- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Interconnection of Cisco SD-WAN and AWS Transit Gateway
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 07-10-2023 09:11 AM
The world is going digital, but data is often left in the dark. That's a problem for organizations that need to respond quickly to changing situations and customers, Dark data means that valuable data or information is not adequately utilized or leveraged to its full potential. It implies that data is not being effectively analyzed, understood, or utilized to make informed decisions or drive meaningful insights and there’s multiple reason for this refer to (Lack of resources awareness, data silos with limited or difficult access to it with limit visibility, Limited analytical which’s the most important part as of today change’s, the organizations should be shining a light on the data and applying effective data management and analysis techniques and make data Quality driven decisions. Cisco offers a solution to this challenge with its SD-WAN technology , which ‘s enables organizations to better utilize their data and improve overall performance by providing application visibility and control with quality of experience , centralized management , intelligent routing and most important thing (Cloud Integration) I will explain how CSD-WAN and AWS are interrelated and how an organization can leverage them for its cloud hosting needs , How this interrelate will effect on the users and applications and data movements.
In today's interconnected world, businesses rely heavily on cloud computing and networking solutions to achieve seamless communication between their on-premises networks and cloud-based resources. As we know that internet connectivity is the key to future internet business, but with increasing demand for both speed and security comes a need to better manage and secure our existing IT investments. To improve the performance of today's networks and support the needs of tomorrow, organizations are looking at deployment strategies that include Cloud services. These cloud deployments will provide improvements in efficiency, scalability, cost reduction (read about OPEX) and improved user experience while also providing security and regulatory compliance. SD-WAN is powerful technologies that enable organizations to efficiently connect their networks and access resources in the cloud. In this blog, we will explore the interconnection capabilities of Cisco SD-WAN and AWS Transit Gateway and discuss the benefits they provide to businesses. SD-WAN enables customers to utilize new application architectures that have proven more effective than traditional.
In the could world we can’t ignore the automation and how it’s become the key player of the game, and how it’s help us for managing infrastructure resources efficiently is crucial for businesses. Traditionally, infrastructure provisioning and management have been manual processes J, but Infrastructure as Code (IaC) tools like Terraform have changed the game. Terraform allows you to automate the provisioning and configuration of AWS resources, providing numerous benefits for operations and data analysis. In this blog, we will explore how Terraform can help you automate AWS resources and its impact on operational efficiency and data analysis capabilities.
Let’s start :wink: ……
* Why we are using the cloud
* Understanding AWS Global Infrastructure
* AWS Global infrastructure .
* AWS Region.
* AWS Availability Zone.
* AWS Virtual private cloud.
* VPC Addressing CIDR.
* Public and Private Subnets .
* VPC subnets.
* VPC Route Table.
* Elastic Network Interfaces.
* Security Groups.
* Network Access List (ACLs).
* AWS Elastic Compute Cloud (EC2).
* AWS internet Gateway (IGW).
* AWS Virtual private network (VPN).
* AWS virtual private gateway (VGW).
* AWS Site-to-site VPN Connection.
* AWS client VPN Endpoint.
* AWS transit gateway (TGW).
* AWS transit gateway attachments (Attach).
* AWS transit gateway Policy table.
* AWS transit gateway Route table.
* Aws Reachability Analyzer.
* AWS transit gateway peering.
* Exploring Cisco SD-WAN Technology
* What is SD-WAN?
* Cisco SD-WAN as a Solution
* The Components of Cisco SD-WAN
* SD-WAN Policies and Application-Aware Routing
* Security Features and Unified Communication Voice Services
* Cloud OnRamp for SaaS and IaaS
* Interconnecting Cisco SD-WAN and AWS Transit Gateway
* Understanding AWS Transit Gateway
* Transit Gateway Attachments and Route Tables
* Leveraging SD-WAN and AWS for Cloud Hosting Needs
* Impact on Users, Applications, and Data Movements
* Best Practices and Considerations
* Optimizing Performance with SD-WAN and AWS
* Monitoring and Management with Cloud Watch
* Cost and Operational Considerations
* Cloud Computing Models: IaaS, PaaS, SaaS, and More
* Terraform: A Brief Overview
* Introduction to Terraform and its Features
* Declarative Configuration Files and Infrastructure Management
* Multi-Cloud Support and Versatility
* Automating AWS Resources with Terraform
* Benefits of Infrastructure as Code (IaC)
* Reproducible Infrastructure and Configuration Consistency
* Efficient Provisioning of AWS Resources
* Dependency Management and Resource Ordering
* Impact on Operational Efficiency and Data Analysis
* Faster Provisioning and Deployment
* Consistent and Repeatable Environments for Data Analysis
* Scalability and Elasticity for Handling Data Intensity
* Cost Optimization through Efficient Resource Management
* Terraform Tasks :
* Create VPC-A-us-east-1
* Create route table main-RTP-VPC-A-Us-East-1
* Associate route table with subnet Subnet-VPC-A-Us-East-1
* Create subnet Subnet-VPC-A-Us-East-1
* Create VPC-B-us-east-1
* Create route table main-RTP-VPC-B-Us-East-1
* Associate route table with subnet Subnet-VPC-B-Us-East-1
* Create subnet Subnet-VPC-B-Us-East-1
* Create VPC-C-us-east-1
* Create route table main-RTP-VPC-C-Us-East-1
* Associate route table with subnet Subnet-VPC-C-Us-East-1
* Create subnet Subnet-VPC-C-Us-East-1
* Create VPC-D-us-east-1
* Create internet gateway IGW-VPC-D-Us-East-1
* Create route table main-RTP-VPC-D-Us-East-1
* Associate route table with subnet Subnet-VPC-D-Us-East-1
* Create subnet Subnet-VPC-D-Us-East-1
* Create VPC-A-us-east-2
* Create route table RTP-VPC-A-Us-East-2
* Associate route table with subnet Subnet-VPC-A-Us-East-2
* Create subnet Subnet-VPC-A-Us-East-2
* Create VPC-B-us-east-2
* Create route table main-RTP-VPC-B-Us-East-2
* Associate route table with subnet Subnet-VPC-B-Us-East-2
* Create subnet Subnet-VPC-B-Us-East-2
* Create VPC-C-us-east-2
* Create route table main-RTP-VPC-C-Us-East-2
* Associate route table with subnet Subnet-VPC-C-Us-East-2
* Create subnet Subnet-VPC-C-Us-East-2
* Create VPC-D-us-east-2
* Create internet gateway IGW-VPC-D-Us-East-2
* Create route table main-RTP-VPC-D-Us-East-2
* Associate route table with subnet Subnet-VPC-D-Us-East-2
* Create subnet Subnet-VPC-D-Us-East-2
* Create Transit Gateway TGW-us-east-1
* Create Transit Gateway TGW-us-east-2
* Create Transit Gateway Attachments for VPCs in us-east-1
* Create Transit Gateway Attachments for VPCs in us-east-2
* Create Transit Gateway Peering between TGW-us-east-1 and TGW-us-east-2
* Accept the Peering request from TGW
* Create Security Group for VPC-D in us-east-1
* Create EC2 instance for VPC-D in us-east-1
* Create Security Group for VPC-D in us-east-2
* Create EC2 instance for VPC-D in us-east-2
* Create SD-WAN Controllers (vSmart, vManage, vBond) for VPC-D
**why we are using the cloud ?**
As we know currently all the data centers based on the **CAPEX** **(Capital Expenditure )** model which's install all the hardware and software on-premises with a fully operation including resources and experts engineers . ETC... which's effect to the cost and operation headache + some of vendors their devices support for 3 or 5 years only then organization have to change them to get the fully support and meet the security compliance or standardization of the operation , in the another side of the cloud the model is **OPEX ( Operating Expense )** which is pay as you use which is very attractive for any organization plus fully hosting for all the computes and storage and security services , ETC.... which's will reduce the cost of the operation and reduce the operation headache also will guaranty to deliver availability & resilience services .
Good Example : OPEX looks like the electric and water services at your home
## Aws Global Infrastructure :-
AS we know Amazon web services is leaders of the cloud provider around the world and server more than 1 million clients around the world , Based on this Aws deliver their services with Low latency and highly throughput to help their clients to achieve their goals without any issue , as this demand Aws providing and extending their infrastructure to meets their global requirements , AWS global infrastructure placed in multiple region and each region has their Availability Zones .
· To learn more about the global region up to date, please check out this link :
[ **https://aws.amazon.com/about-aws/global-infrastructure/** ](https://aws.amazon.com/about-aws/global-infrastructure/)
## AWS Region:-
A region is a geographic location where does the cloud resources are located and run, AWS has 31 Regions around the world and Each Amazon Region is designed to be completely isolated from the other Amazon Regions. And this isolation achieves the greatest possible fault tolerance and stability, each Region has there availability zone each Az is isolated but they have inter connect through low latency link and highest Bandwidth.
· To learn more about the global region up to date, please check out this link:
[ **https://aws.amazon.com/about-aws/global-infrastructure/** ](https://aws.amazon.com/about-aws/global-infrastructure/)
## AWS Availability zone:-
Availability Zones consist of one or more discrete data centers, each availability zone has redundant power, networking, and connectivity. These Availability Zones offer you to run your applications and your services with more highly available and resiliency , scalability Etc...
· To learn more about the global region up to date, please check out this link :
· [ **https://aws.amazon.com/about-aws/global-infrastructure/** ](https://aws.amazon.com/about-aws/global-infrastructure/)
## Virtual private cloud :-
Amazon VPC is Networking services that helping you to create a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you created .this services include BYOIP, Subnets, Route table , internet Gateway , DHCP options , Elastic IP for Public purpose , Nat gateway , Endpoints services , Etc..... , You have to customize your vpc based on your solution and case .
For Example :
Deploy application with modernization architecture and migrate from monolithic (old fashion) Create VPC for WEB , VPC for APP , VPC for Database and create subnet for each VPC include private and subnet and create IGW for the public subnet to provide the internet access to the VPC , we will discuss more about this in future with hands-on.
## VPC Addressing CIDR :-
CIDR is Classless Inter-Domain Routing and is a methodology of assigning IP-Address network uses , The subnet masks basically allow part of the underlying IP to get additional from the base IP .
• /0 allows for all IPs = 2^32
• /24 allows for 256 IP = 2^8
• /16 allows for 65,536 IP = 2^16
For Example, VPC-A has CIDR 10.10.0.0/16 and inside the VPC-A there is multiple subnets include private and subnet , Private subnet-1 ( 10.10.1.0/24) , Private subnet-2 ( 10.10.2.0/24) , Private subnet-3 (10.10.3.0/24) , Public Subnet ( 10.10.100.0/24) and this public subnet will route their traffic to the AWS IGW to reach to the internet .
**VPC Subnets :-**
A subnets a range of IP addresses in your VPC. It is logically isolated from other virtual networks in the AWS Cloud
## What are Public and Private subnets :-
(IANA) established certain blocks of IPV4 addresses for the use of private and public . We are using private subnet for internal connection in the vpc, and public subnets are using to reach to internet by route all the traffic of the public subnet to IGW 0.0.0.0/0 -à IGW .
## VPC Route Table :-
The route table contains Routes , Subnet association even public or private , Edge association , route propagation , you can create multiple route table for each VPC
Example : VPC A – has 2 subnets ( private and subnet ) , so we can create 2x route table one RTB for private subnet and other for Public subnet with default route to IGW to reach to the internet.
## Elastic Network Interface :-
ENI ( Elastic network interface ) is a logical components in the vpc which’s represent the virtual network card , you can create the ENI and attach it to the EC2 instance , ENI can support for primary and secondary private IP , one public Ip address , ENI support more Security group is not limited to one , We are using the ENI for the EC2 need dual home or High availability solution .
## AWS Security Group :-
AWS security Groups act as virtual firewalls for the Elastic compute cloud ( EC2) to controlling the traffic for it , Security Group is specifying the inbound & Outbound of the EC2 instance with restriction include Port number , authorized Ip address to access , Protocol , Source and destination , security group can attach to multiple instances , security group working closely for the region , All inbound traffic is blocked by default .
## AWS Network Access List :-
AWS Network Access list (NACL) is working on the subnet level to control the traffic and allow or deny the specific traffic for whole subnet , Each vpc has default NACL and you can used it , you can create your own NACL and assign to the Specific subnet in the VPC , Each subnet can only associate with one NACL , The Default NACL allow all the inbound and outbound traffic , NACL specific the traffic based on Protocol , Traffic type , Port number , Source & Destination , NACL has two actions ( Allow , Deny ) .
## AWS Elastic Compute Cloud :-
Amazon EC2 is a web service that provides compute capacity in the cloud. It is designed to make computing easier for developers.
The simple web interface of Amazon EC2 allows you to have the operating system up and running with few minutes which ‘s reflet to the dev team and reduce the headache , It provides you with complete control of your computing resources, allowing you to quickly scale capacity, both up and down , AWS Ec2 has multiple types such as Spot instances , Reserved instances , On-Demand instances , Dedicated Host .
## AWS internet Gateway (IGW) :-
IT’s AWS services enable the VPC to communicate to the internet with redundance and highly available , the internet gateway is support for IPv4 & ipv6 , IGW it’s help the Ec2 instance run in the Public subnet to reach to the internet , IGW should be attached in the route table of the public subnet and route all the unknown traffic (Public internet) to the IGW .
## AWS virtual private gateway (VGW) :-
AWS virtual private gateway (VGW) It’s VPN connector on AWS when running site to site VPN , VGW is high availability VPN solution because It’s created 2x tunnels endpoints in different availability zone , VGW can be attached for one VPC only , VGW support for the Dynamic routing and here I mean BGP only , VGW also support Static route , VGW is supporting encryption and data integrity.
## AWS Site-to-site VPN Connection :-
It’s secure connection between the on-premises and AWS resources using IPsec tunnels , SITE to SITE VPN can connect to both VPC & Transit Gateway and as we mentioned before It’s created through tunnels for redundancy and availability purpose .
## AWS client VPN Endpoint :-
AWS Client VPN Endpoint is services helping the clients to securely the connection between remote and AWS resources , with the client VPN you can connect to AWS services from any where , AWS client VPN is managed services by AWS , It’s recommend to deploy in high availability mode , With AWS client VPN you have to 2x option to connect to internet even locally or through IGW so If you are looking to use IGW internet you have to disable the Split tunneling as default behavior and If you are looking to segregate the connection for known (AWS Resources) & unknown(Internet) so you have to enable split tunneling at the client VPN.
## AWS transit gateway (TGW) :-
Transit Gateway is AWS services that helping to connect multiple VPC together without any complexity like vpc peering for large connection , TGW allow the customer to inter-Connect the VPC’s and on-Premises network , TGW supporting for attaching multiple vpc , Direct connect connection , SD-wan connection , Each VPC or VPN attachment is associated with a single route table. That route table decides the next hop for the traffic coming from that resource attachment, When you attach a VPC or create a VPN connection on a transit gateway, the attachment is associated with the default route table of the transit gateway, You can create additional route tables inside the transit gateway and change the VPC or VPN association to these route tables, this helping the customer to segment the network .
## AWS transit gateway attachments (Attach) :-
It enables you to attach the VPC or VPN, Each attachment is associated with a single route table. A route table inside the transit gateway allows for both IPv4 or IPv6 CIDRs and targets. The targets are VPCs and VPN connections. When you attach a VPC or create a VPN connection on a transit gateway, the attachment is associated with the default route table of the transit gateway, but you can customize the individual route table as per the solution and you can segregate the whole network based on this route tables attach .
## Aws Reachability Analyzer :-
Reachability Analyzer is an analysis tool that enables you to perform the test between source and destination , to use the Reachability analyzer you have to specify the SRC & DST , source or destination can be EC2 , IGW, ENI, TGW, VPC endpoint , Etc... , AWS Reachability Analyzer support only Ipv4 address , AWS Reachability Analyzer doesn’t support network firewall rules , Reachability analyzer can specify the packet header details of your traffic to evaluate its network reachability based on sources & destination ip and sources & Destination port number and appropriate protocol even TCP or UDP .
## AWS Cloud Watch :-
AWS Cloud Watch provides monitoring and visibility into the performance of AWS resources and applications. Organizations can leverage CloudWatch to collect and analyze performance metrics, such as CPU utilization, network traffic, and application response times.
**What is SD-WAN?**
SD-WAN is Software define wide area network and SD-WAN is key part of the technology of software-defined networking. SDN is a centralized approach to network management which abstracts the underlying network infrastructure away from its applications ,SD-WAN has more advantage such as automation, simplification of operations, provisioning, monitoring, Application Aware and smart troubleshooting.
**Why SD-WAN solution?**
SD-WAN solution has major advantages but the most important of them is Cost &user experience let's imagine the connection with traditional wide area network (WAN) when users at the branch want to connect to applications hosted on servers in the data center through MPLS , look to cost & t-shoot , SD-WAN will reduce cost here because the solution Support for all typed of connections (4G, 5G, Broadband , MPLS that means you can select cheaper connection options for low-priority traffic and high cost for high-priority traffic.can help a branch router avoid loss, latency and jitter within the network, SD-WAN give you ease of management via your single pane of glass interface, Increasing bandwidth through the activate & backup links and dynamic load-balancing, Delivering faster cloud access by enabling direct internet access at the branch .As we are seeing today all business go with Software as a Service (SaaS) and Infrastructure as a Service (IaaS) across multiple clouds, IT departments are struggling with providing a satisfactory experience for business-critical applications, SD-WAN Delivering faster cloud access by enabling direct internet access
**How many planes in the Cisco SD-WAN solution?**
Cisco SD-WAN provides a clear separation between management plane, control plane, and data plane, Cisco SD-WAN solution contains four planes < Management plane , Control Plane , orchestration plane , Data plane > An important consequence of the software-defined networking principles is the separation of control plan and data plan
between the definition of network policies and the forwarding of traffic.This separation is key to the desired flexibility, breaking the network control problem into pieces, and making it easier to create and introduce new abstractions in networking, simplifying network management and facilitating network evolution and innovation.
**What is the components of cisco SD-WAN solution ?**
The Cisco SD-WAN solution contains four key components responsible for each plane :
1-Cisco vManage :- Cisco V-manage is used to handle the management plane and represents the user interface of the solution.
2-Cisco vSmart :- v-Smart is the brain of the solution and exists within the control plane, v-Smart is the component responsible for enforcing these policies centrally and exchange the routing information.
3-Cisco vBond :- v-Bond is the orchestration plane responsible for on boarding the device into the SD-WAN fabric and Zero-Touch Provisioning process as well as first-line to authentication, v-Bond is responsible Network Address Translation (NAT) traversal.
NOTE: Cisco SD-WAN is based on the zero-trust model. All of the components mutually authenticate each other, and all of the edge devices are authorized before they are allowed onto the network.
4- Edge routers :- Edge router is data plane and Edge routers are responsible for establishing the network fabric and forwarding traffic.
**- SD-Wan Policy :-**
Viptela SD-WAN classified two types ( centralized policies or localized policies ) .
- The difference between ( centralized policies or localized policies )
Centralized policies : Those policies that are applied on the vSmart on the overlay network.
Localized policies : Those policies that are applied locally on the vEdge routers on the overlay network .
Centralized policies has two polices ( Control Policy and data Policy )
Localized Policy : Pushed from vManage directly to Edge devices via a NETCONF transaction – affects will happened for specific devices requiring policies.
Centralized Control policies :- Used to manipulate the propagation of routing information in the control plane including OMP, TLOC, VPN Services .
Centralized Data policies : Commonly used to accomplish (DIA) for specific applications, network service insertion, Also data plane manipulations such as packet Forwarding Error Correction (FEC) .
**NOTE :** In traditional wan , configurations are typically applied on a device thorough CLI but cisco SD-WAN is came with a new era of the network which's SDN and it has been designed to overcome this by implementing a centralized management plane that implement on all devices without any human error.
**NOTE :** Before Appalling any policy please be consider this all vEdges routers will sent the local site network to vSmart controller via OMP protocols , All vEdges will send all TLOC routes to vSmart controller via OMP , All vEdge Router will send all service Routes to all vSmart via OMP.
**- Application Aware Routing**
AAR is identify business critical traffic and specify the required SLA for that traffic classified . Viptela SD-WAN provides the ability to use multiple transports such as MPLS , BIZ-Internet, broadband , Etc... more than one method with high availability which 's will effect to the cost and operation . It provides the ability to use intelligent method through SLA detection for the application to used different transports based on the status .
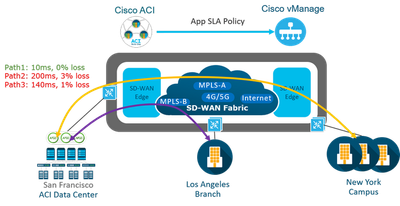
Application-aware routing directs traffic based upon an application SLA LIST parameters and this defined application policies done though the vmanage and push to vSmart then to all SD-wan fabric Traffic is automatically sent to WAN links that have the important network characteristics and meet the SLA conditions to support these applications in production .
**- SD-wan Security Features include IPS/IDS services**
As we know the security is a critical part of today's networking infrastructure, Cisco Viptela SD-WAN align itself with this and from version 18.0 to latest version 20.9 the intrusion prevention/intrusion detection systems and URL filtering is available , and can apply this services for all the SD-WAN fabric .
**- Unified communication Voice**
Cisco Unified Communications requires that Cisco vManage be running Cisco SD-WAN Release 20.1. You can configure feature templates and voice policies to enable Cisco Unified Communications voice services for supported routers. These templates and policies configure parameters for FXO, FXS . When Cisco voice services are enabled, routers can process calls for various endpoints, including voice ports, POTS dial peers, SIP dial peers, and phone profiles in Cisco Unified Survivable Remote Site Telephony mode. Also voice policy defines how the system define and manipulates calls for various endpoint types. Endpoints include voice ports, POTS dial peers, SIP dial peers, and Survivable Remote Site Telephony .
Cisco Viptela with Cisco umbrella (Golden hours of the cloud security services)
**Cloud onRamp for Saas & laas :-**
Cloud OnRamp for SaaS optimizes the performance of Software as a Service (SaaS) cloud applications based on network loss and latency SLA . Cloud OnRamp for SaaS provides clear visibility of the performance of individual applications and automatically chooses the best path for each one even MPLS , BIZ-Internet , 4 G Etc...
Although Cloud onRamp addresses both IaaS and SaaS providers, it's operate for the two types of cloud. With IaaS providers, such as AWS and Azure , Cloud OnRamp for SaaS calculates a value called the Viptela Quality of Experience , you also enable Cloud OnRamp for SaaS on the gateway site , viptela support some of the application now such as Microsoft Office 365 , oracle , sales forces , Zoho , Etc...
Cloud OnRamp for IaaS you can read more helpful details here :
The Cloud onRamp for IaaS works in conjunction with AWS virtual private clouds (VPCs) and Azure virtual networks (VNets). The following image provides a high level overview of multi-cloud onRamp for IaaS.
**what is the models of cloud computing ?**
Cloud modules ( IAAS , PAAS , SAAS , STAAS , DBAAS , DRAAS , CAAS , XAAS , ETC.....
* **IAAS :** Infrastructure as a services which is provide network , storage space , HV of the computer , It's provide the customer high flexibility of the management of these resources .
* **PAAS :** Platform as a services : It's provide fully platform including Network , Storage , , Hardware , HV, Operating system and the customer only manage own database of his application which's help to focus more in the deployment and app programing and was will manage all other .
* **SAAS :** Software as a services It's provide fully & Completed solution including Network , Storage , , Hardware , HV, Operating system, Database , Application Example ( office 356 , ZOHO , Whatsup , ETc....
* **STAAS :** Storage as a services Which is provide the customer Storage services .
* **DBAAS :** Database as a services Which is provide the customer database with magical migration tools .
* **DRAAS :** Disaster recovery as a services Which is provide the customer Disaster Recovery solution with
* **DAAS :** Desktop as a services which is allow the organization to access computing capacity from third party server.
* **CAAS :** Communication as a services it's allow the organization to access variety of communication tools and applications like cisco webex , Zoom, Etc...
* **XAAS :** Anything as a services which's general describe for any services related to the cloud and remote access which is will keep the businesses to stay abreast and align with the latest tech.
How Leveraging SD-WAN and AWS for Cloud Hosting Needs ?
SD-WAN technology provides intelligent routing and traffic optimization, allowing organizations to prioritize critical application traffic and dynamically choose the most efficient network path. By integrating SD-WAN with AWS, organizations can improve network performance, reduce latency, and enhance application response times, AWS offers a highly scalable infrastructure, enabling organizations to easily scale their cloud hosting resources up or down based on demand. SD-WAN complements this scalability by providing seamless connectivity to multiple cloud regions and data centers, allowing organizations to expand their cloud footprint and adapt to changing business requirements, SD-WAN provides advanced security features such as encryption, firewalling, and secure segmentation. When combined with AWS, organizations can benefit from the robust security measures and compliance frameworks provided by AWS, ensuring the secure hosting of applications and protecting sensitive data,Many organizations adopt a hybrid cloud approach, combining on-premises infrastructure with cloud services. SD-WAN can seamlessly integrate on-premises networks with AWS, enabling secure and optimized connectivity between different environments, and allowing organizations to leverage the benefits of both on-premises and cloud resources.
how it will Impact on Users, Applications, and Data Movements?
By leveraging SD-WAN and AWS, organizations can optimize network performance, reduce latency, and improve application response times. This translates to an enhanced user experience, as users can access applications and services faster and with greater reliability, regardless of their location,SD-WAN technology enables organizations to establish highly available network connections and dynamically route traffic to the most optimal path , SD-WAN technology optimizes data traffic flows by intelligently routing data packets over the most efficient network paths. This leads to improved network performance, reduced latency, and optimized data movements between users and cloud applications. Users can access and transfer data more efficiently, enhancing productivity and collaboration.
Optimizing Performance with SD-WAN and AWS
SD-WAN enables application-aware routing, which allows organizations to define policies based on application performance requirements. By integrating SD-WAN with AWS, organizations can route application traffic to the most suitable AWS regions or availability zones, ensuring optimal performance and minimizing latency.
Monitoring and Management with Cloud Watch
As we mentioned overview about the cloud watch above by monitoring these metrics, organizations can identify performance bottlenecks, optimize resource allocation, and troubleshoot issues proactively, also Cloud Watch enables organizations to set up alarms and notifications based on predefined thresholds or custom metrics
Cost and Operational Considerations
organizations can optimize resource allocation and minimize costs. SD-WAN allows for intelligent traffic routing and load balancing, ensuring efficient use of network resources. Additionally, AWS offers cost optimization features such as auto-scaling and resource rightsizing, enabling organizations to align their resource usage with actual demand and avoid unnecessary costs
Let’s move to the terraform :wink: ……
Terraform overview
Terraform is an open-source tool developed by HashiCorp that allows you to define and manage infrastructure resources using declarative configuration files. With Terraform, you can create, modify, and destroy cloud infrastructure resources in a controlled and reproducible way. It supports various cloud providers, including AWS, Azure, and Google Cloud Platform.
Automating AWS Resources with Terraform
Terraform provides several key advantages for automating AWS resource provisioning and management:
Infrastructure as Code (IAC) With Terraform, you define your desired infrastructure configuration in code using a declarative language( NOT Imperative like other which's a strong point for terraform ) . This allows for version control, code review, and collaboration, ensuring that infrastructure changes are treated as code and follow standard development practices, Terraform ensures that your infrastructure is reproducible across different environments, such as development, staging, and production. The same Terraform code can be used to provision identical infrastructure configurations, reducing the risk of configuration drift and improving consistency.
Terraform enables you to provision AWS resources in an automated and scalable manner. By defining your infrastructure needs in code, you can easily create multiple instances of resources, such as EC2 instances, TGW , IGE, Etc... as we will do in our script later
Terraform automatically resolves and applies resource dependencies based on the defined configuration. This ensures that resources are provisioned in the correct order and that dependencies between resources are correctly managed.
Impact on Operational Efficiency and Data Analysis
Terraform's automation capabilities enable faster provisioning and deployment of AWS resources. This reduces manual effort and helps to streamline operations, allowing infrastructure changes to be implemented quickly and consistently.
Consistent and Repeatable Environments
With Terraform, you can ensure that your infrastructure environments are consistent and repeatable. This is essential for data analysis, as it ensures that analysis can be performed on the same infrastructure setup across different datasets and scenarios.
Cost Optimization
Terraform helps optimize costs by allowing you to define and manage AWS resources efficiently. With its infrastructure as code approach, you can accurately estimate and control resource usage, enabling you to make informed decisions and avoid unnecessary expenses.
Terraform Code to build the solution :slight_smile:
Creating VPCs and associated resources in us-east-1 and us-east-2 regions, The code creates four VPCs (VPC-A, VPC-B, VPC-C, VPC-D) in each region. It also creates subnets, route tables, and route table associations for each VPC.
Creating transit gateways in us-east-1 and us-east-2 regions, The code creates transit gateways to enable communication between VPCs in different regions.
Creating transit gateway attachments, The code creates transit gateway attachments to connect VPCs to the transit gateways. Each VPC is associated with a transit gateway attachment.
Creating transit gateway peeringm, The code establishes peering between the transit gateways in us-east-1 and us-east-2 regions to enable communication between VPCs in different regions.
Creating security groups and EC2 instances, The code creates security groups for EC2 instances in both us-east-1 and us-east-2 regions. It also provisions EC2 instances in each VPC with the specified security groups.
Creating SD-WAN controllers, The code creates security groups and EC2 instances for vManage, vSmart, and vBond controllers in us-east-1 region.
Here there is some notes and consideration
You can deploy the following Cisco SD-WAN controllers in an Amazon Web Services (AWS) environment using Amazon Machine Images (AMI): Cisco vManage, Cisco vSmart controller, and Cisco vBond orchestrator.
The AMI images that Cisco provides to you are for your use only. Do not share them with others. You can do the following:
* You can deploy the number of controllers as per your order quantity. For example, if you have ordered 50 Cisco vManage controller PIDs, then you can deploy only 50 Cisco vManage controllers within your AWS account.
* You can copy the AMI between regions and your own separate AWS accounts, if you do not exceed the quantity of PIDs ordered.
* After the initial deployment of the controllers, you are responsible for any upgrades or downgrades.
### Considerations Before Installing Cisco SD-WAN Controllers in AWS
* Cisco SD-WAN controller AMIs are not available on the Cisco software download site or AWS marketplace. They are provided only when you request them with a valid business case to set up Cisco SD-WAN controllers in your AWS cloud account.
* For information about ordering Cisco SD-WAN controllers to use with AWS, contact your Cisco account team or Cisco partner.
* Cisco does not provide support for any issues that arise with the cloud infrastructure during the provisioning or installation of the controllers.
* Troubleshooting:
* Functionality issues: Please open a Cisco TAC case for functionality issues.
* Infrastructure issues: You are responsible for infrastructure management, monitoring, and troubleshooting. After the controllers are provisioned and running in your cloud account, Cisco does not provide support for cloud infrastructure-related issues.
### Benefits of Deploying Cisco SD-WAN Controllers in AWS
* Set-up cost: Low initial set-up cost, as compared with on-premises hosting, as there is no requirement to purchase additional data center infrastructure.
* Deployment: Ease of cloud-based deployment.
* Management: Ability to manage devices worldwide.
* Stability: Because of its reliability, AWS hosting provides a stable environment for Cisco SD-WAN controllers.
* Security: AWS provides a secure hosting environment.
* Scaling: AWS provides an easy path to increase the scale of your Cisco SD-WAN network.
for more information refer to : Deploy Cisco SD-WAN Controllers in the AWS Cloud.
# ############################### Create the VPC's for us-East-1 ###########################
# Create the VPC-A-us-east-1 #
resource "aws_vpc" "VPC-A-Us-East-1" {
cidr_block = "192.168.10.0/24"
tags = {
Name = "VPC-A-Us-East-1"
}
}
# ****************************************** Create a route table ******************************************
resource "aws_route_table" "main-RTP-VPC-A-Us-East-1" {
vpc_id = aws_vpc.VPC-A-Us-East-1.id
tags = {
Name = "my-route-table-main-RTP-VPC-A-Us-East-1"
}
}
# ****************************************** Associate the route table with the subnet******************************************
resource "aws_route_table_association" "Subnet-VPC-A-Us-East-1" {
subnet_id = aws_subnet.Subnet-VPC-A-Us-East-1.id
route_table_id = aws_route_table.main-RTP-VPC-A-Us-East-1.id
}
# ****************************************** Create a subnet ******************************************
resource "aws_subnet" "Subnet-VPC-A-Us-East-1" {
vpc_id = aws_vpc.VPC-A-Us-East-1.id
cidr_block = "192.168.10.0/24"
availability_zone = "us-east-1a"
tags = {
Name = "Subnet-VPC-A-Us-East-1"
}
}
###################/////////////////////////////////############################
# Create the VPC-B-us-east-1 #
resource "aws_vpc" "VPC-B-Us-East-1" {
cidr_block = "192.168.20.0/24"
tags = {
Name = "VPC-B-Us-East-1"
}
}
# ****************************************** Create a route table ******************************************
resource "aws_route_table" "main-RTP-VPC-B-Us-East-1" {
vpc_id = aws_vpc.VPC-B-Us-East-1.id
tags = {
Name = "my-route-table-main-RTP-VPC-B-Us-East-1"
}
}
# ****************************************** Associate the route table with the subnet******************************************
resource "aws_route_table_association" "Subnet-VPC-B-Us-East-1" {
subnet_id = aws_subnet.Subnet-VPC-B-Us-East-1.id
route_table_id = aws_route_table.main-RTP-VPC-B-Us-East-1.id
}
# ****************************************** Create a subnet ******************************************
resource "aws_subnet" "Subnet-VPC-B-Us-East-1" {
vpc_id = aws_vpc.VPC-B-Us-East-1.id
cidr_block = "192.168.20.0/24"
availability_zone = "us-east-1a"
tags = {
Name = "Subnet-VPC-B-Us-East-1"
}
}
###################/////////////////////////////////############################
# Create the VPC-C-us-east-1 #
resource "aws_vpc" "VPC-C-Us-East-1" {
cidr_block = "10.30.102.0/28"
tags = {
Name = "VPC-C-Us-East-1"
}
}
# ****************************************** Create a route table ******************************************
resource "aws_route_table" "main-RTP-VPC-C-Us-East-1" {
vpc_id = aws_vpc.VPC-C-Us-East-1.id
tags = {
Name = "my-route-table-main-RTP-VPC-C-Us-East-1"
}
}
# ****************************************** Associate the route table with the subnet******************************************
resource "aws_route_table_association" "Subnet-VPC-C-Us-East-1" {
subnet_id = aws_subnet.Subnet-VPC-C-Us-East-1.id
route_table_id = aws_route_table.main-RTP-VPC-C-Us-East-1.id
}
# ****************************************** Create a subnet ******************************************
resource "aws_subnet" "Subnet-VPC-C-Us-East-1" {
vpc_id = aws_vpc.VPC-C-Us-East-1.id
cidr_block = "10.30.102.0/28"
availability_zone = "us-east-1a"
tags = {
Name = "Subnet-VPC-C-Us-East-1"
}
}
###################/////////////////////////////////############################
# Create the VPC-D-us-east-1 #
resource "aws_vpc" "VPC-D-Us-East-1" {
cidr_block = "192.168.30.0/24"
enable_dns_hostnames = true
tags = {
Name = "VPC-D-Us-East-1"
}
}
# ****************************************** Create internet gateway ******************************************
resource "aws_internet_gateway" "IGW-VPC-D-Us-East-1" {
vpc_id = aws_vpc.VPC-D-Us-East-1.id
tags = {
Name = "IGW-VPC-D-Us-East-1"
}
}
# ****************************************** Create a route table ******************************************
resource "aws_route_table" "main-RTP-VPC-D-Us-East-1" {
vpc_id = aws_vpc.VPC-D-Us-East-1.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.IGW-VPC-D-Us-East-1.id
}
tags = {
Name = "my-route-table-main-RTP-VPC-D-Us-East-1"
}
}
# ****************************************** Associate the route table with the subnet******************************************
resource "aws_route_table_association" "Subnet-VPC-D-Us-East-1" {
subnet_id = aws_subnet.Subnet-VPC-D-Us-East-1.id
route_table_id = aws_route_table.main-RTP-VPC-D-Us-East-1.id
}
# ****************************************** Create a subnet ******************************************
resource "aws_subnet" "Subnet-VPC-D-Us-East-1" {
vpc_id = aws_vpc.VPC-D-Us-East-1.id
cidr_block = "192.168.30.0/24"
availability_zone = "us-east-1a"
tags = {
Name = "Subnet-VPC-D-Us-East-1"
}
}
######## _______________________________________________________________________________#########
############################### Create the VPC's for us-East-2 ###########################
# Create the VPC-A-us-east-2 #
resource "aws_vpc" "VPC-A-Us-East-2" {
cidr_block = "192.168.0.0/24"
provider = aws.east-2
tags = {
Name = "VPC-A-Us-East-2"
}
}
# ****************************************** Create a route table ******************************************
resource "aws_route_table" "RTP-VPC-A-Us-East-2" {
vpc_id = aws_vpc.VPC-A-Us-East-2.id
provider = aws.east-2
tags = {
Name = "my-route-table-RTP-VPC-A-Us-East-2"
}
}
# ****************************************** Associate the route table with the subnet******************************************
resource "aws_route_table_association" "Subnet-VPC-A-Us-East-2" {
provider = aws.east-2
subnet_id = aws_subnet.Subnet-VPC-A-Us-East-2.id
route_table_id = aws_route_table.RTP-VPC-A-Us-East-2.id
}
# ****************************************** Create a subnet ******************************************
resource "aws_subnet" "Subnet-VPC-A-Us-East-2" {
vpc_id = aws_vpc.VPC-A-Us-East-2.id
provider = aws.east-2
cidr_block = "192.168.0.0/24"
availability_zone = "us-east-2b"
tags = {
Name = "Subnet-VPC-A-Us-East-2"
}
}
###################/////////////////////////////////############################
# Create the VPC-B-us-east-2 #
resource "aws_vpc" "VPC-B-Us-East-2" {
cidr_block = "192.168.1.0/24"
provider = aws.east-2
tags = {
Name = "VPC-B-Us-East-2"
}
}
# ****************************************** Create a route table ******************************************
resource "aws_route_table" "main-RTP-VPC-B-Us-East-2" {
vpc_id = aws_vpc.VPC-B-Us-East-2.id
provider = aws.east-2
tags = {
Name = "my-route-table-main-RTP-VPC-B-Us-East-2"
}
}
# ****************************************** Associate the route table with the subnet******************************************
resource "aws_route_table_association" "Subnet-VPC-B-Us-East-2" {
provider = aws.east-2
subnet_id = aws_subnet.Subnet-VPC-B-Us-East-2.id
route_table_id = aws_route_table.main-RTP-VPC-B-Us-East-2.id
}
# ****************************************** Create a subnet ******************************************
resource "aws_subnet" "Subnet-VPC-B-Us-East-2" {
vpc_id = aws_vpc.VPC-B-Us-East-2.id
provider = aws.east-2
cidr_block = "192.168.1.0/24"
availability_zone = "us-east-2a"
tags = {
Name = "Subnet-VPC-B-Us-East-2"
}
}
###################/////////////////////////////////############################
# Create the VPC-C-us-east-2 #
resource "aws_vpc" "VPC-C-Us-East-2" {
cidr_block = "10.20.101.0/28"
provider = aws.east-2
tags = {
Name = "VPC-C-Us-East-2"
}
}
# ****************************************** Create a route table ******************************************
resource "aws_route_table" "main-RTP-VPC-C-Us-East-2" {
vpc_id = aws_vpc.VPC-C-Us-East-2.id
provider = aws.east-2
tags = {
Name = "my-route-table-main-RTP-VPC-C-Us-East-2"
}
}
# ****************************************** Associate the route table with the subnet******************************************
resource "aws_route_table_association" "Subnet-VPC-C-Us-East-2" {
provider = aws.east-2
subnet_id = aws_subnet.Subnet-VPC-C-Us-East-2.id
route_table_id = aws_route_table.main-RTP-VPC-C-Us-East-2.id
}
# ****************************************** Create a subnet ******************************************
resource "aws_subnet" "Subnet-VPC-C-Us-East-2" {
vpc_id = aws_vpc.VPC-C-Us-East-2.id
provider = aws.east-2
cidr_block = "10.20.101.0/28"
availability_zone = "us-east-2a"
tags = {
Name = "Subnet-VPC-C-Us-East-2"
}
}
###################/////////////////////////////////############################
# Create the VPC-D-us-east-2 #
resource "aws_vpc" "VPC-D-Us-East-2" {
cidr_block = "192.168.3.0/24"
provider = aws.east-2
tags = {
Name = "VPC-D-Us-East-2"
}
}
# ****************************************** Create an internet gateway ******************************************
resource "aws_internet_gateway" "IGW-VPC-D-Us-East-2" {
vpc_id = aws_vpc.VPC-D-Us-East-2.id
provider = aws.east-2
tags = {
Name = "IGW-VPC-D-Us-East-2"
}
}
# ****************************************** Create a route table ******************************************
resource "aws_route_table" "main-RTP-VPC-D-Us-East-2" {
vpc_id = aws_vpc.VPC-D-Us-East-2.id
provider = aws.east-2
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.IGW-VPC-D-Us-East-2.id
}
tags = {
Name = "my-route-table-main-RTP-VPC-D-Us-East-2"
}
}
# ****************************************** Associate the route table with the subnet******************************************
resource "aws_route_table_association" "Subnet-VPC-D-Us-East-2" {
provider = aws.east-2
subnet_id = aws_subnet.Subnet-VPC-D-Us-East-2.id
route_table_id = aws_route_table.main-RTP-VPC-D-Us-East-2.id
}
# ****************************************** Create a subnet ******************************************
resource "aws_subnet" "Subnet-VPC-D-Us-East-2" {
vpc_id = aws_vpc.VPC-D-Us-East-2.id
provider = aws.east-2
cidr_block = "192.168.3.0/24"
availability_zone = "us-east-2a"
tags = {
Name = "Subnet-VPC-D-Us-East-2"
}
}
####################################### Create Transit Gateway for US-east-1 ################################
resource "aws_ec2_transit_gateway" "TGW-us-east-1" {
description = "TGW-us-east-1"
tags = {
Name = "TGW-us-east-1"
}
}
####################################### Create Transit Gateway for US-east-2 ################################
resource "aws_ec2_transit_gateway" "TGW-us-east-2" {
description = "TGW-us-east-2"
provider = aws.east-2
tags = {
Name = "TGW-us-east-2"
}
}
####################################### Create Transit Gateway Attachments for US-east-1 ################################
# Define the Transit Gateway Attachment resources
resource "aws_ec2_transit_gateway_vpc_attachment" "attachment_VPC-A-Us-East-1" {
transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-1.id
vpc_id = aws_vpc.VPC-A-Us-East-1.id
subnet_ids = aws_subnet.Subnet-VPC-A-Us-East-1.*.id
tags = {
Name = "attachment_VPC-A-Us-East-1"
}
}
resource "aws_ec2_transit_gateway_vpc_attachment" "attachment_VPC-B-Us-East-1" {
transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-1.id
vpc_id = aws_vpc.VPC-B-Us-East-1.id
subnet_ids = aws_subnet.Subnet-VPC-B-Us-East-1.*.id
tags = {
Name = "attachment_VPC-B-Us-East-1"
}
}
resource "aws_ec2_transit_gateway_vpc_attachment" "VPC-C-Us-East-1" {
transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-1.id
vpc_id = aws_vpc.VPC-C-Us-East-1.id
subnet_ids = aws_subnet.Subnet-VPC-C-Us-East-1.*.id
tags = {
Name = "attachment_VPC-C-Us-East-1"
}
}
resource "aws_ec2_transit_gateway_vpc_attachment" "VPC-D-Us-East-1" {
transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-1.id
vpc_id = aws_vpc.VPC-D-Us-East-1.id
subnet_ids = aws_subnet.Subnet-VPC-D-Us-East-1.*.id
tags = {
Name = "attachment_VPC-D-Us-East-1"
}
}
####################################### Create Transit Gateway Attachments for US-east-2 ################################
# Define the Transit Gateway Attachment resources
resource "aws_ec2_transit_gateway_vpc_attachment" "attachment_VPC-A-Us-East-2" {
transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-2.id
provider = aws.east-2
vpc_id = aws_vpc.VPC-A-Us-East-2.id
subnet_ids = aws_subnet.Subnet-VPC-A-Us-East-2.*.id
tags = {
Name = "attachment_VPC-A-Us-East-2"
}
}
resource "aws_ec2_transit_gateway_vpc_attachment" "attachment_VPC-B-Us-East-2" {
transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-2.id
provider = aws.east-2
vpc_id = aws_vpc.VPC-B-Us-East-2.id
subnet_ids = aws_subnet.Subnet-VPC-B-Us-East-2.*.id
tags = {
Name = "attachment_VPC-B-Us-East-2"
}
}
resource "aws_ec2_transit_gateway_vpc_attachment" "VPC-C-Us-East-2" {
transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-2.id
provider = aws.east-2
vpc_id = aws_vpc.VPC-C-Us-East-2.id
subnet_ids = aws_subnet.Subnet-VPC-C-Us-East-2.*.id
tags = {
Name = "attachment_VPC-C-Us-East-2"
}
}
resource "aws_ec2_transit_gateway_vpc_attachment" "VPC-D-Us-East-2" {
transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-2.id
provider = aws.east-2
vpc_id = aws_vpc.VPC-D-Us-East-2.id
subnet_ids = aws_subnet.Subnet-VPC-D-Us-East-2.*.id
tags = {
Name = "attachment_VPC-D-Us-East-2"
}
}
###################################### Create Transit Gateway peering from Us-east-1 ################################
resource "aws_ec2_transit_gateway_peering_attachment" "my_peering_attachment" {
transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-1.id
peer_transit_gateway_id = aws_ec2_transit_gateway.TGW-us-east-2.id
peer_region = "us-east-2"
tags = {
Name = "my_peering_attachment"
}
####################################### Accept the Peering request from TGW ################################
resource "aws_ec2_transit_gateway_peering_attachment_accepter" "accepter" {
transit_gateway_attachment_id = "tgw-attach-004825704042e05eb" # replace with the attachment ID
provider = aws.east-2
tags = {
Name = "my_peering_attachment_accepter"
}
}
####################################### Create Security Group for us-east-1 ################################
resource "aws_security_group" "launch-wizard-1" {
name_prefix = "launch-wizard-1"
vpc_id = aws_vpc.VPC-D-Us-East-1.id
ingress {
from_port = 0
to_port = 65535
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
####################################### Create Ec-2 instance for us-east-1-VPC-D ################################
resource "aws_instance" "my_instance-VPC-D-Us-East-1" {
ami = "ami-022e1a32d3f742bd8" # replace with the desired AMI ID
instance_type = "t2.micro"
subnet_id = aws_subnet.Subnet-VPC-D-Us-East-1.id
associate_public_ip_address = "true"
vpc_security_group_ids = [
aws_security_group.launch-wizard-1.id,
]
tags = {
Name = "EC-2-Instance-VPC-D"
}
}
################################## Create Security Group for us-east-2 ################################
resource "aws_security_group" "launch-wizard-2" {
provider = aws.east-2
name_prefix = "launch-wizard-1"
vpc_id = aws_vpc.VPC-D-Us-East-2.id
ingress {
from_port = 0
to_port = 65535
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
####################################### Create Ec-2 instance for us-east-2-VPC-D ################################
resource "aws_instance" "my_instance-VPC-D-Us-East-2" {
ami = "ami-0e820afa569e84cc1" # replace with the desired AMI ID
instance_type = "t2.micro"
provider = aws.east-2
subnet_id = aws_subnet.Subnet-VPC-D-Us-East-2.id
associate_public_ip_address = "true"
vpc_security_group_ids = [
aws_security_group.launch-wizard-2.id,
]
tags = {
Name = "EC-2-Instance-VPC-D-us-east-2"
}
}
############## Create Sd-wan Controllers (vSmart,vManage,vBond) us-east-1-VPC-D #############
resource "aws_security_group_rule" "vmanage_sg_ingress" {
security_group_id = aws_security_group.vmanage_sg.id
type = "ingress"
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
resource "aws_instance" "vmanage" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
subnet_id = aws_subnet.my_subnet.id
vpc_security_group_ids = [aws_security_group.vmanage_sg.id]
user_data = <<-EOF
#!/bin/bash
echo "Starting vManage installation"
# Add vManage installation commands here
echo "vManage installation complete"
EOF
tags = {
Name = "vmanage"
}
}
resource "aws_security_group" "vsmart_sg" {
name_prefix = "vsmart_sg"
vpc_id = aws_vpc.my_vpc.id
}
resource "aws_security_group_rule" "vsmart_sg_ingress" {
security_group_id = aws_security_group.vsmart_sg.id
type = "ingress"
from_port = 12346
to_port = 12346
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
resource "aws_instance" "vsmart" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
subnet_id = aws_subnet.my_subnet.id
vpc_security_group_ids = [aws_security_group.vsmart_sg.id]
user_data = <<-EOF
#!/bin/bash
echo "Starting vSmart installation"
# Add vSmart installation commands here
echo "vSmart installation complete"
EOF
tags = {
Name = "vsmart"
}
}
resource "aws_security_group" "vbond_sg" {
name_prefix = "vbond_sg"
vpc_id = aws_vpc.my_vpc.id
}
resource "aws_security_group_rule" "vbond_sg_ingress" {
security_group_id = aws_security_group.vbond_sg.id
type = "ingress"
from_port = 12346
to_port = 12346
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
resource "aws_instance" "vbond" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
subnet_id = aws_subnet.my_subnet.id
vpc_security_group_ids = [aws_security_group.vbond_sg.id]
user_data = <<-EOF
#!/bin/bash
echo "Starting vBond installation"
# Add vBond installation commands here
echo "vBond installation complete"
EOF
tags = {
Name = "vbond"
}
}
It brings me great joy to share knowledge and insights with all of you.I invite you to stay tuned for the upcoming Part 2, where we will delve deeper into the subject matter and explore new dimensions of learning Make sure to keep an eye out for the next update. I'm committed to providing you with quality content that educates, inspires, and sparks curiosity. Let's continue this journey of growth and knowledge together.
Thank you for being a part of this community (cisco community ). Your feedback, comments, and support mean the world to me. Feel free to reach out with any questions or suggestions. Together, we can create a vibrant space for learning and exploration.
Stay tuned
Mohamed Alhenawy
CCIE #60453 #networking
-
Announcements
-
AppDynamics
-
Assurance and Policy
-
Automation
-
Buying Recommendation
-
Catalyst 4000
-
Catalyst 8000
-
Catalyst 9000 Switches
-
Cisco ENCS
-
Cloud Networking
-
Configuration
-
EEM Scripting
-
IPv6
-
LAN
-
LAN Switching
-
Meraki Switch
-
Network Management
-
NFVIS
-
Optical Networking
-
Other Network Architecture
-
Other Networking
-
Other Routers
-
Other Routing
-
Other SD-WAN
-
Routing
-
Routing Protocols
-
SD-WAN
-
Software Upgrades
-
vEdge Routers
-
WAN
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:










