- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Cisco SD-WAN Cloud Hosting with AWS cloud services-V1-Part |
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-25-2022 07:22 AM - edited 11-25-2022 07:28 AM
Cisco SD-WAN Cloud Hosting with AWS cloud services-Version |
Brief about the article
Today we are going to write about the Cisco SD-WAN Solution (Viptela) and integration with Amazon Web Services (AWS), which is, allows enterprises to seamlessly add AWS resources to their Wide Area Network.
AS the Name of this article, the purpose of this article to explain the sdwan cloud hosting and amazon web services and how it will help the organization to speed up the operations and reduces the cost with a fully resilience and high availability.
Cisco SD-Wan and AWS services deliver a powerful solution that will help the customers to achieve more goals with very efficiency including the Unified management, Automation, Secure cloud platform, as we see most of the IT transform to the cloud with multi models even IAAS , PAAS, SAAS , Cisco and AWS come on the stage to help the customers achieve this with a smoothly process and highly quality of experience which the most important part of the transformation.
Introduction
Let us take a brief about the below address of Sdwan Solution and SDWAN Components and Amazon web services.
- What is SD-WAN ?
- Why SD-WAN Solution?
- How many planes in the SDN?
- What is the Main Components of the SD_WAN solution?
- What is SD-WAN Policy?
- How SD-WAN Policy will help my organization to deliver with high quality of experience?
- What is the Quality of experience?
- What is AARP?
- How SD-WAN understand the APP?
- More and more and More get your coffee, concentrate, and let’s start the journey
What is SD-WAN?
SD-WAN is Software define wide area network and SD-WAN is key part of the technology of software-defined networking. SDN is a centralized approach to network management which abstracts the underlying network infrastructure away from its applications ,SD-WAN has more advantage such as automation, simplification of operations, provisioning, monitoring, Application Aware and smart troubleshooting.
Why SD-WAN solution?
SD-WAN solution has major advantages but the most important of them is Cost &user experience let's imagine the connection with traditional wide area network (WAN) when users at the branch want to connect to applications hosted on servers in the data center through MPLS , look to cost & t-shoot , SD-WAN will reduce cost here because the solution Support for all typed of connections (4G, 5G, Broadband , MPLS that means you can select cheaper connection options for low-priority traffic and high cost for high-priority traffic.can help a branch router avoid loss, latency and jitter within the network, SD-WAN give you ease of management via your single pane of glass interface, Increasing bandwidth through the activate & backup links and dynamic load-balancing, Delivering faster cloud access by enabling direct internet access at the branch .As we are seeing today all business go with Software as a Service (SaaS) and Infrastructure as a Service (IaaS) across multiple clouds, IT departments are struggling with providing a satisfactory experience for business-critical applications, SD-WAN Delivering faster cloud access by enabling direct internet access
How many planes in the Cisco SD-WAN solution?
Cisco SD-WAN provides a clear separation between management plane, control plane, and data plane, Cisco SD-WAN solution contains four planes < Management plane , Control Plane , orchestration plane , Data plane > An important consequence of the software-defined networking principles is the separation of control plan and data plan
between the definition of network policies and the forwarding of traffic.This separation is key to the desired flexibility, breaking the network control problem into pieces, and making it easier to create and introduce new abstractions in networking, simplifying network management and facilitating network evolution and innovation.
What is the components of cisco SD-WAN solution ?
The Cisco SD-WAN solution contains four key components responsible for each plane :
1-Cisco vManage :- Cisco V-manage is used to handle the management plane and represents the user interface of the solution.
2-Cisco vSmart :- v-Smart is the brain of the solution and exists within the control plane, v-Smart is the component responsible for enforcing these policies centrally and exchange the routing information.
3-Cisco vBond :- v-Bond is the orchestration plane responsible for on boarding the device into the SD-WAN fabric and Zero-Touch Provisioning process as well as first-line to authentication, v-Bond is responsible Network Address Translation (NAT) traversal.
NOTE: Cisco SD-WAN is based on the zero-trust model. All of the components mutually authenticate each other, and all of the edge devices are authorized before they are allowed onto the network.
4- Edge routers :- Edge router is data plane and Edge routers are responsible for establishing the network fabric and forwarding traffic.
- SD-Wan Policy :-
Viptela SD-WAN classified two types ( centralized policies or localized policies ) .
- The difference between ( centralized policies or localized policies )
Centralized policies : Those policies that are applied on the vSmart on the overlay network.
Localized policies : Those policies that are applied locally on the vEdge routers on the overlay network .
Centralized policies has two polices ( Control Policy and data Policy )
Localized Policy : Pushed from vManage directly to Edge devices via a NETCONF transaction – affects will happened for specific devices requiring policies.
Centralized Control policies :- Used to manipulate the propagation of routing information in the control plane including OMP, TLOC, VPN Services .
Centralized Data policies : Commonly used to accomplish (DIA) for specific applications, network service insertion, Also data plane manipulations such as packet Forwarding Error Correction (FEC) .
NOTE : In traditional wan , configurations are typically applied on a device thorough CLI but cisco SD-WAN is came with a new era of the network which's SDN and it has been designed to overcome this by implementing a centralized management plane that implement on all devices without any human error.
NOTE : Before Appalling any policy please be consider this all vEdges routers will sent the local site network to vSmart controller via OMP protocols , All vEdges will send all TLOC routes to vSmart controller via OMP , All vEdge Router will send all service Routes to all vSmart via OMP.
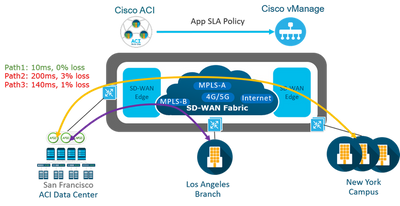
- Application Aware Routing
AAR is identify business critical traffic and specify the required SLA for that traffic classified . Viptela SD-WAN provides the ability to use multiple transports such as MPLS , BIZ-Internet, broadband , Etc... more than one method with high availability which 's will effect to the cost and operation . It provides the ability to use intelligent method through SLA detection for the application to used different transports based on the status .
Application-aware routing directs traffic based upon an application SLA LIST parameters and this defined application policies done though the vmanage and push to vSmart then to all SD-wan fabric Traffic is automatically sent to WAN links that have the important network characteristics and meet the SLA conditions to support these applications in production .
- SD-wan Security Features include IPS/IDS services
As we know the security is a critical part of today's networking infrastructure, Cisco Viptela SD-WAN align itself with this and from version 18.0 to latest version 20.9 the intrusion prevention/intrusion detection systems and URL filtering is available , and can apply this services for all the SD-WAN fabric .
- Unified communication Voice
Cisco Unified Communications requires that Cisco vManage be running Cisco SD-WAN Release 20.1. You can configure feature templates and voice policies to enable Cisco Unified Communications voice services for supported routers. These templates and policies configure parameters for FXO, FXS . When Cisco voice services are enabled, routers can process calls for various endpoints, including voice ports, POTS dial peers, SIP dial peers, and phone profiles in Cisco Unified Survivable Remote Site Telephony mode. Also voice policy defines how the system define and manipulates calls for various endpoint types. Endpoints include voice ports, POTS dial peers, SIP dial peers, and Survivable Remote Site Telephony .
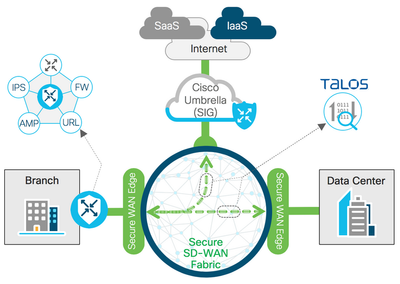
Cisco Viptela with Cisco umbrella (Golden hours of the cloud security services)
Integration with Cisco umbrella
The security, availability, visibility, and performance of the IT sector are the key foundation of a solid business and service environment.
- what you will do if the attacker pivots and enter your network infrastructure to get your sensitive data, attackers need to register with your domain to start his attack, all of this will happen once you respond to the incident.
-Cisco umbrella comes to secure your sensitive data within more than 20x data centers -WW- around the world and tied with a cisco Talos operation center team.
-Cisco Umbrella offers the protection for both enterprise, home network, any connect, through the filtering of all DNS requests that are done under your domain and determine the URL , Cisco Umbrella is a secure cloud platform that provides you a defense against threats, Umbrella is DNS and IP layers, Cisco Umbrella secures your enterprise from malware, Phishing Etc...
Cisco Umbrella provides complete visibility into internet activity , Cisco Umbrella integrations with the other security solutions and the main one here is VIPTELA SD-WAN , Cisco Umbrella has latest updated reputation list.
NOTE: You can get the Cisco umbrella solution in your enterprise within 10 minutes .
Cloud onRamp for Saas & laas :-
Cloud OnRamp for SaaS optimizes the performance of Software as a Service (SaaS) cloud applications based on network loss and latency SLA . Cloud OnRamp for SaaS provides clear visibility of the performance of individual applications and automatically chooses the best path for each one even MPLS , BIZ-Internet , 4 G Etc...
Although Cloud onRamp addresses both IaaS and SaaS providers, it's operate for the two types of cloud. With IaaS providers, such as AWS and Azure , Cloud OnRamp for SaaS calculates a value called the Viptela Quality of Experience , you also enable Cloud OnRamp for SaaS on the gateway site , viptela support some of the application now such as Microsoft Office 365 , oracle , sales forces , Zoho , Etc...
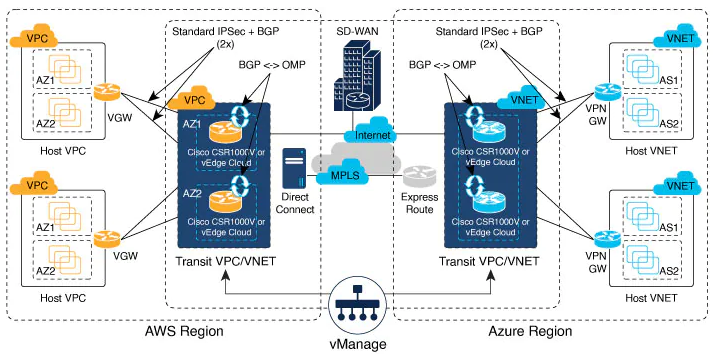
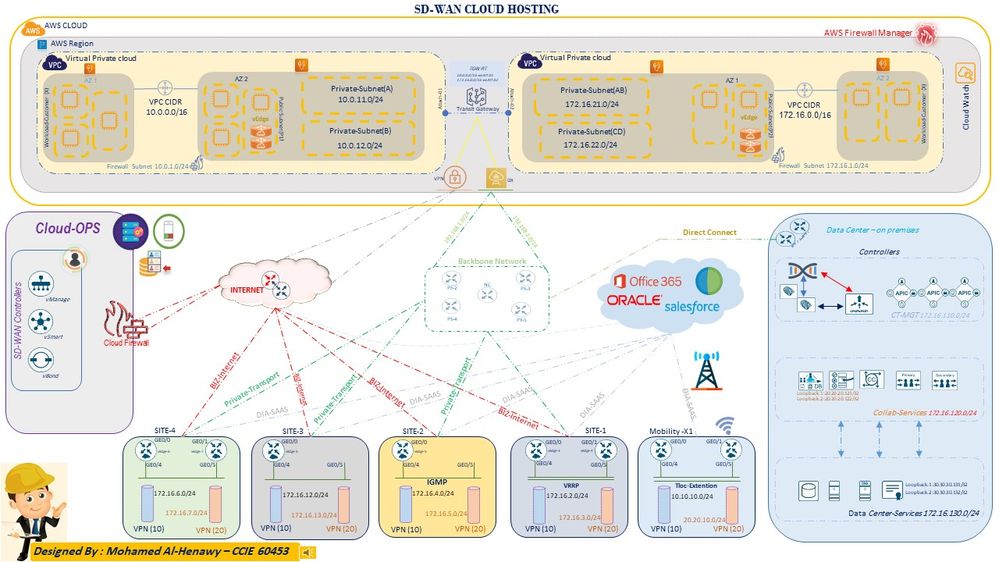
Cloud OnRamp for IaaS you can read more helpful details here :
The Cloud onRamp for IaaS works in conjunction with AWS virtual private clouds (VPCs) and Azure virtual networks (VNets). The following image provides a high level overview of multi-cloud onRamp for IaaS.
Here we have a good brief about viptela solution let's jump to Amazon web services , Let us take a brief about the below address of Amazon web services.
What is Amazon web services platform ?
why we are using the cloud ?
what is the types of cloud computing ?
what is deployment models of the cloud computing ?
what is VPC ?
What is AZ?
what is the type connection available on AWS ?
What is VPC peering ?
what is the best way two communicate between VPC's ?
What AWS cloud watch ?
ETC..........
- What is AWS platform ?
AWS is Amazon web services which is provide cloud computing services widely also including infrastructure as a services , Platform as a services , software as a services , AWS platform have multiple services such as storage services , data base services , network services , security services , governance services, Etc....
why we are using the cloud ?
As we know currently all the data centers based on the CAPEX (Capital Expenditure ) model which's install all the hardware and software on-premises with a fully operation including resources and experts engineers . ETC... which's effect to the cost and operation headache + some of vendors their devices support for 3 or 5 years only then organization have to change them to get the fully support and meet the security compliance or standardization of the operation , in the another side of the cloud the model is OPEX ( Operating Expense ) which is pay as you use which is very attractive for any organization plus fully hosting for all the computes and storage and security services , ETC.... which's will reduce the cost of the operation and reduce the operation headache also will guaranty to deliver availability & resilience services .
Good Example : OPEX looks like the electric and water services at your home
what is the models of cloud computing ?
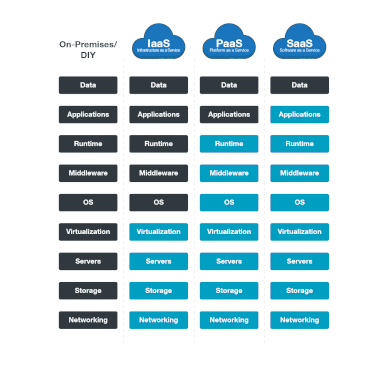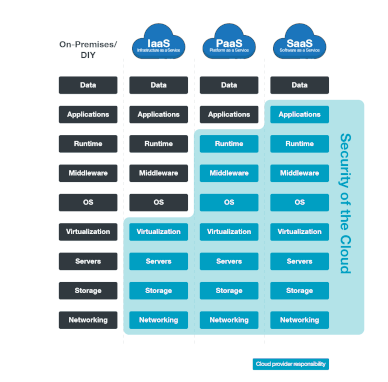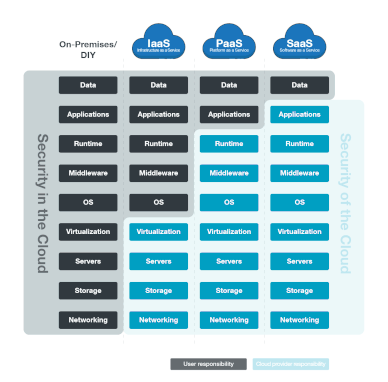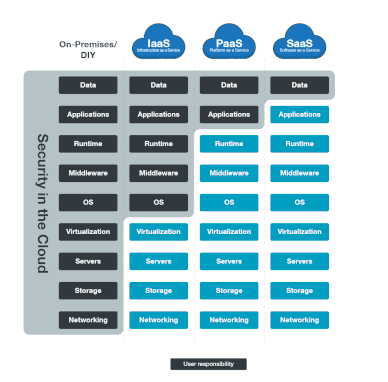
Cloud modules ( IAAS , PAAS , SAAS , STAAS , DBAAS , DRAAS , CAAS , XAAS , ETC.....
- IAAS : Infrastructure as a services which is provide network , storage space , HV of the computer , It's provide the customer high flexibility of the management of these resources .
- PAAS : Platform as a services : It's provide fully platform including Network , Storage , , Hardware , HV, Operating system and the customer only manage own database of his application which's help to focus more in the deployment and app programing and was will manage all other .
- SAAS : Software as a services It's provide fully & Completed solution including Network , Storage , , Hardware , HV, Operating system, Database , Application Example ( office 356 , ZOHO , Whatsup , ETc....
- STAAS : Storage as a services Which is provide the customer Storage services .
- DBAAS : Database as a services Which is provide the customer database with magical migration tools .
- DRAAS : Disaster recovery as a services Which is provide the customer Disaster Recovery solution with
- DAAS : Desktop as a services which is allow the organization to access computing capacity from third party server.
- CAAS : Communication as a services it's allow the organization to access variety of communication tools and applications like cisco webex , Zoom, Etc...
- XAAS : Anything as a services which's general describe for any services related to the cloud and remote access which is will keep the businesses to stay abreast and align with the latest tech.
what is deployment models of the cloud computing ?
There 's 3x cloud computing deployment models which is ( Cloud , Hybrid, On-Premises )
Cloud : It's fully deployed in the cloud and all the application run in the cloud .
Hybrid : It's a way to connect between the application hosting in the cloud platform and resources that located in the data center.
On-Premises : It's private cloud which is hosting all the Hardware and software on own data center and this way is prefer for some Government and this model looks like Legacy IT .
what is VPC ?
It's virtual private cloud which is give the customer ability to access the AWS resources through virtual network and all of this based on the virtual not hardware or physical connection required .
What is AZ?
It's availability zone , AWS have multiple region around the world and each region has 2 or 3 availability zone, each availability zone have separate HW,Connecton , ETc... which independent AZ , The main propose of the AZ is redundancy because if one workload fail it's able to shift to another AZ but in the same region which 's know as Multi-AZ .
what is the type connection available on AWS ?
AWS have multiple options to connect with your VPC such ( Virtual private network , AWS Direct connect , VPC endpoint , AWS internet gateway , AWS nat gateway , ETC...
what is the best way two communicate between VPC's ?
AWS has two way to communicate between the VPC's :
1- VPC peering : which connect two vpc's together with different subnet to avoid looping , and VPC is not transitive connection so you cannot connect there VPC together through transitive VPC peer .
Example : Solution has 3 x VPC's ( VPC-A , VPC-B , VPC-C ) VPC A & B peering with each other , VPC A & C Peering with each other BUT VPC B cannot Reach to VPC C trough VPC A , why because as we mentioned VPC peering not transitive connection .
2- AWS Transit Gateway : Transit gateway is next generation of the VPC's connections and it's transitive connection and you can connect multiple VPC's together through AWS transit gateway with Difference subnet to avoid the looping , AWS transit gateway can connect on-premise DC with AWS transit gateway through Direct connect or through VPN connection .
Example : Solution has 3x VPC's ( VPC-A , VPC-B , VPC-C ) and 2 x On-premise DC ( DC-1 , DC-2 ) now ( VPC-A , VPC-B , VPC-C ) all of them connect direct with Transit gateway through TGW-Attachment and ( DC-1 ) connect direct with AWS transit gateway through Direct connect & ( DC-2 ) connect with Transit gateway though VPN, So now all the endpoints connect with direct connect can reach to each other through transit gateway and for sure if you want to do some restriction we have to do through some policy and public and private VIF and the is advanced part we can write about it later on
What AWS cloud watch ?
AS we mentioned above AWS have multiple services so cloud watch is one of them and it's very important tools because it's used for monitoring data and application on AWS and manage actionable insight for AWS .
NOTE : Cloud watch support for AWS , Hybrid , On-premises applications and Resources applicable to work with it .
What is the AWS DPD ?
AWS DPD ( Data Packet detection ) is the service to detect the liveliness of the ipsec (phase 1) of the vpc connection , but this working during the phase 1 ( IKE phase1 ) because in the Phase 2 the tunnel already up and IKE phase already pass the test , In phase 2 we have one option to monitor the tunnel also It's called Tunnel monitor , If Data Packet Detection enable so contentiously send every 10 second like this :
Source send to the destination ( Customer X ) , ( Customer X ) have to replay by two answer .
1- Yes , I'm here ( Send send the Acknowledged )
2- No , I'm not here ( request time out )
Quick note : the Default time out is 30 seconds , DPD used port number 500 , DPD timeout Action ( Clear , Restart , NONE ) .
Cisco Viptela SD-WAN on your platform
The Cisco Viptela SD-WAN solution can deployed on a different platforms is called WAN Edge routers, which are available in different resources even Hardware or software , Regardless of which deployment is chosen, all WAN Edge routers will be part of the SD-WAN overlay fabric and managed by vManage.
NOW IT TIME TO MOVE TO OUR LAB & CONFIGURATION .
NOTE: AS This lab practice so some cloud services we will replace by the hosted devices on the virtualization platform , For AWS you have to create your own VPN and some Services to used it (PAYG).
| Initial Configuration for Devices & SD-WAN Controllers |
hostname SP-C
!
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip cef
ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface Ethernet0/0
ip address 10.10.1.1 255.255.255.0
!
interface Ethernet0/1
ip address 10.10.3.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.2.1 255.255.255.0
!
interface Ethernet0/3
ip address 10.10.4.1 255.255.255.0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 1.1.1.1
redistribute connected subnets
redistribute static subnets
network 1.1.1.1 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 65010
bgp router-id 1.1.1.1
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor SP-CORE peer-group
neighbor SP-CORE remote-as 65001
neighbor SP-CORE log-neighbor-changes
neighbor SP-CORE update-source Loopback0
neighbor 2.2.2.2 peer-group SP-CORE
neighbor 3.3.3.3 peer-group SP-CORE
neighbor 4.4.4.4 peer-group SP-CORE
neighbor 5.5.5.5 peer-group SP-CORE
!
address-family ipv4
network 1.1.1.1 mask 255.255.255.255
redistribute connected
redistribute static
redistribute ospf 1
neighbor SP-CORE send-community both
neighbor SP-CORE route-reflector-client
neighbor SP-CORE next-hop-self
neighbor 2.2.2.2 activate
neighbor 3.3.3.3 activate
neighbor 4.4.4.4 activate
neighbor 5.5.5.5 activate
exit-address-family
!
address-family vpnv4
neighbor SP-CORE send-community both
neighbor SP-CORE route-reflector-client
neighbor SP-CORE next-hop-self
neighbor 2.2.2.2 activate
neighbor 3.3.3.3 activate
neighbor 4.4.4.4 activate
neighbor 5.5.5.5 activate
exit-address-family
!
ip forward-protocol nd
!
ip http server
ip http secure-server
control-plane
hostname SP-PE-2
!
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip vrf DC-1
rd 1:1
route-target export 1:1
route-target import 1:1
route-target import 1:7
route-target import 2:2
route-target import 2:4
route-target import 4:1
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip vrf S4-V7
rd 1:7
route-target export 1:7
route-target import 1:7
route-target import 1:1
route-target import 2:2
route-target import 2:4
route-target import 4:1
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip cef
ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding S4-V7
ip address 192.168.140.1 255.255.255.0
!
interface Ethernet0/1
ip vrf forwarding AWS-DirectConnnect
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.1.2 255.255.255.0
!
router ospf 2 vrf AWS-DirectConnnect
redistribute bgp 65010 subnets
network 192.168.1.0 0.0.0.255 area 0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 2.2.2.2
redistribute bgp 65010 subnets
network 2.2.2.2 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 65010
bgp router-id 2.2.2.2
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 1.1.1.1 remote-as 65523
neighbor 1.1.1.1 update-source Loopback0
!
address-family ipv4
network 2.2.2.2 mask 255.255.255.255
redistribute ospf 1
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family ipv4 AWS-DirectConnnect
network 192.168.1.0
redistribute connected
redistribute static
redistribute ospf 2
neighbor 192.168.1.2 remote-as 65523
neighbor 192.168.1.2 activate
exit-address-family
!
address-family ipv4 vrf S4-V7
network 192.168.140.0
redistribute connected
redistribute static
neighbor 192.168.140.2 remote-as 65004
neighbor 192.168.140.2 activate
exit-address-family
!
ip forward-protocol nd
!
ip http server
ip http secure-server
!
control-plane
hostname SP-PE-3
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip vrf AWS-DirectConnnect-2
rd 2:2
route-target export 2:2
route-target import 2:2
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 4:1
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip vrf S1-V4
rd 2:4
route-target export 2:4
route-target import 2:4
route-target import 1:7
route-target import 1:1
route-target import 2:2
route-target import 4:1
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding S1-V4
ip address 192.168.110.1 255.255.255.0
!
interface Ethernet0/1
ip vrf forwarding AWS-DirectConnnect-2
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.2.2 255.255.255.0
!
router ospf 2 vrf AWS-DirectConnnect-2
redistribute bgp 65010 subnets
network 192.168.2.0 0.0.0.255 area 0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 3.3.3.3
redistribute bgp 65010 subnets
network 3.3.3.3 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 65010
bgp router-id 3.3.3.3
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 1.1.1.1 remote-as 65523
neighbor 1.1.1.1 update-source Loopback0
!
address-family ipv4
network 3.3.3.3 mask 255.255.255.255
redistribute ospf 1
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family ipv4 vrf AWS-DirectConnnect-2
network 192.168.2.0
redistribute connected
redistribute static
redistribute ospf 2
neighbor 192.168.2.2 remote-as 65523
neighbor 192.168.2.2 activate
exit-address-family
!
address-family ipv4 vrf S1-V4
network 192.168.110.0
redistribute connected
redistribute static
neighbor 192.168.110.2 remote-as 65001
neighbor 192.168.110.2 activate
exit-address-family
!
ip forward-protocol nd
ip http server
ip http secure-server
control-plane
hostname SP-PE-4
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip vrf S3-V1
rd 4:1
route-target export 4:1
route-target import 4:1
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 2:2
route-target import 4:6
route-target import 5:3
route-target import 5:1
!
ip vrf S4-V6
rd 4:6
route-target export 4:6
route-target import 4:6
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 2:2
route-target import 4:1
route-target import 5:3
route-target import 5:1
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
!
interface Loopback0
ip address 4.4.4.4 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding S4-V6
ip address 192.168.40.1 255.255.255.0
!
interface Ethernet0/1
ip vrf forwarding S3-V1
ip address 192.168.30.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.3.2 255.255.255.0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 4.4.4.4
network 4.4.4.4 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 65010
bgp router-id 4.4.4.4
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 1.1.1.1 remote-as 65010
neighbor 1.1.1.1 update-source Loopback0
!
address-family ipv4
network 4.4.4.4 mask 255.255.255.255
redistribute ospf 1
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family ipv4 vrf S3-V1
network 192.168.30.0
redistribute connected
redistribute static
neighbor 192.168.30.2 remote-as 65003
neighbor 192.168.30.2 activate
exit-address-family
!
address-family ipv4 vrf S4-V6
network 192.168.40.0
redistribute connected
redistribute static
neighbor 192.168.40.2 remote-as 65004
neighbor 192.168.40.2 activate
exit-address-family
!
ip forward-protocol nd
!
ip http server
ip http secure-server
control-plane
hostname SP-PE-5
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip vrf S1-V3
rd 5:3
route-target export 5:3
route-target import 5:3
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 2:2
route-target import 4:1
route-target import 4:6
route-target import 5:1
!
ip vrf S2-V1
rd 5:1
route-target export 5:1
route-target import 5:1
route-target import 1:7
route-target import 1:1
route-target import 2:4
route-target import 2:2
route-target import 4:1
route-target import 4:6
route-target import 5:3
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password Cisco
mpls ldp neighbor 2.2.2.2 password Cisco
mpls ldp neighbor 3.3.3.3 password Cisco
mpls ldp neighbor 4.4.4.4 password Cisco
mpls ldp neighbor 5.5.5.5 password Cisco
!
cts logging verbose
!
redundancy
!
interface Loopback0
ip address 5.5.5.5 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding S1-V3
ip address 192.168.10.1 255.255.255.0
!
interface Ethernet0/1
ip vrf forwarding S2-V1
ip address 192.168.20.1 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.4.2 255.255.255.0
!
router ospf 1
mpls ldp autoconfig area 0
router-id 5.5.5.5
network 5.5.5.5 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 65010
bgp router-id 5.5.5.5
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 1.1.1.1 remote-as 65010
neighbor 1.1.1.1 update-source Loopback0
!
address-family ipv4
network 5.5.5.5 mask 255.255.255.255
redistribute ospf 1
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 send-community both
neighbor 1.1.1.1 next-hop-self
exit-address-family
!
address-family ipv4 vrf S1-V3
network 192.168.10.0
redistribute connected
redistribute static
neighbor 192.168.10.2 remote-as 65001
neighbor 192.168.10.2 activate
exit-address-family
!
address-family ipv4 vrf S2-V1
network 192.168.20.0
redistribute connected
redistribute static
neighbor 192.168.20.2 remote-as 65002
neighbor 192.168.20.2 activate
exit-address-family
!
ip forward-protocol nd
!
ip http secure-server
control-plane
!
hostname Public-Internet
boot-start-marker
boot-end-marker
!
aaa new-model
!
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
ip cef
ipv6 cef
!
multilink bundle-name authenticated
!
cts logging verbose
!
redundancy
!
interface Ethernet0/0
ip address 92.68.10.1 255.255.255.0
!
interface Ethernet0/1
ip address 92.68.110.1 255.255.255.0
!
interface Ethernet0/2
ip address 92.68.2.1 255.255.255.0
!
interface Ethernet0/3
ip address 92.68.20.1 255.255.255.0
!
interface Ethernet1/0
ip address 92.68.40.1 255.255.255.0
!
interface Ethernet1/1
ip address 92.68.140.1 255.255.255.0
!
interface Ethernet1/2
ip address 92.68.1.1 255.255.255.0
!
interface Ethernet1/3
ip address 92.68.30.1 255.255.255.0
!
ip forward-protocol nd
!
ip route 200.200.200.0 255.255.255.0 92.68.1.2 10
ip route 200.200.200.0 255.255.255.0 92.68.2.2 20
control-plane
!
---------------------------------------------------------------------------------------------------------
Public Internet Verification :
DC-ED-1(config)#do pin www.google.com
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 114/126/135 ms
------------------------------------------
DC-ED-2(config)#do pin www.google.com
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 105/114/120 ms
------------------------------------------
Public-Internet(config)#do ping www.google.com
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 105/115/122 ms
Public-Internet(config)#
------------------------------------------
MPLS Verification :
SP-C(config)#do show mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 2.2.2.2/32 5428 Et0/0 10.10.1.2
17 Pop Label 3.3.3.3/32 6608 Et0/2 10.10.2.2
18 Pop Label 4.4.4.4/32 1770 Et0/1 10.10.3.2
19 Pop Label 5.5.5.5/32 2360 Et0/3 10.10.4.2
SP-C(config)#do show mpls ldp neighbor
Peer LDP Ident: 2.2.2.2:0; Local LDP Ident 1.1.1.1:0
TCP connection: 2.2.2.2.38221 - 1.1.1.1.646
State: Oper; Msgs sent/rcvd: 1689/1688; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/0, Src IP addr: 10.10.1.2
Addresses bound to peer LDP Ident:
10.10.1.2 2.2.2.2
Peer LDP Ident: 3.3.3.3:0; Local LDP Ident 1.1.1.1:0
TCP connection: 3.3.3.3.30480 - 1.1.1.1.646
State: Oper; Msgs sent/rcvd: 1683/1688; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.2.2
Addresses bound to peer LDP Ident:
10.10.2.2 3.3.3.3
Peer LDP Ident: 4.4.4.4:0; Local LDP Ident 1.1.1.1:0
TCP connection: 4.4.4.4.49818 - 1.1.1.1.646
State: Oper; Msgs sent/rcvd: 1686/1691; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/1, Src IP addr: 10.10.3.2
Addresses bound to peer LDP Ident:
10.10.3.2 4.4.4.4
Peer LDP Ident: 5.5.5.5:0; Local LDP Ident 1.1.1.1:0
TCP connection: 5.5.5.5.34188 - 1.1.1.1.646
State: Oper; Msgs sent/rcvd: 1690/1693; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/3, Src IP addr: 10.10.4.2
Addresses bound to peer LDP Ident:
10.10.4.2 5.5.5.5
------------------------------------------
SP-PE-2#show mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 1.1.1.1/32 0 Et0/2 10.10.1.1
17 Pop Label 10.10.2.0/24 0 Et0/2 10.10.1.1
18 Pop Label 10.10.3.0/24 0 Et0/2 10.10.1.1
19 Pop Label 10.10.4.0/24 0 Et0/2 10.10.1.1
20 17 3.3.3.3/32 0 Et0/2 10.10.1.1
21 18 4.4.4.4/32 0 Et0/2 10.10.1.1
22 19 5.5.5.5/32 0 Et0/2 10.10.1.1
23 No Label 192.168.1.0/24[V] \
3990 aggregate/DC-1
24 No Label 192.168.140.0/24[V] \
570 aggregate/S4-V7
25 No Label 30.30.30.0/24[V] 570 Et0/1 192.168.1.2
26 No Label 92.68.1.0/24[V] 0 Et0/1 192.168.1.2
SP-PE-2#show mpls ldp neighbor
Peer LDP Ident: 1.1.1.1:0; Local LDP Ident 2.2.2.2:0
TCP connection: 1.1.1.1.646 - 2.2.2.2.38221
State: Oper; Msgs sent/rcvd: 1690/1691; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.1.1
Addresses bound to peer LDP Ident:
10.10.1.1 10.10.3.1 10.10.2.1 10.10.4.1
1.1.1.1
------------------------------------------
SP-PE-3(config)#do show mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 1.1.1.1/32 0 Et0/2 10.10.2.1
17 Pop Label 10.10.1.0/24 0 Et0/2 10.10.2.1
18 Pop Label 10.10.3.0/24 0 Et0/2 10.10.2.1
19 Pop Label 10.10.4.0/24 0 Et0/2 10.10.2.1
20 16 2.2.2.2/32 0 Et0/2 10.10.2.1
21 18 4.4.4.4/32 0 Et0/2 10.10.2.1
22 19 5.5.5.5/32 0 Et0/2 10.10.2.1
23 No Label 192.168.2.0/24[V] \
3420 aggregate/DC-2
24 No Label 192.168.110.0/24[V] \
570 aggregate/S1-V4
25 No Label 50.50.50.0/24[V] 2394 Et0/1 192.168.2.2
26 No Label 92.68.2.0/24[V] 0 Et0/1 192.168.2.2
SP-PE-3(config)#do show mpls ldp neighbor
Peer LDP Ident: 1.1.1.1:0; Local LDP Ident 3.3.3.3:0
TCP connection: 1.1.1.1.646 - 3.3.3.3.30480
State: Oper; Msgs sent/rcvd: 1691/1686; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.2.1
Addresses bound to peer LDP Ident:
10.10.1.1 10.10.3.1 10.10.2.1 10.10.4.1
1.1.1.1
------------------------------------------
SP-PE-4#sho mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 1.1.1.1/32 0 Et0/2 10.10.3.1
17 Pop Label 10.10.1.0/24 0 Et0/2 10.10.3.1
18 Pop Label 10.10.2.0/24 0 Et0/2 10.10.3.1
19 Pop Label 10.10.4.0/24 0 Et0/2 10.10.3.1
20 16 2.2.2.2/32 0 Et0/2 10.10.3.1
21 17 3.3.3.3/32 0 Et0/2 10.10.3.1
22 19 5.5.5.5/32 0 Et0/2 10.10.3.1
23 No Label 192.168.30.0/24[V] \
1140 aggregate/S3-V1
24 No Label 192.168.40.0/24[V] \
570 aggregate/S4-V6
SP-PE-4#show mpls ldp neighbor
Peer LDP Ident: 1.1.1.1:0; Local LDP Ident 4.4.4.4:0
TCP connection: 1.1.1.1.646 - 4.4.4.4.49818
State: Oper; Msgs sent/rcvd: 1695/1690; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.3.1
Addresses bound to peer LDP Ident:
10.10.1.1 10.10.3.1 10.10.2.1 10.10.4.1
1.1.1.1
------------------------------------------
SP-PE-5#show mpls forwarding-table
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
16 Pop Label 1.1.1.1/32 0 Et0/2 10.10.4.1
17 Pop Label 10.10.1.0/24 0 Et0/2 10.10.4.1
18 Pop Label 10.10.2.0/24 0 Et0/2 10.10.4.1
19 Pop Label 10.10.3.0/24 0 Et0/2 10.10.4.1
20 16 2.2.2.2/32 0 Et0/2 10.10.4.1
21 17 3.3.3.3/32 0 Et0/2 10.10.4.1
22 18 4.4.4.4/32 0 Et0/2 10.10.4.1
23 No Label 192.168.10.0/24[V] \
1140 aggregate/S1-V3
24 No Label 192.168.20.0/24[V] \
1140 aggregate/S2-V1
SP-PE-5#show mpls ldp neighbor
Peer LDP Ident: 1.1.1.1:0; Local LDP Ident 5.5.5.5:0
TCP connection: 1.1.1.1.646 - 5.5.5.5.34188
State: Oper; Msgs sent/rcvd: 1699/1696; Downstream
Up time: 1d00h
LDP discovery sources:
Ethernet0/2, Src IP addr: 10.10.4.1
Addresses bound to peer LDP Ident:
10.10.1.1 10.10.3.1 10.10.2.1 10.10.4.1
1.1.1.1
------------------------------------------------------------------------------------
BGP Verification :
SP-C(config)#do show ip bgp vpnv4 all summary
Neighbor V AS Msg Rcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
2.2.2.2 4 50000 230 234 13 0 0 03:16:52 4
3.3.3.3 4 50000 230 234 13 0 0 03:16:52 4
4.4.4.4 4 50000 227 237 13 0 0 03:16:52 2
5.5.5.5 4 50000 228 236 13 0 0 03:16:52 2
------------------------------------------
SP-PE-2(config)#do show ip bgp vpnv4 all summary
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
1.1.1.1 4 50000 1107 1102 59 0 0 16:29:01 8
192.168.1.2 4 65000 1138 1152 59 0 0 17:09:28 3
192.168.140.2 4 65004 0 0 1 0 0 19:09:28 3
------------------------------------------
SP-PE-3(config)#do show ip bgp vpnv4 all summary
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
1.1.1.1 4 50000 1105 1111 59 0 0 16:32:19 8
192.168.2.2 4 65000 1131 1147 59 0 0 17:03:38 3
192.168.110.2 4 65001 0 0 1 0
------------------------------------------
SP-PE-4(config)#do show ip bgp vpnv4 all summary
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
1.1.1.1 4 50000 1114 1102 67 0 0 16:33:40 10
192.168.30.2 4 65003 0 0 1 0 0 never Idle
192.168.40.2 4 65004 0 0 1 0
------------------------------------------
SP-PE-5(config)#do show ip bgp vpnv4 all summary
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
1.1.1.1 4 50000 1112 1107 69 0 0 16:34:27 10
192.168.10.2 4 65001 0 0 1 0 0 never Active
192.168.20.2 4 65002 0 0 1 0
------------------------------------------------------------------------------------
**Viptela Controllers initial configuration**
NOTE : All Controllers Work with version ((((viptela 20.3.4))))
{Vmanage initial configuration }
configure
system
host-name vmanage
system-ip 100.100.100.101
site-id 1
admin-tech-on-failure
organization-name "Cisco Sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$cUCfm1swmEQhJ1zJ$pnOPy.FKMGCxzM.FPeiEh0RNQXP5SXXBgSn3X.qPC39vZnsOsBpfXpDKd/NyLimCwc6txSIMzax9wNI3OCxfk1
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
vpn 0
interface eth0
ip address 200.200.200.101/24
ipv6 dhcp-client
tunnel-interface
allow-service all
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
interface eth1
ip dhcp-client
no shutdown
!
ip route 0.0.0.0/0 192.168.205.1
!
------------------------------------------------------------------------------------
{Vsmart initial configuration }
configure
system
host-name vsmart
system-ip 100.100.100.102
site-id 1
admin-tech-on-failure
organization-name "Cisco Sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$heVRjPJAGcTR/AX5$TPN9s2iG1ogb7.3OtfeWCKieIx90KMuet2Vzg2Lr4c1g/sLziUAgQF20UgpWfMOL6AfH3Ek8MBtv4lVZe3RUa0
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
!
vpn 0
interface eth0
ip address 200.200.200.102/24
ipv6 dhcp-client
tunnel-interface
allow-service all
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service stun
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
!
------------------------------------------------------------------------------------
{Vbond initial configuration }
**Viptela Controllers initial configuration** Viptela Version 20.6.3.1
{Vmanage initial configuration }
configure
system
host-name vmanage
system-ip 100.100.100.101
site-id 1
admin-tech-on-failure
organization-name "Cisco Sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$cUCfm1swmEQhJ1zJ$pnOPy.FKMGCxzM.FPeiEh0RNQXP5SXXBgSn3X.qPC39vZnsOsBpfXpDKd/NyLimCwc6txSIMzax9wNI3OCxfk1
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
vpn 0
interface eth0
ip address 200.200.200.101/24
ipv6 dhcp-client
tunnel-interface
allow-service all
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
interface eth1
ip dhcp-client ( 192.168.205.179 )
no shutdown
!
ip route 0.0.0.0/0 192.168.205.1
!
{Vsmart initial configuration }
configure
system
host-name vsmart
system-ip 100.100.100.102
site-id 1
admin-tech-on-failure
organization-name "Cisco Sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$heVRjPJAGcTR/AX5$TPN9s2iG1ogb7.3OtfeWCKieIx90KMuet2Vzg2Lr4c1g/sLziUAgQF20UgpWfMOL6AfH3Ek8MBtv4lVZe3RUa0
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
!
vpn 0
interface eth0
ip address 200.200.200.102/24
ipv6 dhcp-client
tunnel-interface
allow-service all
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service stun
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
!
{Vbond initial configuration }
system
host-name vbond
system-ip 100.100.100.103
site-id 1
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco Sdwan"
clock timezone Asia/Riyadh
vbond 200.200.200.103 local
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$GcfTQKxQdG5jHL75$WwWDC6KW6zWUVhKDxgWpBo/EjGL8dyw A7/irYodz4ne5xYt1lgT.8gu.vkR2ngkIcNs/7JVDs2XV99UWrG0Ly1
!
user ciscotacro
description CiscoTACReadOnly
group operator
status enabled
!
user ciscotacrw
description CiscoTACReadWrite
group netadmin
status enabled
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 200.200.200.103/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
------------------------------------------------------------------------------------
Then We will access to vmanage as GUI https://192.168.205.179
Welcome to SD-WAN Viptela World
**** I hope that has been informative for you and thank you *****
Mohamed Alhenawy
CCIE#60453
-
Announcements
-
Assurance and Policy
-
Automation
-
Buying Recommendation
-
Catalyst 9000 Switches
-
Catalyst Switch
-
Cisco Annual Internet Report
-
Cisco DNA Automation
-
Cisco DNA Cloud
-
Cloud Networking
-
Configuration
-
LAN
-
LAN Switching
-
Network Management
-
NFVIS
-
Optical Networking
-
Other IPv6
-
Other Network Architecture
-
Other Networking
-
Other Routers
-
Other Routing
-
Other SD-WAN
-
Other Switches
-
Other Switching
-
Routing
-
Routing Protocols
-
SD-WAN
-
Software Upgrades
-
vEdge Routers
-
WAN
-
Wi-Fi 6
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Mohamed,
Another very useful article! Great Explanation and crazy LAB. I really appreciate your work!
Regards Rafael
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: