- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- SD-WAN Security - Deployment Guide
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-07-2019 07:40 AM - edited 01-10-2023 12:29 PM
- Documentation
- Prerequisites and disclaimers
- Download Software images
- Configuring Security Template
- Application Firewall Policy
- Intrusion Prevention
- URL-Filtering
- Advanced Malware Protection (AMP/TG)
- DNS/web-layer Security
- Policy Summary
- Attach the security policy to the device template
- Overall Dashboard
- Enterprise Firewall
- IPS
- URL Filtering
- Advanced Malware Protection (AMP/TG)
- Device-Specific Dashboard
- Real Time Data
- Further reading
Contributed by Kureli Sankar and Rudresh Veerappaji
Documentation
This configuration example is meant to be interpreted with the aid of the official documentation from the configuration guide located here:
- https://www.cisco.com/c/en/us/td/docs/routers/sdwan/configuration/Security/Security-Book/security-solution.html (Latest 16.12/19.2)
- https://sdwan-docs.cisco.com/Product_Documentation/Software_Features/Release_18.4/05Security/Configuring_the_18.4_Security_Virtual_Image_for_IPS%2F%2FIDS_and_URL_Filtering
Prerequisites and disclaimers
- This deployment guide assumes that the controllers and the edges have been successfully deployed and are operational.
- For firewall ports that need to be open for device on-boarding please refer this link: https://sdwan-docs.cisco.com/Product_Documentation/Getting_Started/Viptela_Overlay_Network_Bringup/01Bringup_Sequence_of_Events/Firewall_Ports_for_Viptela_Deployments
-
Upload the image for virtual service if you intent to test IPS/IPS and/or URL-F
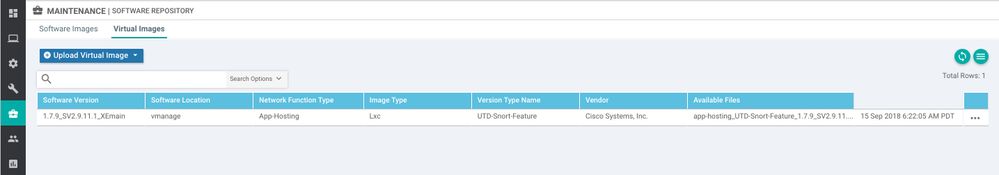
Click Maintenance >> Software Repository then choose the "Virtual Images" tab and upload the App Hosting tar file to the software repository.
- Security policy does not support CLI device template. Please attach security policy only to feature device template.
- ISR platforms need to have minimum 8 GB DRAM and 8 GB of FLASH if IPS/URL-F functions are required.
- If configuring DNS/web-layer Security, log into your Umbrella Portal and copy the API token so we can configure the DNS security section on vManage.
Under Deployments >> Network Devices >> Choose the API token on the far right corner and copy the long string of numbers to clip board.
This token needs to be populated (pasted from clip board) under the vManage settings like shown below under "Umbrella API Token":
Download Software images
Release Notes for both 16.11.1 and 19.2:
Release Notes for both 16.11.1 and 19.1:
Release Notes for 16.10.1 and 18.4:
16.10.1 Software Download Link for ISR 1K/4K and ASR:
ISR 1K: https://software.cisco.com/download/home/286321996/type/286321980/release/16.10.1
ISR 4K: https://software.cisco.com/download/home/286321991/type/286321980/release/16.10.1
ASR1K: https://software.cisco.com/download/home/286321999/type/286321980/release/16.10.1
18.4 vManage New Deployment Download Link:
https://software.cisco.com/download/home/286320995/type/286321039/release/18.4.0
18.4 vManage upgrade image download Link:
https://software.cisco.com/download/home/286320995/type/286321394/release/18.4.0
19.2 vManage New Deployment Download Link:
https://software.cisco.com/download/home/286320995/type/286321039/release/19.2.0
19.2 vManage upgrade image download Link:
https://software.cisco.com/download/home/286320995/type/286321394/release/19.2.0
Configuring Security Template
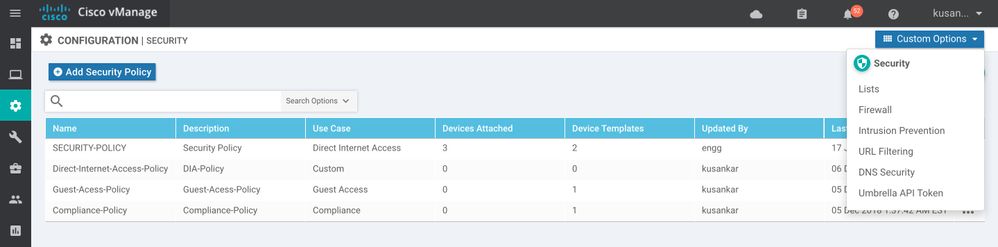
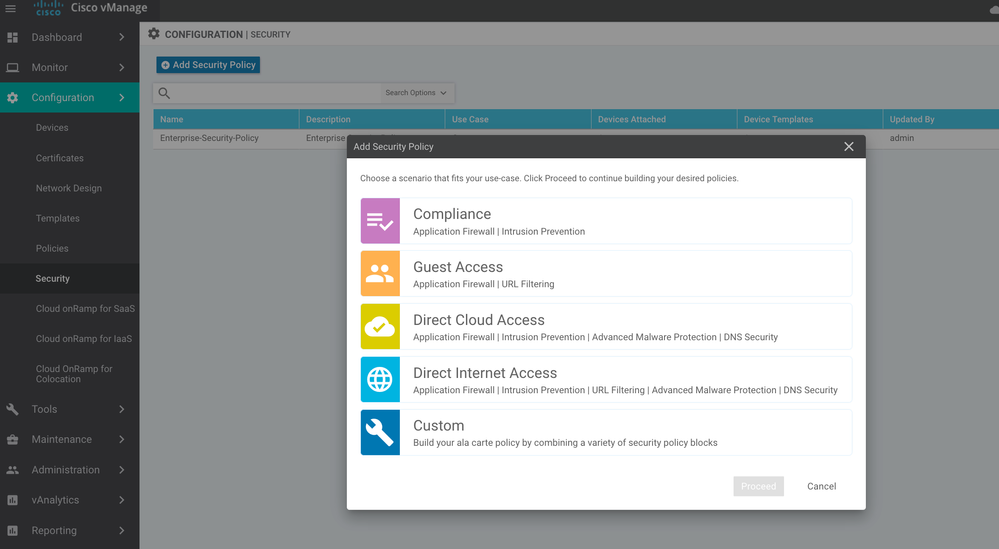
Click under Configuration >> Security and click "Add Security Policy" and pick one of the features that you like to implement or if you need more than one choose the "custom" option and proceed.
Application Firewall Policy
Click on "Add Firewall Policy" choose "Create New" and proceed.
Give the policy a name and description as shown below and start creating sequence rule. If you need to configure permission for DIA (Direct Internet Access) for example only allow http, https, dns follow the screen shots for below:
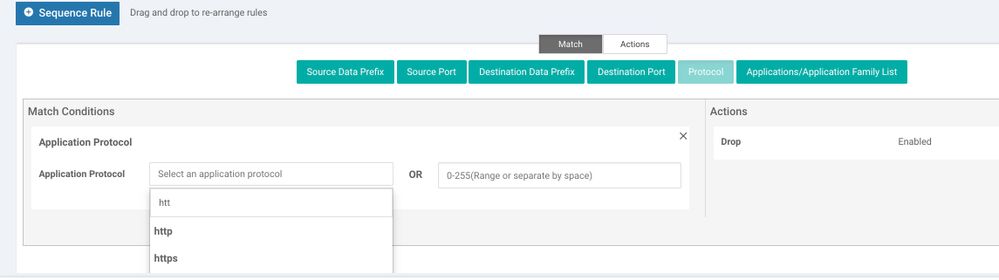
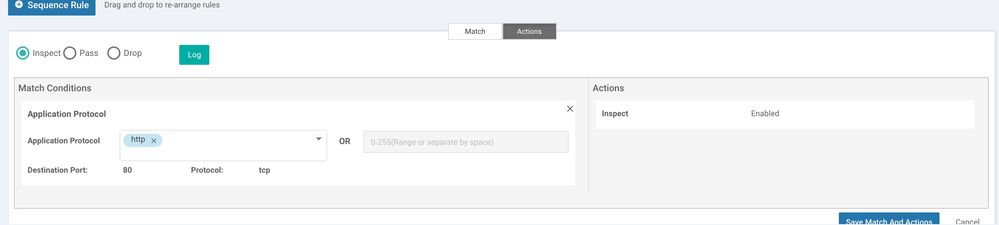
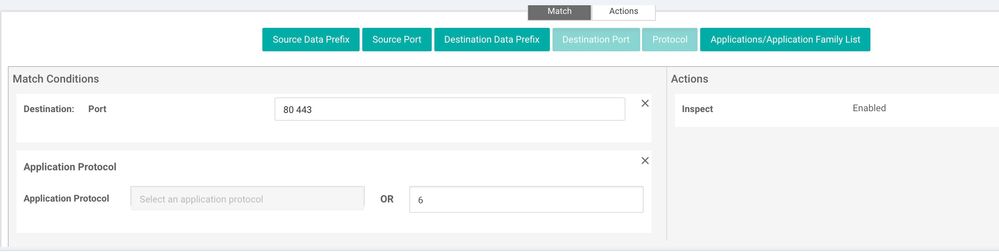
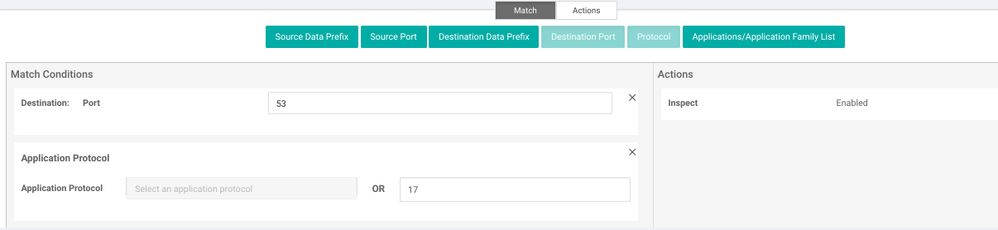
Intrusion Prevention
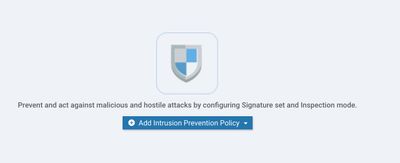
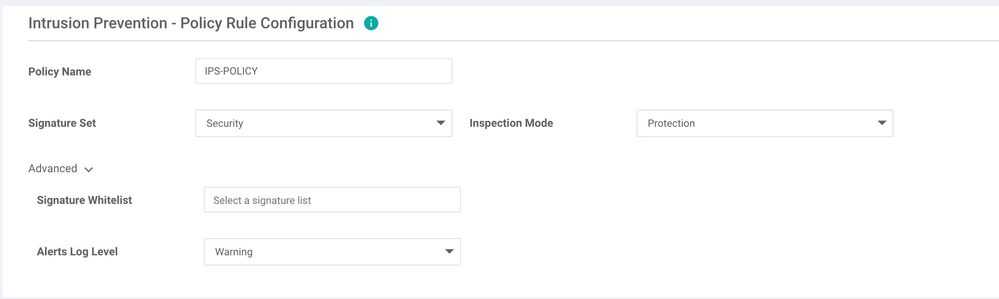
Moving on to IPS, click on "Add Intrusion Prevention policy".
Give the policy a name and proceed with choosing a Signature Set, Inspection Mode.
Optionally one could under configure a Signature Whitelist by importing or creating a new file on the local computer and set the "Alerts Log Level".
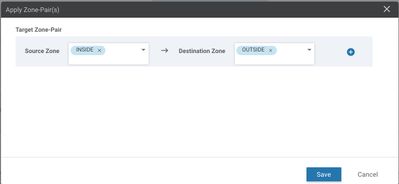
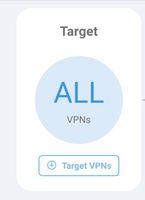
Once done make sure to apply the policy to all or only selected Target VPNs.
IPS signature update
On the vManage screen, click on "Administration" and go to "Settings" and "IPS signature Update" and provide CCO credentials (could be any CCO account or the companies CCO account) for vManage to download the subscription signature set and update the WAN edges.
Router#sh utd engine standard status
Engine version : 1.0.8_SV2.9.13.0_XE16.12
Profile : Cloud-Low
System memory :
Usage : 22.00 %
Status : Green
Number of engines : 1
Engine Running Health Reason
===========================================
Engine(#1): Yes Green None
=======================================================
Overall system status: Green
Signature update status:
=========================
Current signature package version: 29130.51.s =========> .s indicates subscription
Last update status: Successful
Last successful update time: Wed Dec 11 19:53:19 2019 UTC
Last failed update time: None
Last failed update reason: None
Next update scheduled at: None
Current status: Idle
URL-Filtering
Prerequisite:
For this feature to work we need NAT configured for the WAN interface. The security App Hosting container uses the virtual port group 0 to reach out to the internet and talk to Webroot/Brightcloud in order to download the URL-Filtering database if the device has 16 MB of DRAM or do a cloud lookup for the URLs to get the category information if the device only has 8 GB of DRAM. Either way the WAN interface needs to be NAT enabled (even if an upstream device provides NAT for this WAN edge router). This is because the virtual port group uses the subnet 192.168.1.0/30 subnet and if you do not PAT this to the WAN interface, you need to provide routes on the upstream device for response packets to get back to this WAN edge router for 192.168.1.0/30 network.
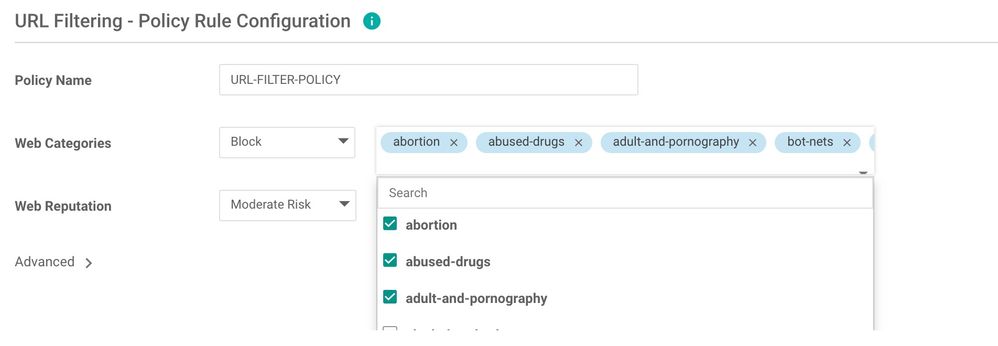
Click "Add URL Filtering Policy" and choose "create new". Give it a policy name and proceed with choosing the categories using the down arrow.
- Choose whether to block or allow (with block, all categories are allowed but those blocked and vise versa)
- Choose the categories from the search option
- Choose the Web Reputation
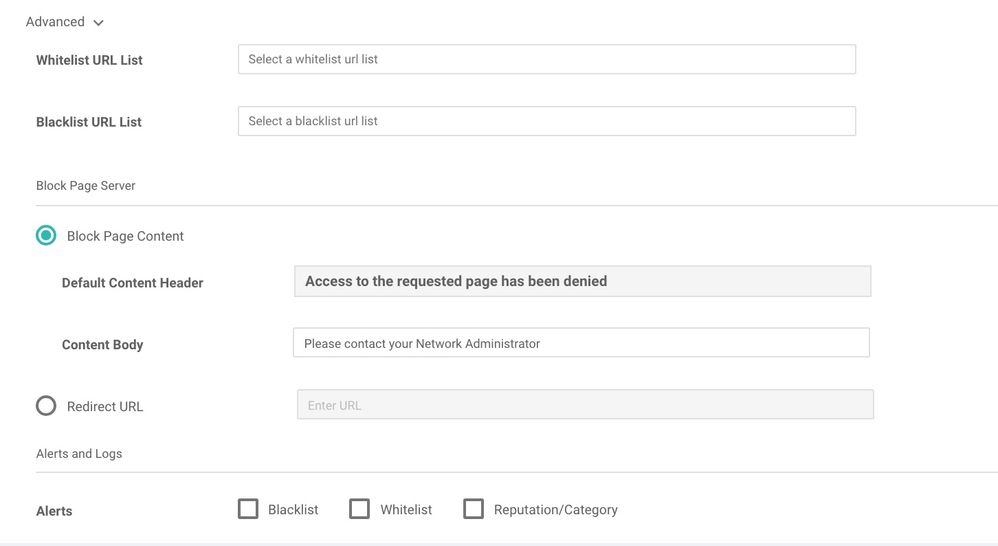
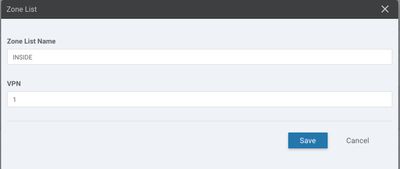
Under Advanced choose create a new URL list for White or Black List. Eg. whitelisted URLs bypass all URL filtering policy. Blacklisted URL's are immediately dropped without further processing the URL filtering policy. Under the Block Page Content the "Default Content Header" cannot be changed (we will hide/remove this from the UI for FCS). Under "Content Body" you can type a message or add the help desk number that the users could call if needed.
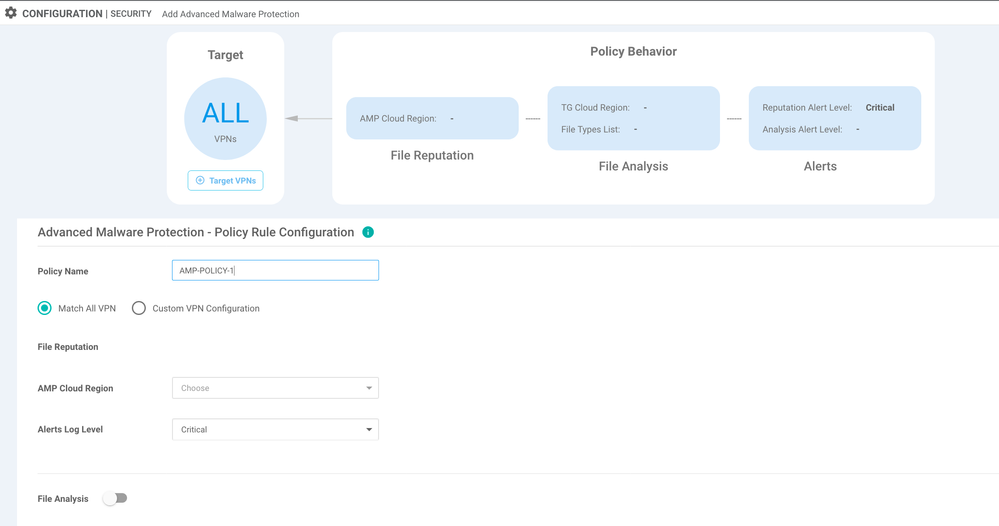
Advanced Malware Protection (AMP/TG)
Click next from the previous screen, and configure AMP/TG feature from "Add Advanced Malware Protection Policy" and choose "Create New". Give it a policy name and proceed. Choose an AMP Cloud region that is closest to your device location, and set Alerts log level from the options available.
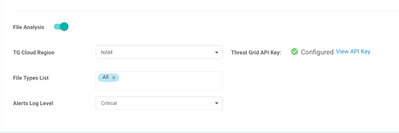
Toggle the "File Analysis" option at the bottom of the screen to enable Threat Grid (TG) feature. Enter the Threat Grid API key under "Custom Options"->"Threat Grid API Key"
From here you can select the closet Threat grid cloud region to your device location, and also select the file types that you would like to send to TG for sandboxing and analysis.
DNS/web-layer Security
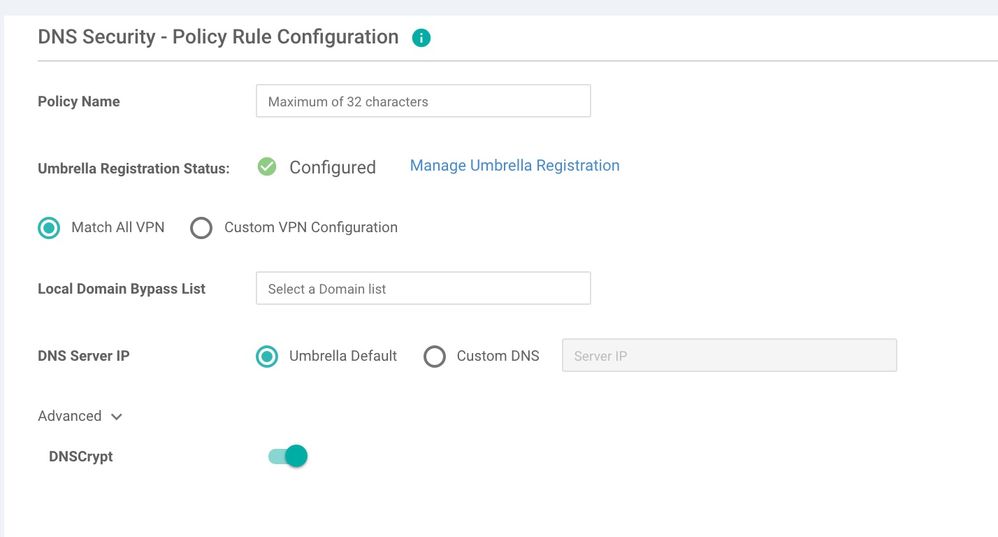
Start configuring DNS/web-layer security feature "Add DNS security Policy" and choose "create new" give it a policy name and proceed.
Since we have already keyed in the Umbrella Token ID under settings, Umbrella Registration Status shows "green" configured.
Now create an optional domain bypass list for DNS requests (for internal company only websites) that do not need to be re-directed to Umbrella. DNScrypt is enabled by default which will encrypt the DNS packets with the EDNS headers of client IP etc. and be sent to the umbrella cloud.
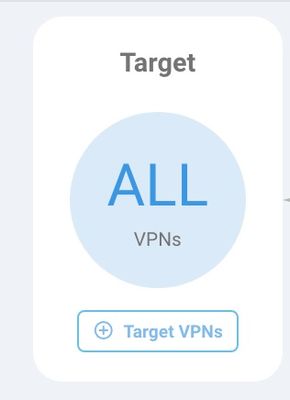
Make sure to apply the policy to all or only selected target VPNs.
Make sure to apply the policy to all or only selected VPNs. Then, go next and review the policy summary page
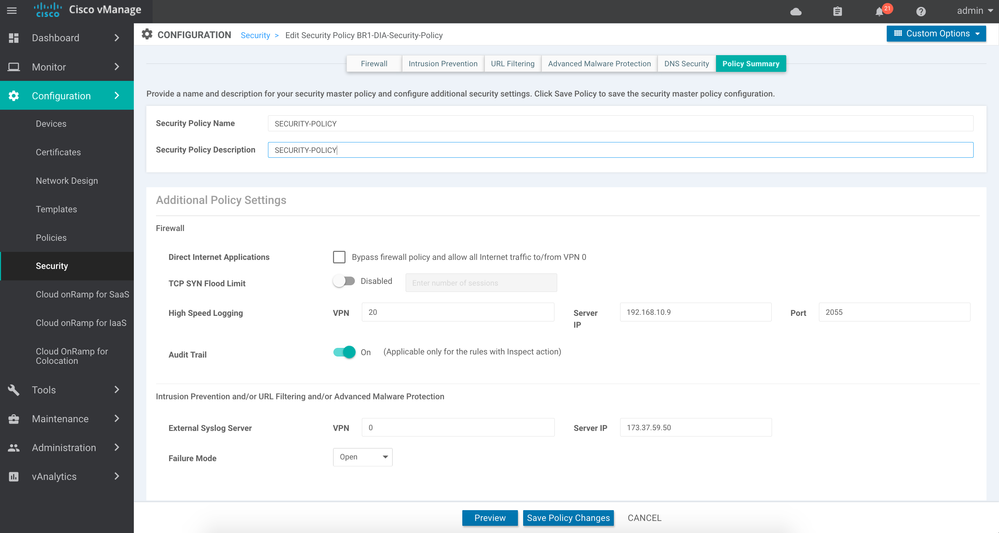
Policy Summary
Make sure to uncheck the box that says 'Allow Internet Traffic to VPN 0 if VPN 0 is not in a zone'. Checking this will allow all traffic without being inspected by the firewall. You can enable High Speed logging to send all Enterprise firewall logs in the form of Netflow v9 records to a Netflow Collector. Also you can enable External Syslog server for UTD services namely IPS, URL Filtering and AMP/TG in the policy summary page. Save the policy.
Attach the security policy to the device template
Before attaching the security policy to the device template, since the IPS and URL-F features are container based, we need to upload the image for App Hosting. If you haven't done this already, now is the time to do this.
Click Maintenance >> Software Repository then choose the "Virtual Images" tab and upload the App Hosting tar file to the repository.
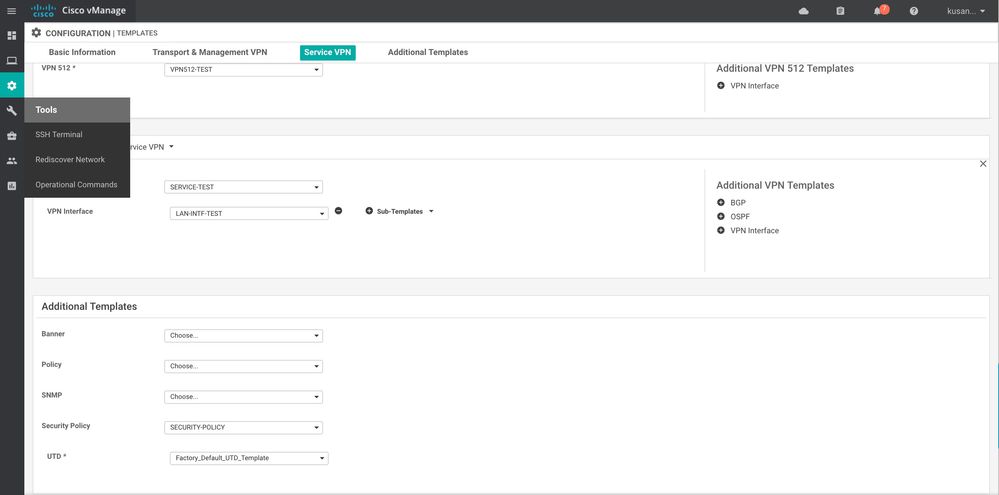
Next, go to the Configuration >> Templates choose the template that is attached to the device then click on the far left ... and choose edit. Now, scroll all the way down choose the security policy that we just configured and also choose the UTD "Factory Default_UTD_Template" if you are deploying IPS or URL-F.
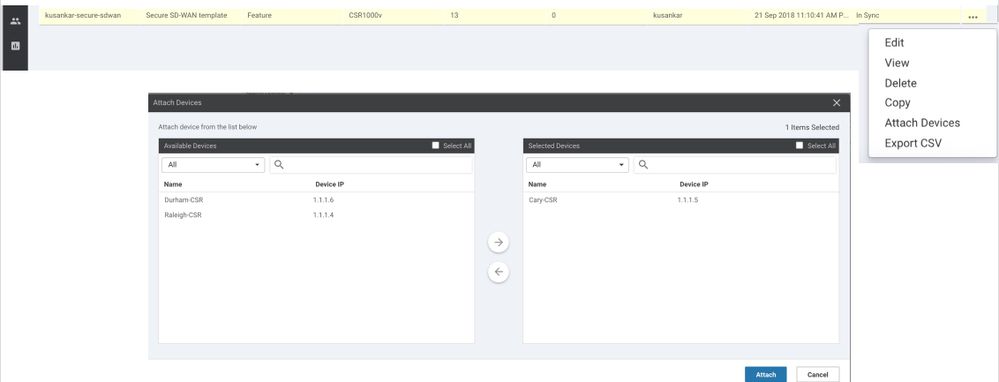
Now, attach the device(s) to the template as shown below.
This process takes a few minutes (up to 10 minutes) so, please be patient and watch the progress by clicking on the "Tasks".
Overall Dashboard
Go to "Dashboard" -> "Security" for the Security specific Global/Overall Dashboard
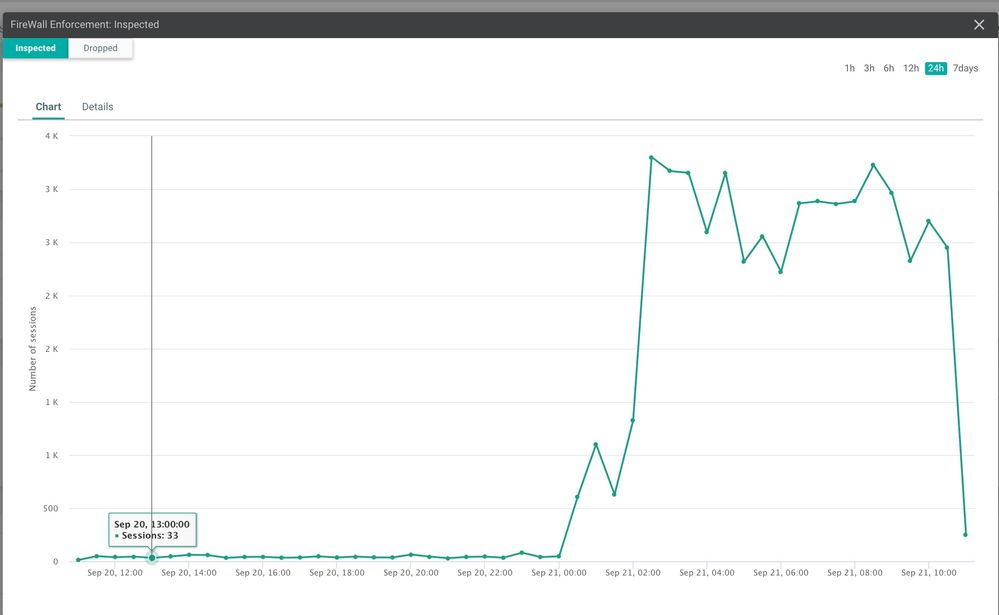
Enterprise Firewall
Toggle between Inspected VS Dropped, click on 1h, 3h, 6h and click at any point on the trend for further drilling down.
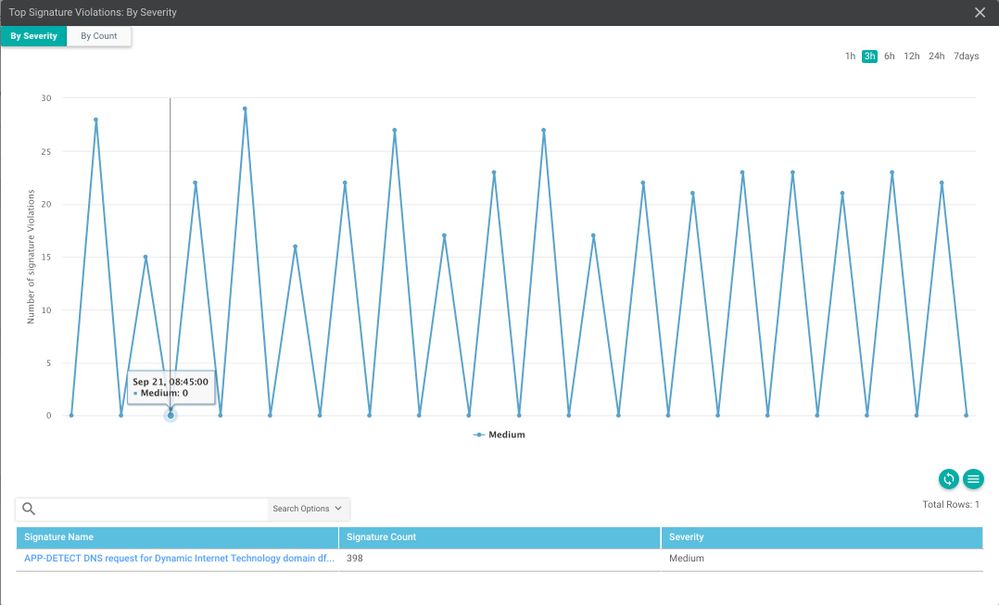
IPS
Toggle between "By Severity" or "By Count" to further drill-down by signature name on the bottom that will show more details about the 5-tuples responsible for triggering the signature.
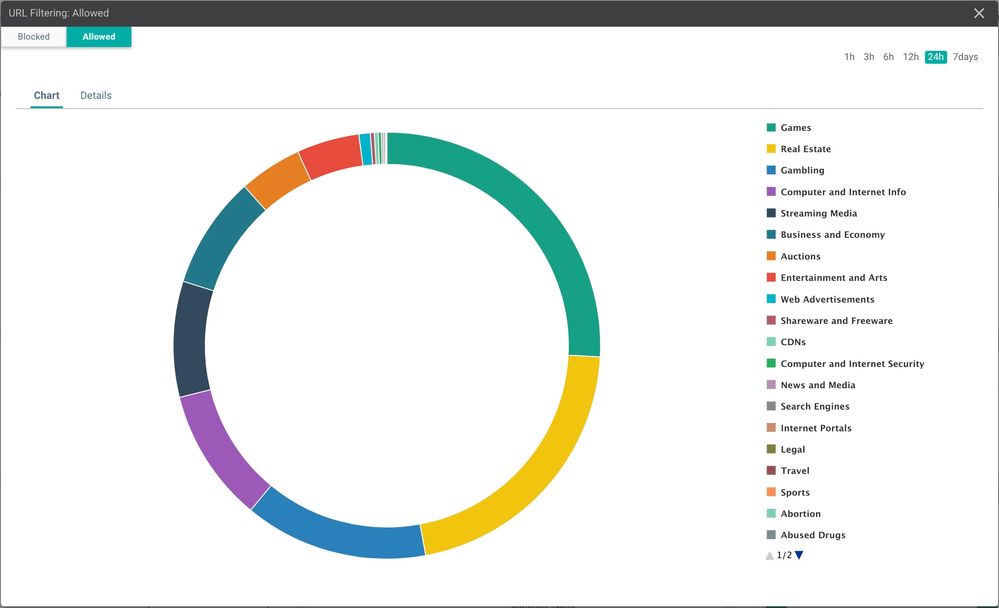
URL Filtering
Toggle between "Blocked" VS "Allowed" and click on certain color band to get more details about the number of sessions processed by all the devices in the enterprise for the particular category.
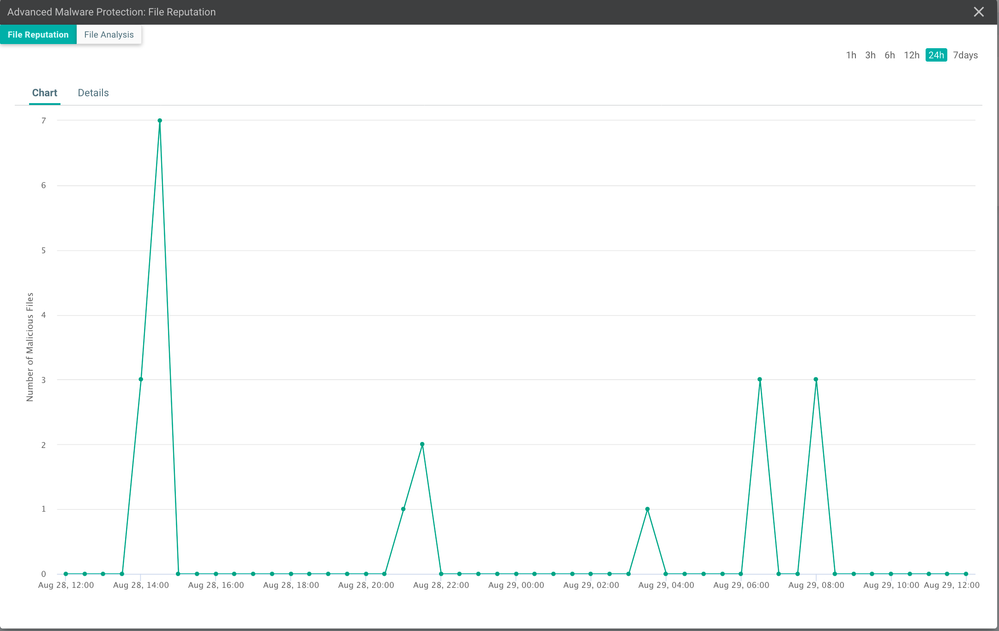
Advanced Malware Protection (AMP/TG)
Toggle between "File Reputation" for AMP and "File Analysis" for Threat Grid, and click on any point in the graph to get additional details such as the devices where the malicious files were seen and number of times they were seen.
Device-Specific Dashboard
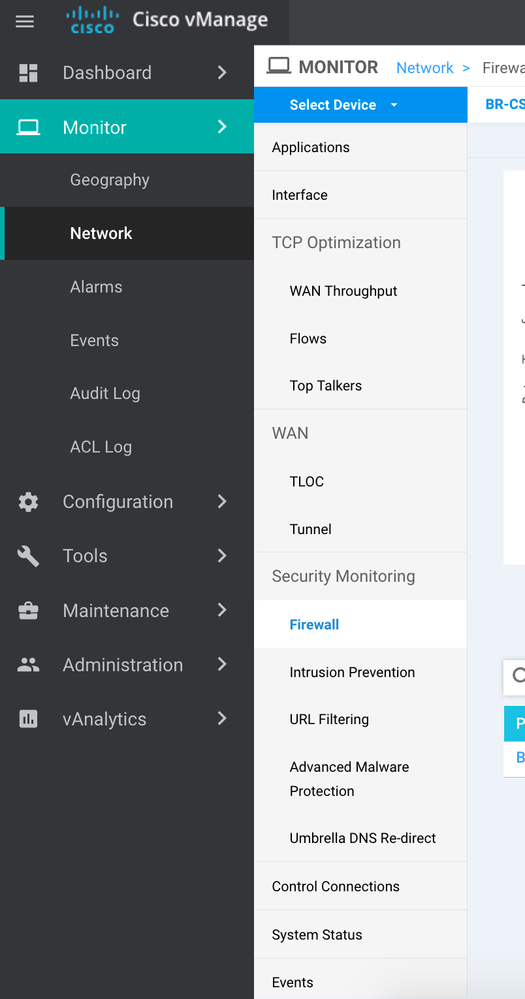
Click under Monitor >> Network and choose the device in question and choose one feature at a time under "Security Monitoring"
Choose all different options and drill downs. This dashboard has "Umbrella DNS re-direct" as well.
Real Time Data
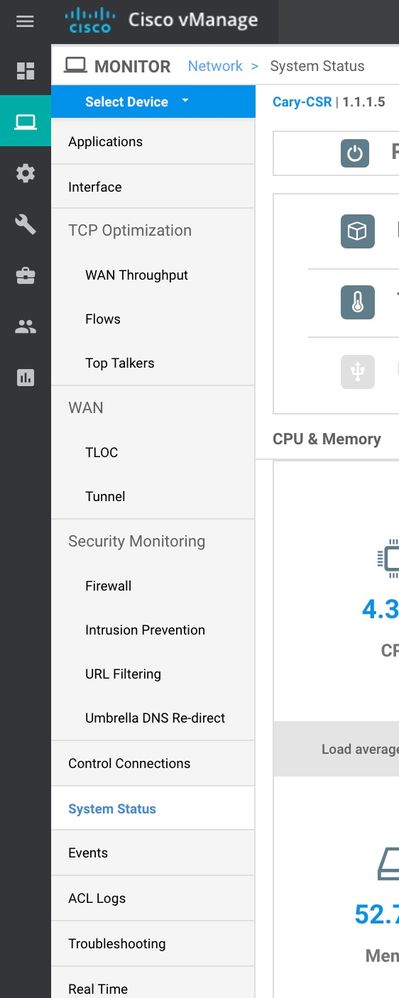
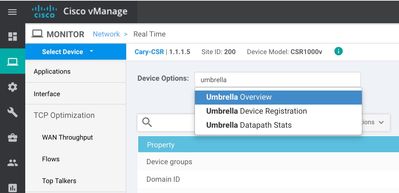
Under the device specific dashboard, you can get some real time stats on the security features. For example if you click under Monitor >> Network >> Choose the device >> Real Time (very bottom on the left pane).
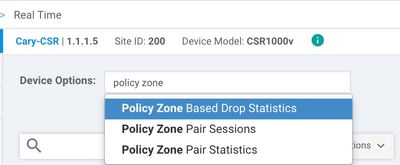
You can type "Policy Zone" and get FW statics real time as shown below:
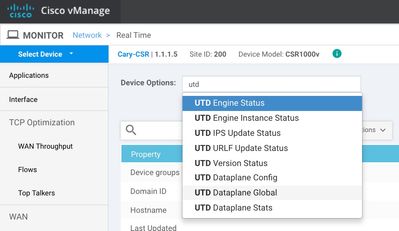
You can type "UTD" and get IPS statics real time as shown below:
You can type "Umbrella" and get Umbrella (DNS/web-layer security) statics real time outputs as shown below:
Further reading
Refer to the release notes, configuration guides and troubleshooting guide for further information on SD-WAN Security
- https://www.cisco.com/c/en/us/support/routers/xe-sd-wan-routers/products-release-notes-list.html
- https://www.cisco.com/c/en/us/support/routers/sd-wan/products-installation-and-configuration-guides-list.html
- https://community.cisco.com/t5/networking-documents/sd-wan-security-troubleshooting-guide/ta-p/3735301
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
this is the most in-depth content I've ever seen about SD wan security deployment. I'd love to add some of the points from your article to our ultimate guide on Understanding SD WAN basics here managed SD wan
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: