- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- SD-WAN Overview & Advanced Deployment Lab | Part.1
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-16-2021 12:13 AM - edited 04-19-2021 07:13 PM
Today I'm going to talk about SD-wan including SD-WAN advanced lab ,, first thing let's take a small brief about the SD_WAN.
What is SD-WAN?
SD-WAN is Software define wide area network and SD-WAN is key part of the technology of software-defined
networking . SDN is a centralized approach to network management which abstracts the underlying network infrastructure away from its applications ,SD-WAN has more advantage such as automation, simplification of operations, provisioning, monitoring, and smart troubleshooting.
Why SD-WAN solution ?
SD-WAN solution has major advantages but the most important of them is Cost and user experience let's imagine the connection with traditional wide area network (WAN) when users at the branch want to connect to applications hosted on servers in the data center through MPLS , look to cost & t-shoot , SD-WAN will reduce cost here because the solution Support for all typed of connections (4G, 5G, Broadband , MPLS that means you can select cheaper connection options for low-priority traffic and high cost for high-priority traffic.can help a branch router avoid loss, latency and jitter within the network, SD-WAN give you ease of management via your single pane of glass interface, Increasing bandwidth through the activate & backup links and dynamic load-balancing, Delivering faster cloud access by enabling direct internet access at the branch .As we are seeing today all business go with Software as a Service (SaaS) and Infrastructure as a Service (IaaS) across multiple clouds, IT departments are struggling with providing a satisfactory experience for business-critical applications, SD-WAN Delivering faster cloud access by enabling direct internet access .
How many planes in the Cisco SD-WAN solution ?
Cisco SD-WAN solution contains four planes < Management plane , Control Plane , orchestration plane , Data plane > .
What is the components of cisco SD-WAN solution ?
The Cisco SD-WAN solution contains four key components responsible for each plane :
1-Cisco v-Manage :- Cisco V-manage is used to handle the management plane and represents the user interface of the solution.
2-Cisco v-Smart :- v-Smart is the brain of the solution and exists within the control plane, v-Smart is the component responsible for enforcing these policies centrally and exchange the routing information.
3-Cisco v-Bond :- v-Bond is the orchestration plane responsible for on boarding the device into the SD-WAN fabric and Zero-Touch Provisioning process as well as first-line to authentication, v-Bond is responsible Network Address Translation (NAT) traversal.
4- Edge routers :- Edge router is data plane and Edge routers are responsible for establishing the network fabric and forwarding traffic.
!
!
!
!
Let's start our SD_WAN LAB *
****************************************************
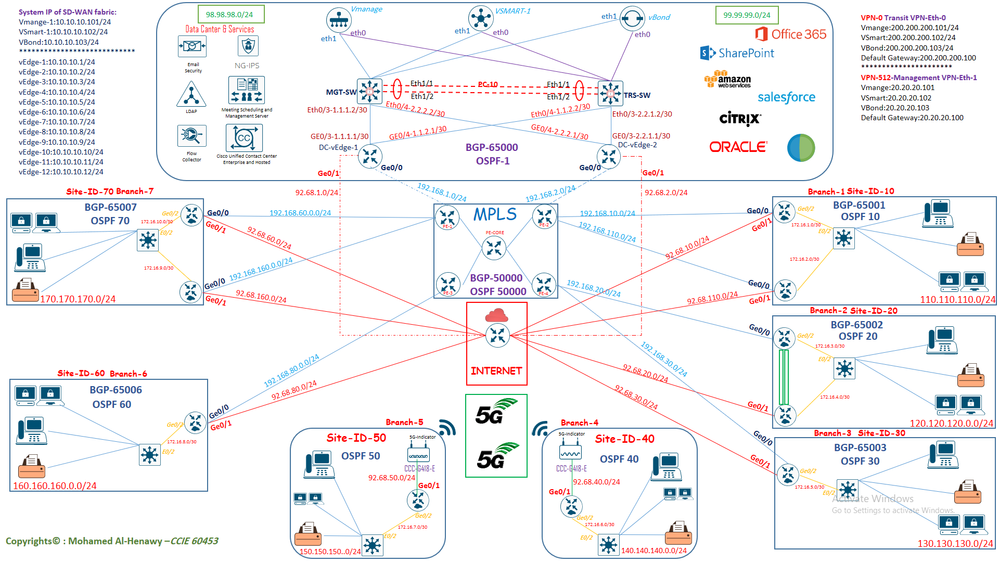
******* LAB TOPOLOGY *******
****************************************************
Initial Configuration for DC & LAN Switches :
****************************************************
1- Management Switch
****************************************************
spanning-tree mode rapid-pvst
spanning-tree extend system-id
interface Port-channel10
description UPLINK-MGT-TRS
switch port trunk encapsulation dot1q
switchport mode trunk
!
interface Ethernet0/0
switchport access vlan 20
switchport mode access
spanning-tree port fast edge
!
interface Ethernet0/1
switchport access vlan 20
switchport mode access
spanning-tree portfast edge
!
interface Ethernet0/2
switchport access vlan 20
switchport mode access
spanning-tree portfast edge
!
interface Ethernet0/3
description UPLINK-TO-Vedge-1
no switchport
ip address 1.1.1.2 255.255.255.252
duplex auto
!
interface Ethernet1/0
!
interface Ethernet1/1
switchport trunk encapsulation dot1q
switchport mode trunk
channel-protocol lacp
channel-group 10 mode active
!
interface Ethernet1/2
switchport trunk encapsulation dot1q
switchport mode trunk
channel-protocol lacp
channel-group 10 mode active
!
interface Ethernet1/3
!
interface Ethernet2/0
description UPLINK-TO-Vedge-2
no switchport
ip address 2.2.2.2 255.255.255.252
duplex auto
!
interface Vlan20
ip address 20.20.20.100 255.255.255.0
!
***************************************************
2- Trans-Switch
***************************************************
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
interface Port-channel10
description UPLINK-MGT-TRS
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface Ethernet0/0
description UPLINK-TO-VPN-0
switchport access vlan 200
switchport mode access
duplex auto
spanning-tree portfast edge
!
interface Ethernet0/1
description UPLINK-TO-VPN-0
switchport access vlan 200
switchport mode access
duplex auto
spanning-tree portfast edge
!
interface Ethernet0/2
description UPLINK-TO-VPN-0
switchport access vlan 200
switchport mode access
duplex auto
spanning-tree portfast edge
!
interface Ethernet0/3
no switchport
ip address 2.2.1.2 255.255.255.252
duplex auto
!
interface Ethernet1/0
!
interface Ethernet1/1
switchport trunk encapsulation dot1q
switchport mode trunk
channel-protocol lacp
channel-group 10 mode active
!
interface Ethernet1/2
switchport trunk encapsulation dot1q
switchport mode trunk
channel-protocol lacp
channel-group 10 mode active
!
interface Vlan200
ip address 200.200.200.100 255.255.255.0
!
***************************************************
3- LAN-Switch-Site-1
***************************************************
interface Loopback1
description IPTPF
ip address 110.110.110.1 255.255.255.255
!
interface Loopback2
description Printer
ip address 110.110.110.2 255.255.255.255
!
interface Loopback3
description PC
ip address 110.110.110.3 255.255.255.255
!
interface Ethernet0/0
ip address 172.16.1.2 255.255.255.252
!
interface Ethernet0/1
ip address 172.16.2.2 255.255.255.252
!
***************************************************
4-LAN-Switch-Site-2
***************************************************
interface Loopback1
description IPTPF
ip address 120.120.120.1 255.255.255.255
!
interface Loopback2
description Printer
ip address 120.120.120.2 255.255.255.255
!
interface Loopback3
description PC
ip address 120.120.120.3 255.255.255.255
!
interface Ethernet0/0
ip address 172.16.3.2 255.255.255.252
!
interface Ethernet0/1
ip address 172.16.4.2 255.255.255.252
!
***************************************************
5-LAN-Switch-Site-3
***************************************************
interface Loopback1
description IPTPF
ip address 130.130.130.1 255.255.255.255
!
interface Loopback2
description Printer
ip address 130.130.130.2 255.255.255.255
!
interface Loopback3
description PC
ip address 130.130.130.3 255.255.255.255
!
interface Ethernet0/0
ip address 172.16.5.2 255.255.255.252
!
***************************************************
6-LAN-Switch-Site-4
***************************************************
interface Loopback1
description IPTPF
ip address 140.140.140.1 255.255.255.255
!
interface Loopback2
description Printer
ip address 140.140.140.2 255.255.255.255
!
interface Loopback3
description PC
ip address 140.140.140.3 255.255.255.255
!
interface Ethernet0/0
ip address 172.16.6.2 255.255.255.252
!
***************************************************
7-LAN-Switch-Site-5
***************************************************
interface Loopback1
description IPTPF
ip address 150.150.150.1 255.255.255.255
!
interface Loopback2
description Printer
ip address 150.150.150.2 255.255.255.255
!
interface Loopback3
description PC
ip address 150.150.150.3 255.255.255.255
!
interface Ethernet0/0
ip address 172.16.7.2 255.255.255.252
!
***************************************************
8-LAN-Switch-Site-6
*************************************************
interface Loopback1
description IPTPF
ip address 160.160.160.1 255.255.255.255
!
interface Loopback2
description Printer
ip address 160.160.160.2 255.255.255.255
!
interface Loopback3
description PC
ip address 160.160.160.3 255.255.255.255
!
interface Ethernet0/0
ip address 172.16.8.2 255.255.255.252
!
***************************************************
9-LAN-Switch-Site-7
***************************************************
interface Loopback1
description IPTPF
ip address 170.170.170.1 255.255.255.255
!
interface Loopback2
description Printer
ip address 170.170.170.2 255.255.255.255
!
interface Loopback3
description PC
ip address 170.170.170.3 255.255.255.255
!
interface Ethernet0/0
ip address 172.16.10.2 255.255.255.252
!
interface Ethernet0/1
ip address 172.16.9.2 255.255.255.252
******************************************************
Internet Service Provider
******************************************************
!
interface Ethernet0/0
ip address 92.68.50.1 255.255.255.0
!
interface Ethernet0/1
ip address 92.68.40.1 255.255.255.0
!
interface Ethernet0/2
ip address 92.68.20.1 255.255.255.0
!
interface Ethernet0/3
ip address 92.68.10.1 255.255.255.0
!
interface Ethernet1/0
ip address 92.68.110.1 255.255.255.0
!
interface Ethernet1/1
ip address 92.68.30.1 255.255.255.0
!
interface Ethernet1/2
ip address 92.68.60.1 255.255.255.0
!
interface Ethernet1/3
ip address 92.68.170.1 255.255.255.0
!
interface Ethernet2/0
ip address 92.68.70.1 255.255.255.0
******************************************************
MPLS Service Provider
******************************************************
SP-CORE
******************************************************
interface Loopback0
ip address 5.5.5.5 255.255.255.255
!
interface Ethernet0/0
ip address 10.10.1.2 255.255.255.0
!
interface Ethernet0/1
ip address 10.10.2.2 255.255.255.0
!
interface Ethernet0/2
ip address 10.10.4.2 255.255.255.0
!
interface Ethernet0/3
ip address 10.10.3.2 255.255.255.0
!
router ospf 50000
mpls ldp auto config area 0
router-id 5.5.5.5
network 5.5.5.5 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 5.5.5.5
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor CORE peer-group
neighbor CORE remote-as 50000
neighbor CORE log-neighbor-changes
neighbor CORE update-source Loopback0
neighbor 1.1.1.1 peer-group CORE
neighbor 2.2.2.2 peer-group CORE
neighbor 3.3.3.3 peer-group CORE
neighbor 4.4.4.4 peer-group CORE
!
address-family ipv4
network 5.5.5.5 mask 255.255.255.255
redistribute connected
redistribute ospf 50000
neighbor CORE send-community both
neighbor CORE route-reflector-client
neighbor CORE next-hop-self
neighbor 1.1.1.1 activate
neighbor 2.2.2.2 activate
neighbor 3.3.3.3 activate
neighbor 4.4.4.4 activate
exit-address-family
!
address-family vpnv4
neighbor CORE send-community both
neighbor CORE route-reflector-client
neighbor CORE next-hop-self
neighbor 1.1.1.1 activate
neighbor 2.2.2.2 activate
neighbor 3.3.3.3 activate
neighbor 4.4.4.4 activate
exit-address-family
!
mpls label protocol ldp
mpls ldp router-id Loopback0 force
mpls ldp neighbor 1.1.1.1 password CISCO
mpls ldp neighbor 2.2.2.2 password CISCO
mpls ldp neighbor 3.3.3.3 password CISCO
mpls ldp neighbor 4.4.4.4 password CISCO
mpls ldp neighbor 5.5.5.5 password CISCO
!
******************************************************
SP-PE-1
******************************************************
ip vrf DC-S-1
rd 50000:1
route-target export 50000:1
route-target import 50000:1
route-target import 50000:70
route-target import 50000:170
route-target import 50000:2
route-target import 50000:10
route-target import 50000:110
route-target import 50000:60
route-target import 50000:20
route-target import 50000:30
!
ip vrf SITE-7-S-1
rd 50000:70
route-target export 50000:70
route-target import 50000:70
route-target import 50000:1
route-target import 50000:170
route-target import 50000:2
route-target import 50000:10
route-target import 50000:110
route-target import 50000:60
route-target import 50000:20
route-target import 50000:30
!
ip vrf SITE-7-S-2
rd 50000:170
route-target export 50000:170
route-target import 50000:170
route-target import 50000:1
route-target import 50000:70
route-target import 50000:2
route-target import 50000:10
route-target import 50000:110
route-target import 50000:60
route-target import 50000:20
route-target import 50000:30
!
!
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 2.2.2.2 password CISCO
mpls ldp neighbor 1.1.1.1 password CISCO
mpls ldp neighbor 3.3.3.3 password CISCO
mpls ldp neighbor 4.4.4.4 password CISCO
mpls ldp neighbor 5.5.5.5 password CISCO
!
!
!
!
!
!
!
cts logging verbose
!
!
!
redundancy
!
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding DC-S-1
ip address 192.168.1.1 255.255.255.0
ip ospf 1 area 0
!
interface Ethernet0/1
ip address 10.10.1.1 255.255.255.0
!
interface Ethernet0/2
ip vrf forwarding SITE-7-S-2
ip address 192.168.170.1 255.255.255.0
ip ospf 170 area 0
!
interface Ethernet0/3
ip vrf forwarding SITE-7-S-1
ip address 192.168.70.1 255.255.255.0
ip ospf 70 area 0
!
!
router ospf 70 vrf SITE-7-S-1
redistribute bgp 50000 subnets
!
router ospf 170 vrf SITE-7-S-2
redistribute bgp 50000 subnets
!
router ospf 1 vrf DC-S-1
redistribute bgp 50000 subnets
!
router ospf 50000
mpls ldp autoconfig area 0
router-id 1.1.1.1
redistribute bgp 50000 subnets
network 1.1.1.1 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 1.1.1.1
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 5.5.5.5 remote-as 50000
neighbor 5.5.5.5 update-source Loopback0
!
address-family ipv4
network 1.1.1.1 mask 255.255.255.255
redistribute ospf 50000
neighbor 5.5.5.5 activate
neighbor 5.5.5.5 send-community both
neighbor 5.5.5.5 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 5.5.5.5 activate
neighbor 5.5.5.5 send-community both
neighbor 5.5.5.5 next-hop-self
exit-address-family
!
address-family ipv4 vrf DC-S-1
redistribute static
redistribute ospf 1
neighbor 192.168.1.2 remote-as 65000
neighbor 192.168.1.2 activate
exit-address-family
!
address-family ipv4 vrf SITE-7-S-1
redistribute connected
redistribute static
redistribute ospf 70
neighbor 192.168.70.2 remote-as 65007
neighbor 192.168.70.2 activate
exit-address-family
!
address-family ipv4 vrf SITE-7-S-2
redistribute connected
redistribute static
redistribute ospf 170
neighbor 192.168.170.2 remote-as 65007
neighbor 192.168.170.2 activate
exit-address-family
!
ip forward-protocol nd
!
!
ip http server
ip http secure-server
!
!
!
mpls ldp router-id Loopback0 force
!
******************************************************
SP-PE-2
******************************************************
!
ip vrf DC-S-2
rd 50000:2
route-target export 50000:2
route-target import 50000:2
route-target import 50000:1
route-target import 50000:70
route-target import 50000:170
route-target import 50000:10
route-target import 50000:110
route-target import 50000:60
route-target import 50000:20
route-target import 50000:30
!
ip vrf SITE-1-S-1
rd 50000:10
route-target export 50000:10
route-target import 50000:10
route-target import 50000:1
route-target import 50000:70
route-target import 50000:170
route-target import 50000:2
route-target import 50000:110
route-target import 50000:60
route-target import 50000:20
route-target import 50000:30
!
ip vrf SITE-1-S-2
rd 50000:110
route-target export 50000:110
route-target import 50000:110
route-target import 50000:1
route-target import 50000:70
route-target import 50000:170
route-target import 50000:2
route-target import 50000:10
route-target import 50000:60
route-target import 50000:20
route-target import 50000:30
!
!
!
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password CISCO
mpls ldp neighbor 2.2.2.2 password CISCO
mpls ldp neighbor 3.3.3.3 password CISCO
mpls ldp neighbor 4.4.4.4 password CISCO
mpls ldp neighbor 5.5.5.5 password CISCO
!
!
!
cts logging verbose
!
!
redundancy
!
!
interface Loopback0
ip address 2.2.2.2 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding DC-S-2
ip address 192.168.2.1 255.255.255.0
ip ospf 2 area 0
!
interface Ethernet0/1
ip address 10.10.2.1 255.255.255.0
!
interface Ethernet0/2
ip vrf forwarding SITE-1-S-1
ip address 192.168.10.1 255.255.255.0
ip ospf 10 area 0
!
interface Ethernet0/3
ip vrf forwarding SITE-1-S-2
ip address 192.168.110.1 255.255.255.0
ip ospf 110 area 0
!
router ospf 2 vrf DC-S-2
redistribute bgp 50000 subnets
!
router ospf 10 vrf SITE-1-S-1
redistribute bgp 50000 subnets
!
router ospf 110 vrf SITE-1-S-2
redistribute bgp 50000 subnets
!
router ospf 50000
mpls ldp autoconfig area 0
router-id 2.2.2.2
network 2.2.2.2 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 2.2.2.2
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 5.5.5.5 remote-as 50000
neighbor 5.5.5.5 update-source Loopback0
!
address-family ipv4
network 2.2.2.2 mask 255.255.255.255
redistribute ospf 50000
neighbor 5.5.5.5 activate
neighbor 5.5.5.5 send-community both
neighbor 5.5.5.5 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 5.5.5.5 activate
neighbor 5.5.5.5 send-community both
neighbor 5.5.5.5 next-hop-self
exit-address-family
!
address-family ipv4 vrf DC-S-2
redistribute ospf 2
neighbor 192.168.2.2 remote-as 65000
neighbor 192.168.2.2 activate
exit-address-family
!
address-family ipv4 vrf SITE-1-S-1
redistribute ospf 10
neighbor 192.168.10.2 remote-as 65001
neighbor 192.168.10.2 activate
exit-address-family
!
address-family ipv4 vrf SITE-1-S-2
redistribute ospf 110
neighbor 192.168.110.2 remote-as 65001
neighbor 192.168.110.2 activate
exit-address-family
!
ip forward-protocol nd
!
!
mpls ldp router-id Loopback0 force
!
control-plane
******************************************************
SP-PE-3
******************************************************
ip vrf SITE-6-S-1
rd 50000:60
route-target export 50000:60
route-target import 50000:60
route-target import 50000:1
route-target import 50000:70
route-target import 50000:170
route-target import 50000:2
route-target import 50000:10
route-target import 50000:110
route-target import 50000:20
route-target import 50000:30
!
!
!
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password CISCO
mpls ldp neighbor 2.2.2.2 password CISCO
mpls ldp neighbor 3.3.3.3 password CISCO
mpls ldp neighbor 4.4.4.4 password CISCO
mpls ldp neighbor 5.5.5.5 password CISCO
!
!
interface Loopback0
ip address 3.3.3.3 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding SITE-6-S-1
ip address 192.168.60.1 255.255.255.0
ip ospf 60 area 0
!
interface Ethernet0/1
ip address 10.10.3.1 255.255.255.0
!
router ospf 60 vrf SITE-6-S-1
redistribute bgp 50000 subnets
!
router ospf 50000
mpls ldp autoconfig area 0
router-id 3.3.3.3
network 3.3.3.3 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 3.3.3.3
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 5.5.5.5 remote-as 50000
neighbor 5.5.5.5 update-source Loopback0
!
address-family ipv4
network 3.3.3.3 mask 255.255.255.255
redistribute ospf 50000
neighbor 5.5.5.5 activate
neighbor 5.5.5.5 send-community both
neighbor 5.5.5.5 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 5.5.5.5 activate
neighbor 5.5.5.5 send-community both
neighbor 5.5.5.5 next-hop-self
exit-address-family
!
address-family ipv4 vrf SITE-6-S-1
redistribute ospf 60
neighbor 192.168.60.2 remote-as 65006
neighbor 192.168.60.2 activate
exit-address-family
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
!
!
mpls ldp router-id Loopback0 force
!
control-plane
!
!
******************************************************
SP-PE-4
******************************************************
ip vrf SITE-2-S-1
rd 50000:20
route-target export 50000:20
route-target import 50000:20
route-target import 50000:1
route-target import 50000:70
route-target import 50000:170
route-target import 50000:2
route-target import 50000:10
route-target import 50000:110
route-target import 50000:60
route-target import 50000:30
!
ip vrf SITE-3-S-1
rd 50000:30
route-target export 50000:30
route-target import 50000:30
route-target import 50000:1
route-target import 50000:70
route-target import 50000:170
route-target import 50000:2
route-target import 50000:10
route-target import 50000:110
route-target import 50000:60
route-target import 50000:20
!
!
!
!
ip cef
ipv6 cef
!
multilink bundle-name authenticated
mpls label protocol ldp
mpls ldp neighbor 1.1.1.1 password CISCO
mpls ldp neighbor 2.2.2.2 password CISCO
mpls ldp neighbor 3.3.3.3 password CISCO
mpls ldp neighbor 4.4.4.4 password CISCO
mpls ldp neighbor 5.5.5.5 password CISCO
!
interface Loopback0
ip address 4.4.4.4 255.255.255.255
!
interface Ethernet0/0
ip vrf forwarding SITE-2-S-1
ip address 192.168.20.1 255.255.255.0
ip ospf 20 area 0
!
interface Ethernet0/1
ip address 10.10.4.1 255.255.255.0
!
interface Ethernet0/2
ip vrf forwarding SITE-3-S-1
ip address 192.168.30.1 255.255.255.0
ip ospf 30 area 0
!
router ospf 20 vrf SITE-2-S-1
redistribute bgp 50000 subnets
!
router ospf 30 vrf SITE-3-S-1
redistribute bgp 50000 subnets
!
router ospf 50000
mpls ldp autoconfig area 0
router-id 4.4.4.4
network 4.4.4.4 0.0.0.0 area 0
network 10.10.0.0 0.0.255.255 area 0
!
router bgp 50000
bgp router-id 4.4.4.4
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 5.5.5.5 remote-as 50000
neighbor 5.5.5.5 update-source Loopback0
!
address-family ipv4
network 4.4.4.4 mask 255.255.255.255
redistribute ospf 50000
neighbor 5.5.5.5 activate
neighbor 5.5.5.5 send-community both
neighbor 5.5.5.5 next-hop-self
exit-address-family
!
address-family vpnv4
neighbor 5.5.5.5 activate
neighbor 5.5.5.5 send-community both
neighbor 5.5.5.5 next-hop-self
exit-address-family
!
address-family ipv4 vrf SITE-2-S-1
redistribute ospf 20
neighbor 192.168.20.2 remote-as 65002
neighbor 192.168.20.2 activate
exit-address-family
!
address-family ipv4 vrf SITE-3-S-1
redistribute ospf 30
neighbor 192.168.30.2 remote-as 65003
neighbor 192.168.30.2 activate
exit-address-family
!
ip forward-protocol nd
!
!
!
mpls ldp router-id Loopback0 force
!
control-plane
!
******************************************************
V-Manage
******************************************************
Welcome to Viptela CLI
admin connected from 127.0.0.1 using console on Vmanage
config
system
host-name Vmanage
system-ip 10.10.10.101
site-id 100
admin-tech-on-failure
sp-organization-name "Cisco-ARCH"
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
vpn 0
interface eth0
description Connect-To-VPN-0-TRNS
ip address 200.200.200.101/24
ipv6 dhcp-client
tunnel-interface
allow-service all
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
interface eth1
ip dhcp-client
no shutdown
!
ip route 0.0.0.0/0 192.168.205.2
******************************************************
V-Smart
******************************************************
system
host-name v-smart
system-ip 10.10.10.102
site-id 100
admin-tech-on-failure
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
!
vpn 0
interface eth0
ip address 200.200.200.102/24
ipv6 dhcp-client
tunnel-interface
allow-service all
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service stun
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
interface eth1
ip address 20.20.20.102/24
no shutdown
!
ip route 0.0.0.0/0 20.20.20.100
!
******************************************************
V-Bond
******************************************************
Welcome to Viptela CLI
system
host-name vbond
system-ip 10.10.10.103
site-id 100
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103 local
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 200.200.200.103/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
interface eth0
ip address 20.20.20.103/24
no shutdown
!
ip route 0.0.0.0/0 20.20.20.100
!
******************************************************
Open Vmanage through GUI and Generate the CA and Add the controllers include V-samrt & V-bond
******************************************************
Access to the ip address of the vmanage : https://192.168.205.151/#/app/config/devices/controller and Add the V-smart Controller
Configure ----> Device -----> Controller ----->add controller -----> V-samrt -----> write ip address -----> save
Configure ----> Device -----> Controller ----->add controller -----> V-bond -----> write ip address -----> save
Generate the certificate for the V-smart & V-Bond and install on the vmanage
******************************************************
Certification Installation - vManage:
******************************************************
- Go to shell mode---> vshell
- Generate RK ---> openssl genrsa -out ROOTCA.key
- Generate ROOTCA.pem
openssl req -x509 -new -nodes -key ROOTCA.key -sha256 -days 365 \
-subj "/C=US/ST=Egypt/L=Cairo/O=Cisco-ARCH/CN=Cisco-ARCH" \
-out ROOTCA.pem
-Copy the contents of ROOTCA.pem by below steps:
vManage cli --> vshell --> cat ROOTCA.pem
-Change the Controller Certificate Authorization to use Enterprise Root Certificate in vManage GUI -->Controller Certificate Authorization -->and paste the copy contents here.
- CREATING CSR FOR vMANAGE:
vManage GUI --> Config --> Cert --> Controllers --> vManage --> Generate CSR
Copy the contents of CSR -- > vshell --> ls (to check vmanage.csr file is there or not) if not we need to create it by vim vmanage.csr and paste the contents from step 6 using below method.
-Create a file in vManage vshell named "vim vmanage.csr"
Press "i" to insert.
Press Esc, and type :wq and press Enter. (to save file in vim)
- vManage --> vshell --> cat vmange.crt
copy the contents .. go to vmange GUI --> cert --> controllers --> install cert -- and paste it and install.
******************************************************
Certification Installation - v-Bond:
******************************************************
- Add vBond to control plane from vManage GUI and generate certificate.
- Copy the generated certificate:
Create a file in vManage vshell named "vim vbond.csr"
Press "i" to insert.
Press Esc, and type :wq and press Enter. (to save file in vim)
- Use below command to create vbond.crt.
openssl x509 -req -in vbond.csr \
-CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial \
-out vbond.crt -days 365 -sha256
- In vmange --> vshell --> ls (You will see vbond.crt) --> cat vbond.crt
copy the content of vbond.crt
Go to vManage GUI --> Certificates --> Controllers --> Install Certificate (Paste it here) and click install.
******************************************************
Certification Installation - v-Smart:
******************************************************
- Add v-Smart to control plane from vManage GUI and generate certificate.
- Copy the generated certificate:
Create a file in vManage vshell named "vim vsmart.csr"
Press "i" to insert.
Press Esc, and type :wq and press Enter. (to save file in vim)
- Use below command to create vbond.crt.
openssl x509 -req -in vsmart.csr \
-CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial \
-out vsmart.crt -days 365 -sha256
In vmange --> vshell --> ls (You will see vbond.crt) --> cat vsmart.crt
copy the content of vsmart.crt
Go to vManage GUI --> Certificates --> Controllers --> Install Certificate (Paste it here) and click install.
Once Finish start the process to upload Wan Edge list Serial number to V-Manage
Initial Configuration for V-Edges
******************************************************
Edge-1
******************************************************
interface Ethernet0/0
ip address 192.168.1.2 255.255.255.0
!
interface Ethernet0/1
ip address 92.68.1.2 255.255.255.0
!
interface Ethernet0/2
no ip address
shutdown
!
interface Ethernet0/3
ip address 1.1.1.1 255.255.255.252
ip ospf 65000 area 0
!
router ospf 65000
redistribute connected subnets
redistribute static subnets
network 0.0.0.0 255.255.255.255 area 0
!
ip forward-protocol nd!
control-plane
******************************************************
Edge-2
******************************************************
interface Ethernet0/0
ip address 192.168.2.2 255.255.255.0
!
interface Ethernet0/1
ip address 92.68.2.2 255.255.255.0
ip ospf 200 area 0
!
interface Ethernet0/2
no ip address
shutdown
!
interface Ethernet0/3
ip address 2.2.1.1 255.255.255.252
ip ospf 65000 area 0
!
router ospf 65000
redistribute connected subnets
redistribute static subnets
!
router ospf 200
!
ip forward-protocol nd
******************************************************
V-Edge-3
******************************************************
system
host-name vedge3
system-ip 10.10.10.3
site-id 10
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$VCWr0lO6AuUXq5Lq$pB5Sbj2Y3aThQH8mB1dxJ48MeoyFsnzfy5Yw48tcOTF8hCbbRDc/jWDuNMLL2UgFrkorVRwgzh8rJa/pWis9b.
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 192.168.10.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.10.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
******************************************************
V-Edge-4
******************************************************
system
host-name vedge4
system-ip 10.10.10.4
site-id 10
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$kdYaJgEKgTE1lYPg$790vxuzZsntcANPeszeY3n5zEHki3nNAgHvk1w4QIJfL/8Lc2.iyrqfJThY0rdGOBWdzhyoU8ZK3QjE0ljnGc/
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 192.168.110.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.110.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
******************************************************
V-Edge-5
******************************************************
system
host-name vedge5
system-ip 10.10.10.5
site-id 20
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$NHI7YW/5h5RP7Gl1$EawSHFWSCGTLuL9A.zINchu0MVeb4ZE/QkDugZJAIt3E9hpKrY9Szm0L5cV6w6UzuIw5gUTGJ7WzU6ISv7yVU0
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 192.168.20.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.20.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
******************************************************
V-Edge-6
******************************************************
system
host-name vedge6
system-ip 10.10.10.6
site-id 20
admin-tech-on-failure
no route-consistency-check
organization-name"Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$OW9PFx22kGwp07mL$7.zL8RFr2/soNnki9mVnzAFMowdJhE00j632EXVVZxc/zcIXLHaSOTwQX13GhhZ.eHxiSyBs6BFt4v2yweCXO0
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
router
ospf
timers spf 200 1000 10000
area 0
interface ge0/1
exit
exit
!
!
interface ge0/1
ip address 92.68.20.2/24
tunnel-interface
encapsulation ipsec
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 92.68.20.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
******************************************************
V-Edge-7
******************************************************
system
host-name vedge7
system-ip 10.10.10.7
site-id 30
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$Wzq28VHh8I.vHQY5$2hp2UpSLT3IZ1Zx16nudgD/uS789TZTsqcfSi/c1yi0RgNXjT/LQBFS0YxxTxTqusOnK.OWIxvxOL91BM/EOU.
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 192.168.30.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.30.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
******************************************************
V-Edge-8
******************************************************
system
host-name vedge8
system-ip 10.10.10.8
site-id 40
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$.KEyw/4ylWbWRBHf$CHYbWd4rp6DcMAHDw0mVcTOc0gLhyC7bO7rIhoijsYNsVZ4THenElrEG0K3jd2F7tSr3RZaHcRhSlaoC3lMhm0
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/1
ip address 92.68.40.2/24
tunnel-interface
encapsulation gre
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 92.68.40.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
******************************************************
V-Edge-9
******************************************************
system
host-name vedge9
system-ip 10.10.10.9
site-id 50
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$e9MOUVqPdEygM8Ne$tQF0SSmNolqdv9UsBFYicTzhfxtLQzsZZ0xkcv574O3ZSk62Lydnx7KTje8y2v.HVapxxxPNQXR5etxSjmx2u0
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/1
ip address 92.68.50.2/24
tunnel-interface
encapsulation gre
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 92.68.50.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
******************************************************
V-Edge-10
******************************************************
system
host-name vedge10
system-ip 10.10.10.10
site-id 60
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$rrdeQ5D9nmbVhka9$KzIcOifpliu6QQMIDD2lfFO4RjTN0ARsEpuPPryMQGT6SOpmECFnYXZZ2IDK9AlpGbzLP/n7GzjTPYYOhUXMa/
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 192.168.60.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.60.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
******************************************************
V-Edge-11
******************************************************
system
host-name vedge11
system-ip 10.10.10.11
site-id 70
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$0Yk6/BKcz/DUuXXo$k2o2vhy8SZuY9dXnUlHdF.IL.SgAtt5yvcX5UGq2L9OFuYaleMTkpvM.FeqFyAXR9Qh1U2QMvvtyVgCB1fIeD.
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
router
ospf
timers spf 200 1000 10000
area 0
interface ge0/0
exit
exit
!
!
interface ge0/0
ip address 192.168.70.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.70.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!
******************************************************
V-Edge-12
******************************************************
system
host-name vedge12
system-ip 10.10.10.12
site-id 70
admin-tech-on-failure
no route-consistency-check
organization-name "Cisco-ARCH"
clock timezone Africa/Cairo
vbond 200.200.200.103
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$jH1.AEHiGCFi9f.p$B8Thld1CTDMrrTZf.lnsvNvGCKi6uAw.w6jmQRh6ML3.hs/y4O1XlZH4wC0RDGGmXwiZJWQxaEtFaAHV0nHlE.
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip address 192.168.170.2/24
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 192.168.170.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
---------------------------------------------------------------------------------------------
Verification reachability to Controllers :
vedge3# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
vedge4# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
vedge5# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
vedge6# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
vedge7# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
vedge8# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
vedge9# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
vedge10# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
vedge11# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
vedge12# ping 200.200.200.103
Ping in VPN 0
PING 200.200.200.103 (200.200.200.103) 56(84) bytes of data.
64 bytes from 200.200.200.103: icmp_seq=1 ttl=59 time=39.1 ms
64 bytes from 200.200.200.103: icmp_seq=2 ttl=59 time=44.8 ms
--- 200.200.200.103 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 39.106/41.976/44.846/2.870 ms
vedge3# ping 200.200.200.102
Ping in VPN 0
PING 200.200.200.102 (200.200.200.102) 56(84) bytes of data.
64 bytes from 200.200.200.102: icmp_seq=1 ttl=59 time=18.6 ms
64 bytes from 200.200.200.102: icmp_seq=2 ttl=59 time=10.8 ms
--- 200.200.200.102 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 10.822/16.336/19.555/3.920 ms
vedge3# ping 200.200.200.101
Ping in VPN 0
PING 200.200.200.101 (200.200.200.101) 56(84) bytes of data.
64 bytes from 200.200.200.101: icmp_seq=1 ttl=59 time=22.5 ms
64 bytes from 200.200.200.101: icmp_seq=2 ttl=59 time=25.2 ms
******************************
Stay tuned for part || , Press Star if it's helpful for your knowledge !
***** I hope that has been informative for you and thank you *****
Mohamed Alhenawy
CCIE#60453
-
Announcements
-
Assurance and Policy
-
Automation
-
Buying Recommendation
-
Catalyst 9000 Switches
-
Catalyst Switch
-
Cisco ENCS
-
Cloud Networking
-
Configuration
-
LAN
-
LAN Switching
-
Network Management
-
NFVIS
-
Other Network Architecture
-
Other Networking
-
Other Routers
-
Other Routing
-
Other SD-WAN
-
Other Switches
-
Other Switching
-
Routing
-
SD-WAN
-
vEdge Routers
-
WAN
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Mohamed Alhenawy great work. Can you share me the eve-ng lab or perhaps dcloud lab if you have
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @navchoud
Thanks Mate , yes sure please share your mail by DM .
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Mohamed, thanks for sharing. kindly share the eve-ng lab
Thanks
rono
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Mohamed Alhenawy
Can you share the files eve-ng please?
Thank you
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Mohamed.
Many thanks for this can you please share the EVE-NG files.
Regards
Wayne
- « Previous
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: