- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Understanding DHCPv6 Guard
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-18-2013 10:46 AM - edited 03-01-2019 04:55 PM
Introduction:
DHCPv6 guard feature blocks DHCP reply and advertisement messages that originate from unauthorized DHCP servers and relay agents that forward DHCP packets from servers to clients. Client messages or messages sent by relay agents from clients to servers are not blocked. The filtering decision is determined by the device role assigned to the receiving switch port, trunk, or VLAN. This functionality helps to prevent traffic redirection or denial of service (DoS).
Let's discussed about common problem scenario also called man-in-middle attack:
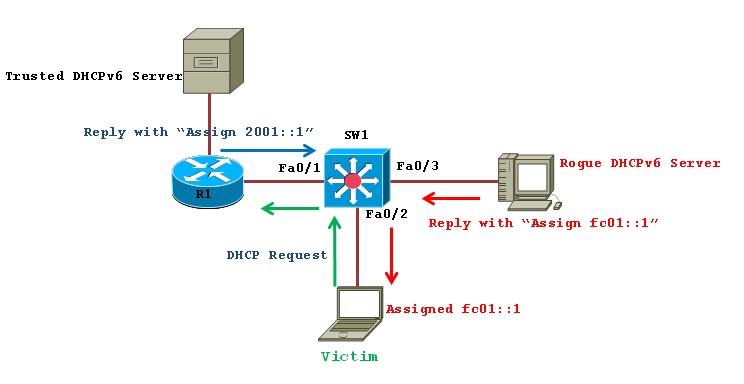
We’ve got our multilayer switch in the center and somewhere off to the side of router R1,we’ve got a DHCPv6 server which is our legitimate device. And in our access domain on the down we have our victim, who is a person coming into work on a normal morning, turning on his Laptop and requesting a DHCPv6 address with a solicit message. Unfortunately for him, a neighbor of his is the rogue man sitting next to him in the cubicle, can see his DHCP solicit message and can actually reply, pretending that he is the DHCPv6 server and assign credentials and…such as the DNS address to be used etc. and which he can use then to redirect traffic to himself. So, unprotected, this would be a very dangerous position. So for people to protect themselves in this sort of network layer by simply turning on IPv6 Snooping. By turning on IPv6 Snooping, you automatically drop the switch into “Guard Mode” which will turn on DHCPv6 Guard as well as RA Guard; so none of the redirect advertisements or any DHCPv6 server messages will get through.
Configuration Example:
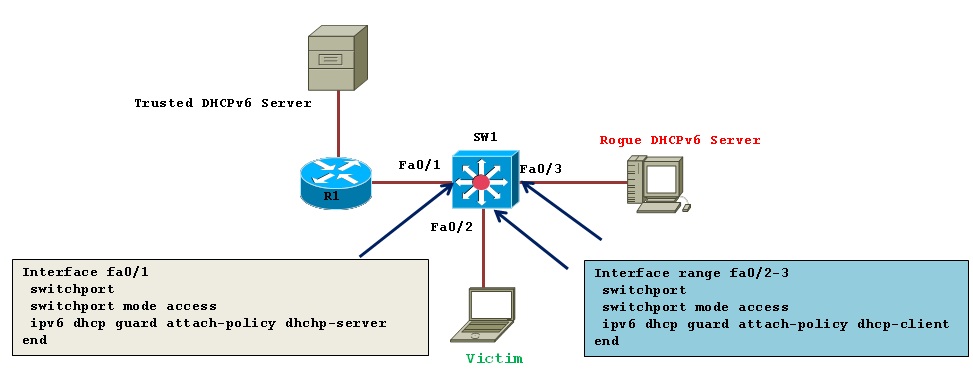
There are two mode:
1) Client: Sets the role of the device to client.
2) Server: Sets the role of the device to server.
Since the default mode of the switch is to “guard”, by default all ports configured with dhcpv6 guard will be in client mode. Thus all ports will be dropping any dhcpv6 server messages by default.
Additional security can be achieved by assigning an access list to only permit dhcpv6 server messages from a specific source address. Assigning a prefix-list to allow address allocation only from a known prefix (i.e. the server has been compromised).
1) 1st Assign Policy for Hosts:
For the Host facing ports you don’t need to do this, but if you want to explicitly configure this, that’s how you do it.
SW1(config)#ipv6 dhcp guard policy dhcp-client
SW1(config-dhcp-guard)#device-role client
Interface range fa0/2-3
switchport
switchport mode access
ipv6 dhcp guard attach-policy dhcp-client
end
2) Then assign policy for DHCP server facing port:
For the server facing ports, you need create DHCPv6 Guard policy.
SW1(config)#ipv6 dhcp guard policy dhcp-server
SW1(config-dhcp-guard)#device-role server
SW1(config-dhcp-guard)#match server access-list ACL1
SW1(config-dhcp-guard)#match reply prefix-list PREF1
You can also provide some extra functionality over access lists; you could block server messages for particular addresses using an access list and you could also block some advertisements from the DHCPv6 server blocking certain prefixes using a prefix list as shown below:
SW1(config)#ipv6 access-list ACL1
SW1(config-ipv6-acl)#permit ipv6 host FE80::1 any
SW1(config)#ipv6 prefix-list PREF1 seq 5 permit 2001::/64 le 128
Interface fa0/1
switchport
switchport mode access
ipv6 dhcp guard attach-policy dhcp-server
end
Verification:
SW1#show ipv6 dhcp guard policy
Dhcp guard policy: dhcp-client
Device Role: dhcp client
Target: fa0/2 fa0/3
Dhcp guard policy: dhcp-server
Device Role: dhcp server
Target: fa0/1
Max Preference: 255
Min Preference: 0
Source Address Match Access List: ACL1
Prefix List Match Prefix List: PREF1
SW1#show ipv6 access-list ACL1
IPv6 access list ACL1
permit ipv6 host FE80::1 any (5 matches) sequence 10
SW1#show ipv6 prefix-list
ipv6 prefix-list PREF1: 1 entries
seq 5 permit 2001::/64 le 128
Debug Commands for troubleshooting:
SW1#debug ipv6 snooping dhcp-guard
Related Information:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Dear Sir,
Many many thanks for your article of DHCPv6 guard.
Here i have a little confusion,
SW1(config)#ipv6 access-list ACL1
SW1(config-ipv6-acl)#permit ipv6 host FE80::1 any
This link local address is from SW1 interface fa0/1, which is connected to DHCPV6 server.
Am I right? If wrong please help me to understand.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Ashirkar,
Does Cisco DHCPv6 Guard prevent IPv4 roque DHCP Server also?
Thanks,
Audie
Update: Yes, using SISF will block IPv4 and IPv6 rogue DHCP servers
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: