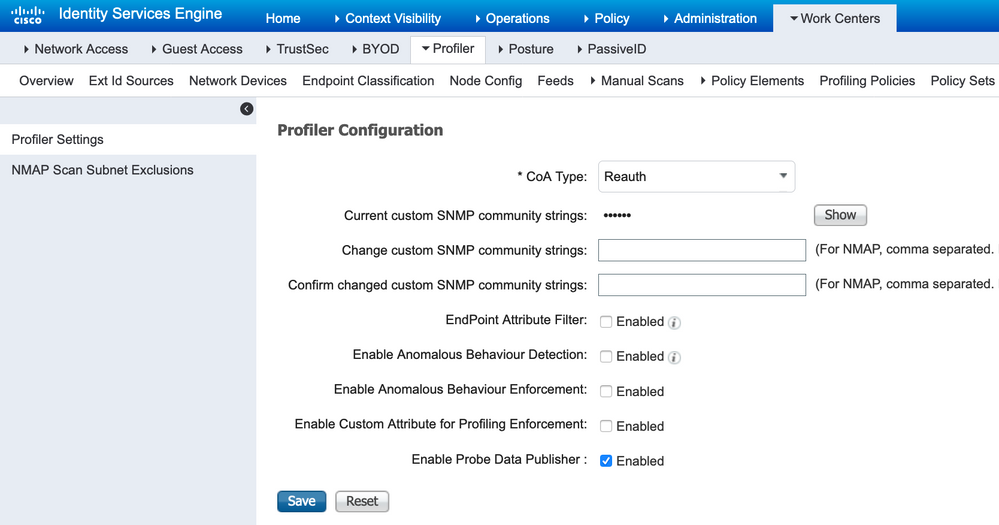
Also ensure the 'Probe Data Publisher' is enabled as shown below. This is needed for ISE to publish endpoint probe data to Cisco DNA Center/Endpoint Analytics via pxGrid.
AI Endpoint Analytics Profile Labels
When endpoints are discovered by Endpoint Analytics, up to four profile labels are assigned. For example:
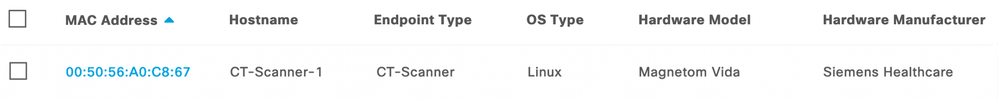
As can be seen from the above capture, the four profile label types are Endpoint Type, OS Type, Hardware Model and Hardware Manufacturer.
The discovered endpoint, a medical scanner in this instance, has labels in all four of these categories, as can be seen above.
When the MAC Address of the discovered endpoint is selected, further details are displayed on the right hand side of the display, including discovered attributes. The following capture shows the attributes placed under the IOTAsset heading:
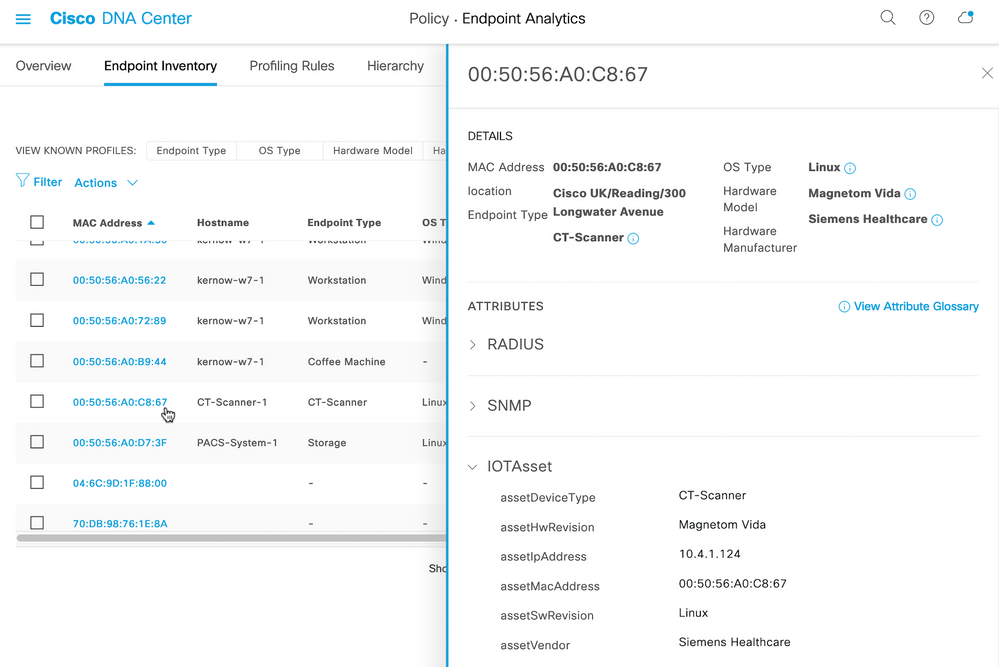
These are the attributes sent over to ISE from Endpoint Analytics via pxGrid. There is an attribute per profile label, as follows:
| Profile Label | IOTAsset Attribute |
| Endpoint Type | assetDeviceType |
| OS Type | assetSwRevision |
| Hardware Model | assetHwRevision |
| Hardware Manufacturer | assetVendor |
NOTE: If Endpoint Analytics learns of an endpoint from SD-AVC enabled Cat9Ks
but that endpoint is not learned from ISE, the attributes will NOT be sent
back to ISE in the existing design.
AI Endpoint Analytics Attributes shown in ISE
Within ISE, the attributes can be seen for that MAC address within Context Visibility (the attributes can be found near the bottom of the list):
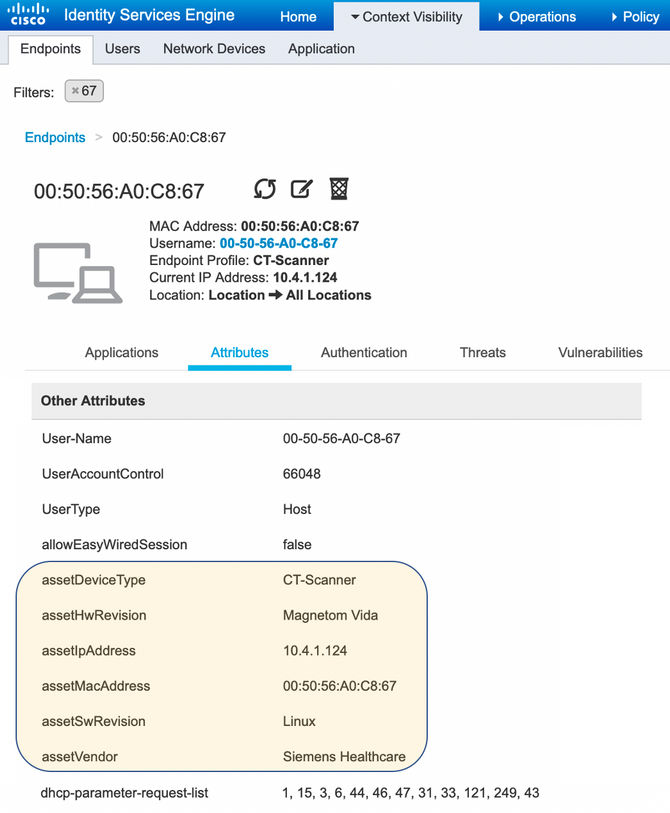
Once ISE has been sent these attributes, they can be used within custom Profiler Policies which in turn can be used in authorization conditions.
AI Endpoint Analytics Attributes used in ISE Custom Profiler Policies
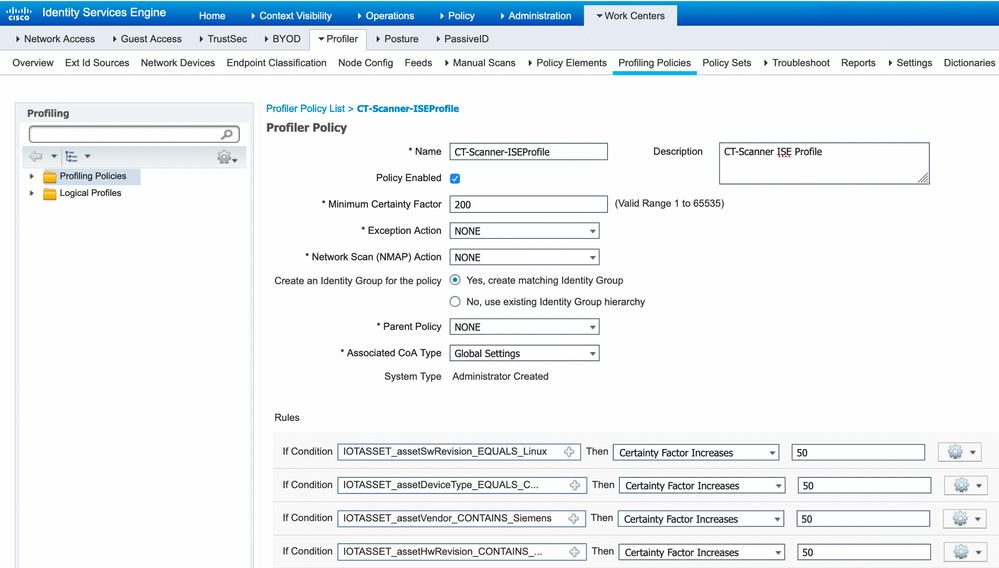
The following is an example ISE custom Profiler Policy (called CT-Scanner-ISEProfile) which uses all four Endpoint Analytics labels within the conditions:
The rules used in the policy are as follows:
| IOTASSET | Operator (in this example) | Value |
| assetSwRevision | Equals | Linux |
| assetDeviceType | Equals | CT-Scanner |
| assetVendor | Contains | Siemens |
| assetHwRevision | Contains | Megnetom |
As can be seen, the minimum certainty factor to assign this custom profile is 200 and the certainty factor for each matched condition is 50. Therefore all four conditions must match in order for this profile to be assigned.
Warning: Changing the Minimum Certainty factor to a higher number will affect all endpoints matched.
So, care must be taken when adding custom profiling policies to ensure only the intended endpoints are affected.
At this time of writing, the Value of 200 is much higher than the Total Certainty Factor of 130 in ISE.
Total Certainty Factor is the aggregated value of all profiles ISE touches to profile endpoints.
(From ISE user interface you can go to Context visibility > Endpoints > Endpoint Classification, click on the MAC
address for details to view the Total Certainty Factor .You can also view this by adding additional column
in Endpoint classification list table from the UI).
Best practice is toTest this with small number of endpoints by adding conditions based on AssetMACaddress, Calling station ID
or other attributes such as Network Device or Network Device Group (NDG) so that the change is limited.
As stated, this is just an example and any number of conditions can be used with appropriate certainty factors depending on the requirements.
A link to the ISE Profiler design guide has been provided at the bottom of this document for reference if further information is required on ISE Profiler operation.
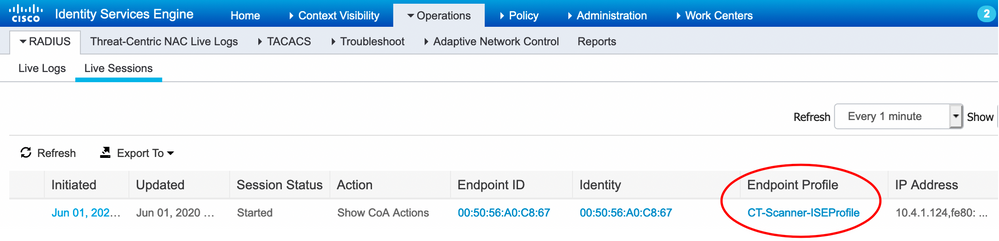
If this custom profile (CT-Scanner-ISEProfile) is matched and assigned to an endpoint then the assignment will be shown for the endpoint within the Live Session:
This ISE Profile can be used as a condition in authorization rules in order to authorize the endpoint (assign an SGT for example).
ISE Profiler Policies used in ISE Authorization Rules
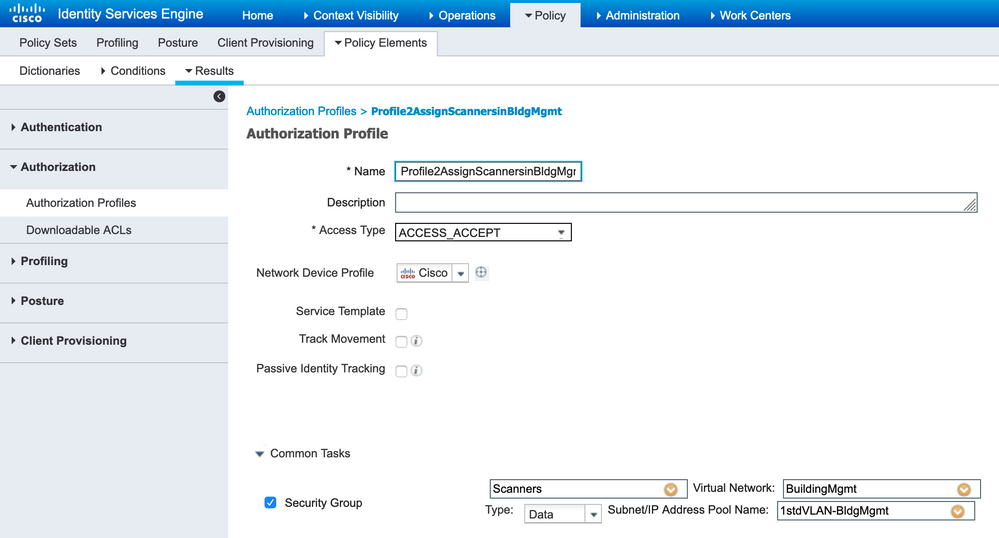
The following is an ISE authorization rule using the CT-Scanner-ISEProfile as a matching condition:
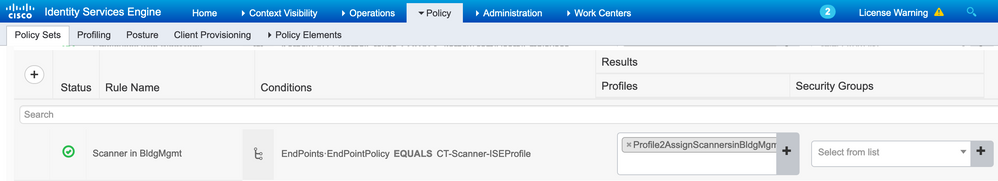
The resulting authorization profile assigns the appropriate SGT (Scanners) and VLAN (1stdVLAN-BldgMgmt) as shown below:
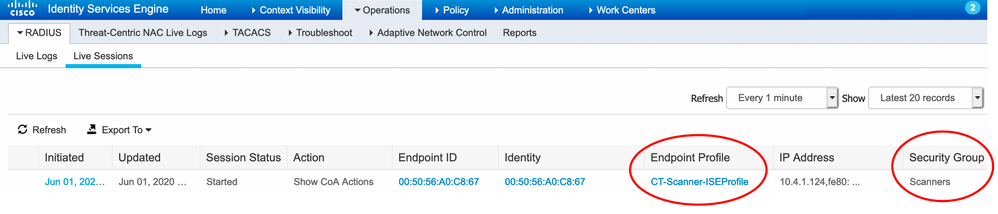
An authorized endpoint matching the ISE Profiler Policy and matching the Authorization Rule will show the assigned profile and SGT within the Live Session:
Recap and Summary
As a recap and summary, each endpoint has up to four profile labels assigned by Endpoint Analytics and four corresponding IOTAsset attributes are sent to ISE. These attributes are used as conditions in ISE custom Profiler Policies. The resulting ISE Profiles are then used as conditions in the ISE authorization rules in order to authorize the endpoints.
For further information on ISE Profiling, please reference the Profiling Design Guide: https://community.cisco.com/t5/security-documents/ise-profiling-design-guide/ta-p/3739456
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Jonathan
is it possible to populate ISE's endpoint DB from DNAC w/o any kind of network AuthC/AuthZ enforced on the switchports?
Let say i have NADs of interest managed by DNAC & EA AI enabled, also i have ISE integrated with DNAC, but no AAA enforcement is configured on any NAD's port. Will it do the job?
thank u
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Andrii Oliinyk Yes, it worked like that. Some of our lab setups have some endpoints that were discovered by CBAR and EA before the fabric site switched to Open/Closed mode and auth with ISE.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello
Is is mandatory to use DNA center for this AI integration or can we proceed without ?
Yes it is not mandatory, how does it works ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@antoine.bak.59 while there are multiple data sources for AI EA (e.g. Catalyst switches itself or CSNA) Catalyst Center remains the "brain" and dashboard for AI EA. So yes, it's mandatory
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: