- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- SD-WAN Overview & Advanced Deployment Lab | Part.2
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-16-2021 08:36 AM - edited 05-17-2021 07:26 AM
Today I'm going to write SD-WAN Overview & Advanced Deployment Lab Part ||
* check out SD-WAN Overview & Advanced Deployment Lab Part | through this link :
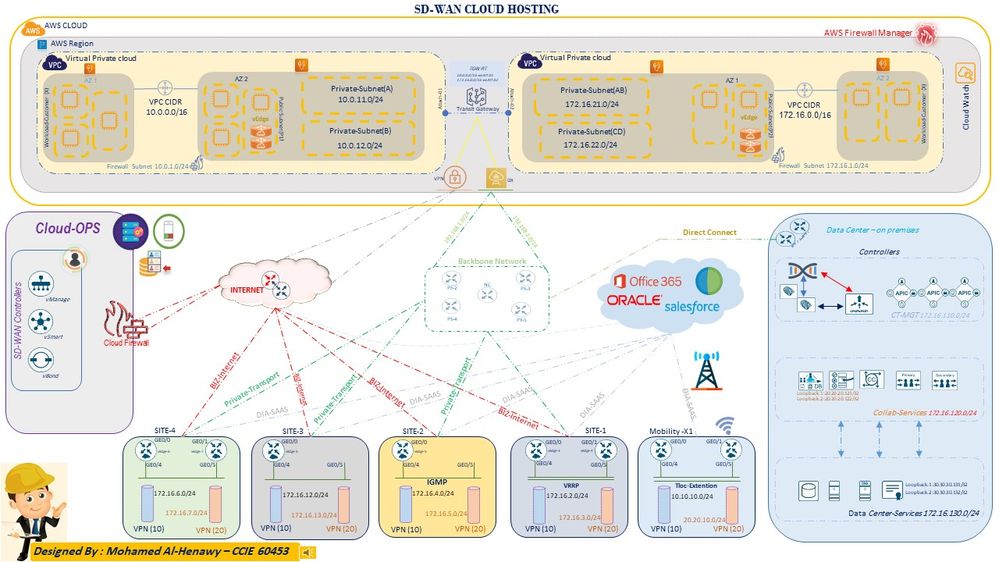
Cisco Viptela SD-WAN on your platform:-
The Cisco Viptela SD-WAN solution can deployed on a different platforms is called WAN Edge routers, which are available in different resources , Regardless of which deployment is chosen, all WAN Edge routers will be part of the SD-WAN overlay fabric and managed by vManage.
There are two types of platforms that can be deployed as part of Cisco viptela SD-WAN:
1. Hardware platforms

- vEdge 100 Router
- vEdge 100b Router
- vEdge 100m Router
- vEdge 100wm Router
- vEdge 1000 Router
- vEdge 2000 Router
- vEdge 5000 Router
Integrated Services Router ISR 4000 and Aggregation Services Router ASR 1000 Series which 's running IOS® XE SDWAN
Software.
● Cisco ASR 1000 Series Aggregation Services Routers
● Cisco 1000 Series ISRs
● Cisco 4000 Series ISRs
● Cisco 5400 ENCS
Existing routers must run 17.2.1 or a later release to interoperate with the Cisco IOS XE SD-WAN image. This is because of code changes introduced to support Bidirectional Forwarding Detection (BFD) tunnel building between a vEdge router and Cisco IOS XE based router.
NOTE : Check out this link : https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/sd-wan/white_paper-c11-741071.html
2. Virtual platforms
• Cloud Services Router (CSR) 1000v running IOS XE SD-WAN Software
• vEdge Cloud Router running Viptela OS
NOTE: Virtual platforms can also run on any hypervisor such as KVM or VMware ESXi.
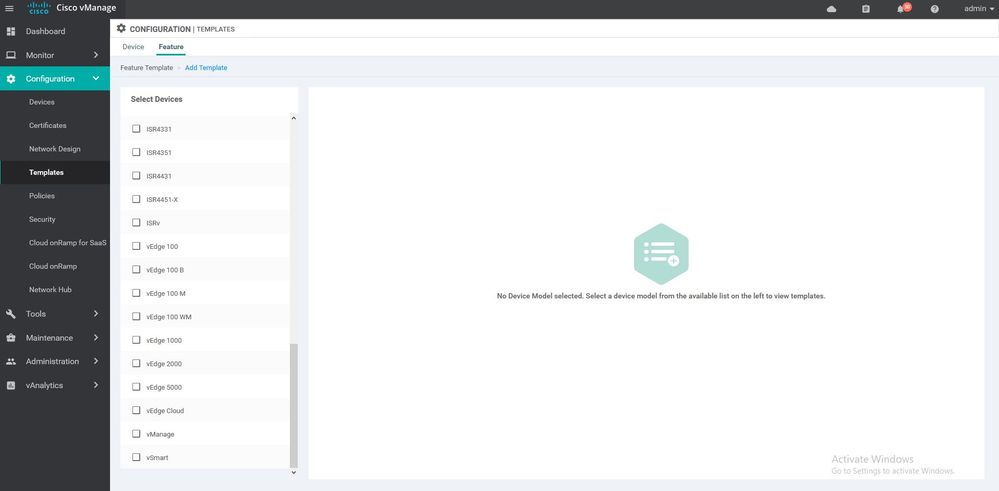
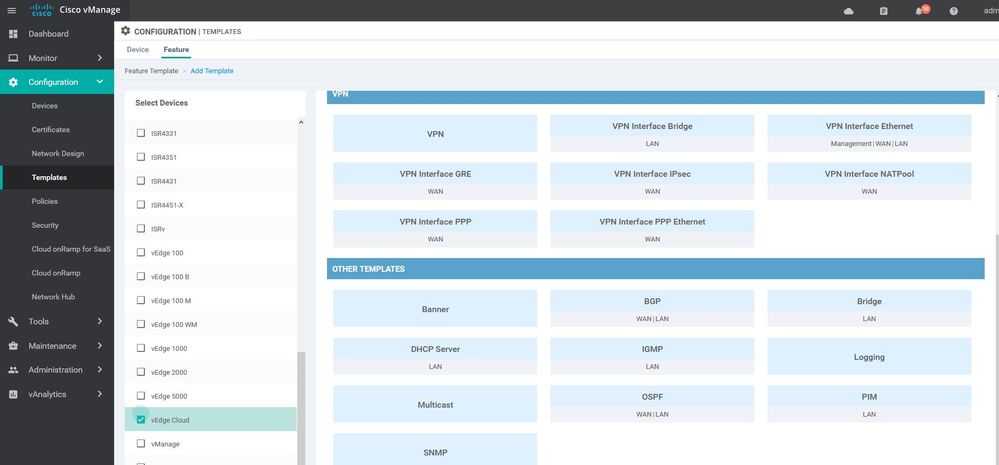
Feature TEMPLATES & Devices TEMPLATES :-
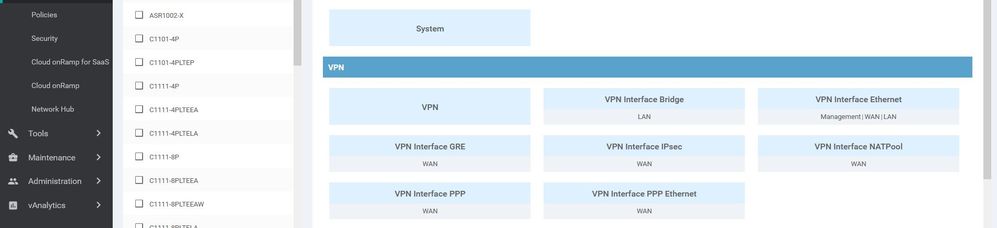
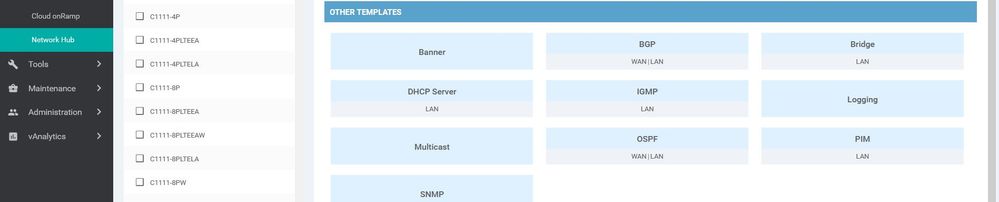
Feature templates are the building blocks for a device’s configuration. Feature templates has three categories < BASIC INFORMATION , VPN ,OTHER TEMPLATES> once you choose the device model device you will see all the available feature .
features templates categories :
- BASIC INFORMATION templates : AAA , Archive ,BFD ,NTP , OMP , Security , System ..
- VPN templates : VPN , VPN Interface Bridge , VPN Interface Ethernet , Management , VPN Interface GRE , VPN Interface IPsec, VPN Interface NATPool, etc ....
- OTHER TEMPLATES: Banner , BGP , Bridge , DHCP Server , IGMP , Logging , Multicast , OSPF, etc...
DEVICES Templet :
Device templates contain a devices complete configuration. You can create device templates by collecting all the feature templates which 's you have done for specific device model, device templates allows customers to configure thousands of devices within few seconds.
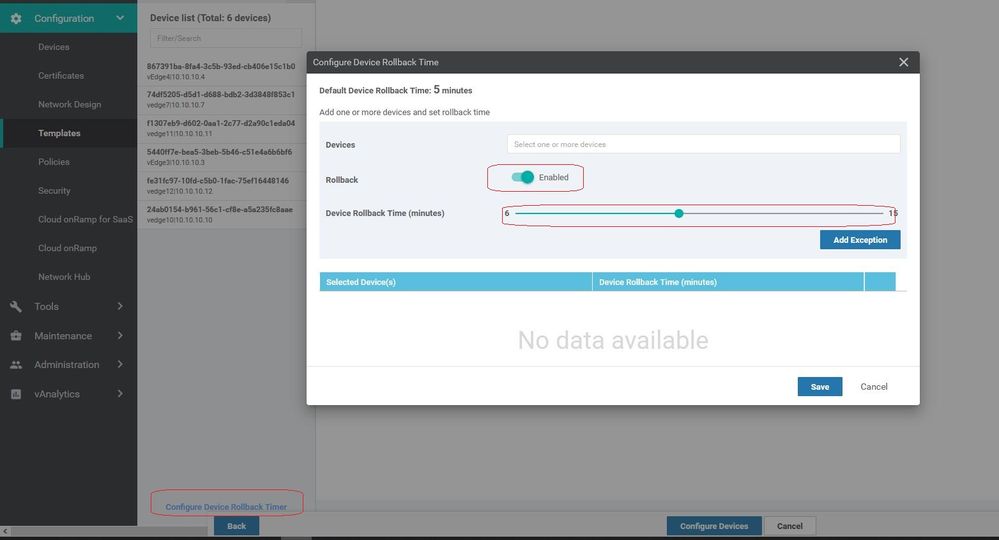
NOTE : In case of configuration errors, the template configuration rolls back to its previous state.
LAB Configurations :
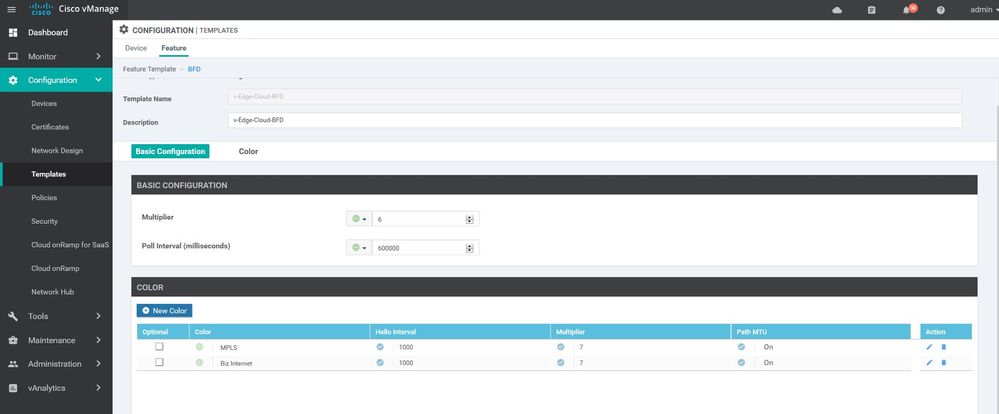
BFD Templet:
Configuration ----> Templates ----> features ----> Add Template ---->BFD
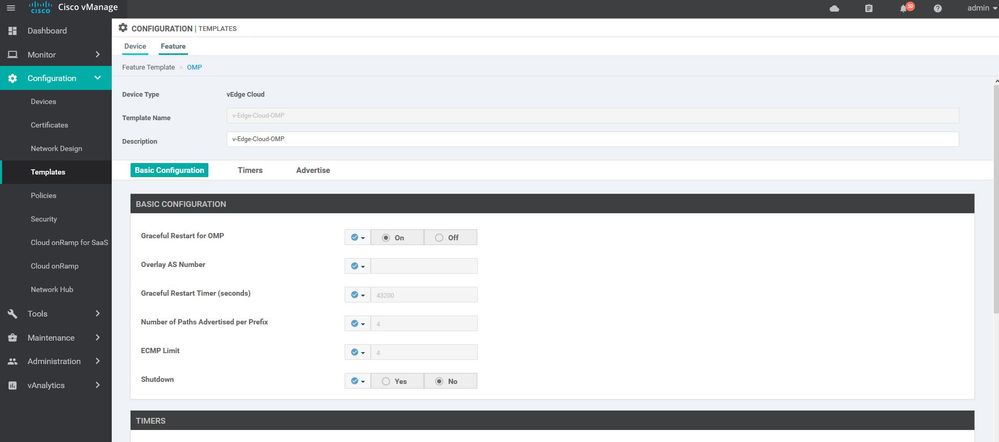
WAN Edge OMP
Configuration ----> Templates ----> features ----> Add Template ---->OMP
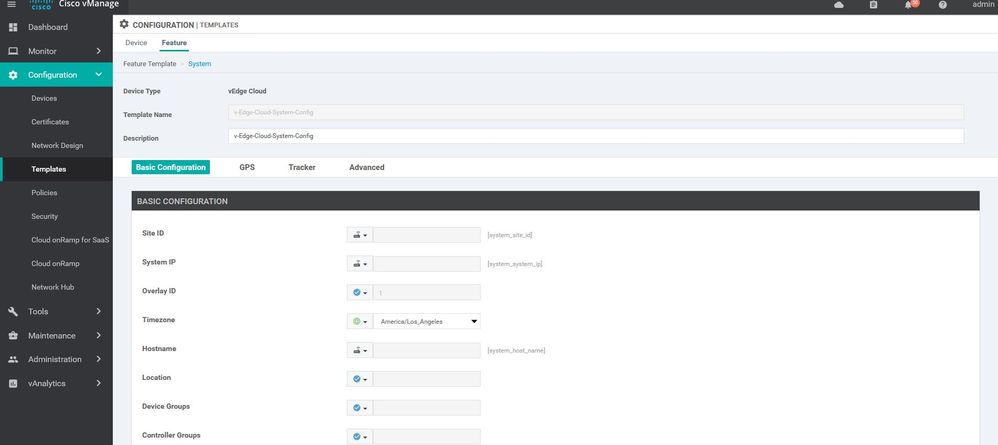
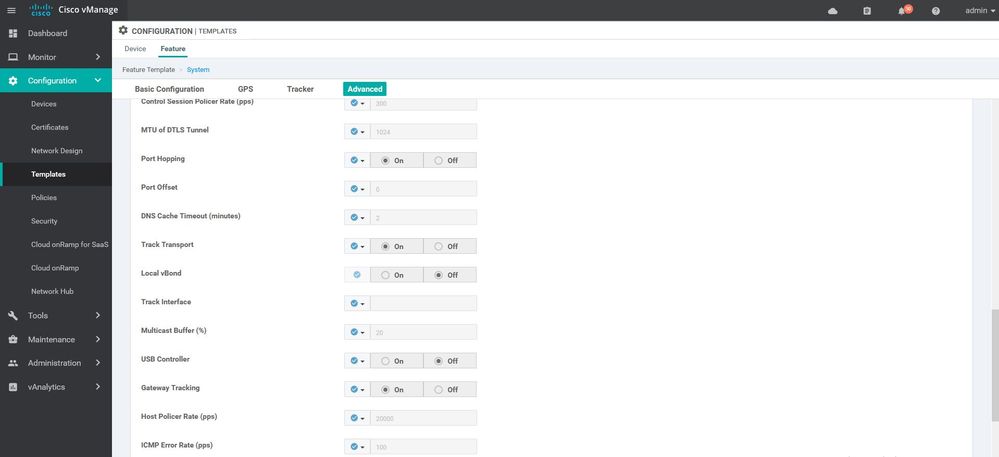
WAN Edge System
Configuration ----> Templates ----> features ----> Add Template ---->WAN Edge System
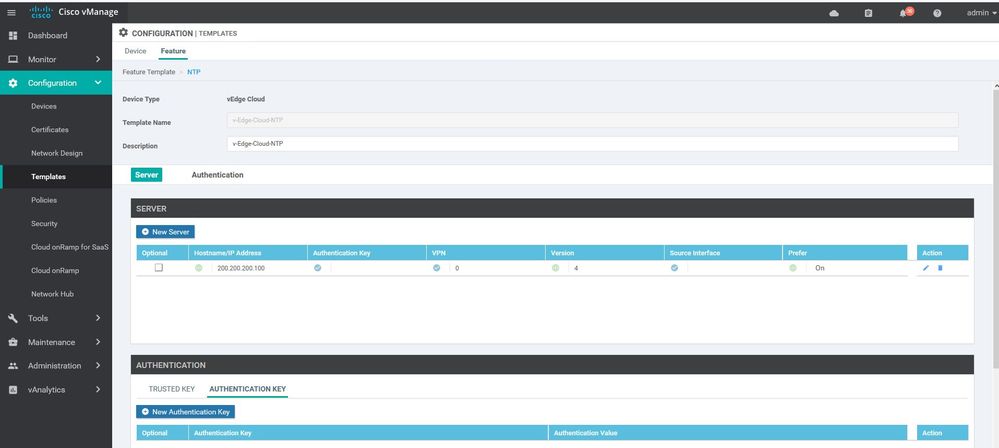
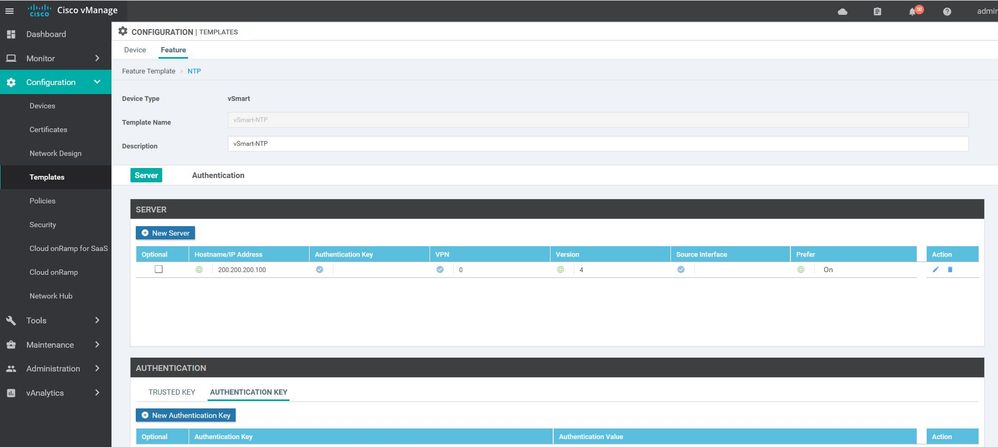
NTP
Configuration ----> Templates ----> features ----> Add Template ---->NTP
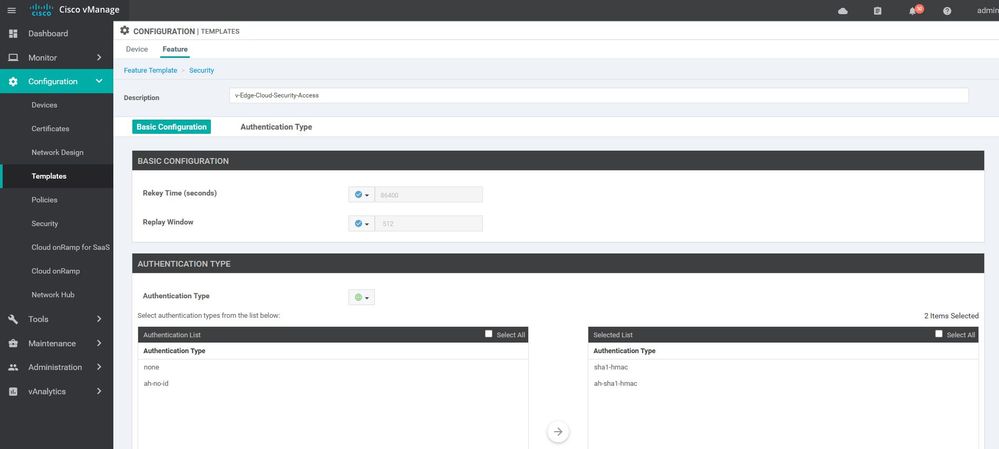
WAN Edge Security
Configuration ----> Templates ----> features ----> Add Template ---->WAN Edge Security
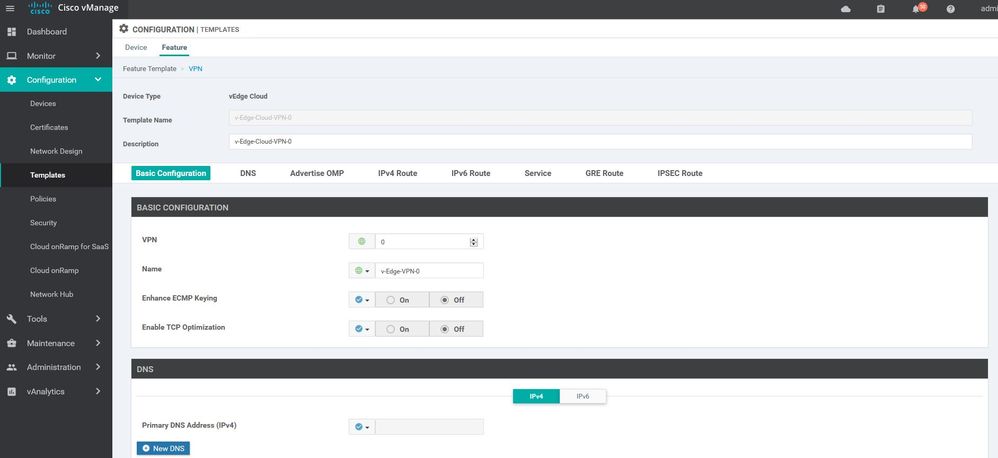
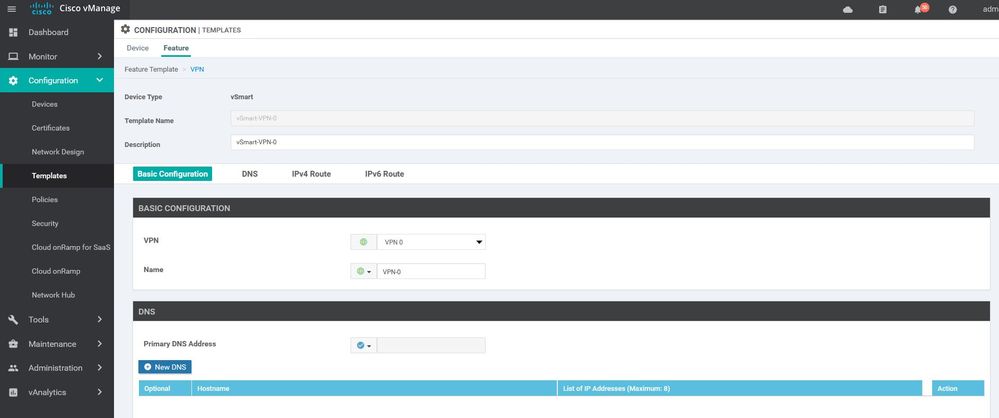
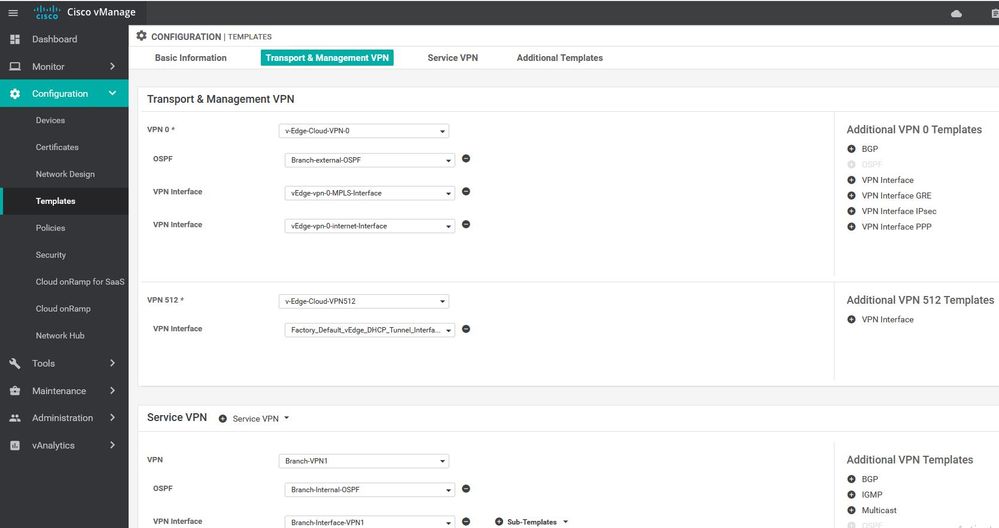
WAN Edge VPN 0
Configuration ----> Templates ----> features ----> Add Template ---->WAN Edge VPN
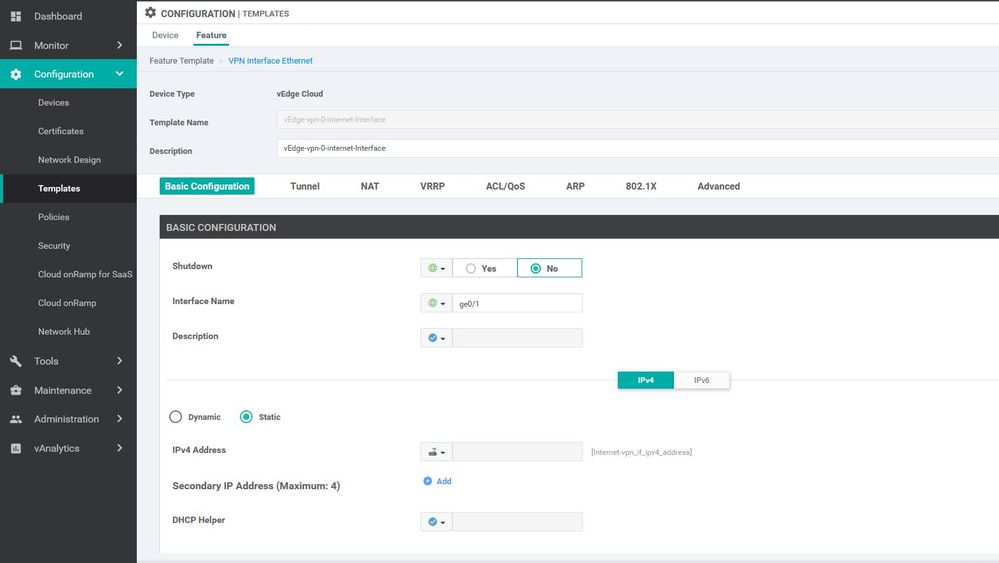
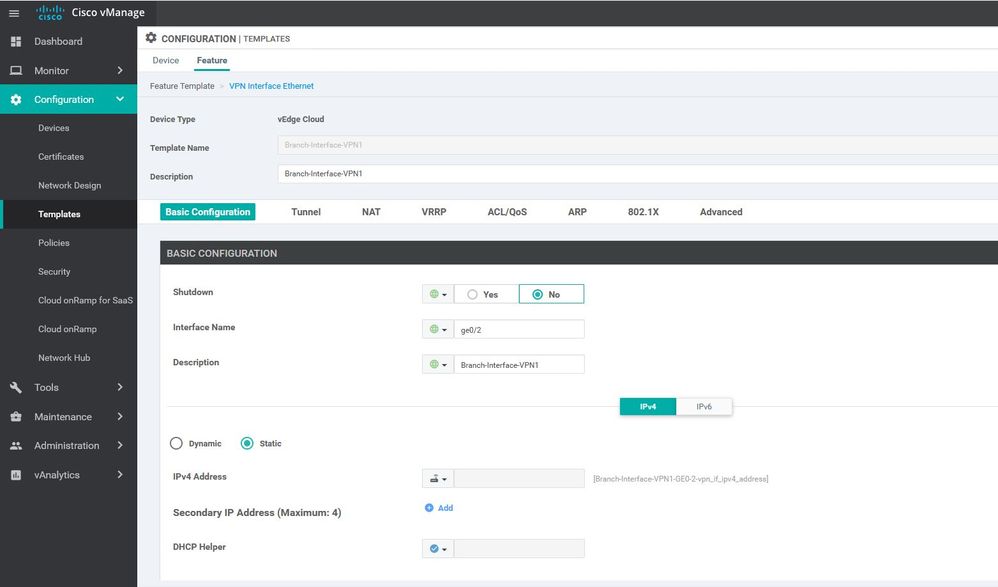
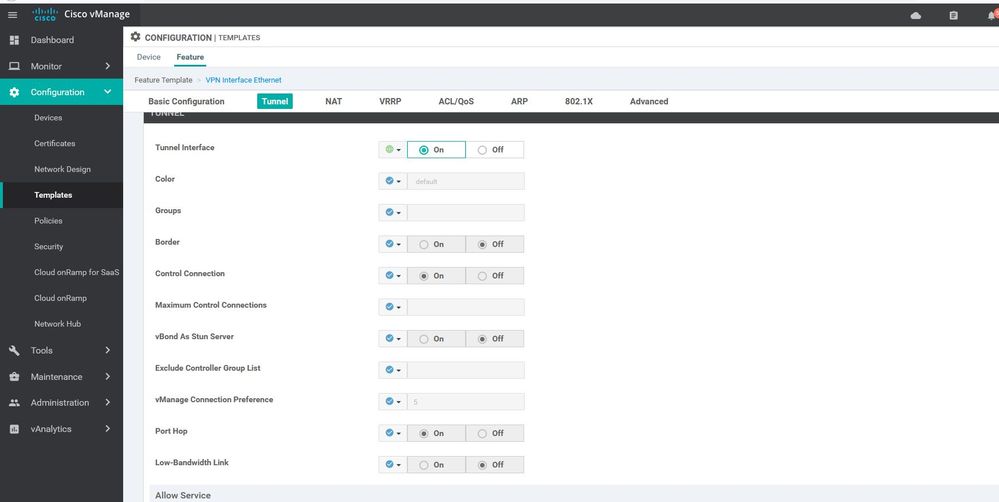
WAN Edge interface VPN 0
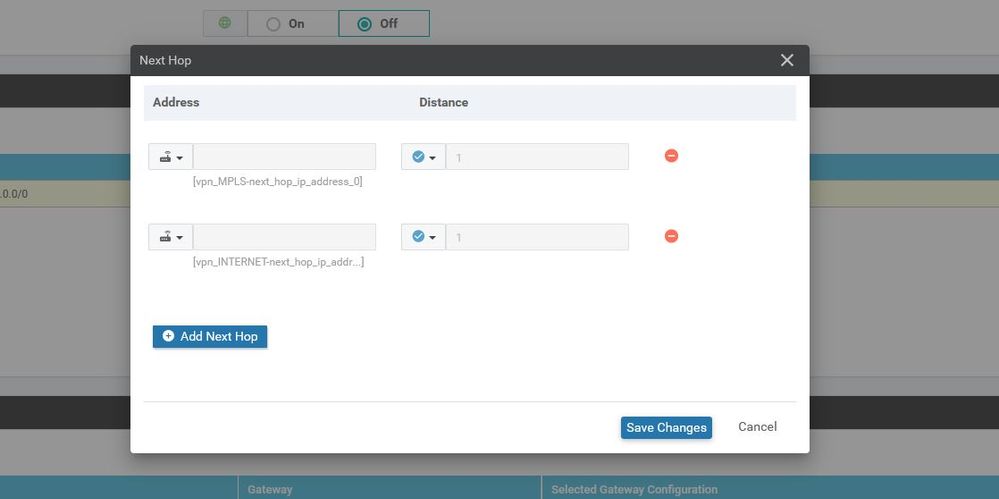
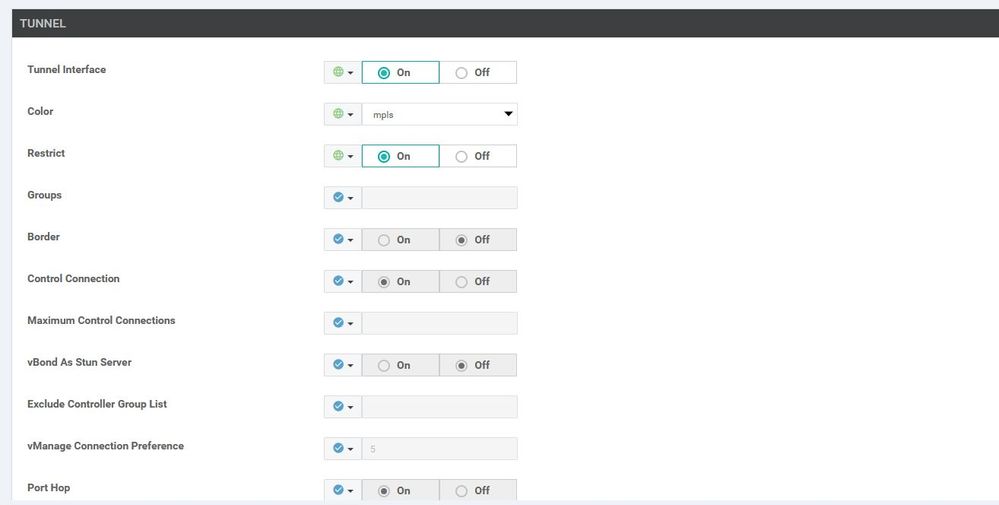
Configuration ----> Templates ----> features ----> Add Template ----> WAN Edge interface VPN 0 - MPLS.
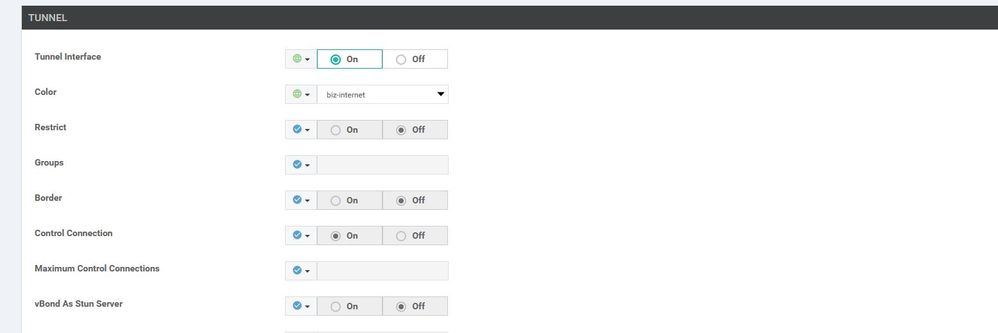
WAN Edge interface VPN 0
Configuration ----> Templates ----> features ----> Add Template ----> WAN Edge interface VPN 0 - Biz-Internet
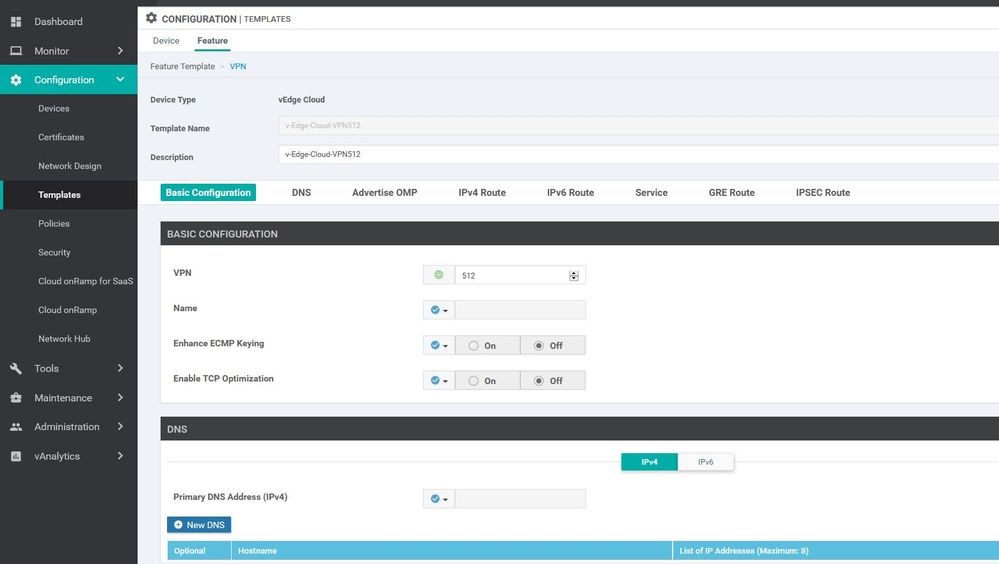
WAN Edge VPN 512
Configuration ----> Templates ----> features ----> Add Template ---->WAN Edge VPN 512
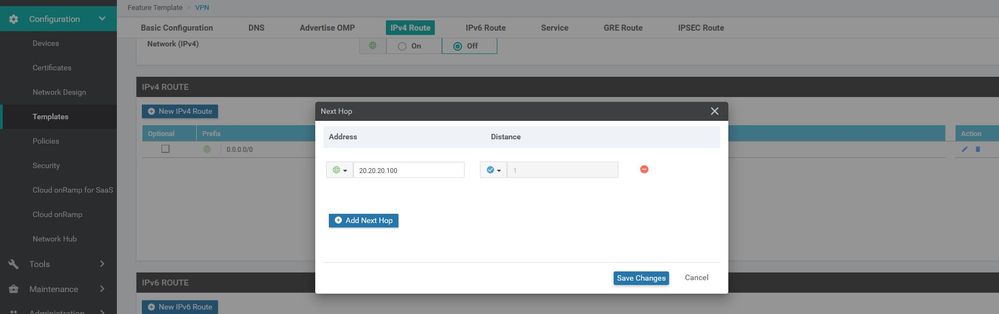
WAN Edge VPN 512
Configuration ----> Templates ----> features ----> Add Template ---->WAN Edge VPN 512
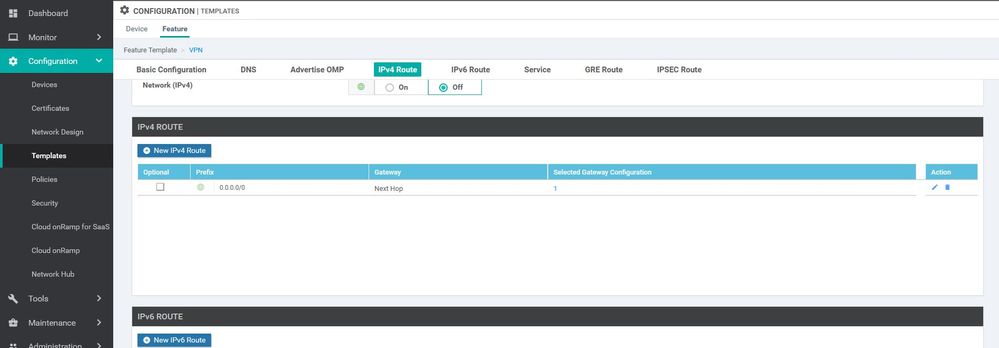
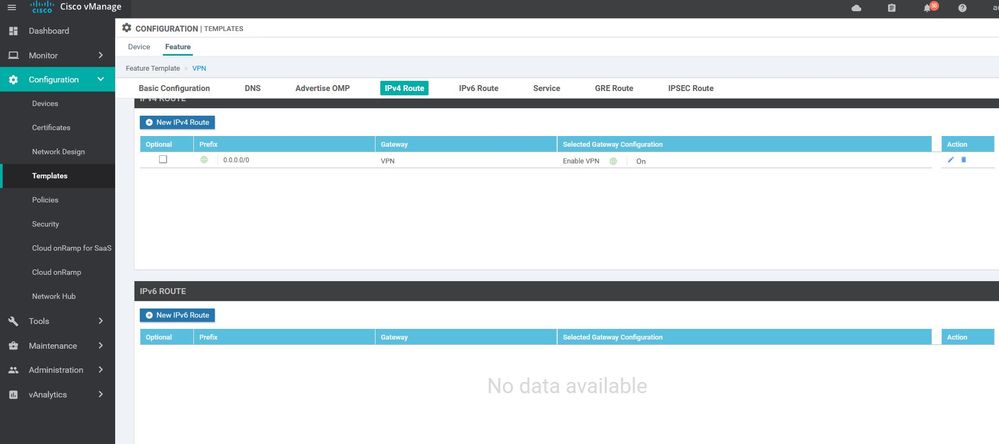
WAN Edge interface VPN 512
Configuration ----> Templates ----> features ----> Add Template ---->WAN Edge interface VPN 512
Banner
Configuration ----> Templates ----> features ----> Add Template ----> Banner
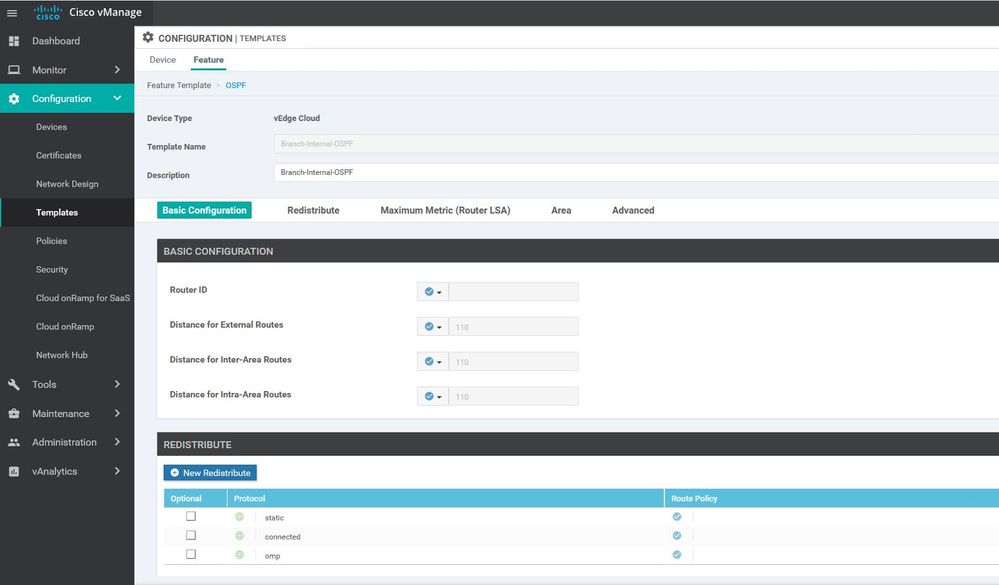
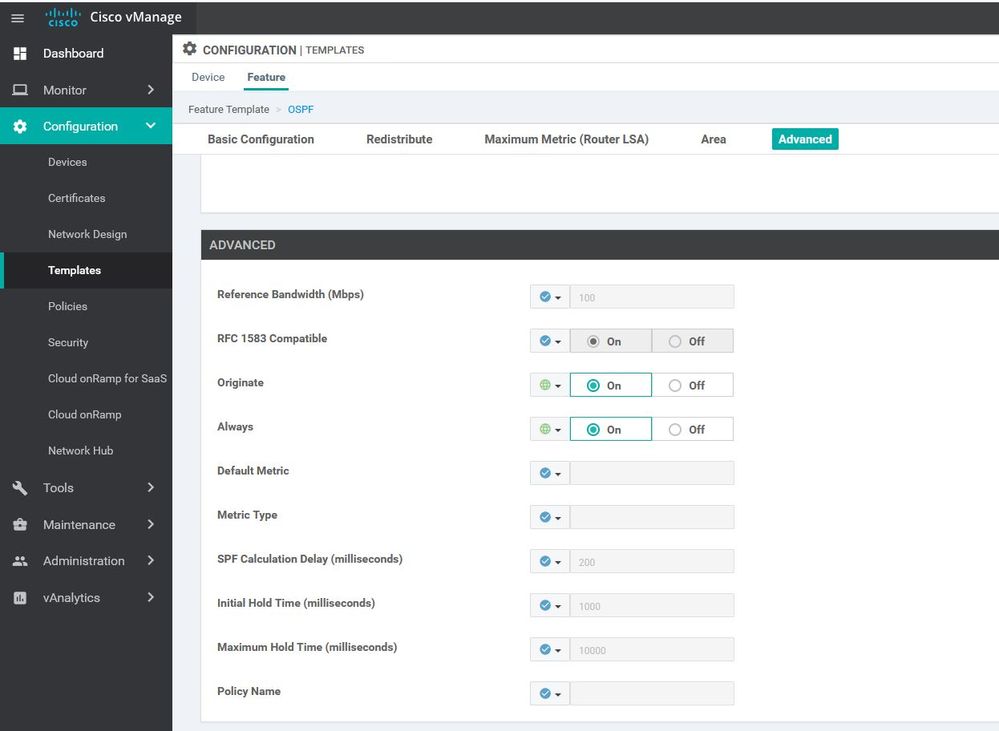
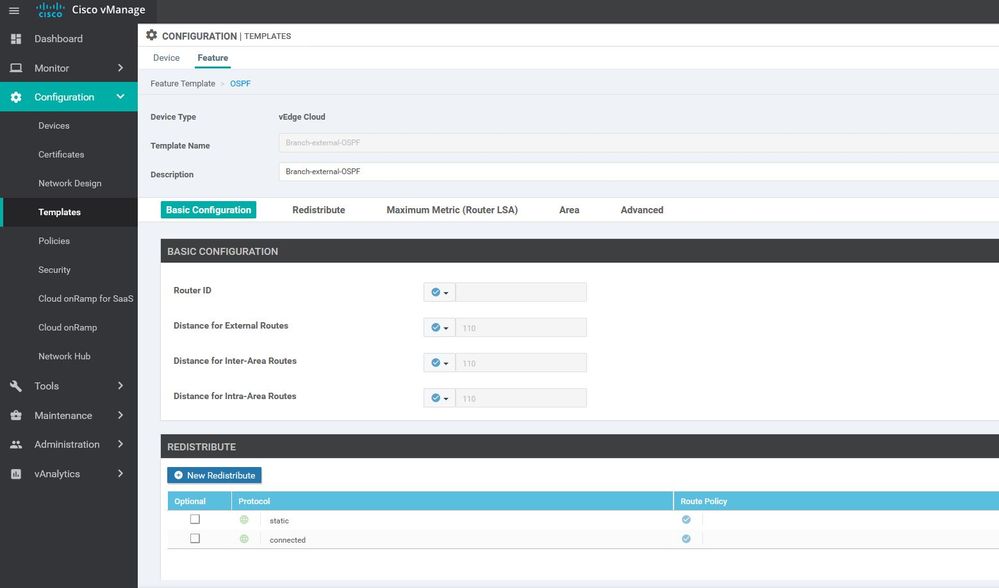

WAN Edge VPN Services 1
Configuration ----> Templates ----> features ----> Add Template ----> VPN1
WAN Edge interface VPN Services 1
Configuration ----> Templates ----> features ----> Add Template ---->WAN Edge interface VPN1
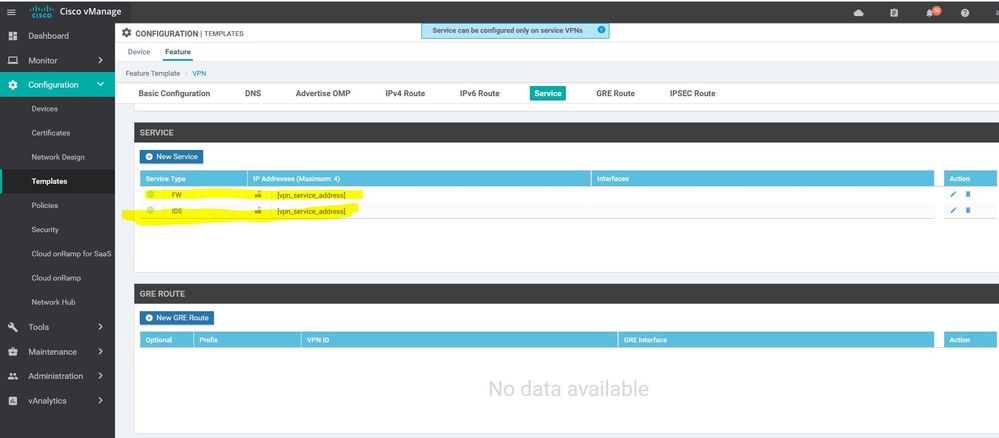
WAN Edge VPN DC-Services 1
Configuration ----> Templates ----> features ----> Add Template ----> DC-VPN1
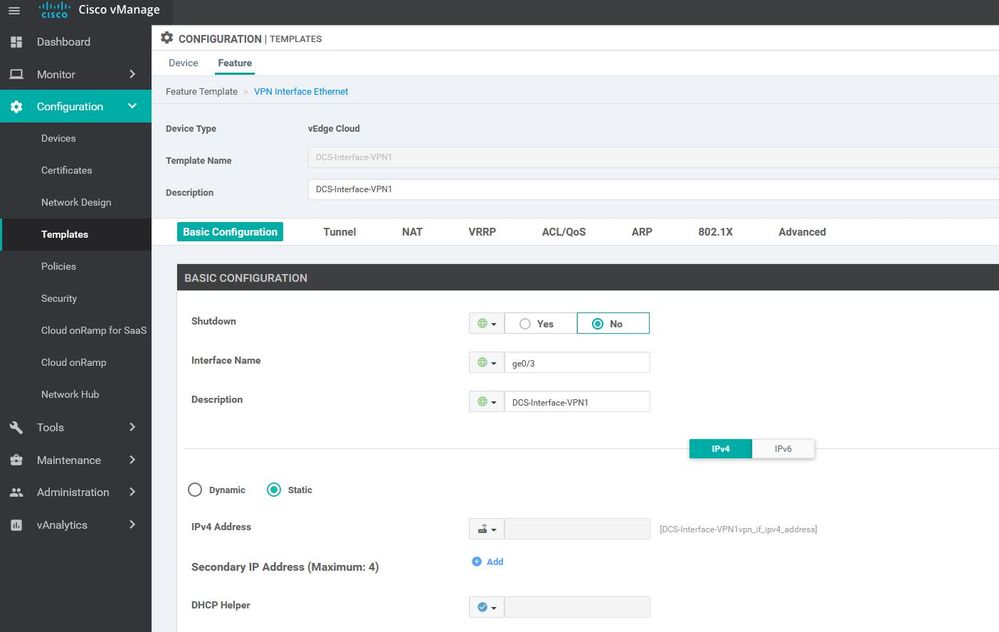
WAN Edge interface VPN DC-Services 1
Configuration ----> Templates ----> features ----> Add Template ----> DC-interface VPN1
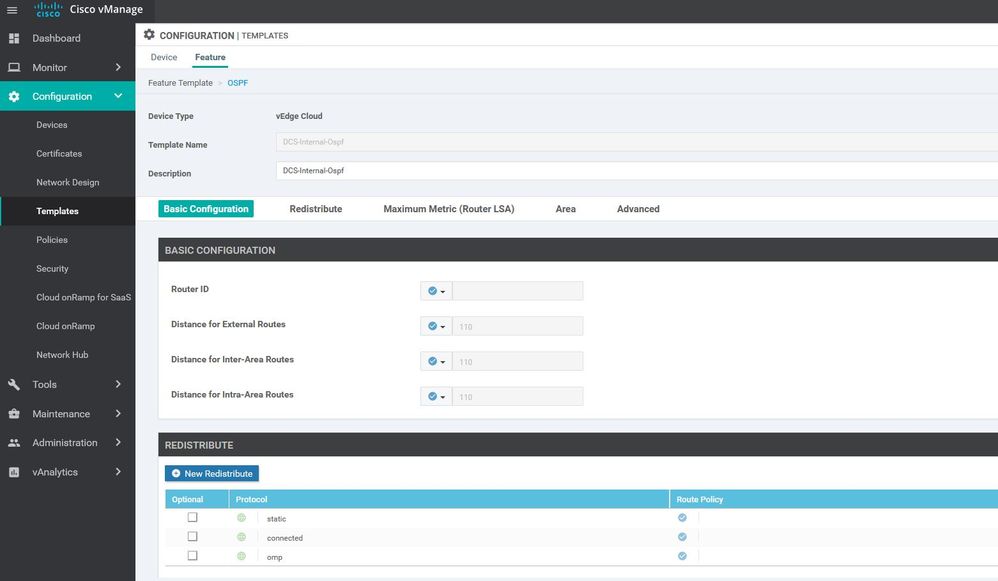
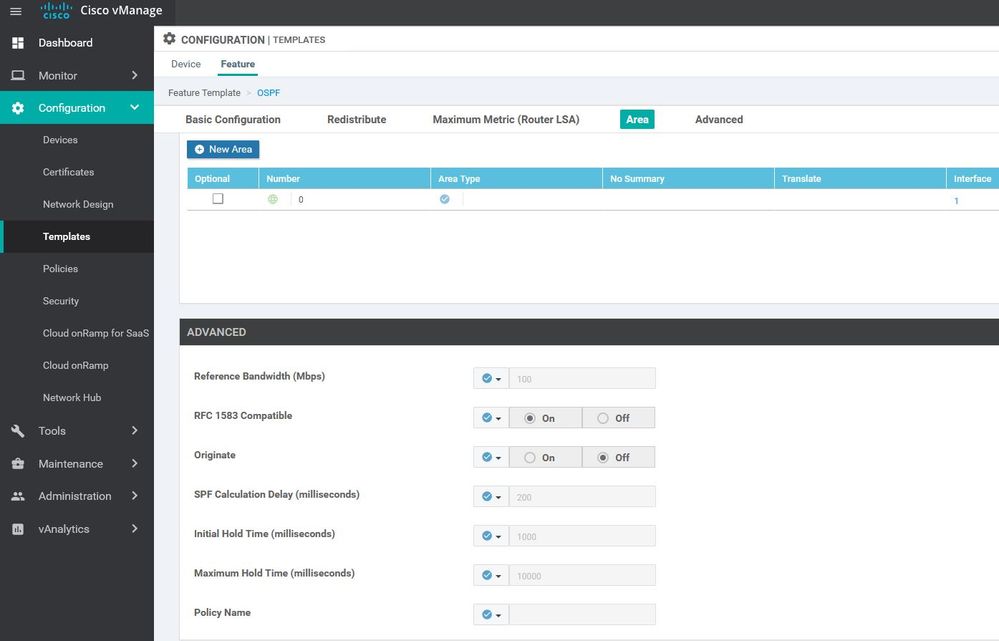
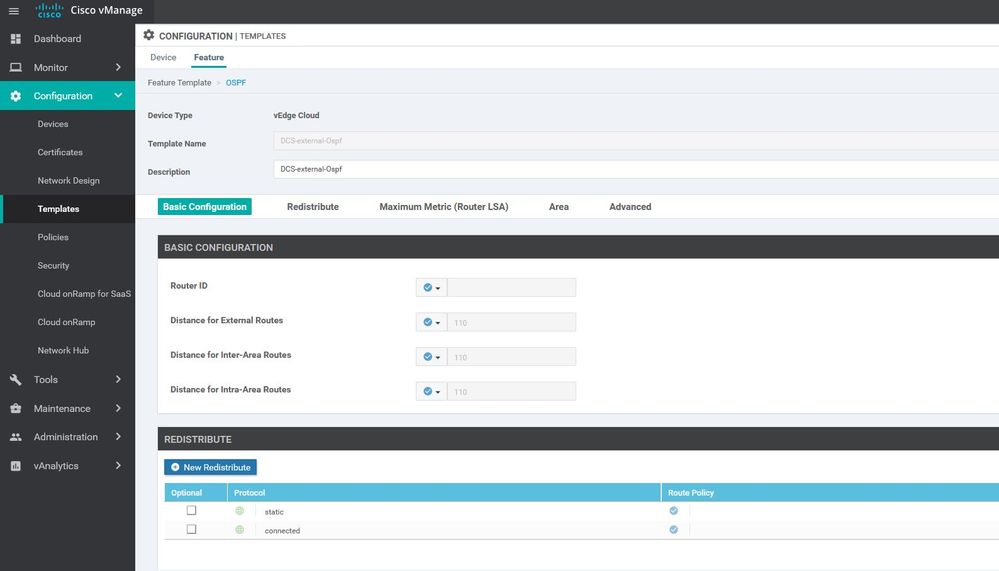
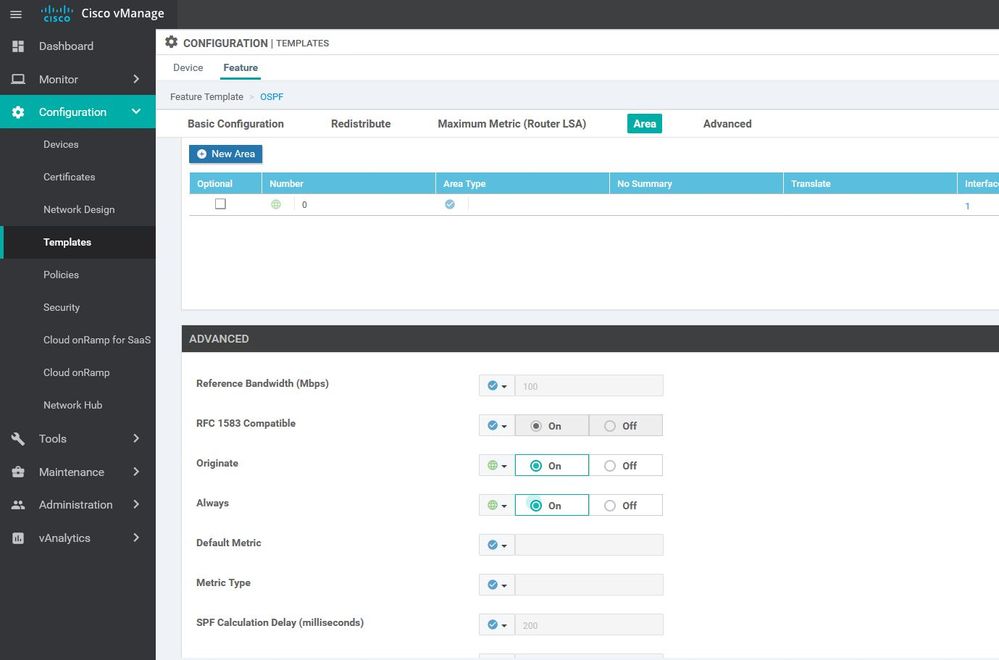
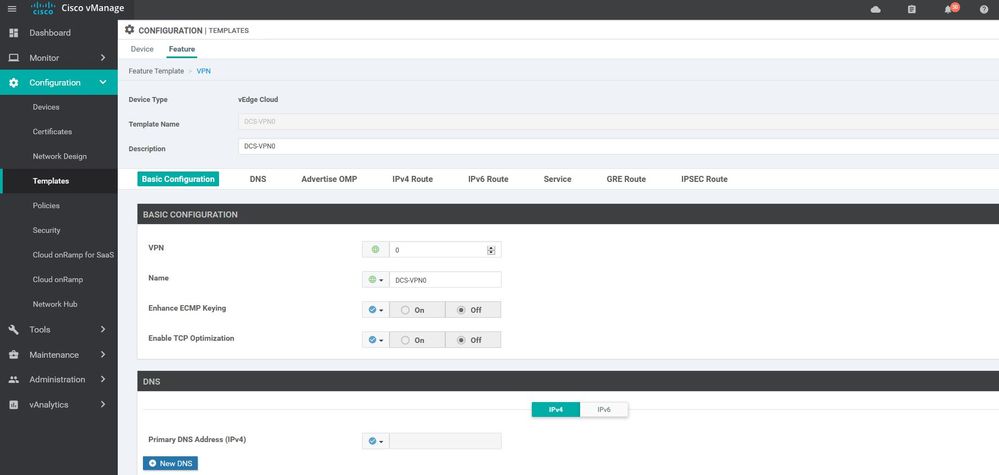
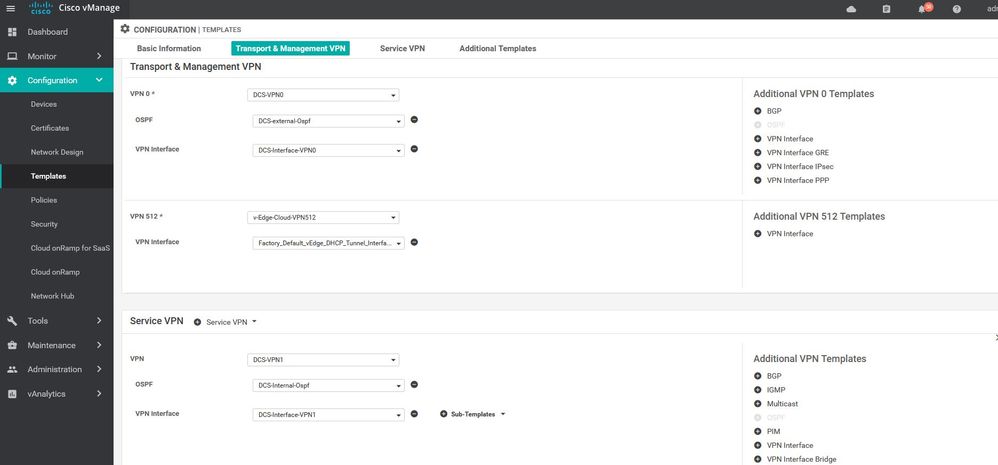
DCS-VPN0
Configuration ----> Templates ----> features ----> Add Template ---->VPN
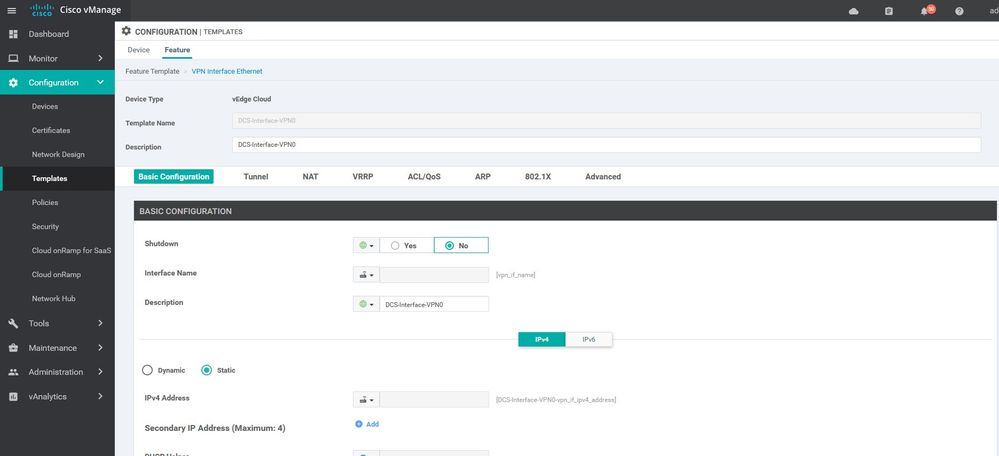
DCS- interface VPN0
Configuration ----> Templates ----> features ----> Add Template ---->wan edge interface
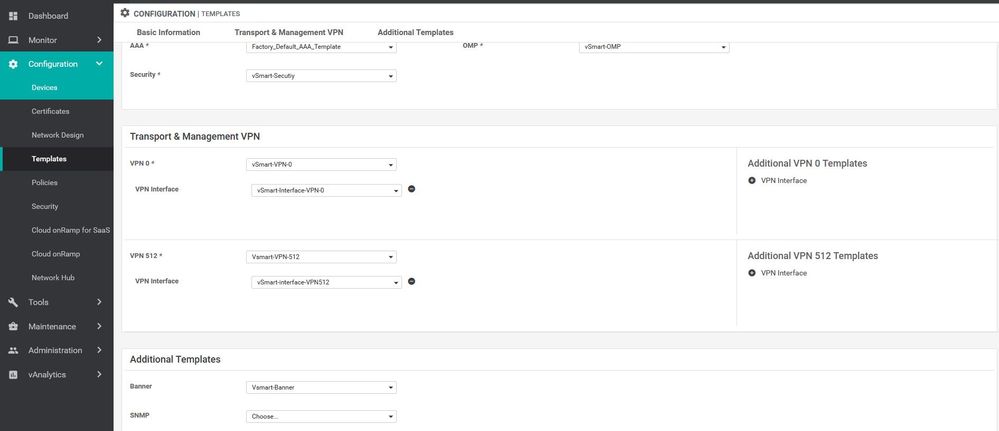
We are going to make Device Templet for the V-smart to move from CLI mode to Vmanage mode so we can push the route & policy to all overlay devices
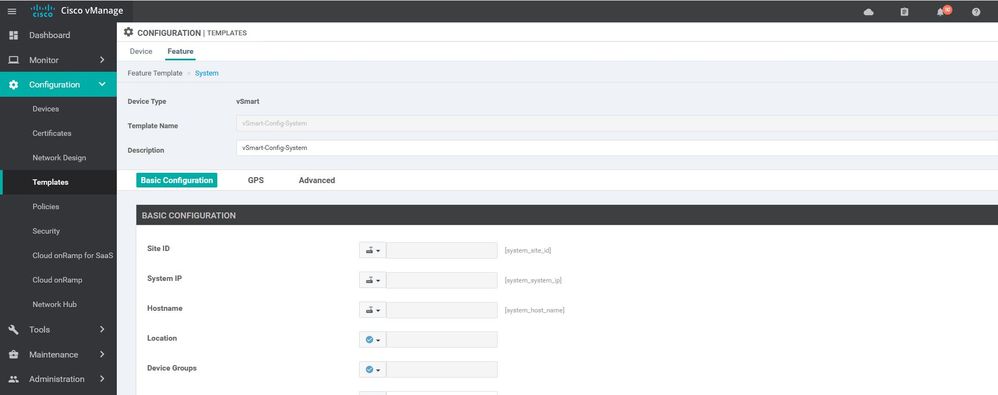
VSmart template
Configuration ----> Templates ----> features ----> Add Template ---->system
NTP template
Configuration ----> Templates ----> features ----> Add Template ----> NTP
Banner template
Configuration ----> Templates ----> features ----> Add Template ----> Banner
Security template
Configuration ----> Templates ----> features ----> Add Template ----> security
VPN 0 template
Configuration ----> Templates ----> features ----> Add Template ----> vpn
Interface VPN 0 template
Configuration ----> Templates ----> features ----> Add Template ----> Vpn interface
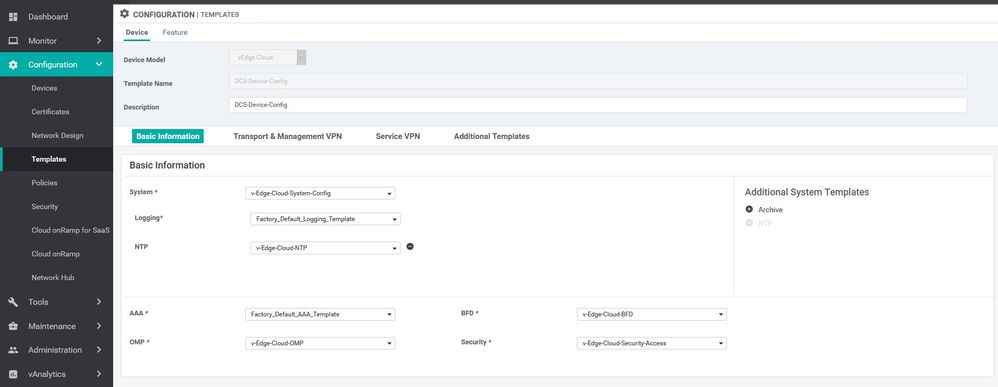
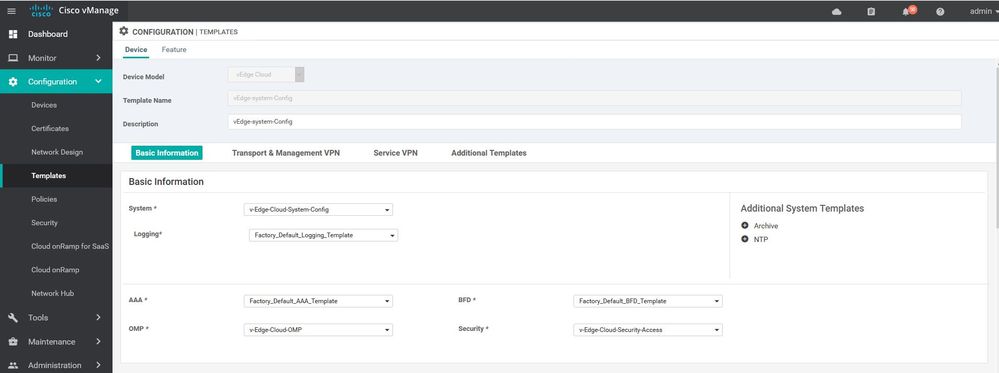
Build the Device Templates for vEdges and V-samrt
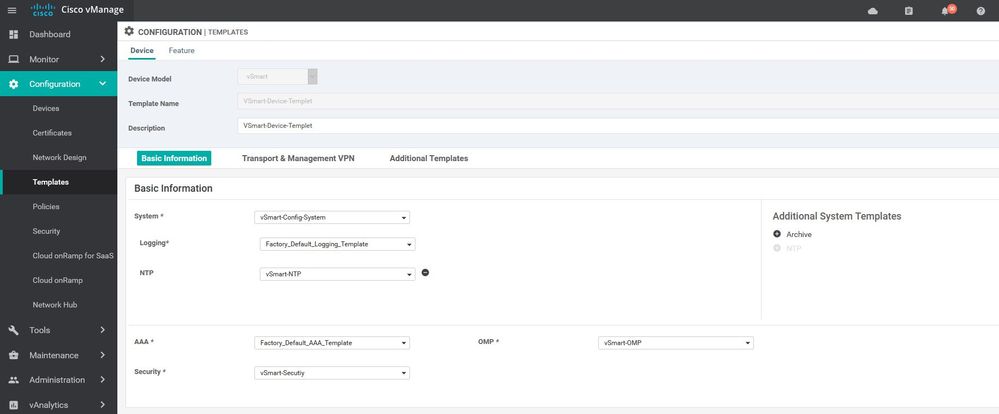
Vsmart Device template
Configuration ----> Templates ----> Device ----> vsmart ----> template name
CLI
viptela-system:system
device-model vsmart
host-name v-Smart
system-ip 10.10.10.102
domain-id 1
site-id 100
admin-tech-on-failure
sp-organization-name "Cisco-ARCH"
organization-name "Cisco-ARCH"
clock timezone America/Los_Angeles
vbond 200.200.200.103 port 12346
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
user admin
password $6$siwKBQ==$wT2lUa9BSreDPI6gB8sl4E6PAJoVXgMbgv/whJ8F1C6sWdRazdxorYYTLrL6syiG6qnLABTnrE96HJiKF6QRq1
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
omp
no shutdown
graceful-restart
!
banner
login "Welcome To SD-Wan Fabric"
motd "Welcome to SD-Wan Fabric Please if you are not authorized to use the system , log out imedietaly"
!
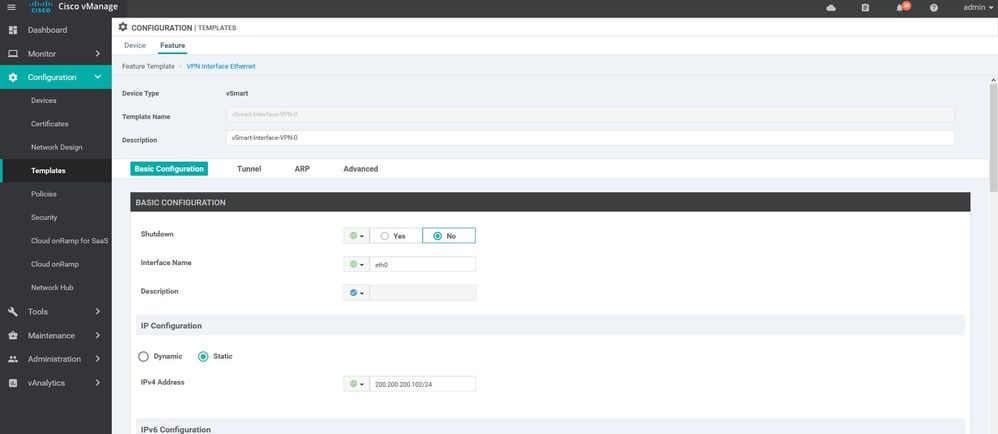
vpn 0
name VPN-0
interface eth0
ip address 200.200.200.102/24
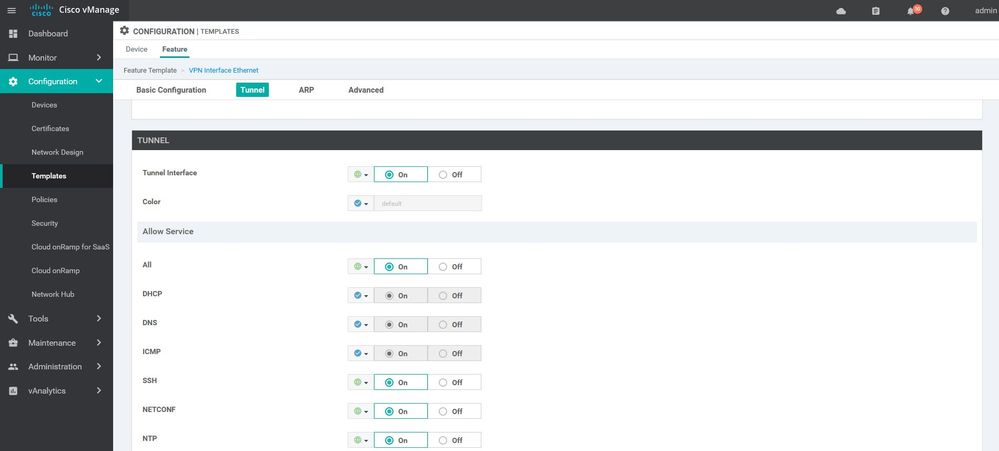
tunnel-interface
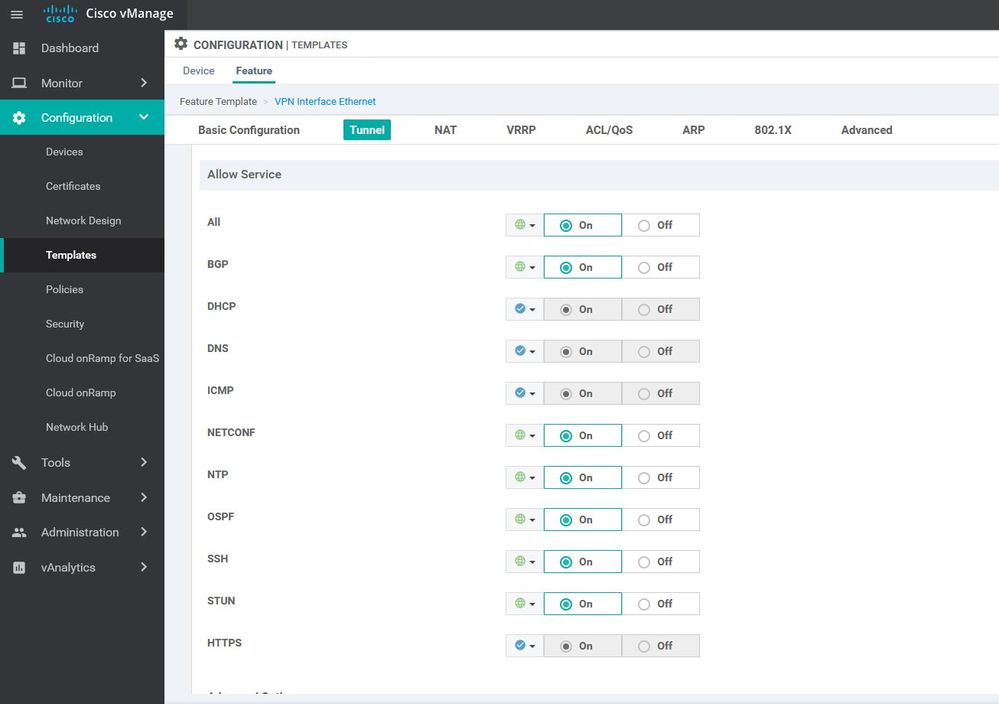
allow-service all
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service stun
!
no shutdown
!
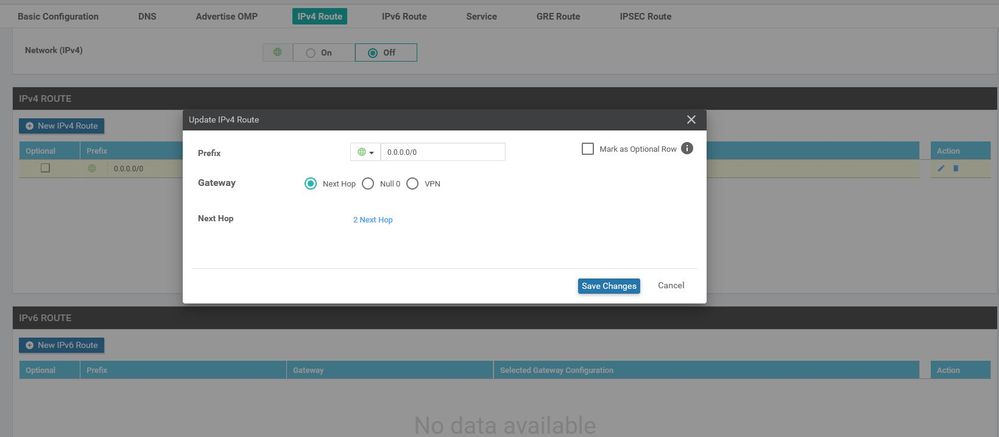
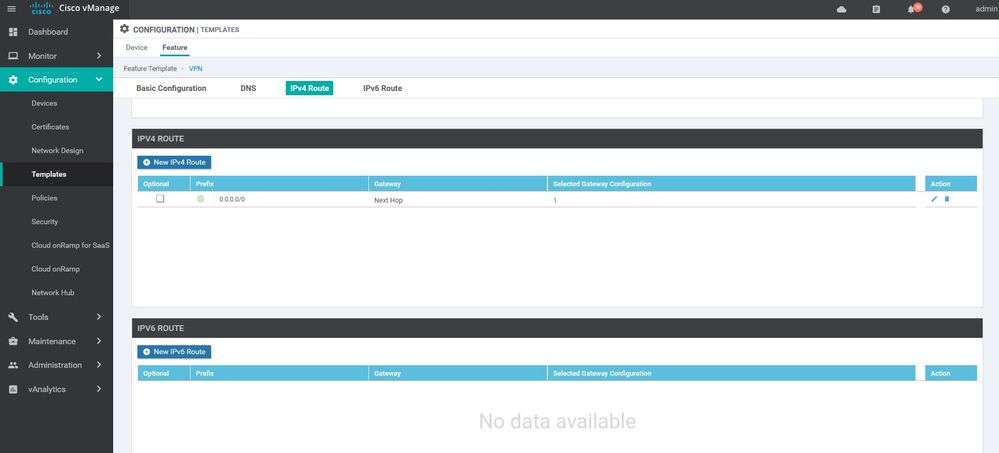
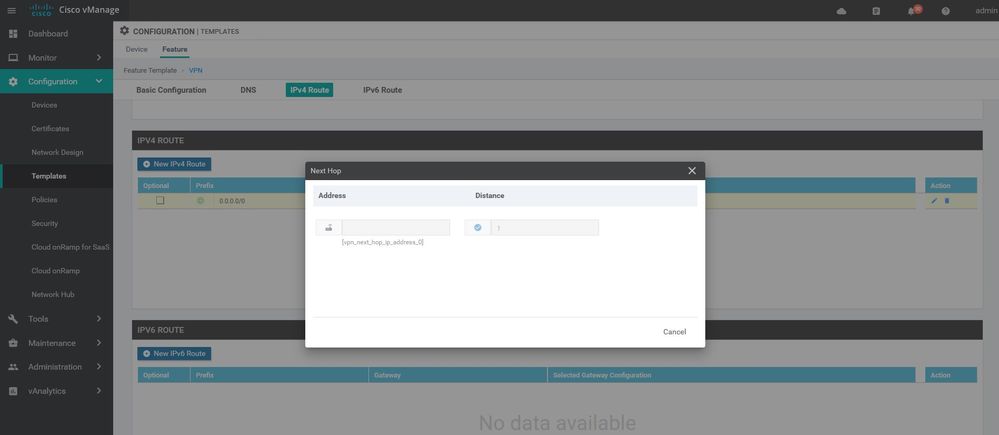
ip route 0.0.0.0/0 200.200.200.100
!
vpn 512
interface eth1
description vSmart-interface-VPN512
ip address 20.20.20.102/24
no shutdown
!
ip route 0.0.0.0/0 20.20.20.100
!
!
!DC vEdges :
CLI
viptela-system:system
device-model vedge-cloud
host-name vedge-DCS
system-ip 10.10.10.211
domain-id 1
site-id 1
admin-tech-on-failure
no route-consistency-check
sp-organization-name "Cisco-ARCH"
organization-name "Cisco-ARCH"
clock timezone America/Los_Angeles
console-baud-rate 9600
vbond 200.200.200.103 port 12346
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
user admin
password $6$siwKBQ==$wT2lUa9BSreDPI6gB8sl4E6PAJoVXgMbgv/whJ8F1C6sWdRazdxorYYTLrL6syiG6qnLABTnrE96HJiKF6QRq1
!
!
logging
disk
enable
!
!
ntp
server 200.200.200.100
version 4
prefer
exit
!
!
bfd app-route multiplier 6
bfd app-route poll-interval 600000
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type sha1-hmac ah-sha1-hmac
!
!
banner
login "Welcome To SD-Wan Fabric"
motd "Welcome to SD-Wan Fabric Please if you are not authorized to use the system , log out imedietaly"
!
vpn 0
name DCS-VPN0
router
ospf
timers spf 200 1000 10000
redistribute static
redistribute connected
area 0
interface ge0/2
exit
exit
!
!
interface ge0/2
description DCS-Interface-VPN0
ip address 211.211.211.2/24
tunnel-interface
encapsulation ipsec
allow-service all
allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
allow-service ntp
allow-service ospf
allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 211.211.211.1
!
vpn 1
name DCS-VPN1
router
ospf
timers spf 200 1000 10000
redistribute static
redistribute connected
redistribute omp
area 0
interface ge0/3
exit
exit
!
!
interface ge0/3
description DCS-Interface-VPN1
ip address 80.80.80.1/24
no shutdown
!
ip route 0.0.0.0/0 80.80.80.2
omp
advertise bgp
advertise ospf external
advertise connected
advertise static
!
!
vpn 512
interface eth1
ip dhcp-client
no shutdown
!
ip route 0.0.0.0/0 20.20.20.100
!
!
!
Stay tuned for part ||| , Press Star if it's helpful for your knowledge !
***** I hope that has been informative for you and thank you *****
Mohamed Alhenawy
CCIE#60453
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks Mohamed.
Can you share files eve-ng please?
Regards
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @borrexlinux
Yes sure , check you DM
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Mohamed.
Great Work ! If you don't mind please share the eve-ng files for LAB 1 & 2. Thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @hadeekeeth
Thanks for your kind keywords , no worries Please share your private mail through DM .
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great Post, I am working my way through lab 1 and 2.
Took me a min to figure out you we using static routing for the "internet"
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Joshb1,
Thanks for your kind keywords , as I understand form you question , you asking about the static route for the internet ?
Here you go , For the know network ( Viptela Controllers ) using static route to route all traffic to DC edge , for unknown network (0.0.0.0) route all the traffic to external interface.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Mohamed very informative lab and nots if possible can I get these Sdwan file notes on email please so I do study please
pawansharma0761@gmail.com
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
NEW POST !!!!
Stay Tune for all the series , Coming Sooon
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi.
I am working on a test environment, only with virtual devices, however when I try to populate the WAN edge device list from CSV file it says that "Error: Virtual Platform is not allowed in CSV Upload."
Is there any other way to do IT? I am planning to have a fully isolated environment in my lab.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes we can solve it check out you private message
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hello @Mohamed Alhenawy great lab, with clear explanation please can you share the lab file
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Helllo @soufiansaheb
thanks for your feedback, yes sure please share your mail through PM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: