Hello folk,
Many times a packet capture needs to be performed within the network to diagnose network issues. Luckily there are a couple of platforms (IOS, IOS-XE and ASA) that allow packet captures to be taken on the network devices themselves. However extracting the packet capture from those devices can be an onerous task requiring installation of software, multiple copy operations before the capture can be opened and analyzed. With the iterative nature of troubleshooting multiple capture are often needed forcing the admin to repeat the multiple operations just to get to the packet capture.
For instance:
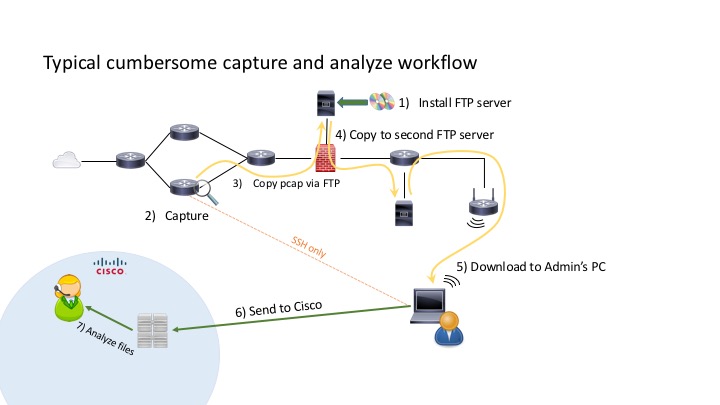
Today a new tool for Cisco Customers has been released. It helps walk the administrator through configuring the capture, starting the capture, stopping it, and most importantly extracting the capture off the device solely via the SSH/CLI session.
The tool is available here:
https://cway.cisco.com/tools/CaptureGenAndAnalyse/
Step 1) The tool guide you to collect the capture
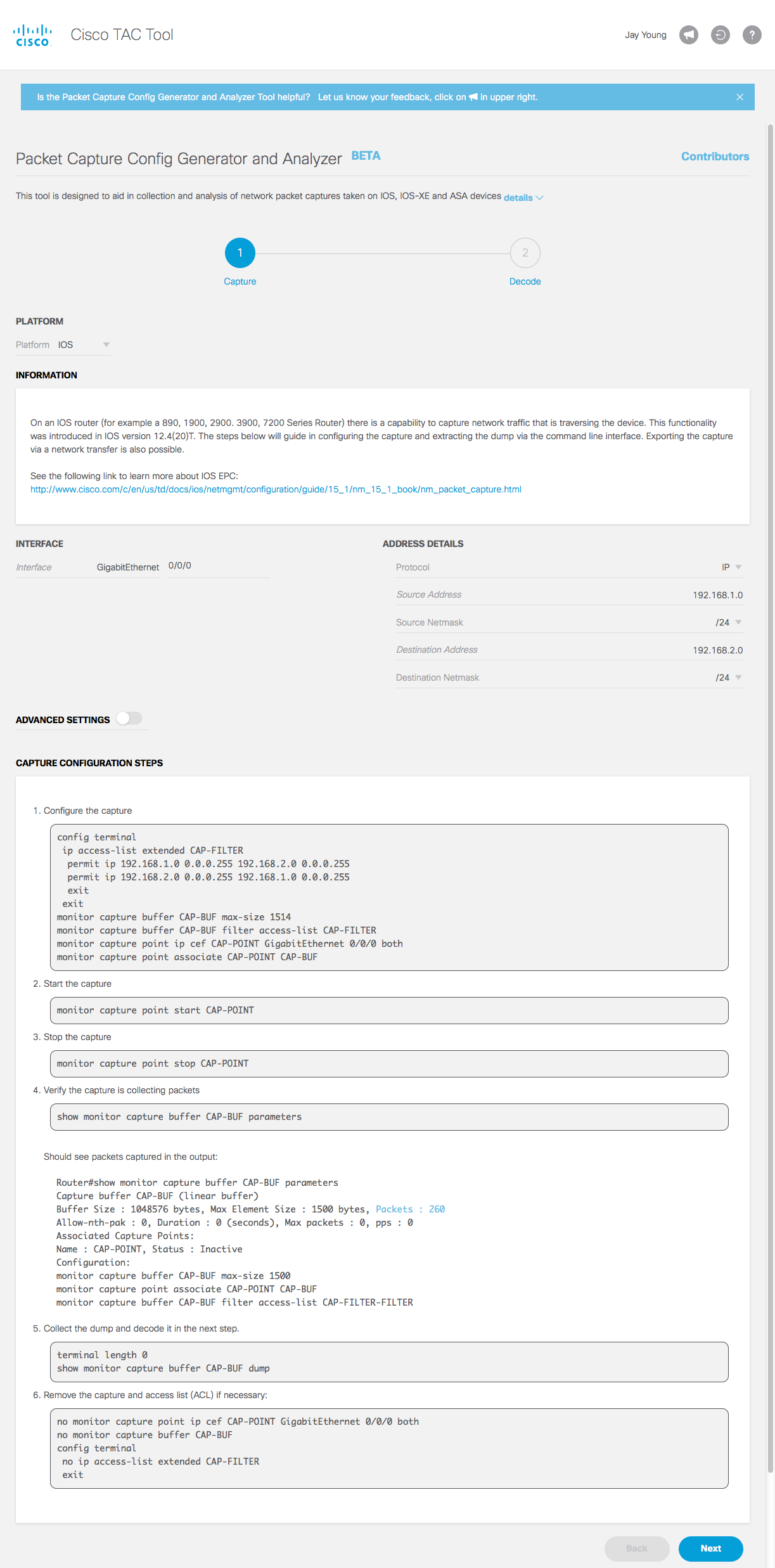
Step 2) The tool decodes the output and presents you with a binary copy of the capture and a basic decoding.
