Purpose: This document shows you how to create a group-based security policy in Cisco DNA Center.
Security policies determine the types of network traffic permitted or denied between scalable groups. Scalable groups are a critical component of the Cisco Software-Defined Access or SD-Access architecture, providing secure micro-segmentation for SD-Access infrastructure.
Group-based security policies identify a specific source and destination group pair and associate an access contract. The access contract specifies what types of traffic are permitted or denied between a source group and a destination group. These policies are unidirectional. They allow intent-based networking and enable you to configure segmentation for the users, devices, and resources in your network.
Cisco DNA Center helps you create and manage security policies for your entire network. In addition, with Cisco DNA Center, you can easily propagate security policies to your users and devices through Cisco Identity Services Engine or ISE.
To create a security policy, following the steps below:
On Cisco DNA Center, navigate to POLICY from the Cisco DNA Center home page
Click Create Policies and choose Source to Destination(s) tocreate a single source for multiple destination groups.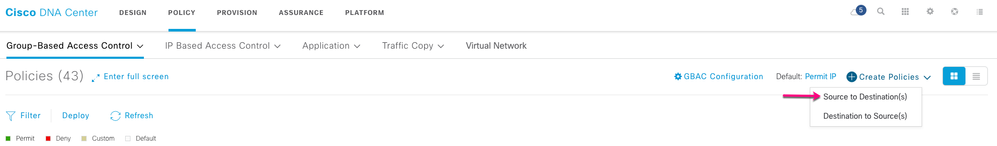
In the Create Policies window that is displayed when you choose Source to Destination(s), select the scalable group that you want to use as the source, and click Next.
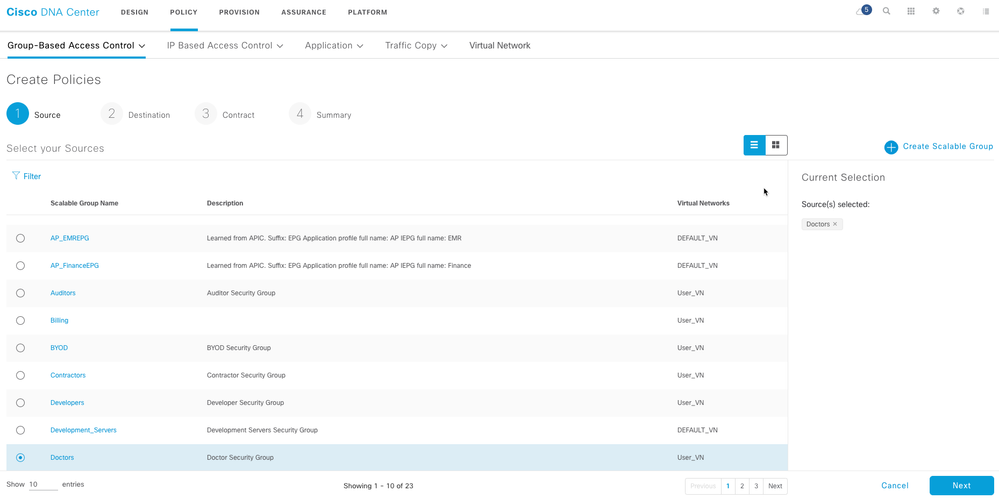
Choose the scalable groups that you want to use as destination groups. An orange triangle icon next to a scalable group indicates that it cannot be a security policy already exists for this group and the source scalable group.
Click Next.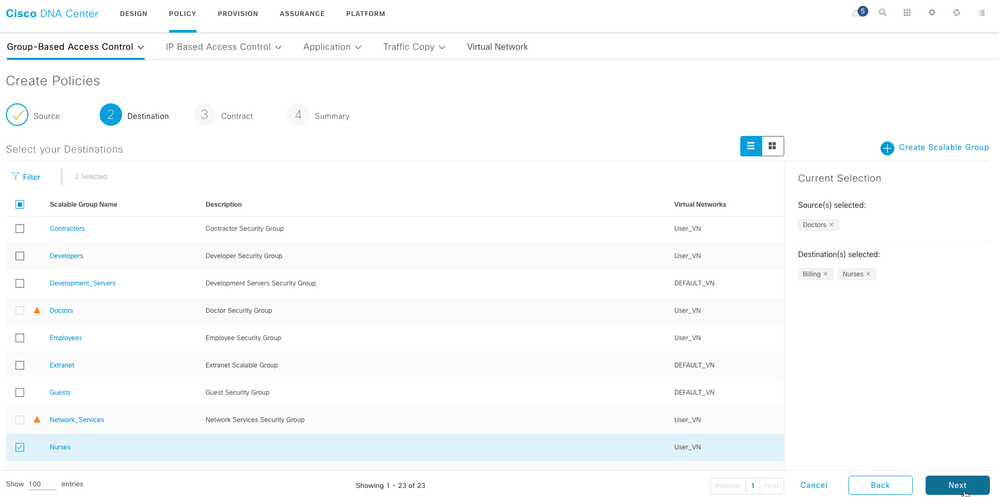
Now, select access contract to determine the traffic flow type that is allowed or denied between the source scalable group and the destination scalable groups.
Click Next. This completes the configuration of the security policy.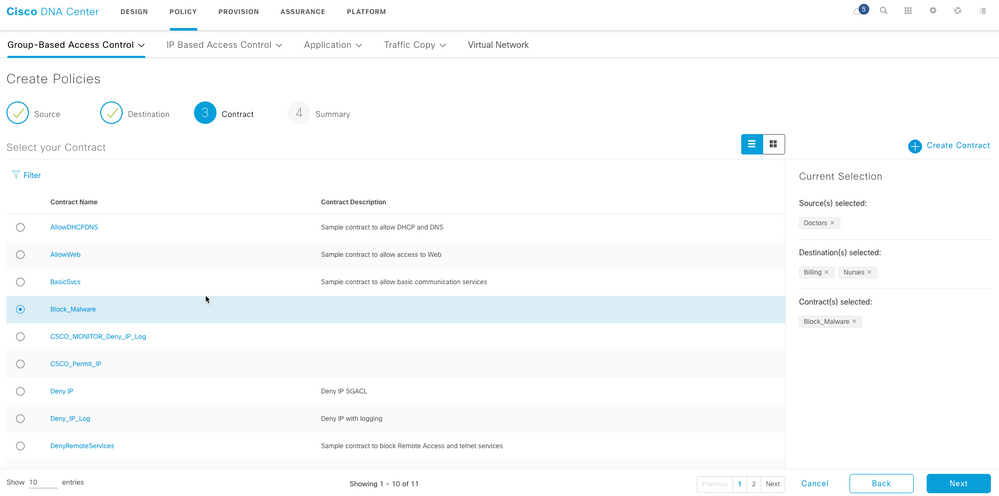
A Review the details and click Save.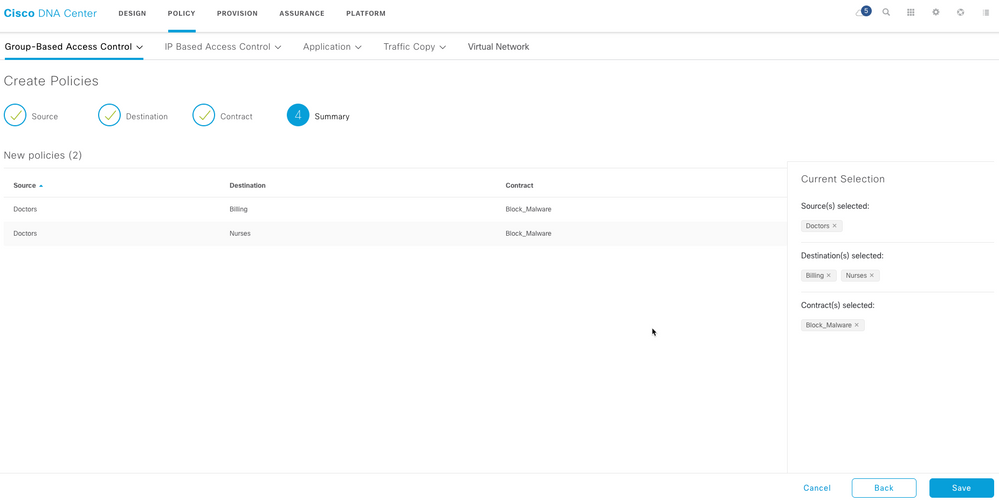
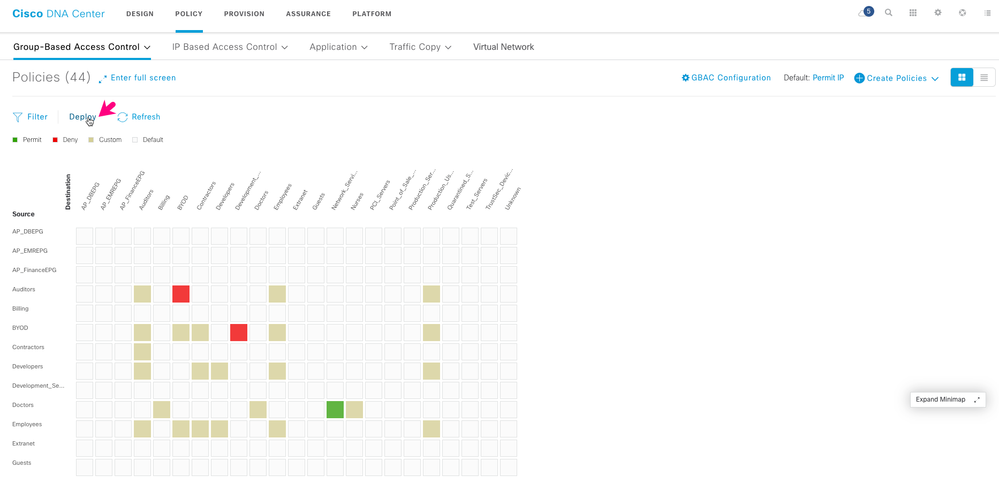
A confirmation message is displayed, and the security policy appears in the matrix view as a beige square at the intersection of Source and Destination.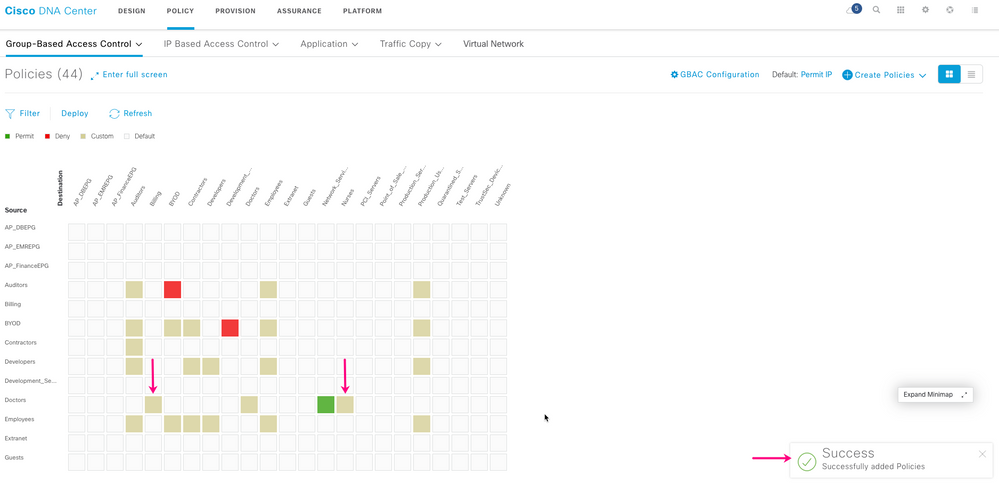
Note that after you create a security policy, it is not automatically deployed to your network. Click Deploy to apply the security policy to the users and devices in your network.