Introduction
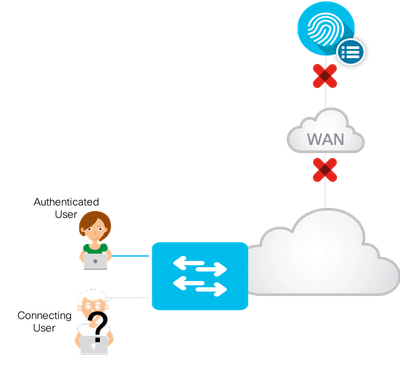
Critical VLAN was introduced to address the situation when the fabric edges are unable to reach the configured RADIUS servers due to some outage such as a WAN outage. During this outage, authentications are not possible for newly connecting endpoints. This feature creates a “fall back” VLAN so that endpoints can successfully onboard and receive some level of access, that’s restricted by policies that you define, during this temporary outage
Functional Overview
- New user connects
- Switch sends RADIUS traffic which are unanswered
- Switch determines RADIUS server is offline and moves the authenticating ports to critical mode. Voice VLAN=2046, Data VLAN=2047. (VLAN based SGT assignment is possible)
- User gets connected and gains network access based upon locally configured ACLs and/or Group-Based Policies
- When RADIUS server comes back online, users in critical vlan are re-authenticated.
Note: Users that are connected prior to RADIUS going offline will remain connected and un-impacted because re-authentication is paused when AAA is detected as offline. Once AAA comes back online, the user is re-authenticated.
Configuration
Enable Critical VLAN feature
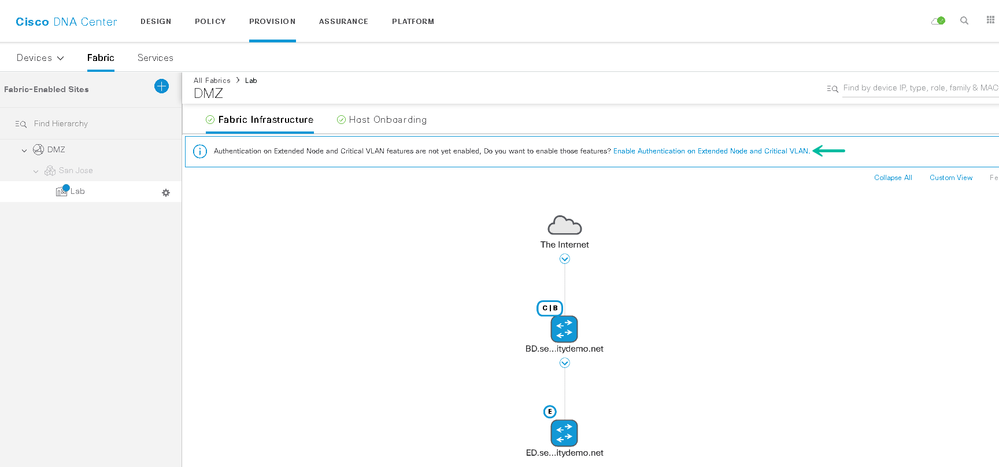
Cisco DNA Center 1.3.3.1 adds the option to enable critical VLAN functionality. This functionality is enabled per site. To enable critical VLAN, navigate to Provision-->Fabric--><Site>-->Fabric Infrastructure and click the link to "Enable Authentication on Extended Node and Critical VLAN"
Critical IP Pool Assignment
Next step is to associate IP pools, or "critical pools", for "critical data" and "critical voice" traffic. The VLAN ids for data and voice are 2047 and 2046 respectively. These ids cannot be modified.
It is important to highlight that there is only 1 critical data vlan and 1 critical voice vlan per fabric. With SD-Access, a VLAN and its associated IP pool are mapped to a single virtual network. In the example below, the IP address pool, 172.16.102.0/24, is mapped as a critical pool for data traffic.

With the above configuration, when the AAA server is down, users in the User_VN will get an IP from 172.16.102.0/24. For a demonstration of this, please reference: Critical VLAN
Considerations
- If fallback is desired for multiple VNs within a fabric, the best option is to create a "Critical VN" and assign a "Critical SGT".
- Policies associated with "Critical SGT" should be configured locally since AAA (ISE) will not be available for policy download during the outage.