- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Configuring SYSLOG TLS on Catalyst 9000
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-05-2022 01:43 PM - edited 08-08-2022 11:47 AM
Table of Contents
- Table of Contents
- Summary
- Support
- Configuration Steps
- Install a Certificate on the Catalyst Switch
- Install a Certificate on the SYSLOG server
- Configure the Cat 9K for SYSLOG TLS
- Optional Configure Specific Cipher Suites
- Verification
- Cat 9000 Certificate
- Windows Server Certificate
- Show Logging
- Single Connection
Summary
SYSLOG UDP is and has been a tried and true method for collecting messages from IOS XE and other devices for decades. SYSLOG UDP uses udp/512 for transport. The sender transmits messages in the clear to the server. As the industry embraces "encrypt everywhere" we should follow suit. SYSLOG TLS is a more modern method of moving these messages from the sender to the server. SYSLOG TLS uses Transport Layer Security to facilitate a TCP-based secure transport for SYSLOG messages. TLS provides confidentiality for the messages, integrity for the message, and mutual authentication for the sender and receiver.
In our examples, the Catalyst 9000 switch will always be a 'transport sender' or a 'TLS Client'. The SYSLOG server will be the 'transport receiver' or 'TLS Server'.
Support
SYSLOG TLS is defined in RFC 5425
I believe SYSLOG TLS support was introduced in Catalyst 9000 in 17.2.
Most modern SYSLOG servers will support SYSLOG TLS.
SYSLOG TLS default port is tcp/6415
Certificates from an Enterprise CA as well as Self Signed Certificates are supported for authentication. This document explains how to use certificates from an Enterprise CA.
Configuration Steps
Install a Certificate on the Catalyst Switch
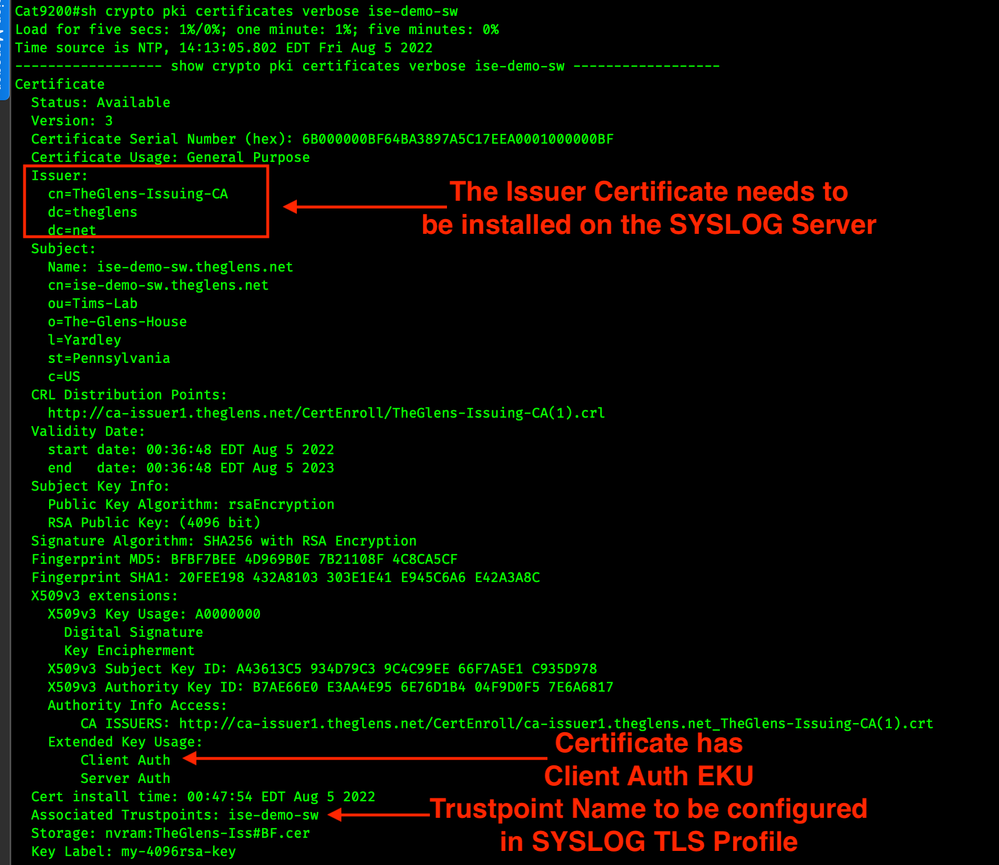
SYSLOG TLS requires certificates on both the sender (Cat9k) and the receiver (SYSLOG server). You can follow this guide for manual Certificate Enrollment. The certificate on the Cat 9000 should have the Client Auth EKU. See below in the Verification section for details.
Install a Certificate on the SYSLOG server
The certificate on the Cat 9000 should have the Server Auth EKU. The method of performing this will depend on your SYSLOG server.
Configure the Cat 9K for SYSLOG TLS
Create the logging profile
Be sure to point the trustpoint to the certificate that was created in Step 1. I'm forcing TLS1.2 primarily because TLSv1.1 should never be used if possible.
!
configure terminal
logging tls-profile SYSLOG-TLS
tls-version TLSv1.2
client-id-trustpoint TRUSTPOINT
!
end
!
Optional Configure Specific Cipher Suites
Please review your SYSLOG TLS server for it's supported cipher suites before enabling this feature in the TLS-PROFILE. CipherSuites are listed in order KeyExchange, Authentication, Bulk Encryption, Message Authentication
CipherSuites are listed here with the strongest toward the top, IMO.
TLSv1.2
ecdhe-ecdsa-aes-gcm-sha2
ecdhe-rsa-aes-gcm-sha2
ecdhe-rsa-aes-cbc-sha2
rsa-aes-gcm-sha2
dhe-aes-gcm-sha2
rsa-aes-cbc-sha2
dhe-aes-cbc-sha2
!
configure terminal
logging tls-profile
ciphersuite ecdhe-ecdsa-aes-gcm-sha2 ecdhe-rsa-aes-cbc-sha2 <OTHER CIPHERS>
!
end
!
Configure Logging to the SYSLOG TLS Server
!
configure terminal
logging host SYSLOG-TLS-IP-ADDR transport tls profile SYSLOG-TLS
!
end
!
Done! This should provide you with a Cat 9K that securely sends SYSLOG messages to a SYSLOG TLS-enabled server!
Keep on reading for some verification steps.
Verification
Cat 9000 Certificate
Use the command show crypto pki certificates verbose TRUSTPOINT to validate the certificate
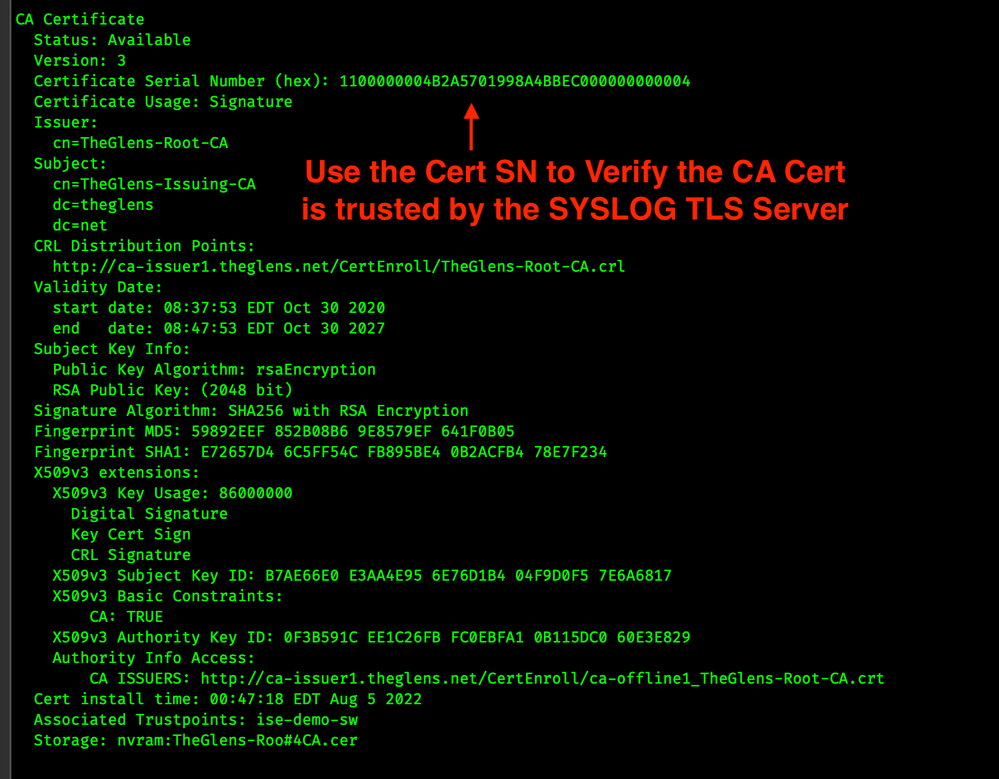
CA Certificate in Trustpoint, Take note of the Serial Number! that's what we will look for on the SYSLOG Server
Windows Server Certificate
Let's examine the Identity Certificate on the SYSLOG Server.
We see the following in the Certificate above.
TheGlens-Root-CA issued a certificate to TheGlens-Issuing-CA.
TheGlens-Issuing-CA issued a certificate to files.thetheglens.net
But remember, Cat9K doesn't trust files.theglens.net, the Cat9K trusts TheGlens-Issuing-CA, the Intermediate.
Let's keep looking, double click on the Intermediate CA.
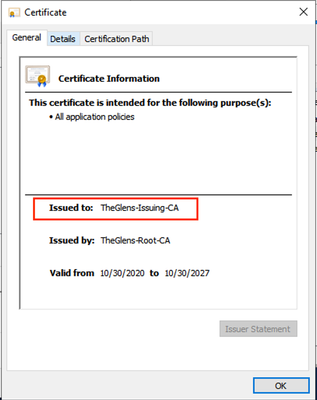
This is the Certificate for the Intermediate. We can see that in 'Issued To' field.
Now click on Details, then the Serial Number.
We can now see that the Serial Number of the CA that issued the Certificate to the SYSLOG server is the same as the CA that issued the Certificate to the Cat9k. We have established Trust.
Show Logging
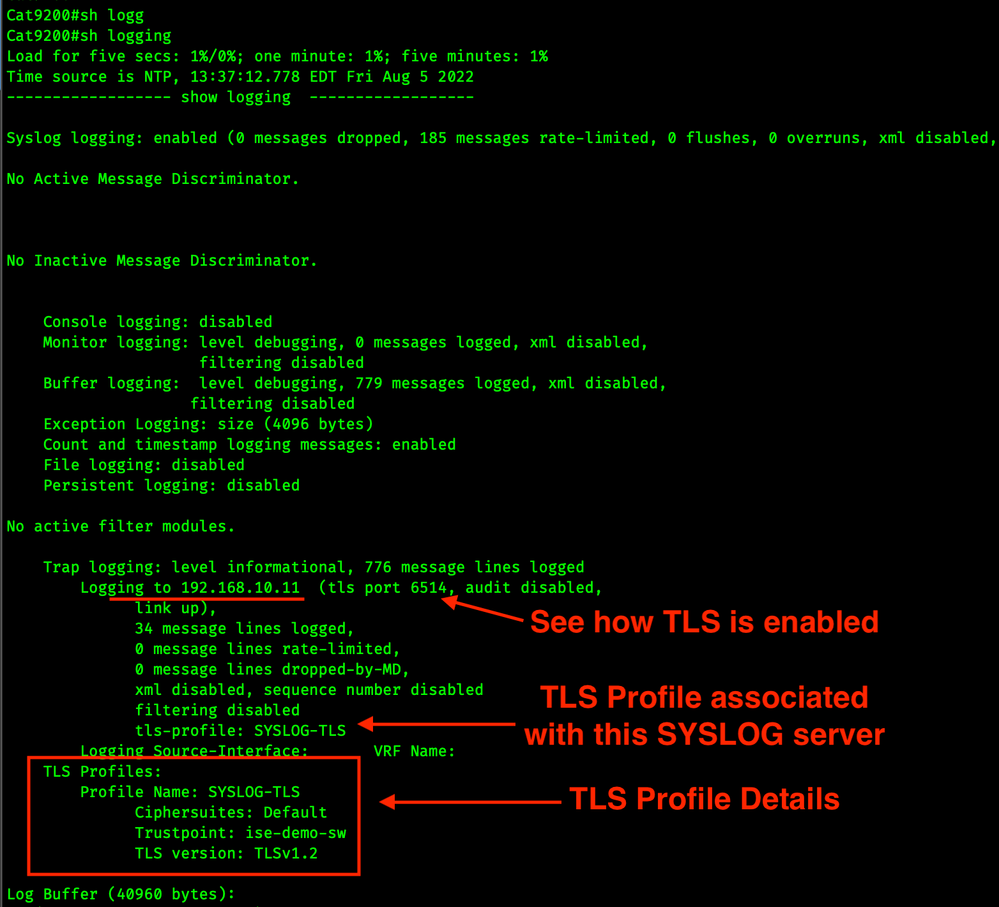
show logging on the switch shows us the relevant configuration for SYSLOG TLS.
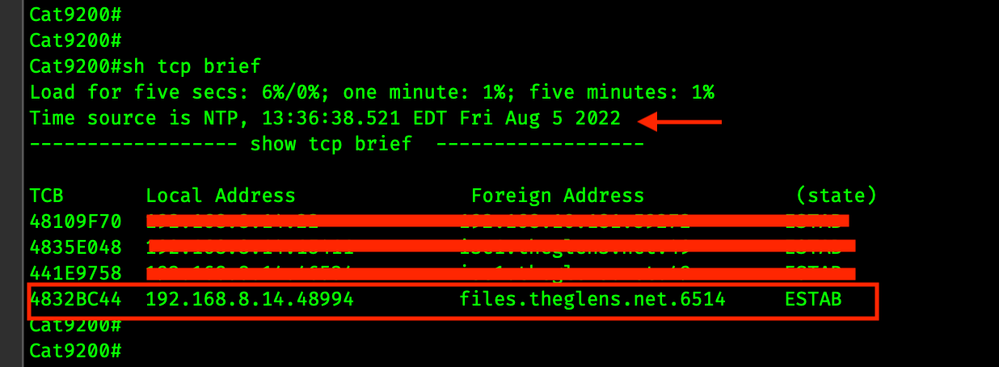
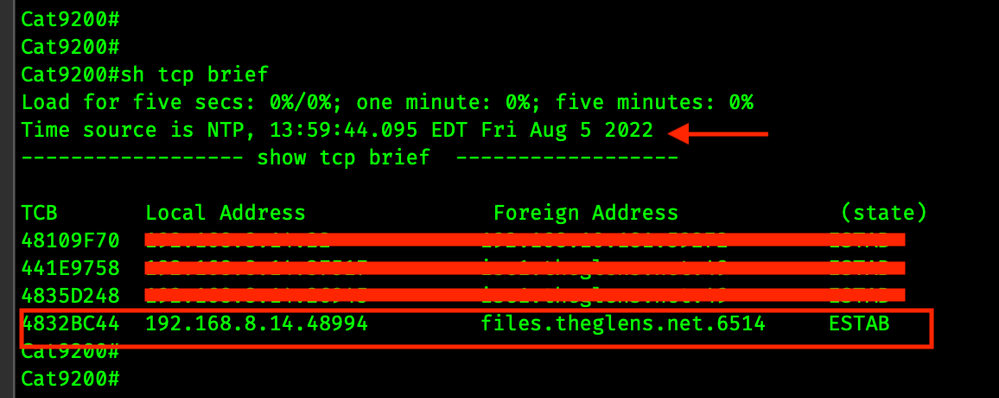
Single Connection
SYSLOG TLS opens a TCP connection and keeps it open. All SYSLOG messages traverse this TCP session.
Below is the output from show tcp brief, this shows open TCP connections from the switch.
Notice how on the first screen shot the time is 13:36. TCP Source Port is 48994
Notice how on the second screen shot the time is 13:59. TCP Source Port is 48994. This is the same TCP connection.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Which Version would this work ?
I've tried 17.9.5 and 17.12.3. Both Versions build TLS session to syslog server but do no logging, no lines are logged.
Reverting back to transport TCP does also not work.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: