Data Center Design question - Firewalls, LB at the access layer as default gateways
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2017 10:15 AM - edited 03-01-2019 08:31 AM
Hello everybody,
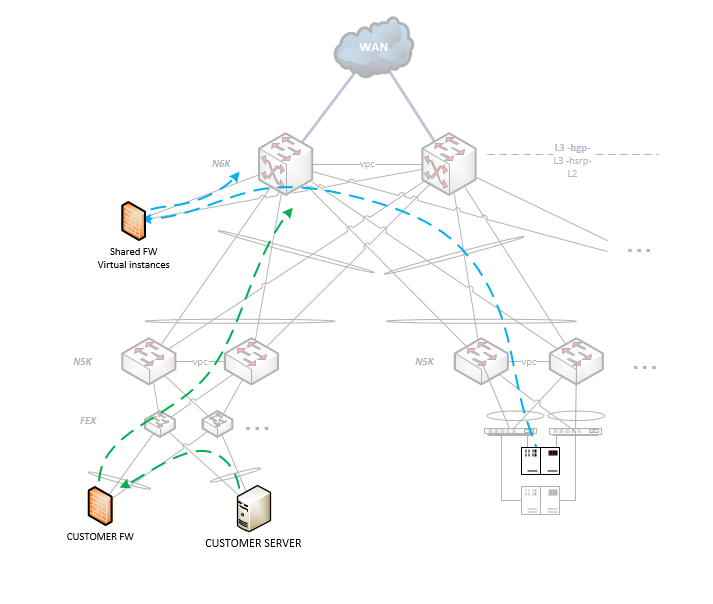
I'm currently reviewing the network architecture of a Data Center vs CIsco best practices. In the Data Center there are cloud services infrastructure, dedicated devices for specific customers (hosting), customer's own devices (colocation).
This is a small two-tier architecture of collapsed core/agg + access layers (diagram attached) and basically, one of the points I've found is related to the connection point of services devices (firewalls, load balancers, etc.), because Cisco's documentation for Data Center design talks about the services being connected at the aggregation layer, but I've found in this review, that most of the physical firewalls that only the big firewalls that are partitioned, are connected at the aggregation but most firewalls that are dedicated for a specific customer or are managed by costumers, are connected at the access layer on FEX or 5Ks because of multiple reasons:
- Most of them use 1G ports
- Because these firewalls are always the default gateway for the servers. (There is no protected vrf)
- Because one of the access layer PoD is physically located on another cage and cabling to the aggregation would be expensive.
By now I've advised to consider possible micro-burst/buffer trouble scenarios with FEX that would require to move connections to the 5Ks switches, besides that, I really don't find much more recommendations or warnings and I've really not found documentation/best practices talking about this scenarios, so I'd really appreciate your opinión on this and/or maybe some references to investigate.
Thanks.
- Labels:
-
Other Data Center Topics
