- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Configuration Template for SNMPv3
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
12-17-2022
02:13 PM
- edited on
07-27-2025
03:45 PM
by
![]() Rich R
Rich R
Table of Contents
- Table of Contents
- Automation
- Summary
- Terminology
- Security Levels
- Support
- Configuration Steps
- Create an SNMP Poller Access List
- Create SNMP Views
- Create SNMP Groups
- Create Read-Only SNMP Users
- Create Read-Write SNMP Users
- Frequently Used OIDs
- Verification
- References
Automation
Ansible Playbooks coming soon!
Summary
I frequently hear folks say "configuring SNMPv3 is too complicated" or "configuring SNMPv2 is easier". I'd like to dispel that myth! SNMP is a very powerful tool that can be used to retrieve information about an IOS XE device and make changes to a networking device. I agree that configuring SNMPv3 does have a few more commands, however, it is easy to understand, easy to configure and if possible we should always encrypt everywhere.
Dance like no one is watching, encrypt like everyone is watching!
Terminology
| Agent | The IOS XE device we will query |
| Authentication Password | A secret key used for authentication |
| Community String | A security string used in non-encrypted SNMP v1 & v2c |
| Get | An operation used by the SNMP manager applications to retrieve one or more values from the managed objects maintained by the SNMP agent |
| Get Next | An operation that retrieves the value of the next OID in the tree. GETNEXT can be used to retrieve the table data and also for variables that are not named. |
| Manager | A program, also known as, a network management station that runs on a host on the network. |
| MIB | Management Information Base. MIBs are a hierarchical collection of OIDs, typically in a text file format. |
| OID | Object Identifiers. OIDs uniquely identify managed objects in a MIB. When queried OIDs return information about the managed device. |
| Privacy Password | A secret key used for encryption |
| Set | An operation that is used by the Manager application to modify values on the Agent |
| SNMP View | Views define the level of access that the poller will have access to. |
| SNMP Group | Groups are mapped to SNMP Views |
| SNMP Poller | An application that queries network devices to obtain statistics about the device |
| SNMP User | Users are members of SNMP Groups |
| Walk | An operation that makes multiple Get Next requests |
Security Levels
There are 3 security levels defined in SNMPv3.
NoAuthNoPriv - Does not use authentication or encryption
AuthNoPriv - Uses authentication but not encryption
AuthPriv - Uses both authentication and encryption. Our example below will use this level.
Support
As of 2022, SNMPv3 support has been supported in IOS XE for over a decade. I've personally used the config below on 2960, 2960G, 2960X, 3560, 9200, 9300, ASR1000, ISR4k, and likely other platforms.
Configuring SNMPv3 means basically means setting up Users and Groups, sounds easy huh, keep reading!
Users should be configured with an Authentication Password and a Privacy Password. The AuthPass is used to authenticate the user and the PrivPass is used to encrypt the data that is sent between the devices. It's best to configure SNMP to use both an AuthPass and a PrivPass.
The Cisco supported Authentication Methods are MD5 and SHA. SHA is stronger and is widely supported. The Cisco supported Encryption \ Privacy algorithms are AES-128, AES-192, and AES-256. Some Network Manager products support AES 192 or AES 256 also. My recommendation is to use Auth=SHA and Priv=AES-128.
Update: note that SHA-2 is supported from IOS-XE 17.10 - see SHA-2 Support for SNMPv3 User Authentication for details.
I started using this template late in IOS 12.1 or 12.2 and I'm still using it in IOS XE 17.9. This template has been very reliable.
Configuration Steps
Create an SNMP Poller Access List
SNMP is a powerful service and should be treated like SSH or any Management Protocol. Only authorized IP addresses should be able to query your network devices.
!
configure terminal
ip access-list standard snmp-service
remark SNMP Poller Server #1
permit 192.168.100.101
remark SNMP Poller Server #2
permit 192.168.100.102
end
!
Create SNMP Views
These commands create a Read Only view and a Read Write view. Both views include the ALL OIDs on the Cisco device.
!
configure terminal
snmp-server view snmp-v3-ReadOnly-View iso included
snmp-server view snmp-v3-ReadWrite-View iso included
end
!
Create SNMP Groups
These groups are tied to the SNMP Views we created in the previous step. These commands create a Read Only group and a Read Write group.
Only IP Addresses that are defined in the ACL we created in the first step are permitted to query.
!
configure terminal
snmp-server group snmp-v3-ReadOnly v3 priv read snmp-v3-ReadOnly-View access snmp-service
snmp-server group snmp-v3-ReadWrite v3 priv write snmp-v3-ReadWrite-View access snmp-service
end
!
Create Read-Only SNMP Users
NOTE: I find that auth or priv passwords work best when they are letters and numbers and less than 15 characters long. Special characters may cause unexpected results.
Notice how these users are a member of the ReadOnly group that was created in the last step.
!
configure terminal
snmp-server user cacti-user snmp-v3-ReadOnly v3 auth sha AaBbCcDdEe1234 priv aes 128 123456789AaBbCc access snmp-service
snmp-server user read-only-user snmp-v3-ReadOnly v3 auth sha 5678MmNnOoPp priv aes 128 MnNnOo7890 access snmp-service
end
!
Create Read-Write SNMP Users
!
configure terminal
snmp-server user net-config-user snmp-v3-ReadWrite v3 auth sha 9876QqRrSsTt priv aes 128 TtUuVv3456 access snmp-service
end
!
Frequently Used OIDs
These are some common OIDs that all Cisco devices should respond to. These are very good for testing.
| OID | OID Name | Friendly Description |
| 1.3.6.1.2.1.1.1 | sysDescr | A textual description of the entity. |
| 1.3.6.1.2.1.1.3 | sysUpTime | The time (in hundredths of a second) since the network management portion of the system was last re-initialized. |
| 1.3.6.1.2.1.1.5 | sysName | An administratively-assigned name for this managed node. By convention, this is the node's fully-qualified domain name. |
Verification
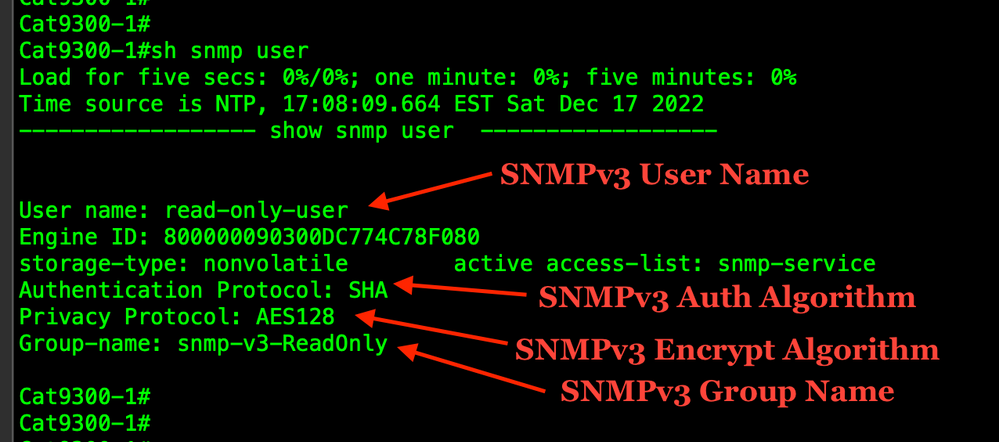
SNMPv3 users are not displayed in the running config but we can see them with this show command.
show snmp user
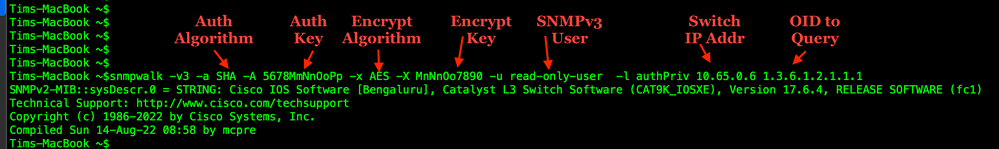
We can use the popular tools snmpget & snmpwalk to query the IOS XE device.
Let's query the sysDescr OID. The command is below. We can see the switch returns it's IOS XE version and some other information.
snmpwalk -v3 -a SHA -A 5678MmNnOoPp -x AES -X MnNnOo7890 -u read-only-user -l authPriv 10.65.0.6 1.3.6.1.2.1.1.1
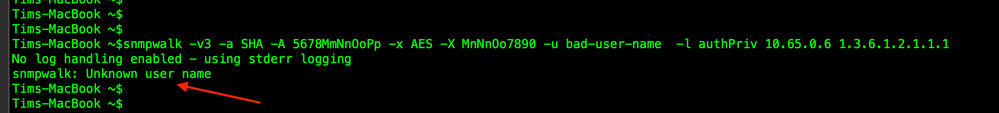
Here is the output when the Username is incorrect.
Here is the output when the Authentication key is incorrect.
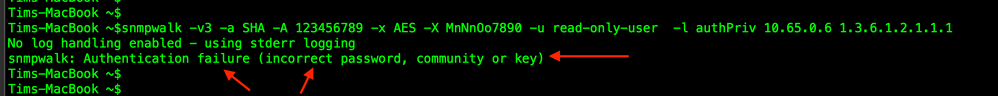
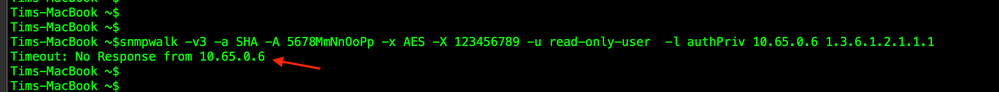
Here is the output when the Privacy key is incorrect.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great post, thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Amazing post! Strugeling with this for a day....
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: