- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Let's talk about Wireshark and Embedded Packet Capture on Cat9K
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-19-2022 05:59 PM - edited 04-19-2022 06:11 PM
- Summary
- Embedded Packet Capture (EPC)
- EPC IOS XE Commands
- Wireshark
- Wireshark IOS XE Commands
- Real-Life Capture Examples
- Capture BGP Traffic
- Capture All Traffic at an Interface
- Capture tcp/22 Traffic using Match
- Export a Capture Buffer
- Troubleshooting
- Licensing
- Frequently Asked Questions
- References
Summary
Wireshark and Embedded Packet Capture (EPC) are methods of capturing and or displaying captured traffic on an IOS XE box. Wireshark is an application that runs natively inside of IOS XE on the Cat 9k. Wireshark can also be an application that runs as a container on C9300 and C9400, this article is NOT about that. SPAN is another way of redirecting traffic to a monitoring destination but has no local display, this article is NOT about SPAN.
Some monitor capture commands in IOS XE use Wireshark others use EPC. Wireshark requires a DNA Advantage term license and EPC requires a Network Essentials perpetual license, this has created confusion. This article is to help network administrators differentiate between Wireshark and EPC and to show examples of both methods.
In summary, Embedded Packet Capture is a method of capturing and displaying traffic in IOS XE. EPC has been in IOS XE for many years. Wireshark on IOS XE is also a method of capturing and displaying traffic in IOS XE, however, Wireshark is much more flexible when it comes to working with the captured traffic and displaying the captured traffic on the CLI.
Finally, both Wireshark and Embedded Packet Capture can be CPU and Memory intensive processes. Please be aware of typical CPU & memory usage before enabling these features. Using filters to capture specific traffic can reduce CPU and memory utilization.
Embedded Packet Capture (EPC)
Embedded Packet Capture is a toolset that actually captures the traffic. EPC allows network administrators to capture data packets flowing through, to, and from a Cisco device and has been in IOS \ IOS XE for many years. Capturing packets that are handled by the CPU (outside the data plane) is performed by attaching the capture to the control plane. Configuration takes place in EXEC mode, not in config mode.
EPC IOS XE Commands
Note: The command references show the Wireshark vs EPC commands.
Note: It's possible not all these commands will be available on your platform.
monitor capture access-list
Use this command to attach an access-list to a capture point.
monitor capture (interface / control plane)
Configures the EPC attachment point.
monitor capture limit
Configures limits like duration (time), packet length (size), or a total number of packets.
monitor capture pktlen-range
Use this command to capture packets that fit into a size range.
monitor capture start
Use this command to start the capture.
monitor capture stop
Use this command to stop the capture.
Wireshark
Wireshark is a packet analyzer program that supports multiple protocols. Wireshark on IOS XE presents information in a text-based user interface, this text interface is also known as tshark. Wireshark on IOS XE exports packets to a well know file format .pcap.
Wireshark IOS XE Commands
monitor capture buffer
Configures a fixed buffer size or circular option.
monitor capture clear
Clears the buffer while the capture is active or stopped. Clearing the buffer is a destructive action, export it first if you need it.
monitor capture export
Exports the captured traffic from the buffer to a .pcap file on local flash, or remote tftp, ftp etc.
monitor capture file
Use this when the destination is a file on local flash. After the file is exported it can be copied to remote TFTP, FTP, etc.
monitor capture match
Configures a core filter based on MAC address, IP version (4or6), host, IP Subnet, ports, protocols etc.
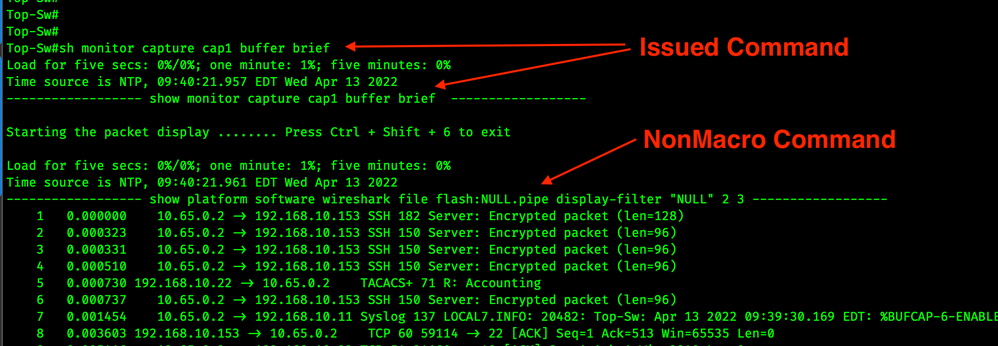
show monitor capture capname buffer brief
Network admins can verify this command is a Wireshark command by adding the following to the config terminal exec prompt expand. After adding the expand command you will see this show monitor command is actually a macro for a show platform command. See the screenshot below.
show monitor capture capname buffer detailed
sh monitor capture capname buffer display-filter "ip.addr==10.20.30.40"
sh monitor capture capname buffer display-filter "ip.addr==10.20.30.40 && !tcp.port==443"
You can use some really complex Wireshark display filters, you just need to know the syntax!
Real-Life Capture Examples
Capture BGP Traffic
This is an EPC capture. Capturing BGP traffic from the control plane is sometimes better than trying to capture it at the interface level.
!
configure terminal
ip access-list extended cap1
permit tcp any eq bgp any
permit tcp any any eq bgp
end
monitor capture cap1 control-plane both
monitor capture cap1 access-list cap1
monitor capture cap1 start
!
!
monitor capture cap1 stop
!
Capture All Traffic at an Interface
This is an EPC capture.
!
configure terminal
ip access-list extended cap1
permit tcp any any
permit tcp any any
end
monitor capture cap1 access-list cap1
monitor capture cap1 interface g1/0/1 both
monitor capture cap1 start
!
!
monitor capture cap1 stop
!
Capture tcp/22 Traffic using Match
This is an EPC capture. Please take note that it works without ever going into configure mode. No ACL required!
!
monitor capture cap1 match ipv4 protocol tcp any any eq 22
monitor capture cap1 inter g1/0/1 both
monitor capture cap1 start
!
!
monitor capture cap1 stop
!
Export a Capture Buffer
This is a Wireshark function.
monitor capture cap1 export flash:/cap1.pcap
or
monitor capture cap1 export location flash:/cap1.pcap
Troubleshooting
There are only two debugs that I am aware of.
debug epc provision
The screenshot above shows the debug output when the EPC is started.
The screenshot above shows the debug output when the EPC is stopped.
debug epc capture-point
This debug produces much more useful information.
The screenshot above occurs when a new capture is created and an access-list is applied to the capture point. Yes, I realize that the below is an EPC command, not Wireshark, and this may be confusing since the debug output clearly says Wireshark, but be assured this is EPC.
monitor capture cap1 access-list cap1
The screenshot above occurred when an interface was attached to the capture point.
monitor capture cap1 interface g1/0/8 both
The screenshot above shows the EPC capture starting.
monitor capture cap1 start
The screenshot above shows when the EPC capture is stopped.
monitor capture cap1 stop
Licensing
Embedded Packet Capture is included in Network Essentials perpetual license.
Wireshark is included in the DNA Advantage term license.

Frequently Asked Questions
Q: Does Wireshark require a DNA Advantage license even though DNA Center is not used or part of the packet capture process?
A: Yes, Wireshark requires a DNA Advantage license. Wireshark is one of a few features that are capable of being used without a DNA Center but require DNA-A. Some of the others are Flexible NetFlow, and EEM.
Q: Will Wireshark work if I don’t renew my DNA Advantage licensing?
A: Wireshark is part of DNA and if Wireshark is used outside of the subscription term this would not be out of compliance.
Q: When should I use control-plane parameter?
A: This should be used when capturing traffic directed at the control plane, examples are routing protocols or any packets that leave the data plane and hit the CPU.
Q: What is a capture point?
A: The capture point describes all the characteristics associated with a capture. These include which packets to capture, where to capture them from, what to do with the captured packets, and when to stop.
Q: What is a core filter?
A: A core filter is any access-list, or monitor capture match that is applied capture point. Core filters occur at the ASIC and they determine what traffic will be sent to the software.
Q: What is a capture filter?
A: A capture filter can be more granular than core filters. They are processed in software.
Q: What is a display filter?
A: Display filters are used on show commands to limit the output to the desired packets.
Q: I can execute Wireshark commands but only have DNA Essentials, what's happening?
A: At this time Cisco is not enforcing and has not blocked usage of these commands from the CLI. Cisco could, at any time, change this by blocking access to the commands via CLI or other methods. TAC will check entitlement when requesting help with Wireshark commands.
Q: How can Wireshark a GUI-based program display captured data in a textual format?
A: It uses tshark, Terminal Based Wireshark.
Q: Why is EPC & Wireshark configured at EXEC prompt and not config prompt?
A: This is to allow network engineers the ability to make troubleshooting changes to the switch without making changes to the running-config which in some organizations could require a lot of approval & red tape.
Q: How can I capture traffic and assure I'm only using the Embedded Packet Capture that's included in Network Essentials?
A: Be sure to use the commands listed above in the EPC section. For reference, this is a script that shows an EPC example.
!
configure terminal
ip access-list extended cap1
permit ip any any
end
monitor capture cap1 access-list cap1
monitor capture cap1 inter g1/0/1 both
monitor capture cap1 start
!
!
monitor capture cap1 stop
!
Note: The Cat9K IOS XE Command Reference clearly calls out commands that are Wireshark commands.
References
Catalyst 9200 IOS XE 17.6 Command Reference
Catalyst 9200 IOS XE 17.6 Configuring Packet Capture
Catalyst 9400 IOS XE 17.6 Command Reference
Catalyst 9400 IOS XE 17.6 Configuring Packet Capture
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: