- Cisco Community
- Technology and Support
- Security
- VPN
- ipsec vpn - no proposal chosen
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2013 08:28 AM - edited 02-21-2020 06:48 PM
HELLO:
I am facing a problem when configuring the ipsec vpn on my 7200 router. This was a site to client topology like shown bellow.
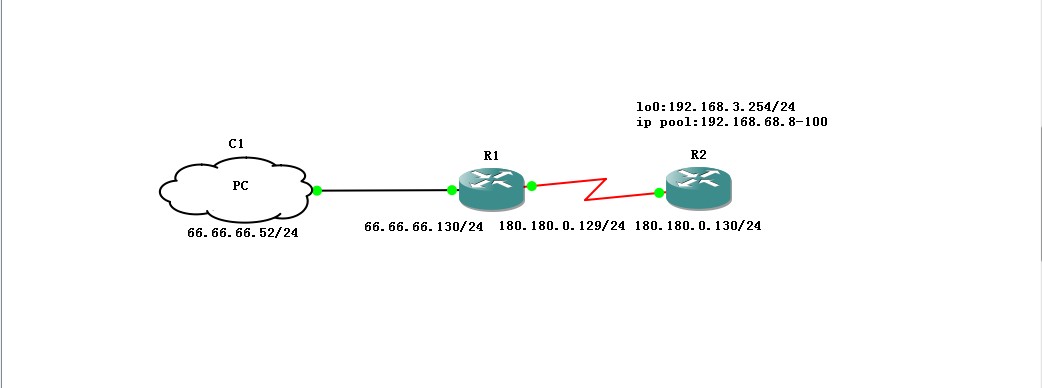
when my pc requests, R2'crypto isa log :
R2#debug crypto isakmp
Crypto ISAKMP debugging is on
R2#
R2#
R2#
*Apr 6 22:41:59.871: ISAKMP (0): received packet from 66.66.66.52 dport 500 sport 500 Global (N) NEW SA
*Apr 6 22:41:59.879: ISAKMP: Created a peer struct for 66.66.66.52, peer port 500
*Apr 6 22:41:59.879: ISAKMP: New peer created peer = 0x67E98D84 peer_handle = 0x80000002
*Apr 6 22:41:59.883: ISAKMP: Locking peer struct 0x67E98D84, refcount 1 for crypto_isakmp_process_block
*Apr 6 22:41:59.887: ISAKMP: local port 500, remote port 500
*Apr 6 22:41:59.891: ISAKMP:(0):insert sa successfully sa = 67E5DCD8
*Apr 6 22:41:59.911: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Apr 6 22:41:59.911: ISAKMP:(0):Old State = IKE_READY New State = IKE_R_MM1
*Apr 6 22:41:59.931: ISAKMP:(0): processing SA payload. message ID = 0
*Apr 6 22:41:59.935: ISAKMP:(0): processing vendor id payload
*Apr 6 22:41:59.939: ISAKMP:(0): processing IKE frag vendor id payload
*Apr 6 22:41:59.939: ISAKMP:(0): processing vendor id payload
*Apr 6 22:41:59.943: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
*Apr 6 22:41:59.947: ISAKMP (0): vendor ID is NAT-T RFC 3947
*Apr 6 22:41:59.947: ISAKMP:(0): processing vendor id payload
*Apr 6 22:41:59.951: ISAKMP:(0): vendor ID seems Unity/DPD but major 123 mismatch
*Apr 6 22:41:59.955: ISAKMP:(0): vendor ID is NAT-T v2
*Apr 6 22:41:59.959: ISAKMP:(0): processing vendor id payload
*Apr 6 22:41:59.959: ISAKMP:(0): vendor ID seems Unity/DPD but major 194 mismatch
*Apr 6 22:41:59.963: ISAKMP:(0): processing vendor id payload
*Apr 6 22:41:59.967: ISAKM
R2#P:(0): vendor ID seems Unity/DPD but major 241 mismatch
*Apr 6 22:41:59.971: ISAKMP:(0): processing vendor id payload
*Apr 6 22:41:59.971: ISAKMP:(0): vendor ID seems Unity/DPD but major 184 mismatch
*Apr 6 22:41:59.975: ISAKMP:(0): processing vendor id payload
*Apr 6 22:41:59.979: ISAKMP:(0): vendor ID seems Unity/DPD but major 134 mismatch
*Apr 6 22:41:59.983: ISAKMP:(0):found peer pre-shared key matching 66.66.66.52
*Apr 6 22:41:59.987: ISAKMP:(0): local preshared key found
*Apr 6 22:41:59.987: ISAKMP : Scanning profiles for xauth ...
*Apr 6 22:41:59.991: ISAKMP:(0):Checking ISAKMP transform 1 against priority 10 policy
*Apr 6 22:41:59.995: ISAKMP: encryption AES-CBC
*Apr 6 22:41:59.995: ISAKMP: keylength of 256
*Apr 6 22:41:59.999: ISAKMP: hash SHA
*Apr 6 22:41:59.999: ISAKMP: unknown DH group 20
*Apr 6 22:41:59.999: ISAKMP: auth pre-share
*Apr 6 22:42:00.003: ISAKMP: life type in seconds
*Apr 6 22:42:00.003: ISAKMP:
R2# life duration (VPI) of 0x0 0x0 0x70 0x80
*Apr 6 22:42:00.011: ISAKMP:(0):Encryption algorithm offered does not match policy!
*Apr 6 22:42:00.011: ISAKMP:(0):atts are not acceptable. Next payload is 3
*Apr 6 22:42:00.011: ISAKMP:(0):Checking ISAKMP transform 2 against priority 10 policy
*Apr 6 22:42:00.011: ISAKMP: encryption AES-CBC
*Apr 6 22:42:00.011: ISAKMP: keylength of 128
*Apr 6 22:42:00.011: ISAKMP: hash SHA
*Apr 6 22:42:00.011: ISAKMP: unknown DH group 19
*Apr 6 22:42:00.011: ISAKMP: auth pre-share
*Apr 6 22:42:00.011: ISAKMP: life type in seconds
*Apr 6 22:42:00.011: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Apr 6 22:42:00.011: ISAKMP:(0):Encryption algorithm offered does not match policy!
*Apr 6 22:42:00.011: ISAKMP:(0):atts are not acceptable. Next payload is 3
*Apr 6 22:42:00.011: ISAKMP:(0):Checking ISAKMP transform 3 against priority 10 policy
R2#r 6 22:42:00.011: ISAKMP: encryption AES-CBC
*Apr 6 22:42:00.011: ISAKMP: keylength of 256
*Apr 6 22:42:00.011: ISAKMP: hash SHA
*Apr 6 22:42:00.011: ISAKMP: unknown DH group 14
*Apr 6 22:42:00.011: ISAKMP: auth pre-share
*Apr 6 22:42:00.011: ISAKMP: life type in seconds
*Apr 6 22:42:00.011: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Apr 6 22:42:00.011: ISAKMP:(0):Encryption algorithm offered does not match policy!
*Apr 6 22:42:00.011: ISAKMP:(0):atts are not acceptable. Next payload is 3
*Apr 6 22:42:00.011: ISAKMP:(0):Checking ISAKMP transform 4 against priority 10 policy
*Apr 6 22:42:00.011: ISAKMP: encryption 3DES-CBC
*Apr 6 22:42:00.011: ISAKMP: hash SHA
*Apr 6 22:42:00.011: ISAKMP: unknown DH group 14
*Apr 6 22:42:00.011: ISAKMP: auth pre-share
*Apr 6 22:42:00.011: ISAKMP: life type in seconds
*Apr 6 22:42:00.011: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Apr 6 22:42:00.011: ISAKMP:(0):Hash algorithm offered does
R2# not match policy!
*Apr 6 22:42:00.011: ISAKMP:(0):atts are not acceptable. Next payload is 3
*Apr 6 22:42:00.011: ISAKMP:(0):Checking ISAKMP transform 5 against priority 10 policy
*Apr 6 22:42:00.011: ISAKMP: encryption 3DES-CBC
*Apr 6 22:42:00.011: ISAKMP: hash SHA
*Apr 6 22:42:00.011: ISAKMP: default group 2
*Apr 6 22:42:00.011: ISAKMP: auth pre-share
*Apr 6 22:42:00.011: ISAKMP: life type in seconds
*Apr 6 22:42:00.015: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Apr 6 22:42:00.019: ISAKMP:(0):Hash algorithm offered does not match policy!
*Apr 6 22:42:00.023: ISAKMP:(0):atts are not acceptable. Next payload is 0
*Apr 6 22:42:00.023: ISAKMP:(0):no offers accepted!
*Apr 6 22:42:00.027: ISAKMP:(0): phase 1 SA policy not acceptable! (local 180.180.0.130 remote 66.66.66.52)
*Apr 6 22:42:00.027: ISAKMP (0): incrementing error counter on sa, attempt 1 of 5: construct_fail_ag_init
*Apr 6 22:42:00.027: ISAKMP:(0): Failed to
R2#construct AG informational message.
*Apr 6 22:42:00.027: ISAKMP:(0): sending packet to 66.66.66.52 my_port 500 peer_port 500 (R) MM_NO_STATE
*Apr 6 22:42:00.027: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Apr 6 22:42:00.031: ISAKMP:(0):peer does not do paranoid keepalives.
*Apr 6 22:42:00.035: ISAKMP:(0):deleting SA reason "Phase1 SA policy proposal not accepted" state (R) MM_NO_STATE (peer 66.66.66.52)
*Apr 6 22:42:00.039: ISAKMP:(0): processing vendor id payload
*Apr 6 22:42:00.039: ISAKMP:(0): processing IKE frag vendor id payload
*Apr 6 22:42:00.039: ISAKMP:(0): processing vendor id payload
*Apr 6 22:42:00.039: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
*Apr 6 22:42:00.039: ISAKMP (0): vendor ID is NAT-T RFC 3947
*Apr 6 22:42:00.039: ISAKMP:(0): processing vendor id payload
*Apr 6 22:42:00.039: ISAKMP:(0): vendor ID seems Unity/DPD but major 123 mismatch
*Apr 6 22:42:00.039: ISAKMP:(0): vendor ID is NAT-T v2
*Apr 6 22:42:00.039: ISAKMP:(0)
R2#: processing vendor id payload
*Apr 6 22:42:00.039: ISAKMP:(0): vendor ID seems Unity/DPD but major 194 mismatch
*Apr 6 22:42:00.039: ISAKMP:(0): processing vendor id payload
*Apr 6 22:42:00.039: ISAKMP:(0): vendor ID seems Unity/DPD but major 241 mismatch
*Apr 6 22:42:00.039: ISAKMP:(0): processing vendor id payload
*Apr 6 22:42:00.039: ISAKMP:(0): vendor ID seems Unity/DPD but major 184 mismatch
*Apr 6 22:42:00.039: ISAKMP:(0): processing vendor id payload
*Apr 6 22:42:00.039: ISAKMP:(0): vendor ID seems Unity/DPD but major 134 mismatch
*Apr 6 22:42:00.039: ISAKMP (0): FSM action returned error: 2
*Apr 6 22:42:00.039: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Apr 6 22:42:00.039: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM1
*Apr 6 22:42:00.059: ISAKMP:(0):deleting SA reason "Phase1 SA policy proposal not accepted" state (R) MM_NO_STATE (peer 66.66.66.52)
*Apr 6 22:42:00.059: ISAKMP: Unlocking peer struct 0x67E98D84 for isadb_m
R2#ark_sa_deleted(), count 0
*Apr 6 22:42:00.067: ISAKMP: Deleting peer node by peer_reap for 66.66.66.52: 67E98D84
*Apr 6 22:42:00.071: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Apr 6 22:42:00.075: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_DEST_SA
*Apr 6 22:42:00.087: ISAKMP:(0):deleting SA reason "No reason" state (R) MM_NO_STATE (peer 66.66.66.52)
*Apr 6 22:42:00.087: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_ERROR
*Apr 6 22:42:00.087: ISAKMP:(0):Old State = IKE_DEST_SA New State = IKE_DEST_SA
*Apr 6 22:42:00.895: ISAKMP (0): received packet from 66.66.66.52 dport 500 sport 500 Global (R) MM_NO_STATE
*Apr 6 22:42:02.911: ISAKMP (0): received packet from 66.66.66.52 dport 500 sport 500 Global (R) MM_NO_STATE
R2#
*Apr 6 22:43:00.087: ISAKMP:(0):purging SA., sa=67E5DCD8, delme=67E5DCD8
R2#
And when I capture on my pc ,I got:
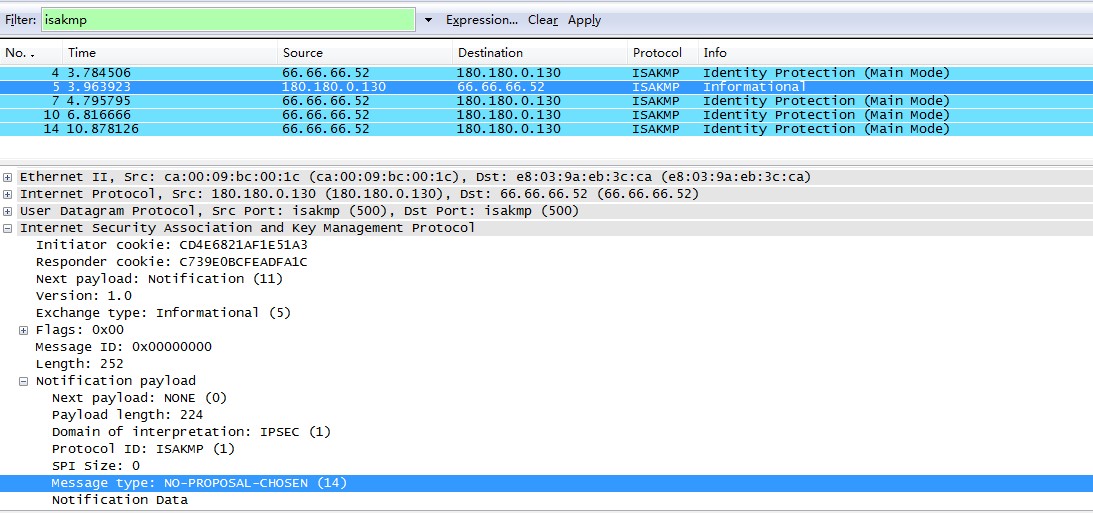
I don't know why,waiting for you kindly help,thanks very much!
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2013 08:01 AM
I think what is wrong is your combination of your encryption, hash and dh group, try to change your hash to sha instead of md5.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2013 12:43 AM
are you using vpn client or anyconnect? can you post your crypto/vpn configuration? you should move the topic to the VPN section.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2013 07:42 AM
I am using the vpn client of win7 system, is it not supported?
and my configuration:
aaa authentication ppp default local
!
!
aaa session-id common
ip source-route
ip cef
!
no ip domain lookup
no ipv6 cef
!
multilink bundle-name authenticated
vpdn enable
!
vpdn-group cisco
! Default L2TP VPDN group
accept-dialin
protocol l2tp
virtual-template 1
no l2tp tunnel authentication
!
!
username cisco password 0 cisco
archive
log config
hidekeys
!
!
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key feixunst address 0.0.0.0 0.0.0.0
crypto isakmp fragmentation
crypto isakmp keepalive 20 5
crypto isakmp nat keepalive 30
!
!
crypto ipsec transform-set feixunset esp-3des esp-md5-hmac
mode transport
!
crypto dynamic-map feixundy 10
set transform-set feixunset
match address 101
!
!
crypto map feixunmap 10 ipsec-isakmp dynamic feixundy
!
!
interface Loopback0
ip address 192.168.3.254 255.255.255.0
!
interface FastEthernet0/0
no ip address
shutdown
duplex half
!
interface Serial1/0
ip address 180.180.0.130 255.255.255.0
serial restart-delay 0
crypto map feixunmap
!
interface Virtual-Template1
ip unnumbered Serial1/0
peer default ip address pool default
ppp authentication chap ms-chap ms-chap-v2
!
ip local pool default 192.168.68.8 192.168.68.100
ip forward-protocol nd
ip route 66.66.66.0 255.255.255.0 180.180.0.129
no ip http server
no ip http secure-server
!
access-list 101 permit ip any any
!
!
!
line con 0
exec-timeout 0 0
logging synchronous
stopbits 1
line aux 0
stopbits 1
line vty 0 4
!
end
aaa authentication ppp default local
!
!
aaa session-id common
ip source-route
ip cef
no ip domain lookup
no ipv6 cef
!
multilink bundle-name authenticated
vpdn enable
!
vpdn-group cisco
! Default L2TP VPDN group
accept-dialin
protocol l2tp
virtual-template 1
no l2tp tunnel authentication
!
memory-size iomem 0
username cisco password 0 cisco
archive
log config
hidekeys
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key feixunst address 0.0.0.0 0.0.0.0
crypto isakmp fragmentation
crypto isakmp keepalive 20 5
crypto isakmp nat keepalive 30
!
crypto ipsec transform-set feixunset esp-3des esp-md5-hmac
mode transport
!
crypto dynamic-map feixundy 10
set transform-set feixunset
match address 101
!
!
crypto map feixunmap 10 ipsec-isakmp dynamic feixundy
!
!
interface Loopback0
ip address 192.168.3.254 255.255.255.0
!
interface Serial1/0
ip address 180.180.0.130 255.255.255.0
serial restart-delay 0
crypto map feixunmap
interface Virtual-Template1
ip unnumbered Serial1/0
peer default ip address pool default
ppp authentication chap ms-chap ms-chap-v2
!
ip local pool default 192.168.68.8 192.168.68.100
ip forward-protocol nd
ip route 66.66.66.0 255.255.255.0 180.180.0.129
no ip http server
no ip http secure-server
!
logging alarm informational
access-list 101 permit ip any any
control-plane
!
line con 0
exec-timeout 0 0
logging synchronous
stopbits 1
line aux 0
stopbits 1
line vty 0 4
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2013 08:01 AM
I think what is wrong is your combination of your encryption, hash and dh group, try to change your hash to sha instead of md5.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2013 11:11 PM
Thanks very much![]()
![]() ,I successed after changing hash to sha.
,I successed after changing hash to sha.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2013 12:50 AM
great! don't forget to mark this post as answered. thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2017 02:12 PM
Hi Friend,
I am implementing the ipsec on centos7.2 with libreswan and getting the same error like below.. could u please help me on this.
Apr 27 16:57:48 DS-990 pluto[2884]: packet from 191.98.15.181:500: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02]
Apr 27 16:57:48 DS-990 pluto[2884]: "mytunnel" #58: enabling possible NAT-traversal with method RFC 3947 (NAT-Traversal)
Apr 27 16:57:48 DS-990 pluto[2884]: "mytunnel" #58: responding to Main Mode
Apr 27 16:57:48 DS-990 pluto[2884]: "mytunnel" #58: policy does not allow OAKLEY_PRESHARED_KEY authentication. Attribute OAKLEY_AUTHENTICATION_METHOD
Apr 27 16:57:48 DS-990 pluto[2884]: "mytunnel" #58: policy does not allow OAKLEY_PRESHARED_KEY authentication. Attribute OAKLEY_AUTHENTICATION_METHOD
Apr 27 16:57:48 DS-990 pluto[2884]: "mytunnel" #58: no acceptable Oakley Transform
Apr 27 16:57:48 DS-990 pluto[2884]: "mytunnel" #58: sending notification NO_PROPOSAL_CHOSEN to 191.98.15.181:500
Apr 27 16:57:48 DS-990 pluto[2884]: "mytunnel" #58: deleting state #58 (STATE_MAIN_R0)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide